Remove alias from Microsoft 365 Groups in your cloud-based organization. The Microsoft 365 group is…
Export Office 365 users MFA status with PowerShell
We want to get a list of users with MFA status. By checking that, we are sure how many users have MFA enabled and which method they used. If you have not yet enabled MFA in your Microsoft 365/Azure tenant, you should do this immediately! In this article, you will learn how to export Office 365 users MFA status to CSV file.
Table of contents
Check MFA status in Microsoft 365 admin center
Let’s look at Microsoft 365 and check the MFA user status. Sign in to Microsoft 365 admin center. Navigate to Users > Active Users > Multi-factor authentication.
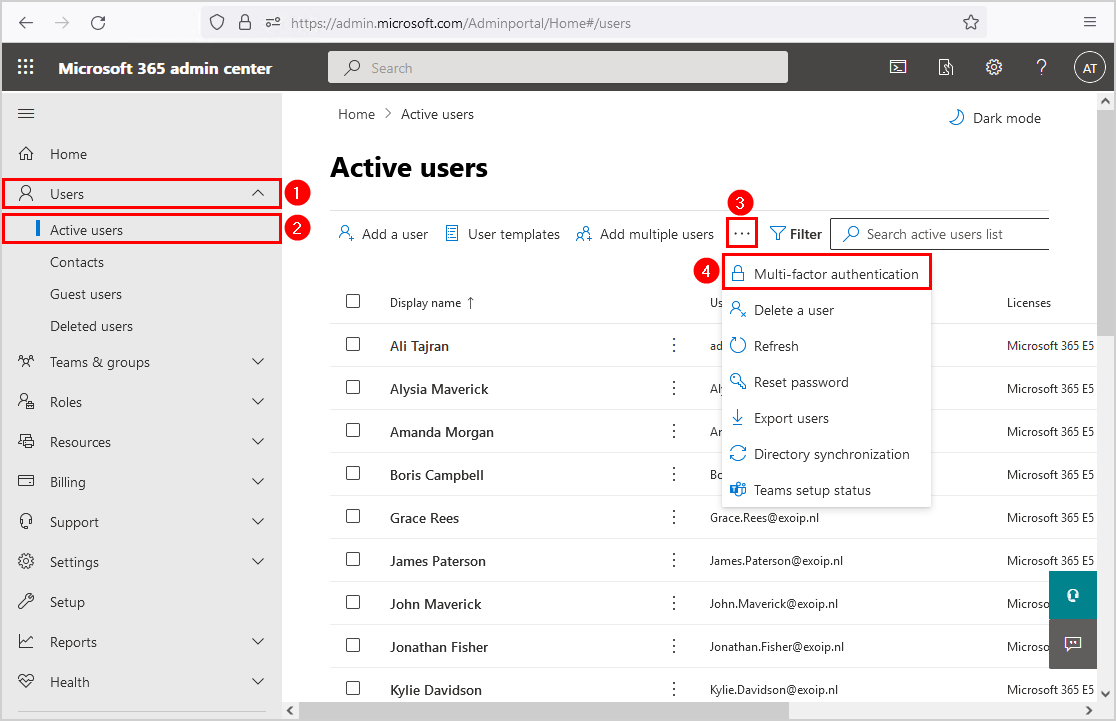
A new page will open, and it will show all the users and their multi-factor auth status. In our example, we have a couple of users MFA enabled, and MFA enforced. Most of the users have MFA disabled.
