You have a DAG setup, and the mailbox database disk is getting full. However, when…
Exchange firewall ports for mail flow and clients
Are you following the course Exchange Server? If you are, you know that we first have to configure Exchange firewall ports for mail flow and clients. After that, we can start testing sending and receiving emails. In this article, you will learn about Exchange firewall ports requirements. Let’s get into the Exchange firewall configuration.
Table of contents
Configure Exchange firewall ports
It’s important to open the following three firewall ports for mail flow and clients. It will enable the Exchange server to communicate with other mail servers outside your organization.
| Purpose | Ports | Source | Destination |
|---|---|---|---|
| Encrypted web connections | 443/TCP (HTTPS) | Internet (any) | 192.168.1.52 |
| Inbound mail | 25/TCP (SMTP) | Internet (any) | 192.168.1.52 |
| Outbound mail | 25/TCP (SMTP) | 192.168.1.52 | Internet (any) |
In our example, the Exchange Server IP address is 192.168.1.52.
An architecture view of the Exchange namespace is shown below in the diagram.
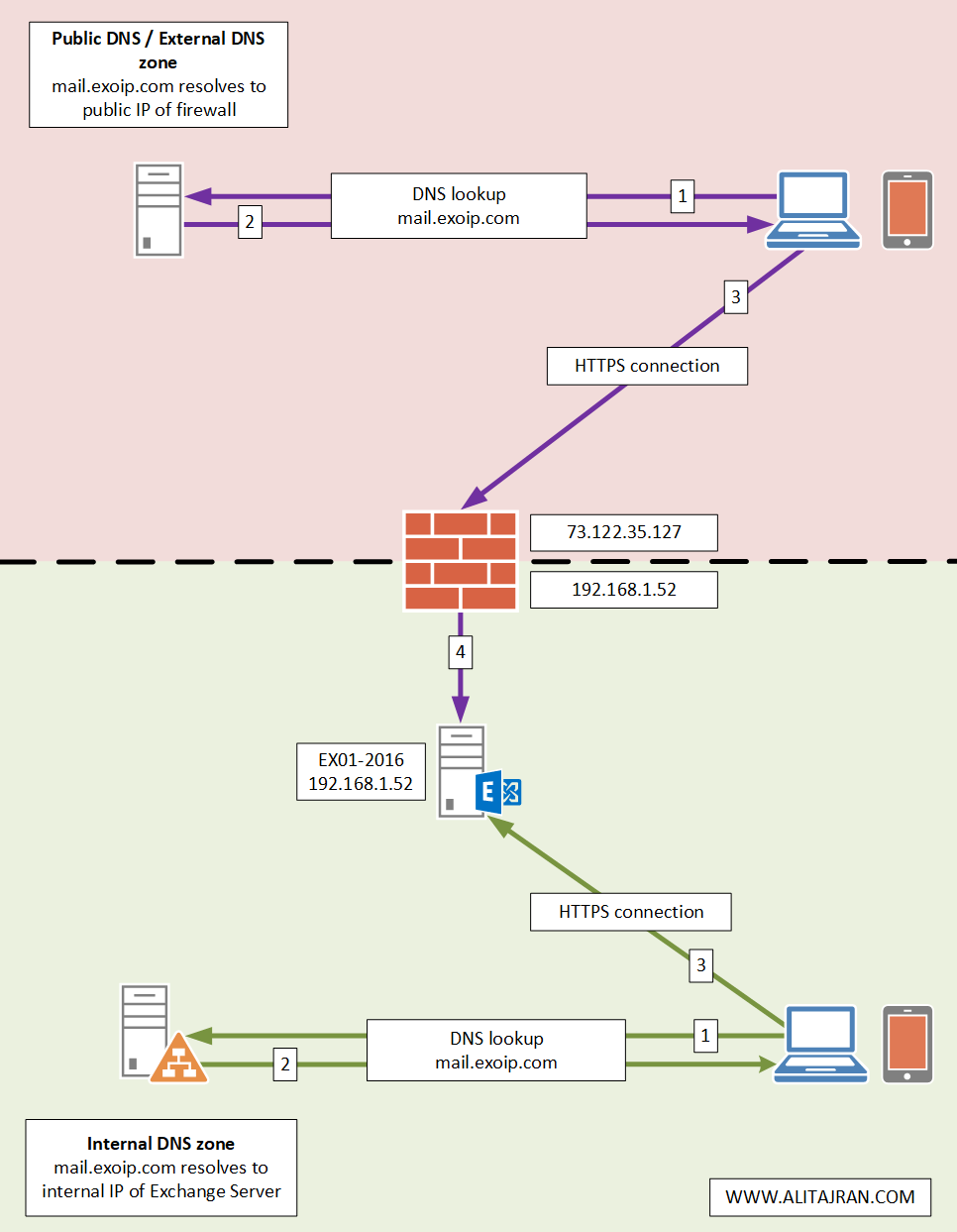
Test firewall ports
Verify the above three firewall rules after configuring them. If you followed the article configure external DNS for Exchange, you already have the public IP of your Exchange Server.
