How to Allowlist a domain in Microsoft 365 and bypass the spam filtering service? An…
Configure Download Domains to address CVE-2021-1730 vulnerability
Your Exchange Server 2016/2019 is up to date with the latest Exchange Cumulative Update and Security Update. But when you check the Exchange Server health, it shows a security vulnerability is detected: Download Domains are not configured. This article will show how to configure Download Domains to address the CVE-2021-1730 vulnerability.
Table of contents
Vulnerability CVE-2021-1730
A spoofing vulnerability exists in Microsoft Exchange Server, which could result in an attack allowing a malicious actor to impersonate the user. To prevent these types of attacks, Microsoft recommends downloading inline images from different DNSdomains than the rest of OWA.
Important: Keep the Exchange Servers up to date with the latest Cumulative Update / Security Update. That’s also the case when you have an Exchange Hybrid Server for management purposes.
Check CVE-2021-1730 vulnerability status
Download and run the Exchange Server Health Checker script to detect if the Exchange Server is up to date and if the CVE-2021-1730 vulnerability exists or is already manually configured.
Generate an Exchange health report for all Exchange Servers. Run Exchange Management Shell and change the path to the C:\scripts folder.
[PS] C:\>cd C:\scripts
[PS] C:\scripts>Get-ExchangeServer | ?{$_.AdminDisplayVersion -Match "^Version 15"} | .\HealthChecker.ps1; .\HealthChecker.ps1 -BuildHtmlServersReport -HtmlReportFile "ExchangeAllServersReport.html"; .\ExchangeAllServersReport.htmlThis is what the Exchange health report looks like. It shows that a vulnerability is detected.
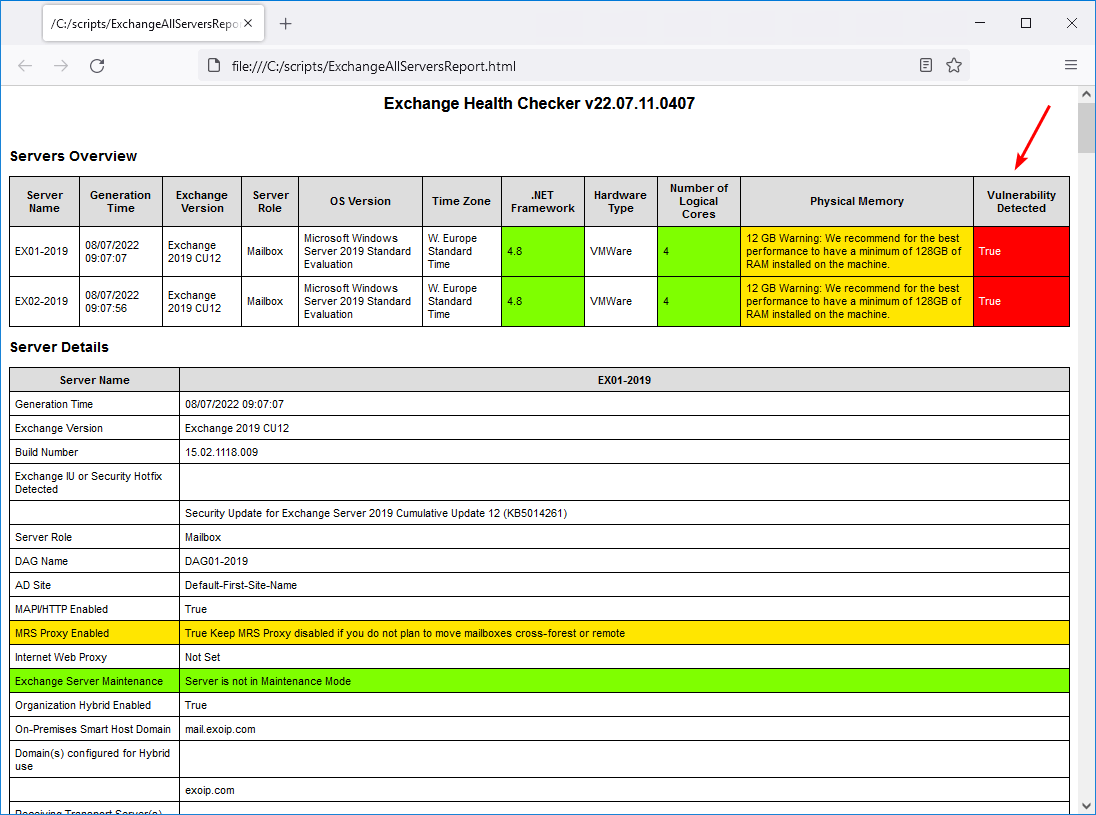
Go through the Exchange health report until you see the Security Vulnerabilities section.