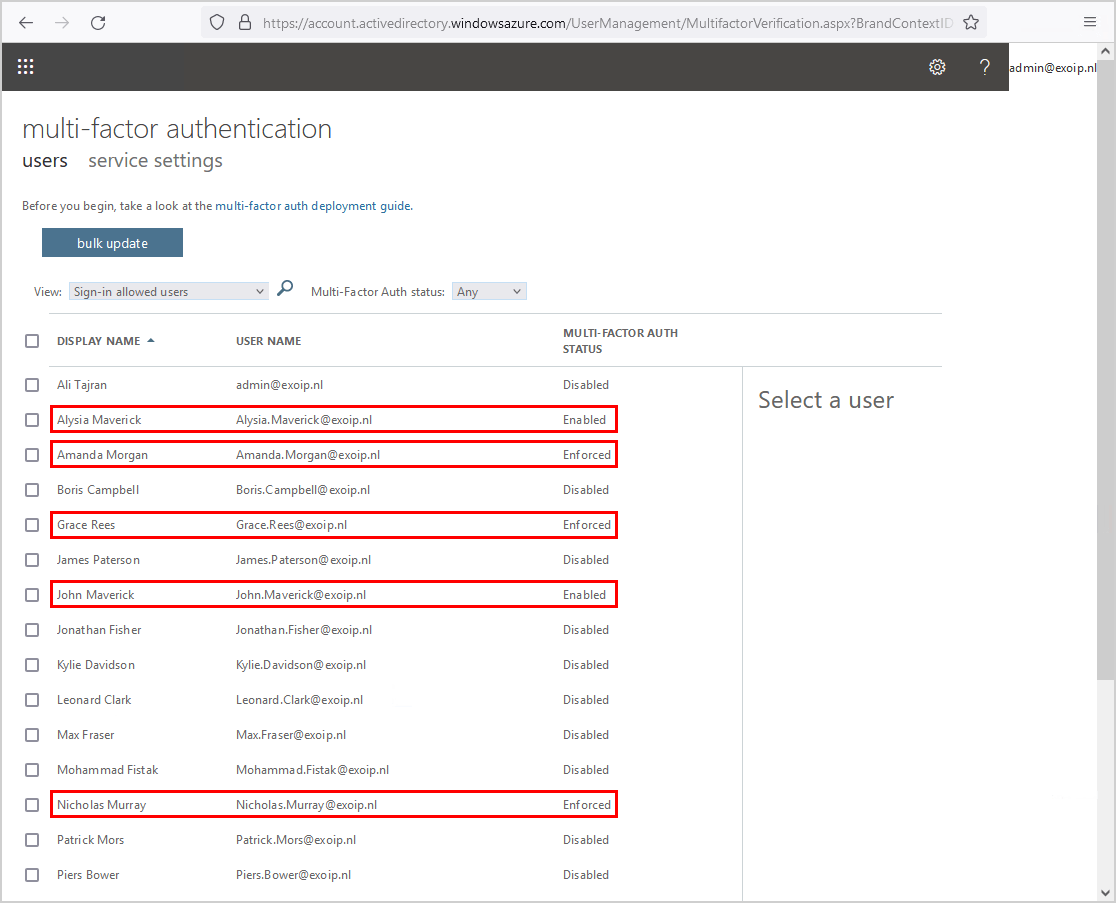
Why we do not recommend you to use the multi-factor authentication web page for information:
- Not shown if the users did finish the MFA process
- It does not indicate which MFA authorization option the user enabled
- No chance for export to CSV file
Note: If you see that MFA is enabled or enforced, it does not mean that MFA is configured.
The PowerShell script can’t identify the MFA status if it’s enabled with Conditional Access. That’s because Microsoft did not provide a way for that.
Is there a better way to have an insight into the MFA instead of the Microsoft 365 page? Yes, there is, and that’s when PowerShell will come to the rescue. In the next step, we will show how to create an MFA report.
Multi-Factor Authentication status
All users start out Disabled. When you enroll users in per-user Azure AD Multi-Factor Authentication, their state changes to Enabled. When enabled users sign in and complete the registration process, their state changes to Enforced. Administrators may move users between states Enforced, Enabled, and Disabled.
- Disabled
The default state for a user not enrolled in per-user Azure AD Multi-Factor Authentication.
- Enabled
The user is enrolled in per-user Azure AD Multi-Factor Authentication, but can still use their password for legacy authentication. If the user hasn’t yet registered MFA authentication methods, they receive a prompt to register the next time they sign in using modern authentication (such as via a web browser).
- Enforced
The user is enrolled per-user in Azure AD Multi-Factor Authentication. If the user hasn’t yet registered authentication methods, they receive a prompt to register the next time they sign in using modern authentication (such as via a web browser). Users who complete registration while in the Enabled state are automatically moved to the Enforced state.
Connect to Azure Active Directory
Before we can proceed further and get the MFA status for all the users, we need to install and connect to Azure AD with PowerShell (MsolService).
Start Windows PowerShell as administrator and run the cmdlet Connect-MsolService.
PS C:> Connect-MsolServiceNow that we are connected, we can go to the next step.
Prepare Get-MFAReport PowerShell script
Create two folders on the (C:) drive:
- Temp
- Scripts
Download the Get-MFAReport.ps1 PowerShell script and place it in C:\scripts folder. The script will export the CSV file to the C:\temp folder.
Another option is to copy and paste the below code into Notepad. Give it the name Get-MFAReport.ps1 and place it in the C:\scripts folder.
Write-Host "Finding Azure Active Directory Accounts..."
