How to migrate Azure AD Connect to a new server? You have Azure AD Connect…
Active Directory weak password checker
How do you know if there is a weak password configured in Active Directory? For auditing and security-wise, it’s essential to have strong passwords. We recommend using an Active Directory weak password checker. In this article, you will learn how to audit with an Active Directory weak password finder tool.
Table of contents
Check Active Directory weak passwords
The product that we are going to talk about is Enzoic for Active Directory Lite. The tool scans for common passwords, passwords found in cracking dictionaries, and passwords that have been previously breached and exposed online. It also finds passwords reused within your organization. It’s a lightweight version of Enzoic for Active Directory, suitable for performing a quick audit using Enzoic’s proprietary database of 7+ billion exposed passwords.
Install Enzoic for Active Directory Lite
To install Enzoic for Active Directory Lite, follow these steps:
1. Go to the following page and download Enzoic for Active Directory Lite. The download size is 8 MB, and it’s a FREE product.
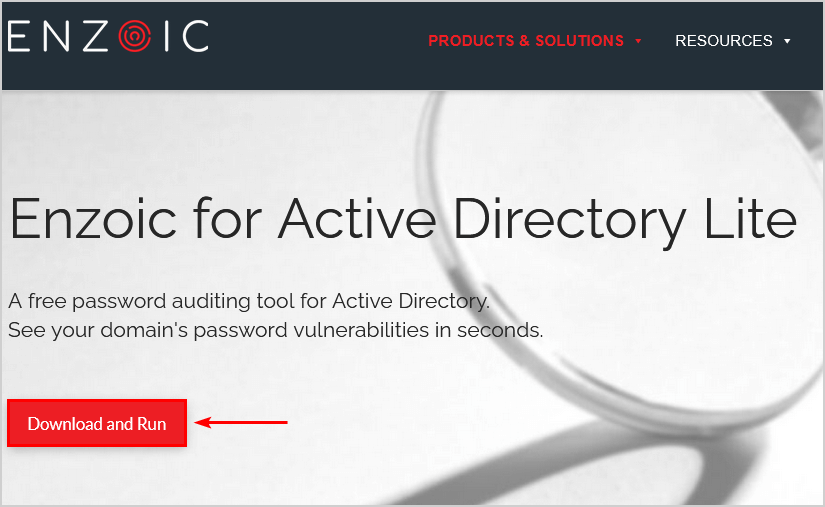
2. Go to the downloaded file. Next, right-click and select Run as administrator.
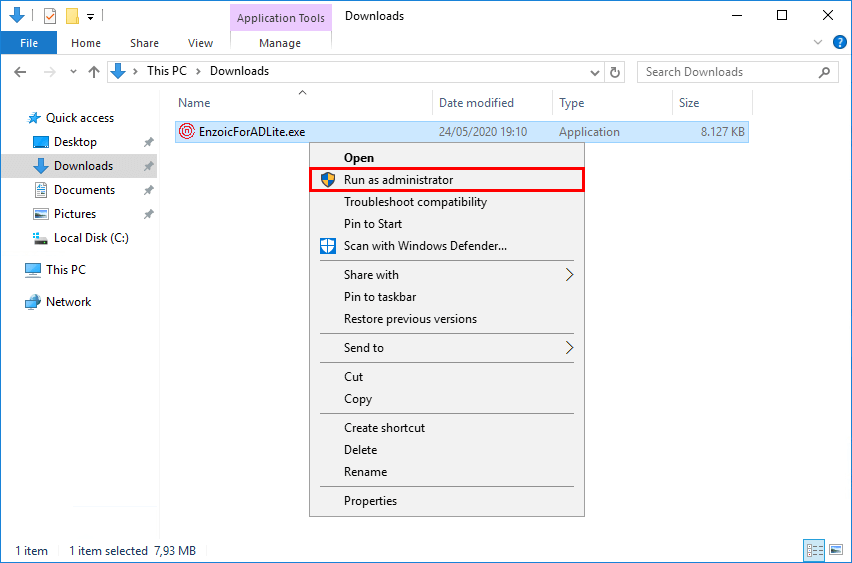
3. The welcome screen of Enzoic for Active Directory Lite shows up. Click Next.