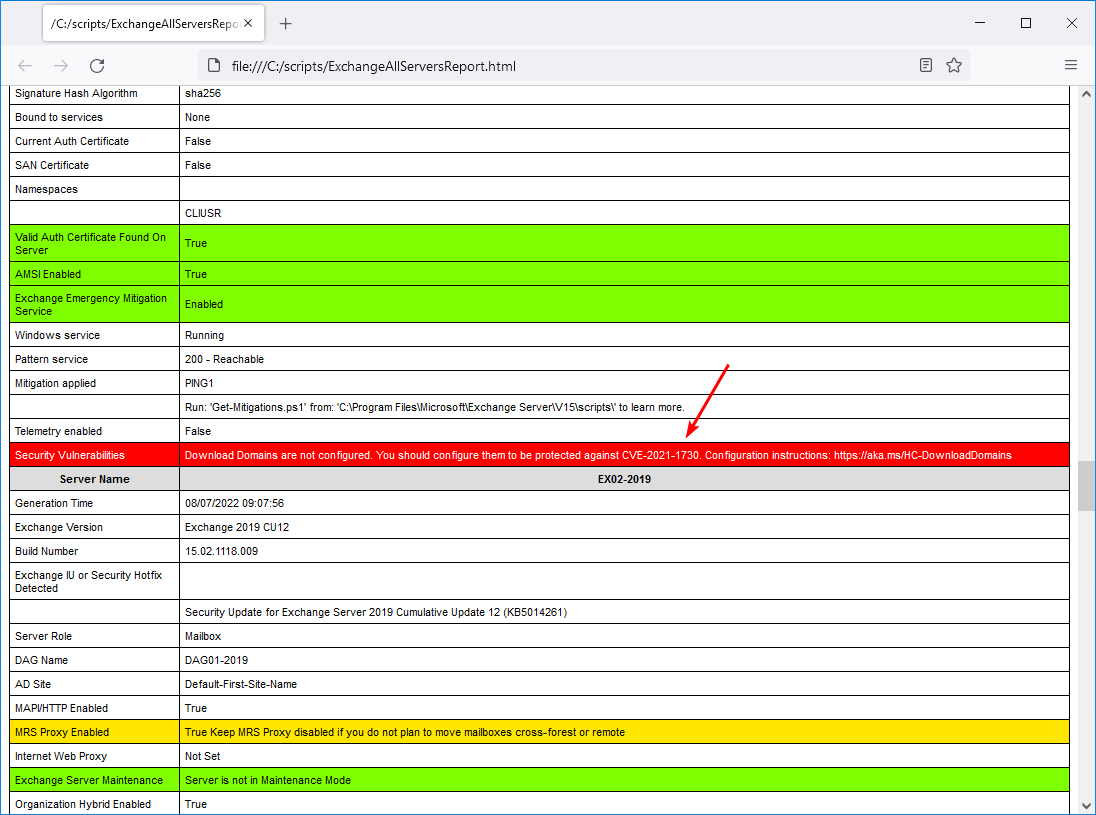
The CVE-2021-1730 vulnerability is detected.