$Users = Get-MsolUser -All | Where-Object { $_.UserType -ne "Guest" }
$Report = [System.Collections.Generic.List[Object]]::new() # Create output file
Write-Host "Processing" $Users.Count "accounts..."
ForEach ($User in $Users) {
$MFADefaultMethod = ($User.StrongAuthenticationMethods | Where-Object { $_.IsDefault -eq "True" }).MethodType
$MFAPhoneNumber = $User.StrongAuthenticationUserDetails.PhoneNumber
$PrimarySMTP = $User.ProxyAddresses | Where-Object { $_ -clike "SMTP*" } | ForEach-Object { $_ -replace "SMTP:", "" }
$Aliases = $User.ProxyAddresses | Where-Object { $_ -clike "smtp*" } | ForEach-Object { $_ -replace "smtp:", "" }
If ($User.StrongAuthenticationRequirements) {
$MFAState = $User.StrongAuthenticationRequirements.State
}
Else {
$MFAState = 'Disabled'
}
If ($MFADefaultMethod) {
Switch ($MFADefaultMethod) {
"OneWaySMS" { $MFADefaultMethod = "Text code authentication phone" }
"TwoWayVoiceMobile" { $MFADefaultMethod = "Call authentication phone" }
"TwoWayVoiceOffice" { $MFADefaultMethod = "Call office phone" }
"PhoneAppOTP" { $MFADefaultMethod = "Authenticator app or hardware token" }
"PhoneAppNotification" { $MFADefaultMethod = "Microsoft authenticator app" }
}
}
Else {
$MFADefaultMethod = "Not enabled"
}
$ReportLine = [PSCustomObject] @{
UserPrincipalName = $User.UserPrincipalName
DisplayName = $User.DisplayName
MFAState = $MFAState
MFADefaultMethod = $MFADefaultMethod
MFAPhoneNumber = $MFAPhoneNumber
PrimarySMTP = ($PrimarySMTP -join ',')
Aliases = ($Aliases -join ',')
}
$Report.Add($ReportLine)
}
Write-Host "Report is in c:\temp\MFAUsers.csv"
$Report | Select-Object UserPrincipalName, DisplayName, MFAState, MFADefaultMethod, MFAPhoneNumber, PrimarySMTP, Aliases | Sort-Object UserPrincipalName | Out-GridView
$Report | Sort-Object UserPrincipalName | Export-CSV -Encoding UTF8 -NoTypeInformation "c:\temp\MFAUsers.csv"This is how it looks.
Run Get-MFAReport PowerShell script
Get MFA status for all users with PowerShell. Change the path to the scripts folder. After that, run the script Get-MFAReport.ps1.
PS C:\> cd c:\scripts\
PS C:\scripts> .\Get-MFAReport.ps1Out-GridView
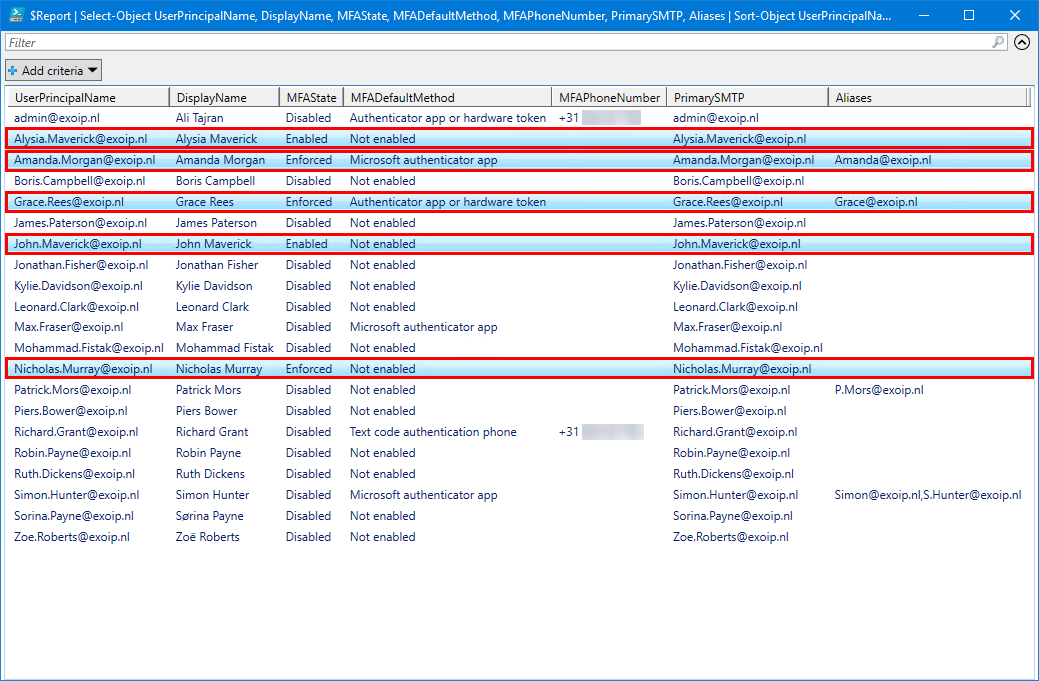
An Out-GridView will show columns with users and much more information than in the Microsoft 365 multi-factor authentication page.
