You should always disable external access to Exchange Control Panel (ECP). You don't want a…
Configure Exchange Server TLS settings
We recommend enabling TLS 1.2 on Exchange Server 2013/2016/2019 and disabling TLS 1.0, TLS 1.1, and TLS 1.3. Even though TLS 1.3 is newer, you should disable it. That’s because TLS 1.3 is not supported for Exchange Server and causes issues when enabled. In this article, you will learn how to configure Exchange Server TLS settings.
Table of contents
Exchange Server version
Ensure that you have the following Exchange Server version running:
- Exchange Server 2013 CU20 and later
- Exchange Server 2016 CU9 and later
- Exchange Server 2019
Important: Keep the Exchange Servers up to date with the latest Cumulative Update / Security Update. That’s also the case when you have an Exchange Hybrid Server for management purposes.
Check Exchange Server TLS settings
Download Exchange Server Health Checker PowerShell script.
Run Exchange Management Shell as administrator. Next, change the path to C:\scripts and run the command to generate an Exchange health report for all Exchange Servers.
[PS] C:\>cd C:\scripts
[PS] C:\scripts>Get-ExchangeServer | ?{$_.AdminDisplayVersion -Match "^Version 15"} | .\HealthChecker.ps1; .\HealthChecker.ps1 -BuildHtmlServersReport -HtmlReportFile "ExchangeAllServersReport.html"; .\ExchangeAllServersReport.htmlGo to the TLS section in the report and check if there are errors.
This is how it looks in our example.
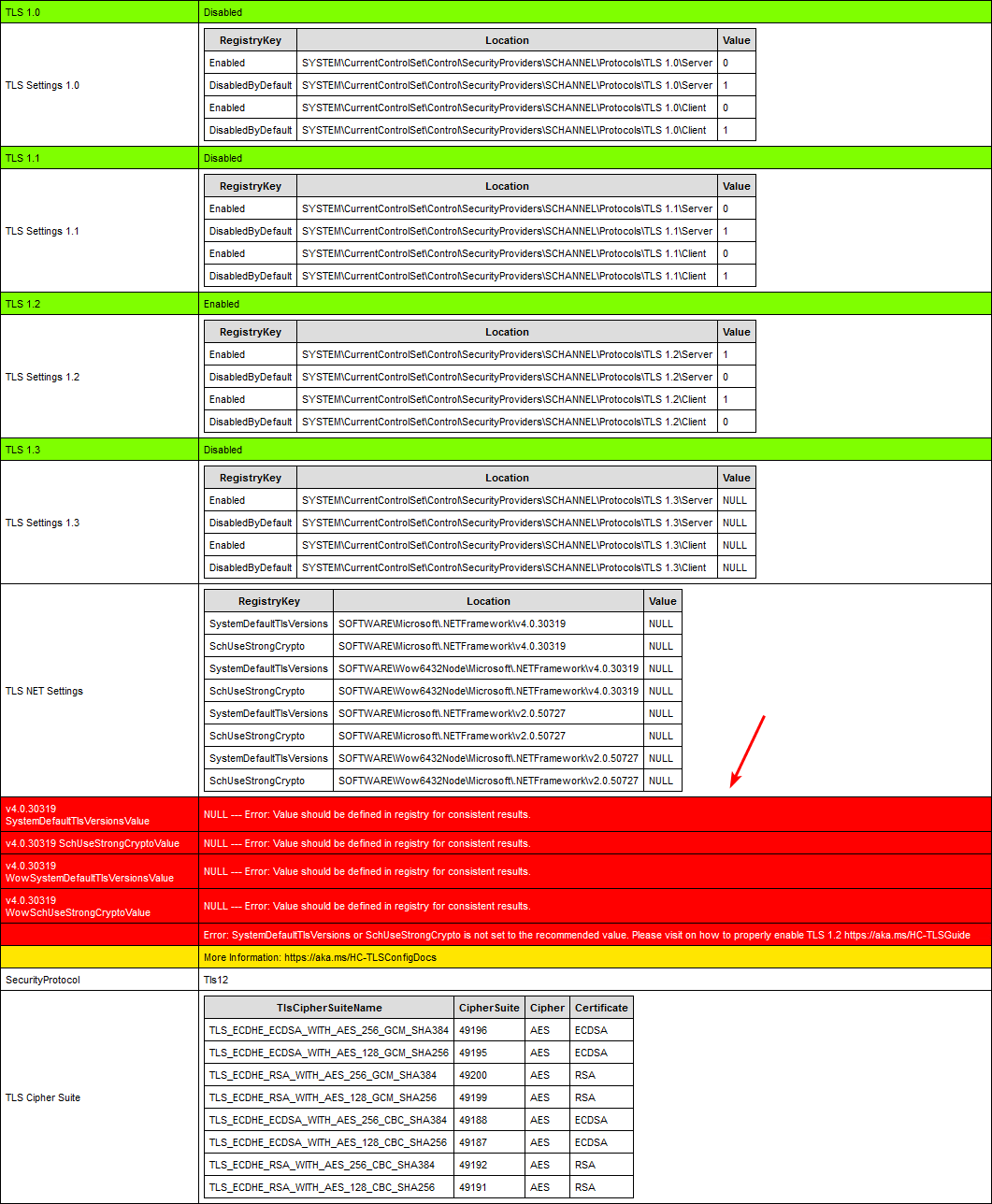
Exchange Server TLS settings PowerShell script
Because of the potential future protocol downgrade attacks and other TLS vulnerabilities, it’s recommended to disable TLS 1.0 and 1.1.