Security Vulnerabilities: Download Domains are not configured. You should configure them to be protected against CVE-2021-1730. Configuration instructions: https://aka.ms/HC-DownloadDomains
If the vulnerability is not present, you’re all set, and you can double-check and confirm that the Download Domain feature is enabled (see below).
Configure Download Domains
Configuring the Download Domains only applies and effect inline images in Outlook Web Access (OWA). So nothing will happen to the inline images in Outlook desktop or mobile application. Let’s say you configure it incorrectly, the inline images will not show up in OWA, but all inline images will work in all the other places.
What if you have all the mailboxes in Exchange Online or the organization does not use OWA? Then, we still recommend configuring Download Domains. That’s because you do not want any vulnerabilities in an organization.
To configure Download Domains go through the below steps:
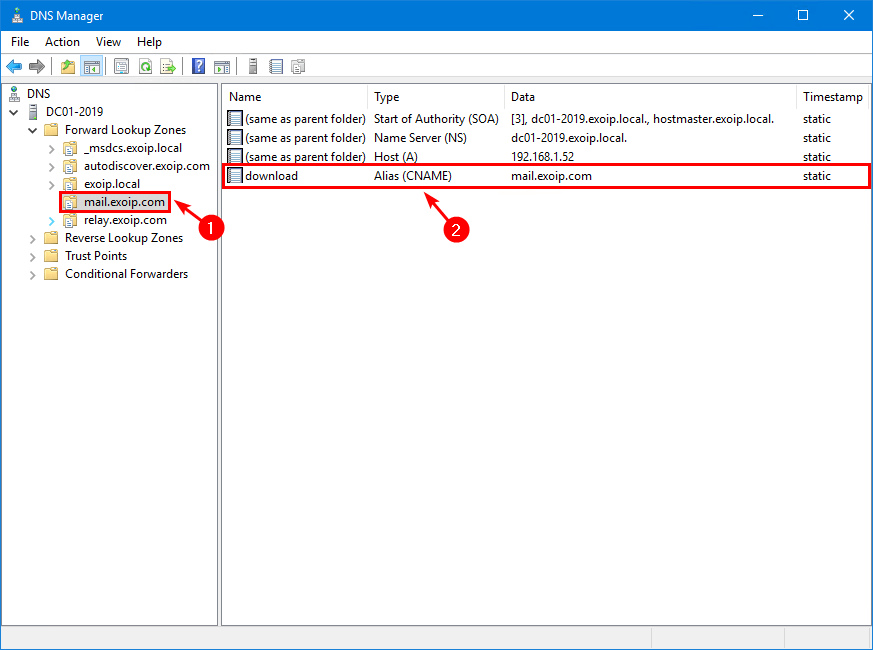
Step 1. Add download domain to internal DNS
Add a new domain name with the name download that points to the primary domain name in the internal DNS.
| Name | Type | Value |
|---|---|---|
| download | Alias (CNAME) | mail.exoip.com |
This is what it looks like.
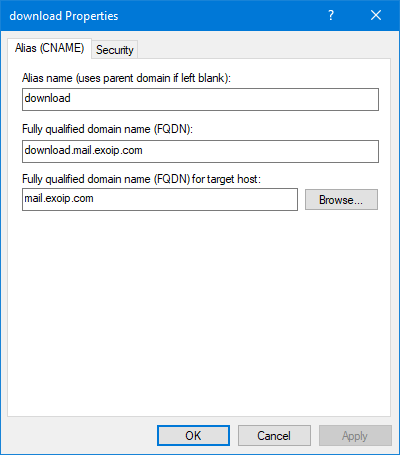
Double-click the download CNAME record to check the properties.
Step 2. Add download domain to external DNS
Add a new domain name with the name download.mail that points to the primary domain name in the external DNS.
| Name | TTL | Type | Value |
|---|---|---|---|
| download.mail | 5 min. | CNAME | mail.exoip.com. |
This is what it looks like.
