How to download OneDrive template files (ADMX/ADML)? You want to ensure that all the OneDrive…
Check TLS settings on Windows Server with PowerShell script
There are no TLS settings configured on a new Windows Server install. Therefore, you must configure TLS on Windows Server with a GPO, manually with the registry editor, or with PowerShell. In this article, you will learn how to check TLS settings on Windows Server with PowerShell script.
Table of contents
Check TLS settings PowerShell script
The Get-TLS.ps1 PowerShell script will check the below TLS settings on Windows Server:
- TLS 1.2 for .NET 4.x
- TLS 1.2 for .NET 3.5
- TLS 1.3
- TLS 1.2
- TLS 1.1
- TLS 1.0
Note: TLS 1.3 is only supported in Windows Server 2022 and later.
The below values can appear in the PowerShell console after running the script:
- Not found: there are no values configured
- 1: Enabled
- 0: Disabled
Prepare Get TLS settings PowerShell script
Download Get-TLS.ps1 PowerShell script and place it in the C:\scripts folder. Create a scripts folder if you don’t have one.
Ensure the file is unblocked to prevent errors when running the script. Read more in the article Not digitally signed error when running PowerShell script.
Another option is to copy and paste the below code into Notepad. Give it the name Get-TLS.ps1 and place it in the C:\scripts\ folder.
Function Get-RegValue {
[CmdletBinding()]
Param
(
# Registry Path
[Parameter(Mandatory = $true,
Position = 0)]
[string]
$RegPath,
# Registry Name
[Parameter(Mandatory = $true,
Position = 1)]
[string]
$RegName
)
$regItem = Get-ItemProperty -Path $RegPath -Name $RegName -ErrorAction Ignore
$output = "" | select Path, Name, Value
$output.Path = $RegPath
$output.Name = $RegName
If ($regItem -eq $null) {
$output.Value = "Not Found"
}
Else {
$output.Value = $regItem.$RegName
}
$output
}
$regSettings = @()
$regKey = 'HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319'
$regSettings += Get-RegValue $regKey 'SystemDefaultTlsVersions'
$regSettings += Get-RegValue $regKey 'SchUseStrongCrypto'
$regKey = 'HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319'
$regSettings += Get-RegValue $regKey 'SystemDefaultTlsVersions'
$regSettings += Get-RegValue $regKey 'SchUseStrongCrypto'
$regKey = 'HKLM:\SOFTWARE\Microsoft\.NETFramework\v2.0.50727'
$regSettings += Get-RegValue $regKey 'SystemDefaultTlsVersions'
$regSettings += Get-RegValue $regKey 'SchUseStrongCrypto'
$regKey = 'HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v2.0.50727'
$regSettings += Get-RegValue $regKey 'SystemDefaultTlsVersions'
$regSettings += Get-RegValue $regKey 'SchUseStrongCrypto'
$regKey = 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.3\Server'
$regSettings += Get-RegValue $regKey 'Enabled'
$regSettings += Get-RegValue $regKey 'DisabledByDefault'
$regKey = 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.3\Client'
$regSettings += Get-RegValue $regKey 'Enabled'
$regSettings += Get-RegValue $regKey 'DisabledByDefault'
$regKey = 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server'
$regSettings += Get-RegValue $regKey 'Enabled'
$regSettings += Get-RegValue $regKey 'DisabledByDefault'
$regKey = 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client'
$regSettings += Get-RegValue $regKey 'Enabled'
$regSettings += Get-RegValue $regKey 'DisabledByDefault'
$regKey = 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server'
$regSettings += Get-RegValue $regKey 'Enabled'
$regSettings += Get-RegValue $regKey 'DisabledByDefault'
$regKey = 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client'
$regSettings += Get-RegValue $regKey 'Enabled'
$regSettings += Get-RegValue $regKey 'DisabledByDefault'
$regKey = 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server'
$regSettings += Get-RegValue $regKey 'Enabled'
$regSettings += Get-RegValue $regKey 'DisabledByDefault'
$regKey = 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client'
$regSettings += Get-RegValue $regKey 'Enabled'
$regSettings += Get-RegValue $regKey 'DisabledByDefault'
$regSettingsRun Check TLS settings PowerShell script
Change the path to the scripts folder. Next, run the PowerShell script to get the Windows Server TLS settings.
This is how it looks when you run Get-TLS.ps1 PowerShell script on a fresh Windows Server 2016/2019.
PS C:\scripts> .\Get-TLS.ps1
Path Name Value
---- ---- -----
HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319 SystemDefaultTlsVersions Not Found
HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319 SchUseStrongCrypto Not Found
HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319 SystemDefaultTlsVersions Not Found
HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319 SchUseStrongCrypto Not Found
HKLM:\SOFTWARE\Microsoft\.NETFramework\v2.0.50727 SystemDefaultTlsVersions Not Found
HKLM:\SOFTWARE\Microsoft\.NETFramework\v2.0.50727 SchUseStrongCrypto Not Found
HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v2.0.50727 SystemDefaultTlsVersions Not Found
HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v2.0.50727 SchUseStrongCrypto Not Found
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.3\Server Enabled Not Found
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.3\Server DisabledByDefault Not Found
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.3\Client Enabled Not Found
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.3\Client DisabledByDefault Not Found
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server Enabled Not Found
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server DisabledByDefault Not Found
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client Enabled Not Found
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client DisabledByDefault Not Found
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server Enabled Not Found
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server DisabledByDefault Not Found
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client Enabled Not Found
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client DisabledByDefault Not Found
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server Enabled Not Found
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server DisabledByDefault Not Found
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client Enabled Not Found
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client DisabledByDefault Not FoundThe below screen shows how it looks.