Open MFA Users report CSV file
The Get-MFAReport.ps1 PowerShell script will export Office 365 users MFA status to CSV file. Find the file MFAUsers.csv in the path C:\temp.
Open the CSV file with your favorite application. In our example, it’s Microsoft Excel.
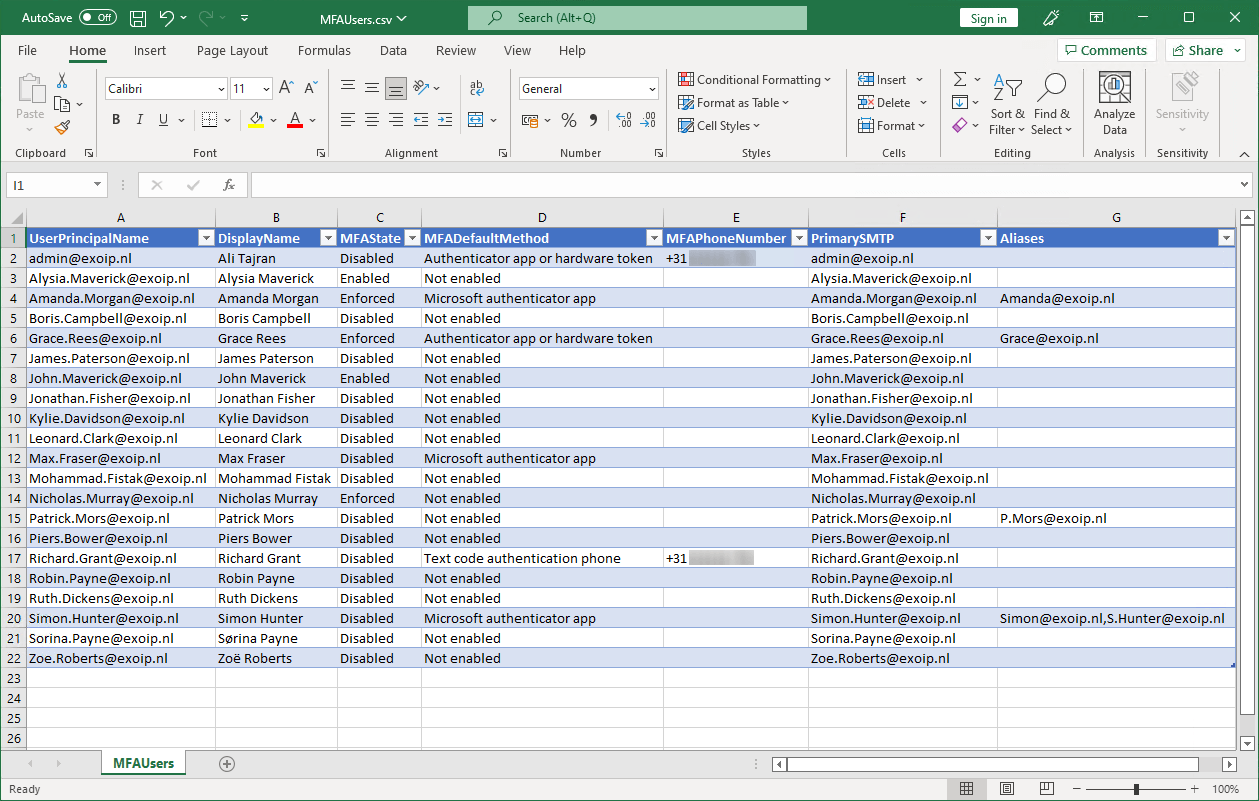
The MFA status report looks excellent.
Important: Don’t forget to enforce MFA for all the users in the tenant! It’s a must to protect the organization from brute force attacks and sign-ins.
