The user has a primary mailbox and an archive mailbox. You only want to move…
Update AD schema to address CVE-2021-34470 vulnerability
Did you run Exchange Server in the past, but you have since uninstalled all Exchange Servers in the organization? Do you run an Exchange Server older than Exchange Server 2013 in the organization? This article is essential for you, and you have to update your AD schema to address the CVE-2021-34470 vulnerability.
Table of contents
Vulnerability CVE-2021-34470
Without explicit action by a schema admin in your organization, you might be vulnerable to CVE-2021-34470 if:
- You ran Exchange Server in the past, but you have since uninstalled all Exchange servers.
- You run Exchange Server older than Exchange 2013 (Exchange 2003, Exchange 2007, or Exchange 2010).
If your organization is in one of these scenarios, we recommend updating your Active Directory schema to address the vulnerability in CVE-2021-34470. More on that below.
When you have Exchange Server running in the organization, you already addressed the CVE-2021-34470 vulnerability. That’s because the fix comes with the July 2021 Exchange Server Security Updates.
Important: Keep the Exchange Servers up to date with the latest Cumulative Update / Security Update. That’s also the case when you have an Exchange Hybrid Server for management purposes.
Schema extensions will stay
Even if your organization has uninstalled all your Exchange servers, the schema extensions made by Exchange to your Active Directory are not removed. If you ran Exchange Server in the past, your Active Directory schema was extended as a part of Exchange Server installation, and any Exchange schema extensions are still present in your organization (unless you completely rebuilt your Active Directory forest). Therefore, you might be vulnerable to CVE-2021-34470, and you should use the script to address this vulnerability.
Note: Exchange Server integrates with the Active Directory schema. If you remove Exchange Server, the Exchange schema extensions will remain part of your schema forever.
The script makes only the change needed to address CVE-2021-34470, and no other schema changes are made. You can run the script in Test mode to see if your Active Directory schema is vulnerable to CVE-2021-34470. The script will also provide validation that CVE-2021-34470 is addressed if you have already updated your schema.
Download Test-CVE-2021-34470 PowerShell script
Download the Test-CVE-2021-34470.ps1 PowerShell script from the official Microsoft GitHub page.
Place the script in the C:\scripts folder on your Domain Controller or Management Server. If you don’t have a scripts folder, create one. Make sure to check if the file is unblocked to prevent any errors when running the script. Read more in the article Not digitally signed error when running PowerShell script.
Check CVE-2021-34470 vulnerability
Run PowerShell as administrator. Change the directory to C:\scripts and run the script to check for the CVE-2021-34470 vulnerability.
PS C:\> cd C:\scripts
PS C:\scripts> .\Test-CVE-2021-34470.ps1You will see one of the following messages in the output:
- WARNING: CVE-2021-34470 vulnerability is present
- CVE-2021-34470 vulnerability is not present
If the vulnerability is not present, you’re set and done. However, if you see the warning that CVE-2021-34470 vulnerability is present, proceed to the next step and apply the fix.
Apply CVE-2021-34470 vulnerability fix
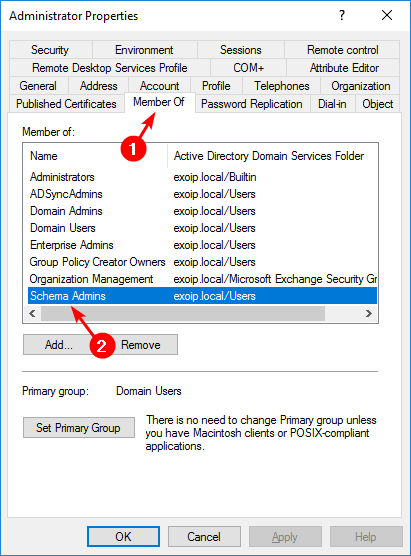
Before you can use the -ApplyFix switch, the user account needs to be added to the Schema Admins group.
Note: If you’ve just added yourself to the Schema Admins group, you’ll need to log out and back into the Server for the new group membership to take effect.
Run the script, but this time with the -ApplyFix switch.
PS C:\scripts> .\Test-CVE-2021-34470.ps1 -ApplyFixThe output will look as follow when the fix is applied successfully.
PS C:\scripts> .\Test-CVE-2021-34470.ps1 -ApplyFix
WARNING: CVE-2021-34470 vulnerability is present.
Attempting to apply fix...
Fix was applied successfully.That’s it! Did this help you to address the CVE-2021-34470 vulnerability?
Read more: Check Exchange Schema version with PowerShell »
Conclusion
We showed how to update AD schema to address CVE-2021-34470 vulnerability. If you had an Exchange Server running in the past, you have to download the Test-CVE-2021-34470.ps1 PowerShell script and apply the fix. When you have Exchange Server running in the organization, you already addressed the vulnerability because you did apply the latest Cumulative Update and Security Update.
Did you enjoy this article? You may also like Microsoft Exchange Server vulnerability check. Don’t forget to follow us and share this article.



You’re great Ali! I really love your website. It’s fantastic and so easy to follow. Please do never stop.