Note: You must ensure that every application supports TLS 1.2 before disabling TLS 1.0 and 1.1.
Think about:
- Domain Controllers
- Partner applications
- Windows desktops, laptops, mobile devices
- Browser applications
- Multi-function printers
- Third-party integrations
The Set-ExchangeTLS.ps1 PowerShell script will set the best practice TLS settings for Exchange Server:
- Enable TLS 1.2
- Enable TLS 1.2 for .NET 4.x
- Enable TLS 1.2 for .NET 3.5
- Disable TLS 1.0
- Disable TLS 1.1
- Disable TLS 1.3
Note: TLS 1.3 is not supported by Exchange Server and has been known to cause issues if enabled.
Another option is to copy and paste the below code in Notepad. Give it the name Set-ExchangeTLS.ps1 and place it in the C:\scripts folder.
# Enable TLS 1.2
If (-Not (Test-Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server')) {
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' -Force | Out-Null
}
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' -Name 'Enabled' -value '1' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' -Name 'DisabledByDefault' -value 0 -PropertyType 'DWord' -Force | Out-Null
If (-Not (Test-Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client')) {
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -Force | Out-Null
}
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -Name 'Enabled' -value '1' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -Name 'DisabledByDefault' -value 0 -PropertyType 'DWord' -Force | Out-Null
Write-Host 'TLS 1.2 has been enabled.' -ForegroundColor Cyan
# Enable TLS 1.2 for .NET 4.x
If (-Not (Test-Path 'HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319')) {
New-Item 'HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319' -Force | Out-Null
}
New-ItemProperty -Path 'HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319' -Name 'SystemDefaultTlsVersions' -value '1' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -Path 'HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319' -Name 'SchUseStrongCrypto' -value '1' -PropertyType 'DWord' -Force | Out-Null
If (-Not (Test-Path 'HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319')) {
New-Item 'HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319' -Force | Out-Null
}
New-ItemProperty -Path 'HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319' -Name 'SystemDefaultTlsVersions' -value '1' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -Path 'HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319' -Name 'SchUseStrongCrypto' -value '1' -PropertyType 'DWord' -Force | Out-Null
Write-Host 'TLS 1.2 for .NET 4.x has been enabled.' -ForegroundColor Cyan
# Enable TLS 1.2 for .NET 3.5
If (-Not (Test-Path 'HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v2.0.50727')) {
New-Item 'HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v2.0.50727' -Force | Out-Null
}
New-ItemProperty -Path 'HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v2.0.50727' -Name 'SystemDefaultTlsVersions' -value '1' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -Path 'HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v2.0.50727' -Name 'SchUseStrongCrypto' -value '1' -PropertyType 'DWord' -Force | Out-Null
If (-Not (Test-Path 'HKLM:\SOFTWARE\Microsoft\.NETFramework\v2.0.50727')) {
New-Item 'HKLM:\SOFTWARE\Microsoft\.NETFramework\v2.0.50727' -Force | Out-Null
}