Do you want to get the public IP with PowerShell? Sign in to Exchange Server. After that, run PowerShell as administrator and run the below command.
PS C:\> (Invoke-WebRequest -Uri "http://ifconfig.me/ip").Content
73.122.35.127Test both ports 443 and 25 against the public IP; this is for incoming connections. Test port 25 against the Exchange Server; this is for outgoing connections.
If it shows the TCP Test Succeeded value as True, you’re good to go. If not, check the firewall ports. Make use of the Test-NetConnection cmdlet.
PS C:\> Test-NetConnection 73.122.35.127 -Port 443
ComputerName : 73.122.35.127
RemoteAddress : 73.122.35.127
RemotePort : 443
InterfaceAlias : LAN
SourceAddress : 192.168.1.52
TcpTestSucceeded : True
PS C:\> Test-NetConnection 73.122.35.127 -Port 25
ComputerName : 73.122.35.127
RemoteAddress : 73.122.35.127
RemotePort : 25
InterfaceAlias : LAN
SourceAddress : 192.168.1.52
TcpTestSucceeded : True
PS C:\> Test-NetConnection 192.168.1.52 -Port 25
ComputerName : 192.168.1.52
RemoteAddress : 192.168.1.52
RemotePort : 25
InterfaceAlias : LAN
SourceAddress : 192.168.1.52
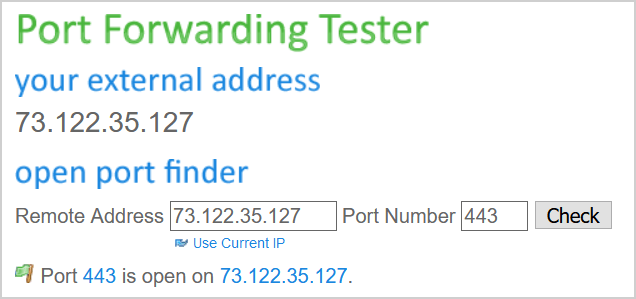
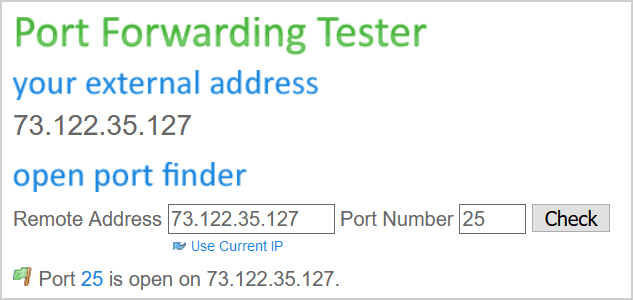
TcpTestSucceeded : TrueYou can check if port 443 and port 25 are open against the public IP with open port check tool. Fill in the public IP and the port numbers. It will scan if the ports are open.
Port 443 is open on public IP.
Port 25 is open on Public IP.
Do you like to know more about the Exchange firewall requirements? Read more in the next parts.
Exchange firewall ports for clients and services
To get clients working with Exchange, it’s very important to open port 443 on the firewall. This is only for inbound. Have a look at the image below. The arrows are only going from the Internet -> On-premises Exchange 2016 environment.
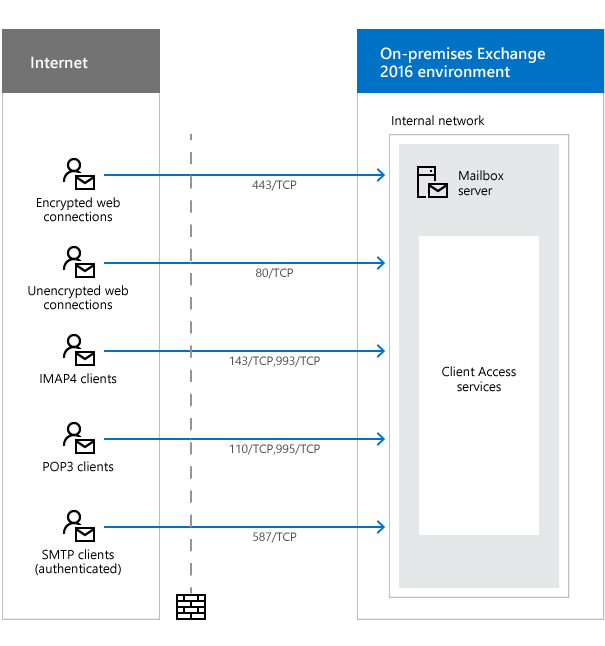
| Purpose | Ports | Source | Destination |
|---|---|---|---|
| Encrypted web connections are used by the following clients and services: • Autodiscover service • Exchange ActiveSync • Exchange Web Services (EWS) • Offline address book (OAB) distribution • Outlook Anywhere (RPC over HTTP) • Outlook MAPI over HTTP • Outlook on the web (formerly known as Outlook Web App) | 443/TCP (HTTPS) | Internet (any) | Mailbox server |
| Unencrypted web connections are used by the following clients and services: • Internet calendar publishing • Outlook on the web (redirect to 443/TCP) • Autodiscover (fallback when 443/TCP isn’t available) | 80/TCP (HTTP) | Internet (any) | Mailbox server |
| IMAP4 clients* | 143/TCP (IMAP), 993/TCP (secure IMAP) | Internet (any) | Mailbox server |
| POP3 clients** | 110/TCP (POP3), 995/TCP (secure POP3) | Internet (any) | Mailbox server |
| SMTP clients (authenticated) | 587/TCP (authenticated SMTP) | Internet (any) | Mailbox server |
*IMAP4 is disabled by default.