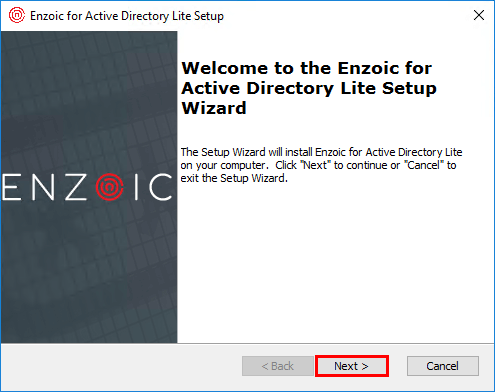
4. Check the I accept the term in the License Agreement and click Next.
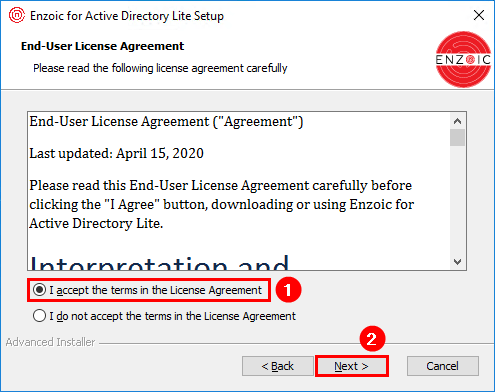
5. Keep the default installation folder and click Next.
6. Click Install to begin the installation.
7. Click Finish to close the setup wizard and launch Enzoic for Active Directory Lite.
A desktop shortcut is created on the desktop and in the start menu.
Didn’t we tell you that the setup is fast and easy to follow? In the next part, we will see the application in action.
Check Active Directory weak passwords
After we clicked Finish in the last part, the check for weak or compromised password window shows up. Click Check Now.
Enzoic for AD Lite will check for weak or compromised passwords in the Active Directory domain.
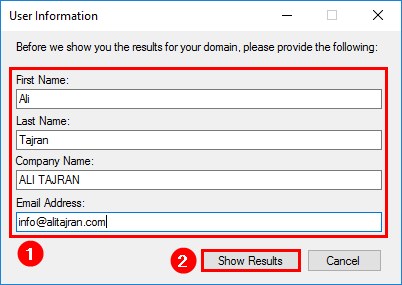
After it’s finished scanning, the user information window appears. Fill in your information, and click Show Results.
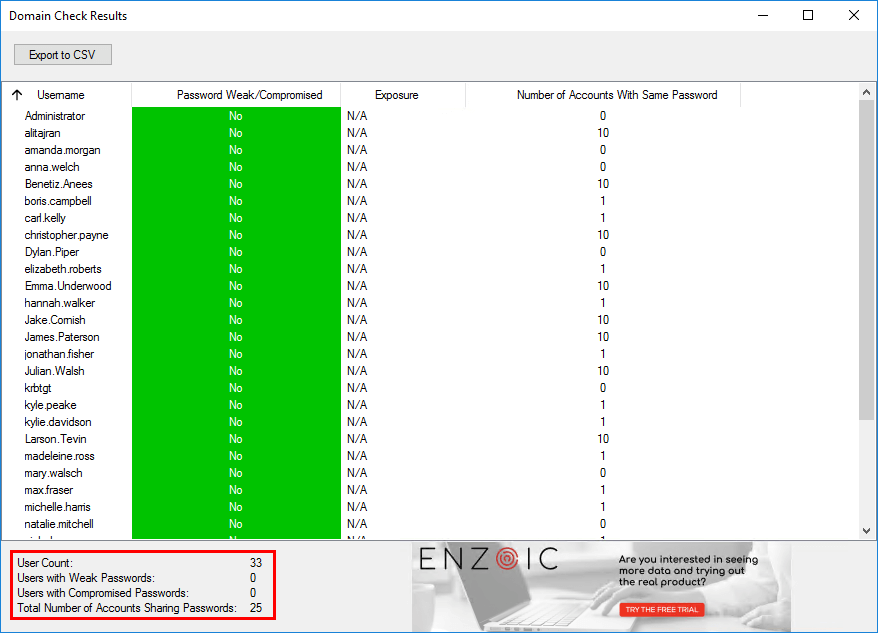
Active directory weak password checker results
After scanning the Active Directory with the database of Enzoic, the results show.
In our example, there are no weak or compromised passwords. However, there are user accounts that use the same passwords. That is not good to see. It’s good to inform the users to change their Active Directory password.
Close the Enzoic application. In the next step, we will check Active Directory weak passwords.