New-ItemProperty -Path 'HKLM:\SOFTWARE\Microsoft\.NETFramework\v2.0.50727' -Name 'SystemDefaultTlsVersions' -value '1' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -Path 'HKLM:\SOFTWARE\Microsoft\.NETFramework\v2.0.50727' -Name 'SchUseStrongCrypto' -value '1' -PropertyType 'DWord' -Force | Out-Null
Write-Host 'TLS 1.2 for .NET 3.5 has been enabled.' -ForegroundColor Cyan
# Disable TLS 1.0
If (-Not (Test-Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server')) {
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server' -Force | Out-Null
}
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server' -Name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server' -Name 'DisabledByDefault' -value 1 -PropertyType 'DWord' -Force | Out-Null
If (-Not (Test-Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client')) {
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client' -Force | Out-Null
}
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client' -Name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client' -Name 'DisabledByDefault' -value 1 -PropertyType 'DWord' -Force | Out-Null
Write-Host 'TLS 1.0 has been disabled.' -ForegroundColor Cyan
# Disable TLS 1.1
If (-Not (Test-Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server')) {
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server' -Force | Out-Null
}
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server' -Name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server' -Name 'DisabledByDefault' -value 1 -PropertyType 'DWord' -Force | Out-Null
If (-Not (Test-Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client')) {
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client' -Force | Out-Null
}
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client' -Name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client' -Name 'DisabledByDefault' -value 1 -PropertyType 'DWord' -Force | Out-Null
Write-Host 'TLS 1.1 has been disabled.' -ForegroundColor Cyan
# Disable TLS 1.3
If (-Not (Test-Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.3\Server')) {
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.3\Server' -Force | Out-Null
}
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.3\Server' -Name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.3\Server' -Name 'DisabledByDefault' -value 1 -PropertyType 'DWord' -Force | Out-Null
If (-Not (Test-Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.3\Client')) {
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.3\Client' -Force | Out-Null
}
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.3\Client' -Name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null
New-ItemProperty -Path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.3\Client' -Name 'DisabledByDefault' -value 1 -PropertyType 'DWord' -Force | Out-Null
Write-Host 'TLS 1.3 has been disabled.' -ForegroundColor Cyan
Write-Host 'You must restart the Windows Server for the changes to take effect.' -ForegroundColor CyanRun PowerShell as administrator. Change the path to C:\scripts and run the script.
PS C:\> cd C:\scripts
PS C:\scripts> .\Set-ExchangeTLS.ps1Reboot the Exchange Server.
Verify Exchange Server TLS settings
Run the Exchange Health Checker script and check the TLS settings.
You can see that there are no more errors, and everything looks great. Also, all the values are set as 0 or 1 and not NULL values, which is the best configuration.
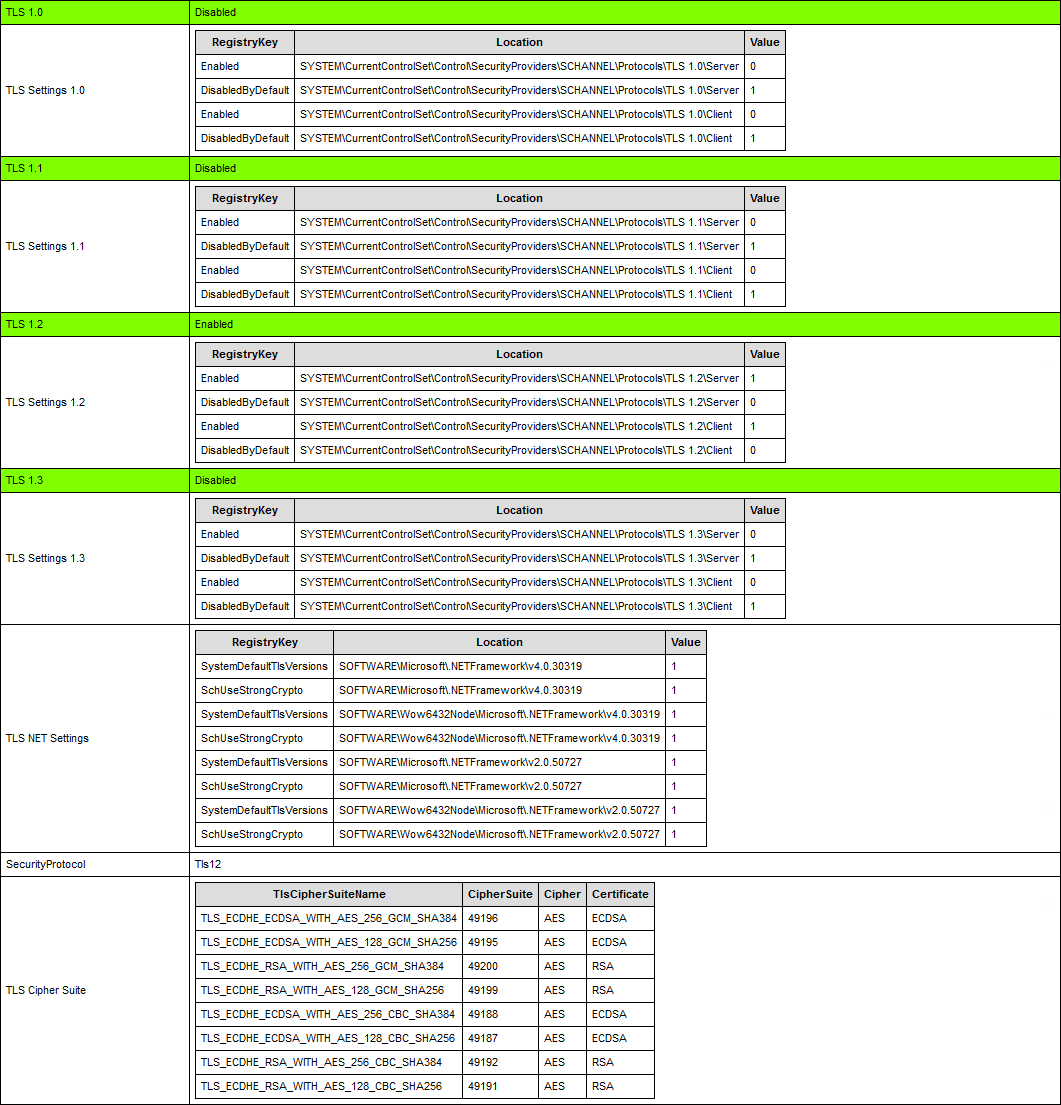