**POP3 is disabled by default.
Exchange firewall ports for mail flow
To get mail flow working with Exchange, it’s very important to open port 25 on the firewall. This is for both inbound and outbound. Have a look at the image below. The arrows are going from the Internet <-> On-premises Exchange 2016 environment.
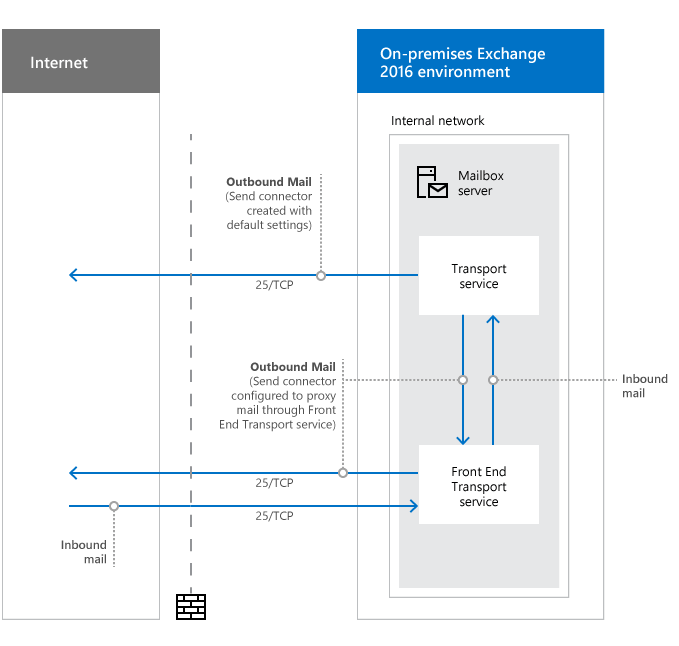
| Purpose | Ports | Source | Destination |
|---|---|---|---|
| Inbound mail | 25/TCP (SMTP) | Internet (any) | Mailbox server |
| Outbound mail | 25/TCP (SMTP) | Mailbox server | Internet (any) |
| Outbound mail (if proxied through the Front End transport service) | 25/TCP (SMTP) | Mailbox server | Internet (any) |
Conclusion
You learned how to configure Exchange firewall ports for mail flow and clients. First, enable the ports on the firewall. After that, test if the ports are open. The Exchange firewall configuration is important. Otherwise, you can’t send and receive emails.
Did you enjoy this article? You may also like Create bulk mailboxes in Exchange Server with PowerShell. Don’t forget to follow us and share this article.

Ali, Thank you for sharing your knowledge and great work. I have a question I have not been able to find a clear answer on… The Default Frontend connector, by default, has all IP 4 and 6 ranges listed as accepted ranges. To the best of my understanding, any internal IP can send mail anonymously via this connector. In the case of port 25 being NATTed to Exch through the firewall, does it make sense to restrict the Default Frontend connector to only the internal IP of the firewall? And then build custom connectors for internal devices. Or does Exchange need to be ‘fed’ the actual external IP of the incoming message to properly do its thing? I know we can’t remove Anonymous since that will break receiving mail from external. But it seems like a (relatively minor) security risk to be allowing remote connections from all internal IPs. I did see other methods for restricting this by removing permissions from the receive connector, but I’m wondering if restricting the connector to the internal IP of the firewall will accomplish the same thing. I hope I asked that question clearly. Thanks again for what you do!!
Hello Ali
Your Article is the BEST, your diagram conveys THOUSANDS of Words, Clear Understanding without the need of reading it.
Thank you
Hi Ali ,
the Security department asked me to change smtp port from 25 to 587.
I have 2 question about that :
1- This change occurs on the input and output edges of the edge server or MailBox server or both؟
2- If I completely disable port 25, I won’t have any problems to receive and send emails from outside the organization ?
Hello Ali, I make use of your essays a lot. Thanks indeed. I have question which confuses me whose answer I have not been able find so far. Everyone I ask tells different things.
Does an Outlook client of Exchange Server who connects with MAPI or RPC use the port numbers of 25 or 587 to send e-mail or is it enough for the client Outlook client to connect through 443 to the Exchange Server to send an e-mail? Some people say that Outlook does not use any port numbers and some people say it is enough for the client Outlook client to connect through 443 to the Exchange Server to send an e-mail.
I need your answer. Thanks a lot for now.
Could it be possible for you to respond to the question I asked in this comment?
Hi Ali do you have an article for exchange hybrid and o365 port and f/w requirements?
Thanks you!
Here you go: Exchange Hybrid firewall ports.