Active directory weak password checker test
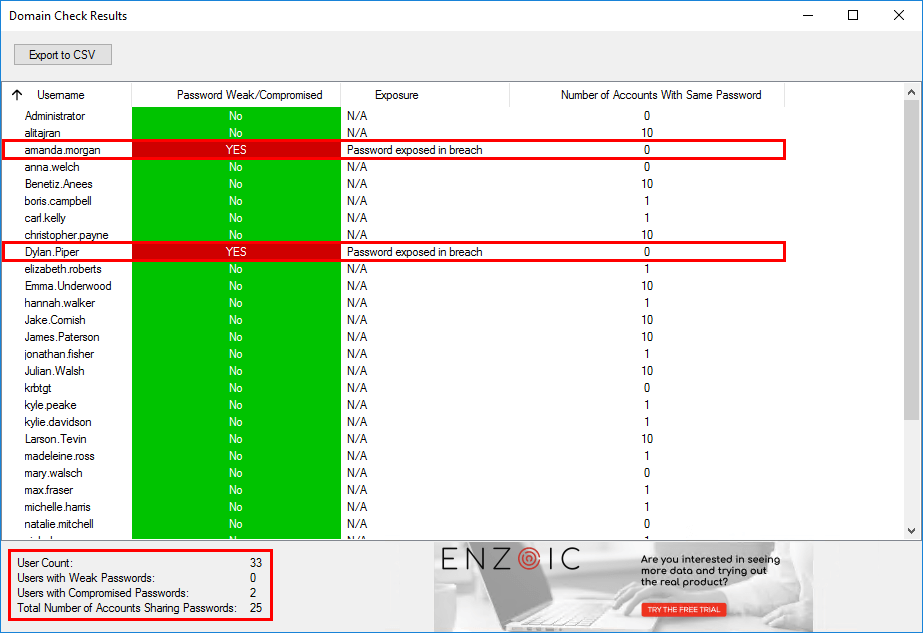
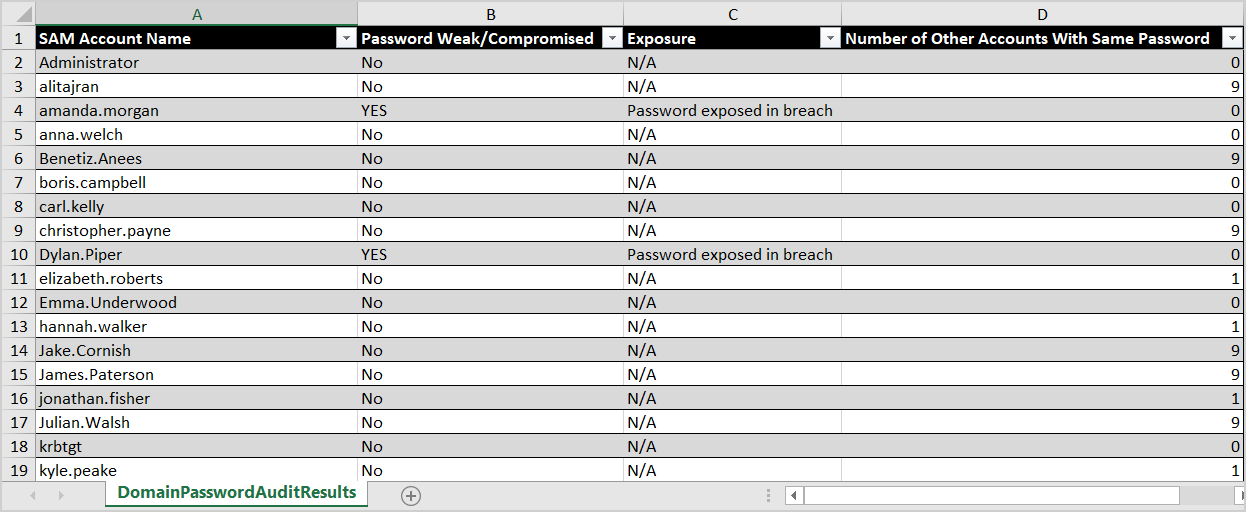
We want to test the Enzoic Active Directory password checker. That’s why we changed the password of two user accounts. The new password of Amanda Morgan is Ferrari02. The password of Dylan Piper is Welcome12.
Start Enzoic and check for weak or compromised passwords in the Active Directory domain.

The user information is already filled in. If not, fill it out again and click Show results.

After scanning the Active Directory with the database of Enzoic, the results show up.
This time, the password exposed in breach shows up for both users.
We can always export the results to CSV and open it with our favorite CSV viewer. For example, Microsoft Excel.
Use the tool to check Active Directory weak passwords. If you notice weak passwords or compromised passwords in Active Directory, change them immediately. After that, inform the users that the password is changed.
Read more: Secure Active Directory passwords from breaches »
Conclusion
We talked about Active Directory weak password checker. Install the Active Directory weak password finder on the domain controller or management server. Let it check the user account passwords and look at the results. If there are user accounts with weak passwords or compromised passwords, change them. Don’t forget to notify the user.
Did you enjoy this article? You may also like to read Bulk create AD Users with random passwords. Follow us on Twitter and LinkedIn to stay up to date with the latest articles.



I would better suggest DSInternals with Test-PasswordQuality.
https://github.com/MichaelGrafnetter/DSInternals/blob/master/Documentation/PowerShell/Test-PasswordQuality.md
Their report will be quite good.
Futhermore, you can extract all hashes and pass them to Hashcat to bruteforce by mask or any wordlist (there are 500GB+ in public for free)
I wrote about it in the article Secure Active Directory passwords from breaches.