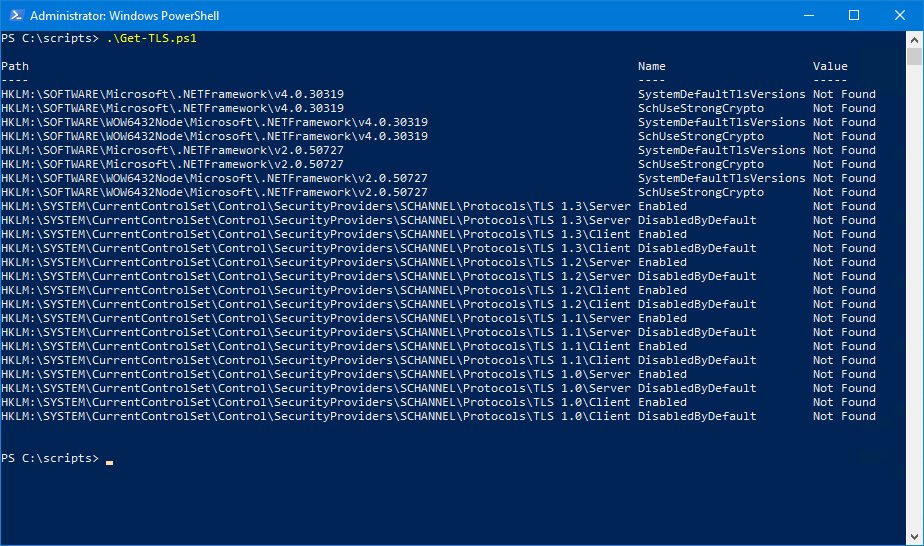
In our example, we only did configure the below TLS settings on Windows Server 2019:
- Enable TLS 1.2 for .NET 4.x
- Enable TLS 1.2 for .NET 3.5
- Disable TLS 1.3
- Enable TLS 1.2
- Disable TLS 1.1
- Disable TLS 1.0
This is how it looks after running the Get-TLS.ps1 PowerShell script.
PS C:\scripts> .\Get-TLS.ps1
Path Name Value
---- ---- -----
HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319 SystemDefaultTlsVersions 1
HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319 SchUseStrongCrypto 1
HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319 SystemDefaultTlsVersions 1
HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319 SchUseStrongCrypto 1
HKLM:\SOFTWARE\Microsoft\.NETFramework\v2.0.50727 SystemDefaultTlsVersions 1
HKLM:\SOFTWARE\Microsoft\.NETFramework\v2.0.50727 SchUseStrongCrypto 1
HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v2.0.50727 SystemDefaultTlsVersions 1
HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v2.0.50727 SchUseStrongCrypto 1
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.3\Server Enabled 0
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.3\Server DisabledByDefault 1
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.3\Client Enabled 0
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.3\Client DisabledByDefault 1
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server Enabled 1
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server DisabledByDefault 0
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client Enabled 1
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client DisabledByDefault 0
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server Enabled 0
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server DisabledByDefault 1
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client Enabled 0
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client DisabledByDefault 1
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server Enabled 0
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server DisabledByDefault 1
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client Enabled 0
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client DisabledByDefault 1The below screen shows how it looks.
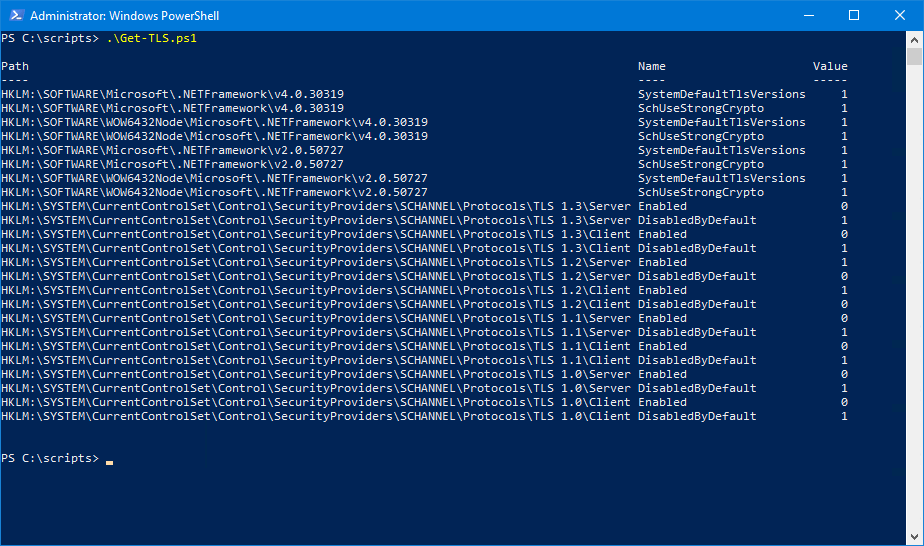
Did this help you to check TLS settings on Windows Server with PowerShell?
Read more: Configure Exchange Server TLS settings »
Conclusion
You learned how to check TLS settings on Windows Server with PowerShell. Run the Get-TLS.ps1 PowerShell script to get the TLS settings on Windows Server. It’s much faster to get the TLS settings and easier to read with PowerShell than checking the TLS values through the Registry Editor.
Did you enjoy this article? You may also like Export disabled users from Active Directory. Don’t forget to follow us and share this article.



You save my days.
Thanks a lot
Hi Ali,
Thanks for the script. We need to run this script against all the Windows servers in our environment. Also, we need it to check to KeyExchangeAlgorithm about it being Enabled or not. If enabled, what is the ServerMinKeyBitLength? Your response would be appreciated.
Hi ALI TAJRAN,
Great Script.
Can you help me to use this script for remote computers? Where to pass the computer names ? Please assist.