Did this help you to export Office 365 users MFA status to CSV file?
Read more: Office 365 Recommended Configuration Analyzer »
Conclusion
You learned how to export MFA status Office 365 users with PowerShell. Get the MFA status report with Get-MFAReport PowerShell script and have a close look through it. Force MFA for all the users and check that they use the Authenticator app, which is Microsoft’s recommendation.
Did you enjoy this article? You may also like Install Exchange Online PowerShell module. Don’t forget to follow us and share this article.



This script is amazing! Worked brilliantly and very nice outputs. Thank you very much!
I just wanted to stop and say thank you for this. Made my life pretty easy this afternoon.
Thanks so much for all your work on your site. Always helping the community. Keep it up!
Many thanks for the very detailed explanation and screenshots, along with your script. I don’t do PowerShell very often. Following your instructions, this is the first time I have used the console without errors popping up all over the place!
I just tweaked the script slightly to drop the file in my User’s downloads folder. It has been a great help determining where I’m at with the MFA rollout. We don’t have a good enough Azure licence to get the info. from there!
Cheers!!!
Hi Ali,
How can I edit this script to only show MFAState “Disabled” so I don’t then have to filter within the csv?
Many thanks, this has already saved me lots of time!
This is great!
I’ve tried and failed to add the sign-in status, whether allowed or blocked.
And if the account is licensed or not.
Any pointers?
Thanks Ali.. script worked well..
Great work!
hi, would it be possible to modify this script so that you can input a csv with specific users instead of pulling alll?
Works great!
Thank You for share.
This was perfect, that and the input from commenters. Thank you very much Ali, your articles are really well written!
Ali,
Thank you so much for sharing. This is super helpful. I use this all the time now.
Thanks Brooooo…..You’re the best
Hello Ali,
When running the script, I am getting the following error:
.\Get-MFAReport.ps1 : File C:\scripts\Get-MFAReport.ps1 cannot be loaded. The file C:\scripts\Get-MFAReport.ps1 is not
digitally signed. You cannot run this script on the current system.
What can I change on my end to allow it to run this script?
Thank you,
Javier
Run this in PowerShell first:
And check the article Not digitally signed error when running PowerShell script.
Thank you man! Great job, this is very useful.
Ali, thank you so much for this. Can finally filter on disabled MFA users.
Because we only wanted AAD P1 licensed users (since we do have some shared mailboxes, SMTP AUTH, etc.), I changed the second line to
with our SKUID for our P1 and worked like a dream. In case anyone else is running into a similar situation.
Thanks! Great Job!
Hi Ali
Is it possible to change you script to show the MFA status of members in a particular group?
I’ve tried using get-msolgroupmember, but wasn’t successful. Assume it’s because it doesn’t return a UPN, but email address.
Thanks
Is there an option for the account status? That could be handy if you have a large account pool to see if those accounts are active. Ie AccountStatus = Active or disabled and even last logon ?
You the best mr. Ali. It works perfectly.
Works like a charm, thank you so much !
Hi, thanks for the script.
My scenario needs more values.
Department, Licenses, State, Company and Last Login Date.
i have added
$ReportLine = [PSCustomObject] @{
LastLogon = [datetime]::fromfiletime($logon)
Department = $User.Department
Licenses = $LicenseInfo
Country = $User.Country
Company = $Users.Company
Licenses info is a empty and LastLogon show 01.01.1601 02:00:00
what am i doing wrong ?
The best MFA export script out there! Thanks a lot!!
Hi Ali,
Thanks for the script , i have tried in test environment. it is working fine. i want to filter the users directly from the script based on the Department ,Country, Job Title, Region. can you help on this?
Thanks for the script. Got me the exact information I needed quickly.
Thank you for your scipt, saved me a big amount of time!
Hi all,
i have 1almost 1000 tenants with various active users – i need to see all the tenants active users MFA status.
i never tryed scripting, is there any video explaining it.
i am using 365 AD
Hi Ali and many thanks for the script.
It’s possible to add JobTitle information on the script, please?
Hello Ali,
Is there an alternative to get this information with ms graph for example?
I have looked at the /reports/authenticationMethods/userRegistrationDetails and /reports/credentialUserRegistrationDetails but I cant figure out the Enforced status from them.
Same issue here.
@ALI TAJRAN: Since MS Online will be depreciated soon are you planning to make this script usable with Graph?
I noticed that this shows only one MFA Method for each user. If a user has multiple MFA options configured in their myaccount.microsoft.com or their aka.ms/MFASetup user screens, then only one is selected for your report.