An alternative method is to run the Get-TLS.ps1 PowerShell script, which will display the TLS configuration. Read more in the article Check TLS settings on Windows Server with PowerShell script.
That’s it!
Keep reading: Unable to install NuGet provider for PowerShell »
Conclusion
You learned how to configure Exchange Server TLS settings. Run the PowerShell script to set the Exchange Server TLS best practices. Always make a backup of the registry before you apply changes, so you can restore it immediately when something goes wrong.
Did you enjoy this article? You may also like A fatal error occurred while creating a TLS client credential. Don’t forget to follow us and share this article.



Set-ExchangeTLS.ps1 won’t run because it’s not digitally signed.
Unblock the file.
Read more in the article: Not digitally signed error when running PowerShell script.
Hi Ali,
I havent enabled extended protection yet. Because it gave TLS error.
I applied this TLS settings to the second member of our Exchange server 2016 DAG to see if there will be an issue. After configuring registry settings and restarting the server, one problem occured: When i add new exchange account over Android outlook application it always gives cannot login on server error. The problem was not there before restarting the server. I installed last updated application but cannot add the account. We tried 3-4 account and android phone.
Has anyone encountered such an error?
beware old sql 2012 connection got broken after applying this tls1.2.
SQL Server 2012 supports TLS 1.2.
I recommend that you look at which SQL Server 2012 is running and upgrade to a supported TLS 1.2 version.
You shouldn’t use SQL Server 2012 anyway because its out of support since 12 July, 2022.
Hi ALi
i guest that Set-ExchangeTLS.ps1 PowerShell script should Enable the TLS1.3
TLS 1.3 is enabled by default in WIn Server 2022
in the article you mentioned : Disable TLS 1.3
thank a lot for your awesome Articles
good luck
As written in the article:
Note: TLS 1.3 is not supported by Exchange Server and has been known to cause issues if enabled.
After configuring HCW on Exchange 2013 with minimal classic configuration, TLS fails on receiving connector with Gmail only the NDR response was:
TLS Negotiation failed: FAILED_PRECONDITION: starttls error (0): protocol error. Disabling TLS on the default receive connector and mail flow is restored.
Any advise will be greatly appreciated.
My Friend,
Need your help to re-enable TLS 1.0 and 1.1 exchange 2013.
Also the server keep show the below event:
EXCHANGE 36887 Error Schannel System
A fatal alert was received from the remote endpoint. The TLS protocol defined fatal alert code is 46.
I really don’t know if this event occurs because of TLS 1.0 & 1.1 disabled.
Thanks.
Can TLS 1.0 and 1.1 be disabled after the Windows Extended Protection script has already been applied (specifically with a DAG)?
Yes.
Ensure to have the same TLS settings on all Exchange Servers, and remember to reboot the Exchange Servers for changes to take effect.
Hi Ali,
Thanks for the guide, much appreciated!
Should the same changes be applied to domain controllers?
It’s recommended only to enable TLS 1.2/TLS 1.3 in the organization (Windows Servers/Windows Clients).
Read more in the article How to Enable TLS 1.2/TLS 1.3 on Windows Server.
Thanks for your help!
Thanks Ali for the exchange of technical knowledge. I will apply this change with the team this week. Thank you.