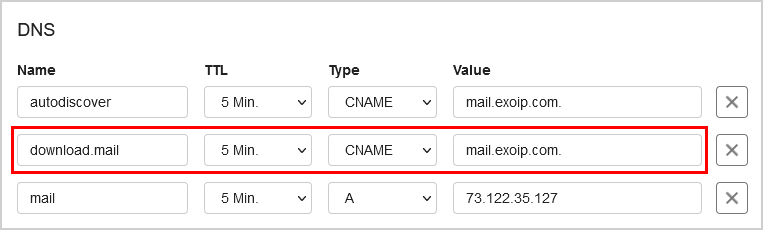
Step 3. Add download domain to certificate
Add the download domain to your existing SSL certificate (SAN).
This is how the third-party certificate looks in our example.
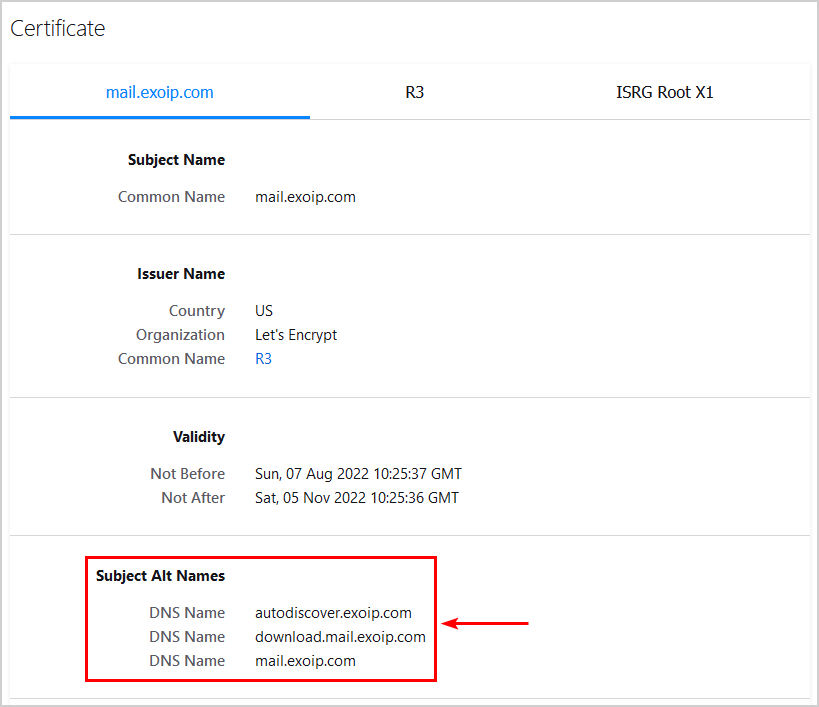
If we don’t adjust the certificate, it will break the inline images in Outlook Web Access (OWA) because the domain name download.mail.exoip.com is not on the list.
Suppose you have a multi-domain wildcard certificate, you don’t have to do anything, and you’re all set. That’s because a multi-domain wildcard certificate will secure multi-level subdomains.
Note: If you have a wildcard certificate, it will not work, and you must create a multi-domain wildcard certificate or create a SAN certificate, including the subdomain.
Step 4. Add download domain to OWA virtual directory
Add the download domain to the OWA virtual directory using the following two cmdlets on the Exchange Server.
Note: Run the commands on all the Exchange Servers OWA virtual directory.
Internal download hostname:
[PS] C:\>Set-OwaVirtualDirectory -Identity "EX01-2019\owa (Default Web site)" -InternalDownloadHostName "download.mail.exoip.com"External download hostname:
[PS] C:\>Set-OwaVirtualDirectory -Identity "EX01-2019\owa (Default Web site)" -ExternalDownloadHostName "download.mail.exoip.com"Verify that the internal and external download host names are set.