That’s correct. Only the default MFA method (MFADefaultMethod) is shown in the MFA report.
To hide guest and disabled accounts we changed line 2 to this:
That works!
Thank you for this comment. The original script included all the disabled users as well and I had no idea how to filter through the 100s of users we have. Much appreciated.
Hi Ali,
Thanks – that worked great on one of my tenants.
Quesstion,
this script will not show if a user enabled mfa on their own accord, this will only show if we manually went in and selected “enabled” on the per user mfa screen?
If that is the case is there a way to add to this report something to tell us that this user has *some kind of* mfa enabled, even though it wasnt done via the normal admin enabling mfa for the user?
Also would be good if this report could exclude disabled users.
I updated the script. It will show if the user manually configured MFA. Note that MFA will not appear for the user if the administrator doesn’t enable/enforce MFA for the user.
To exclude disabled users from the MFA report, change line 2
from:
to:
sweet! thanks bro!
Thank you, Ali! very usefull
Very handy script!!!
Thank you, Ali. 🙂
Hi Ali!
Thanks for your article!
Hi Ali,
Is it possible to add the mailbox type (usermailbox or shared mailbox) to the report. I was playing with $User.RecipientType or RecipientTypeDetails but I can’t get it right.
What can I do to add it to the script?
Thanks in advance!
Rudi
Hi Rudi,
Install Exchange Online PowerShell module and add the Connect-ExchangeOnline cmdlet in the PowerShell script to retrieve the mailbox types.
Hi Ali,
since i am using an Unicode language , how do i make the csv report to dispaly the characters since they displayed as ???? . suppose a command to use UTF-8.
Regards
Udi
Hi Udi,
I added the -Encoding UTF8 parameter to the script. The CSV report will now display the Unicode characters.
Thanks, worked perfectly.
Thanks for the script Ali, oddly for me I didn’t find the information the script provided was accurate. Nor the portal itself:
https://account.activedirectory.windowsazure.com/usermanagement/multifactorverification.aspx
For example, users I knew for sure had it enabled is coming up as disabled, in the above portal.
Have you ever experienced this?
You’re welcome, Abdush.
The script will create a report for per-user Office 365 Multi-Factor Authentication. I use the Get-MFAReport.ps1 script in different organizations, and it always gives me the correct values.
It looks like you use Azure Conditional Access Policy for MFA. However, the script will not work for it. At the moment, it’s not possible to create an accurate script when using Azure Conditional Access Policy for MFA.
Read more on how to move from per-user MFA to Conditional Access MFA.
Abdush is correct. Users can choose for themselfs to setup MFA, and after that they will still showup as ‘disabled’ in the MFA portal (second picure on this page).
In the MFA portal, you just indicate if MFA is required. And indeed, this can also be enforced by a conditional access policy.
When a user chooses to use MFA, that doesn’t mean the user will be “Enabled” or “Enforced”. That’s why it’s correct that it will show the MFA status for that user as “Disabled” in the Microsoft 365 MFA portal.
You still have to “Enable” or “Enforce” the user from the Microsoft 365 MFA portal or with PowerShell. After that, it will apply MFA to the user.
That’s how it works and is the correct behavior.
Hey Ali thanks so much for this guide!
Hi Ali,
Thank you for this detailed article.
Is it possible to include the date of when MFA was enabled on the report? can you please assist with editing the script if is possible.
Thank you.
Hi Leonah,
Microsoft didn’t give us an option to get the enabled MFA date. So, it’s not possible to add it to the report script.
Great work. but I have users who are enforced, they is using Hardware token (I configured it last week) but your script is showing “Enforced”,”Not enabled”. What might be wrong here? Thank you
Difficult to tell as I can’t reproduce it myself.
I do have tokens and I tested it right now. It shows the user as “Enforced – Authenticator app or hardware token”.
Thanks, works fine.
Hello Ali,
Thank you for this detailed article.
I would like to have user’s email populated as one more attribute.
Please help out with the script for that.
Hi Amit,
I updated the script. It will show the user’s primary SMTP and their aliases (secondary SMTP addresses).
Brilliant! Thank you, Ali!
I need to add UserPrincipalName to the output. I have tried various syntax but have not been successful. Please help!
You’re welcome, Jeri.
I updated the script. The UserPrincipalName will show in the Out-GridView and CSV report.
Works great !! Thanks Ali.
Nice little script, what would be handy is if it only displayed Licensed users ??
Change line 2
from:
to: