Microsoft released Active Directory in 1999 and is still used by 90% of the world's…
A fatal error occurred while creating a TLS client credential
The monitoring software triggers you with the error Event ID 36871: A fatal error occurred while creating a TLS client credential. The internal error state is 10013. In this article, you will learn why this is happening, and the solution for a fatal error occurred while creating a TLS client credential.
Table of contents
A fatal error occurred while creating a TLS client credential
Sign in to the Windows Server and start Event Viewer. Navigate to Windows Logs > System. You will see error Event ID 36871. A fatal error occurred while creating a TLS client credential. The internal error state is 10013.
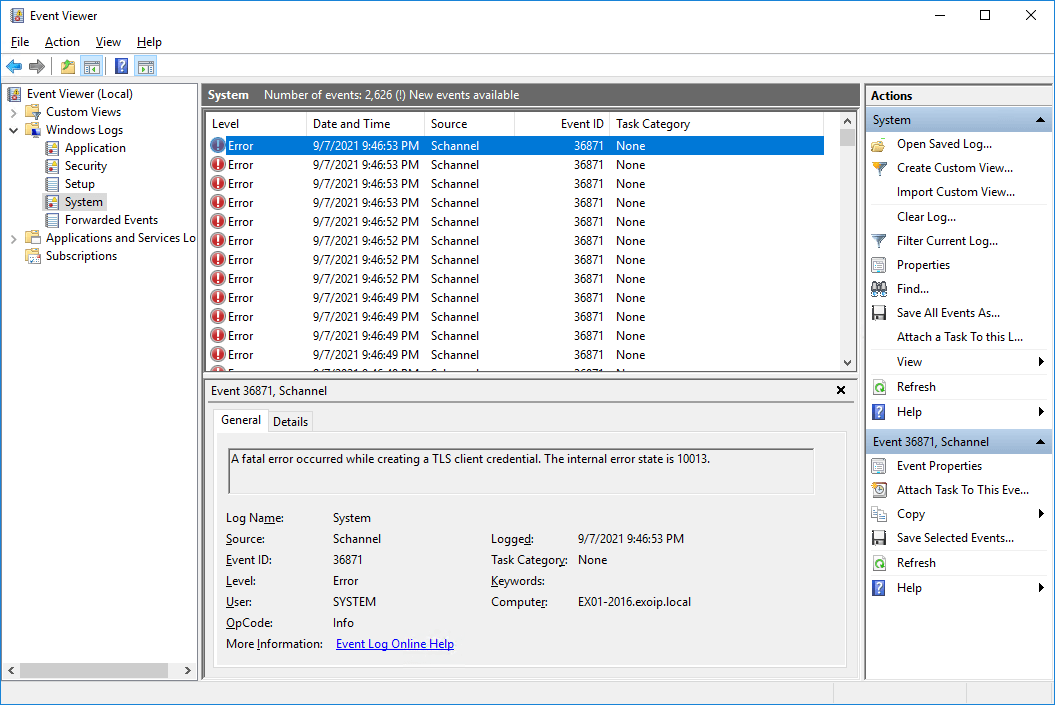
Why do we get this error, and what is the solution for a fatal error occurred while creating a TLS client credential. The internal error state is 10013?
Check Transport Layer Security protocols
Schannel is a Security Support Provider (SSP) that implements the Secure Sockets Layer (SSL) and Transport Layer Security (TLS) Internet standard authentication protocols.
Download IIS Crypto GUI by Nartac Software. After the application is downloaded, start the application.
We see that Server Protocols and Client Protocols TLS 1.0 and TLS 1.1 are unchecked.
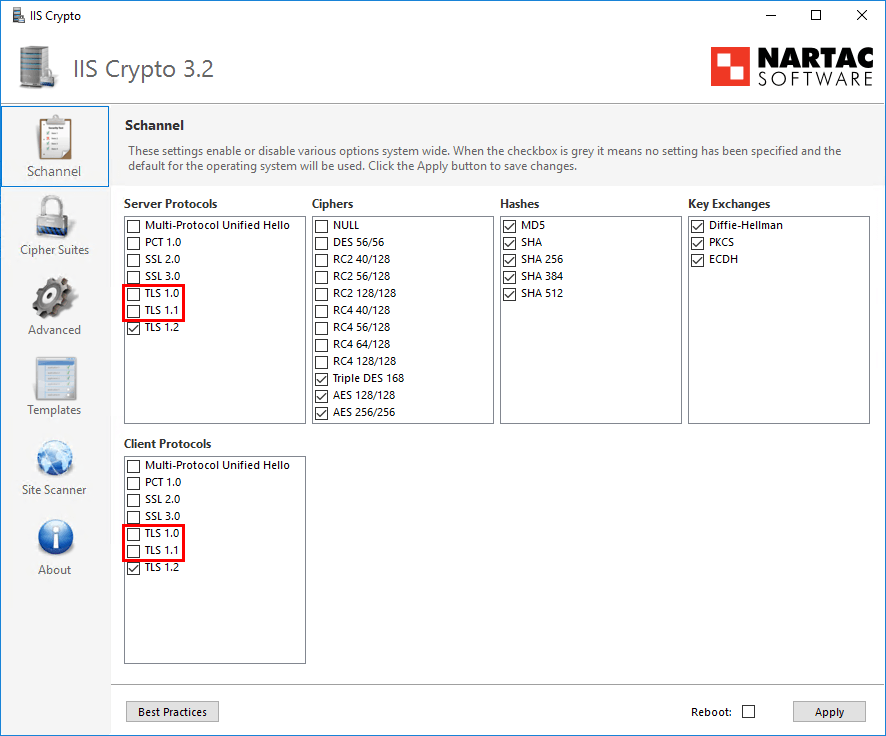
If we click on Best Practices, it will enable Server Protocols and Client Protocols TLS 1.0 and TLS 1.1. After a reboot, the event error will not show up. When doing that, we fix the problem, but we enable the deprecated protocols. That’s what we do not want.
So how do we keep TLS 1.0 and TLS 1.1 unchecked (disabled) without a fatal error TLS client credential 10013 from showing up?
Transport Layer Security protocols status
See a list of the security protocols and when they are published, including the current status.
Note: Only TLS 1.3 and TLS 1.2 are approved. The protocol TLS 1.3 is only available to enable in Windows Server 2022 or newer.
| Protocol | Published | Status |
|---|---|---|
| SSL 2.0 | 1995 | Deprecated in 2011 |
| SSL 3.0 | 1996 | Deprecated in 2015 |
| TLS 1.0 | 1999 | Deprecated in 2020 |
| TLS 1.1 | 2006 | Deprecated in 2020 |
| TLS 1.2 | 2008 | Approved |
| TLS 1.3 | 2018 | Approved |
Solution for a fatal error occurred while creating a TLS client credential
Now that we gathered all the information, we are going to enable TLS 1.2 on the system by running the script. After a reboot, we will check the Event Viewer. It should not show any errors.
- Download Enable-TLS1.2.ps1 PowerShell script if you have Windows Server 2019 or lower / Download Enable-TLS1.3.ps1 PowerShell script if you have Windows Server 2022 or higher
- Save the script in the C:\scripts folder
- Run the script from PowerShell
C:\scripts\.\Enable-TLS1.2.ps1- Reboot the Windows Server
Start Event Viewer. Expand Windows Logs and click System. The error “Event ID 36871: A fatal error occurred while creating a TLS client credential. The internal error state is 10013.” doesn’t show up anymore.
Did it work for you?
Conclusion
You learned why you get a fatal error occurred while creating a TLS client credential. The internal error state is 10013. The solution to this problem is configuring TLS 1.2 on the Windows Server. After that, you don’t see the Event ID 36871 errors in Event Viewer.
Did you enjoy this article? You may also like How to Enable TLS 1.2/TLS 1.3 on Windows Server. Don’t forget to follow us and share this article.



Thanks, Very helpful!
Well done… found lots of other articles that just talked about SSL / TLS settings but looks like the root cause is .net still trying to use depracated cihpers. The top part of your script telling .net to use 1.2 for default was the fix on more than one server….
Exchange 2016 here. I was getting about 10 errors per second and it was filling up log file. This solution has decreased the error messages considerably. I only get the error only 2 per minute. Any way to get rid of the errors completely?
Thank you for the solution which was very helpful.
Hi Ali,
After making the changes on one out of four domain controllers I’ve started getting event log 36871 on the TLS 1.2 only enabled DC
I’ve double checked the registry settings and they are identical to the above script
When you made the changes in your environment did you do it in a specific order
1) domain controllers
2) exchange servers,
3) domain members
Thanks for your help!
What if i run this command on my network-connected machine?
Thanks for your site and articles very helpful more so than Microsoft.
Your script worked well after then making change to the advanced internet settings in inetcpl.cpl to use only TLS 1.2. The error messages disappeared from my event log! Hooray!
Thank you man!
After a few days, your script solve the problem we had to execute a program.
Best wishes to you man!
How about Pc workstations in a domain? I am trying to disable weak ciphers and strengthen security across the lan. I have seemed to have broken something if this TLS warning comes up on a Pc.
Дуже вам вдячний. Помилка зникла.
It worked for me (Windows 10 Pro 64 21H2)! Thanks!
1. Internet Option – Advanced – Disable TLS 1.2 – Reboot PC
2. Internet Option – Advanced – Enable TLS 1.2 – Reboot PC
disabling TLS, rebooting + enabling TLS, rebooting doesn’t work on Windows 11.
Also scripts around here and other internet sites to tweak registry don’t work.
Permissions are set as expected but no workarounds seem to fix this certificate issue, nor Windows updates.
The same for me in a Windows 10, I apply de ps1 that disable TLS 1.0 and 1.1 and disabled TLS 1.0 and 1.1 in Internet Options, but I got lots of registry error ID 36871 yet. Someone has solve it?
I have the exact same do to running the IIS Crypt disabling all but TLS 1.2, have all the registry entries in the correct places based on your post, running Server 2016, along with Exchange 2016 CU22 and I am still receiving the event error. I verified everything is correct… but still occurring. Thoughts?
Good write up, very helpful
Great stuff again! Thanks Ali!
Greetz,
Cor, CT Taxes
Thanks, Cor. Glad that you enjoyed it.