[PS] C:\>Get-OwaVirtualDirectory | ft Identity,*DownloadHostName
Identity ExternalDownloadHostName InternalDownloadHostName
-------- ------------------------ ------------------------
EX01-2019\owa (Default Web Site) download.mail.exoip.com download.mail.exoip.com
EX02-2019\owa (Default Web Site) download.mail.exoip.com download.mail.exoip.comStep 5. Enable Download Domains
Set the EnableDownloadDomains flag to true.
[PS] C:\>Set-OrganizationConfig -EnableDownloadDomains $trueStep 6. Restart Internet Information Services (IIS)
Restart the Internet Information Services (IIS).
[PS] C:\>iisresetConfirm Download Domains enabled
You should always confirm that the Download Domain is enabled successfully by following the below steps:
1. Send an email with an inline image from a user to another user in the organization.
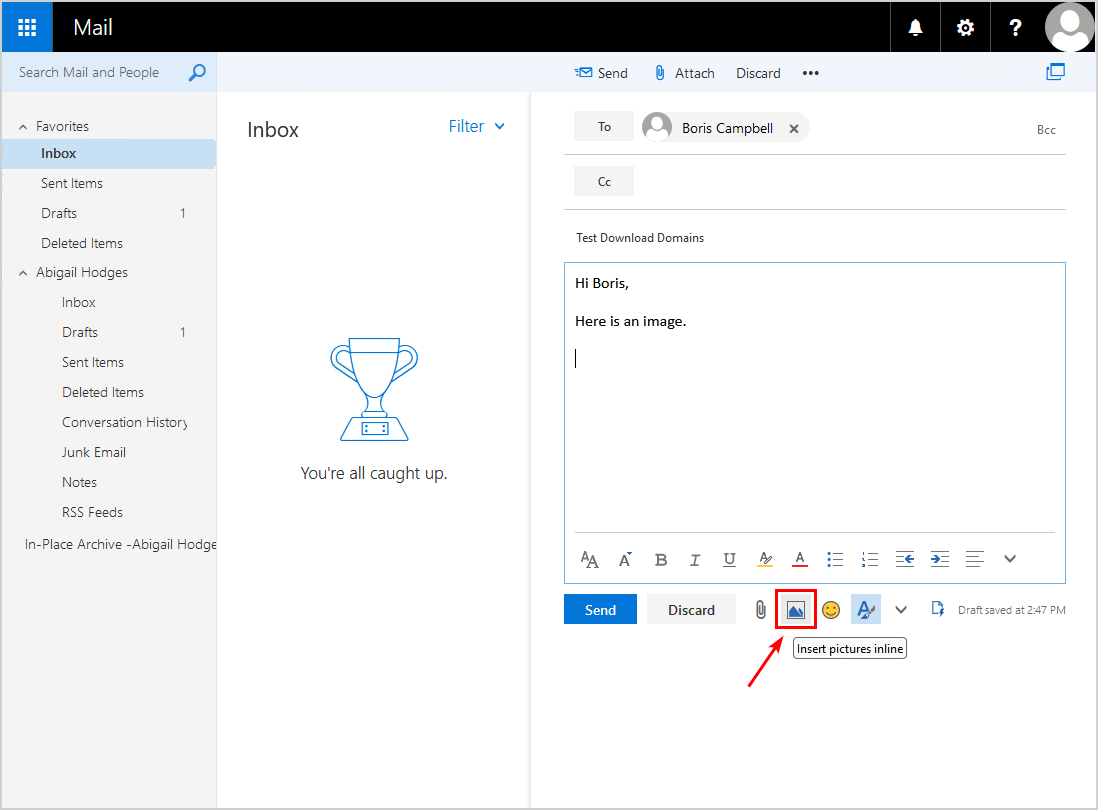
2. Login into OWA and open the email with the inline image. The image should load and be displayed in the reading pane.
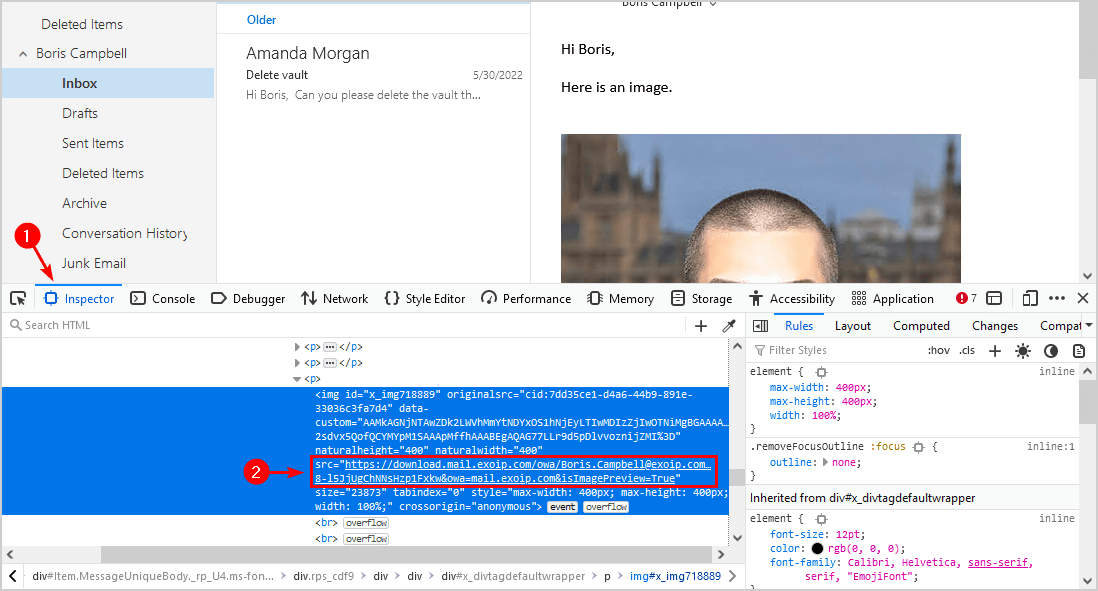
3. Right-click the page and select Inspect to open the inspector tool.
4. Ensure that the Inspector tab is selected and select the image. Verify that the download domain URL appears.
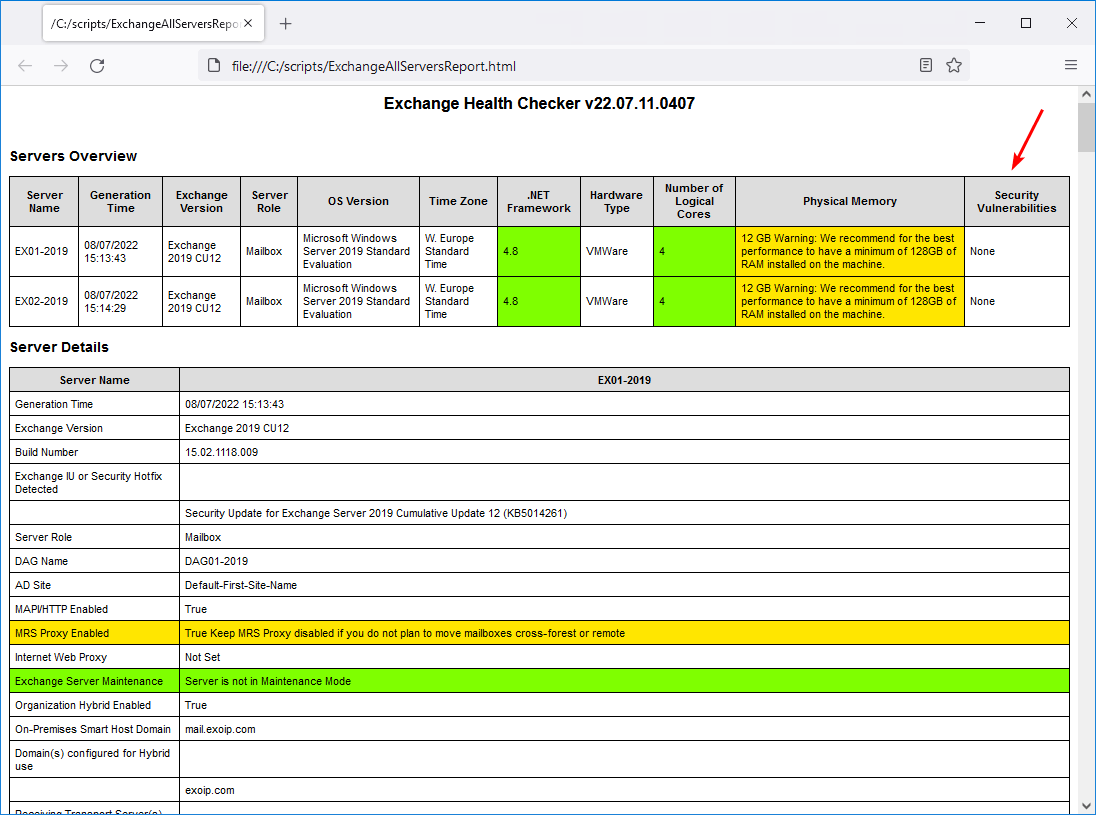
5. Run the Exchange Health Checker script and check the health report.
The Exchange health report shows that there are no security vulnerabilities detected.
That’s it! Did this help you to address the CVE-2021-1730 vulnerability?
Read more: Change DAG witness server and witness directory »
Conclusion
We showed how to configure Download Domains to address CVE-2021-1730 vulnerability. This vulnerability is not automatically addressed when you install Exchange Cumulative Update or Security Update. You must manually configure Download Domains in Exchange Server.
Did you enjoy this article? You may also like Exchange database dismounts unexpectedly. Don’t forget to follow us and share this article.



I have set up download domain for our Exchange Server 2019, but after applying CU14 it returns http error 500. Disabling download domain feature in Set-OrganizationConfig fixes it immediately, without restarting IIS service
Thanks. We had the same problem after CU14.
How do you even add a domain name to a publicly assigned SSL cert? We use a *.domain.com wildcard cert.
Hi,
I have a wildcard certificate like *.exoip.com, my question is can I us download.exoip.com instead of download.mail.exoip.com ?
Thanks,
Fatma
Yes, you can do that.
Hi Ali,
Great articles and information.
In Exchange Hybrid scenarios, where all Mailboxes are in O365, it would only be necessary to enable it with the “Set-OrganizationConfig -EnableDownloadDomains $true” command, without any custom changes at the DNS and IIS record level.
Hi,
Our Exchange has same vulnerability.
We have 3 domain and 8 subdomain.We have UCC/SAN certification.
Can we use your solution for that ?
Shoud we create download.xxx.xxx for 3 domain in certiication ?
thanks.
I was looking at this and created a test environment. Is it 100% necesary to be download.mail.exoip.com why not dl.exoip.com? I tested like that and it worked for me but wanted to know if there where any downsides to using it like that.
By the way, thanks for the information here. It’s been really helpful!
You can configure it like you did, and it has no downside.
Thanks Ali – what is the best way to add a subdomain to an already existing and working Let’s Encrypt certificate?
I updated the article Install FREE Let’s Encrypt certificate in Exchange Server and added the “download” subdomain.
Hi,
It’s a great article. But i think that if you have an wildcard cert like *.exoip.com then an record like download.mail.exoip.com will not work.
I like You work very much.
Thanks.
That’s correct.
I updated the article, which says you need to create a multi-domain wildcard certificate or create a SAN certificate, including the subdomain.
Great articles and blogs on Exchange servers.
I must say, I have accomplished a lot by following your well-organized tips on the exchange server’s setup and configuration.
Keep it up for the good job.
God Bless.
Daniel
Great article. Yours is much better then Microsoft’s as you actually explain what to do with the SSL certificate which now I know is to add it to my SAN or use a multi-domain wildcard.
Thanks Ali