It's time to upgrade Microsoft Azure Active Directory Connect. Unfortunately, we cannot connect to Azure…
Get MFA status in Microsoft Entra and PowerShell
You don’t want to use PowerShell to list Microsoft 365/Microsoft Entra MFA users status? Instead, you want to use a Graphical User Interface (GUI). Do not worry because you can get all MFA details from the Microsoft Entra admin center. In this article, you will learn how to get MFA users authentication methods in Microsoft Entra and PowerShell. portal.
Table of contents
Configure MFA in Microsoft tenant
There are two ways to configure MFA in your Microsoft tenant:
We recommend option 1 because you have more control and more features to configure. But it requires Microsoft Entra ID P1 or Microsoft Entra ID P2 license. So, if you can’t afford those Entra ID editions, choose option 2, which is free.
While at it, read the article Prevent MFA fatigue attacks in organization and enable the settings shown for extra protection.
Important: Enable MFA for every tenant because it’s CRUCIAL.
Suppose you have Microsoft Entra ID P1 or P2 and configured per-user MFA but want to move to Conditional Access MFA; read the article Move from per-user MFA to Conditional Access MFA.
How to get all users MFA status in Microsoft Entra
Check which users have registered for MFA in the Microsoft Entra admin center by following these steps:
- Sign in to Microsoft Entra admin center
- Expand Identity > Protection
- Click on Authentication methods
- Select User registration details
Note: You need a Microsoft Entra ID P1 or P2 license to see the user registration details.
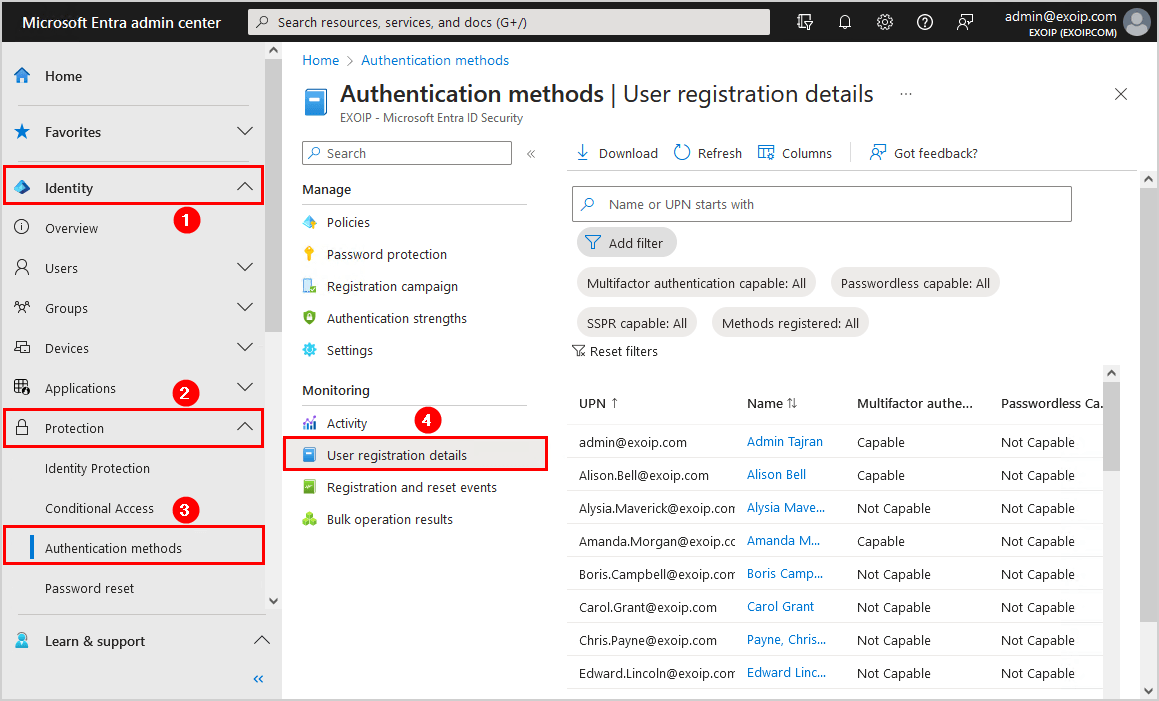
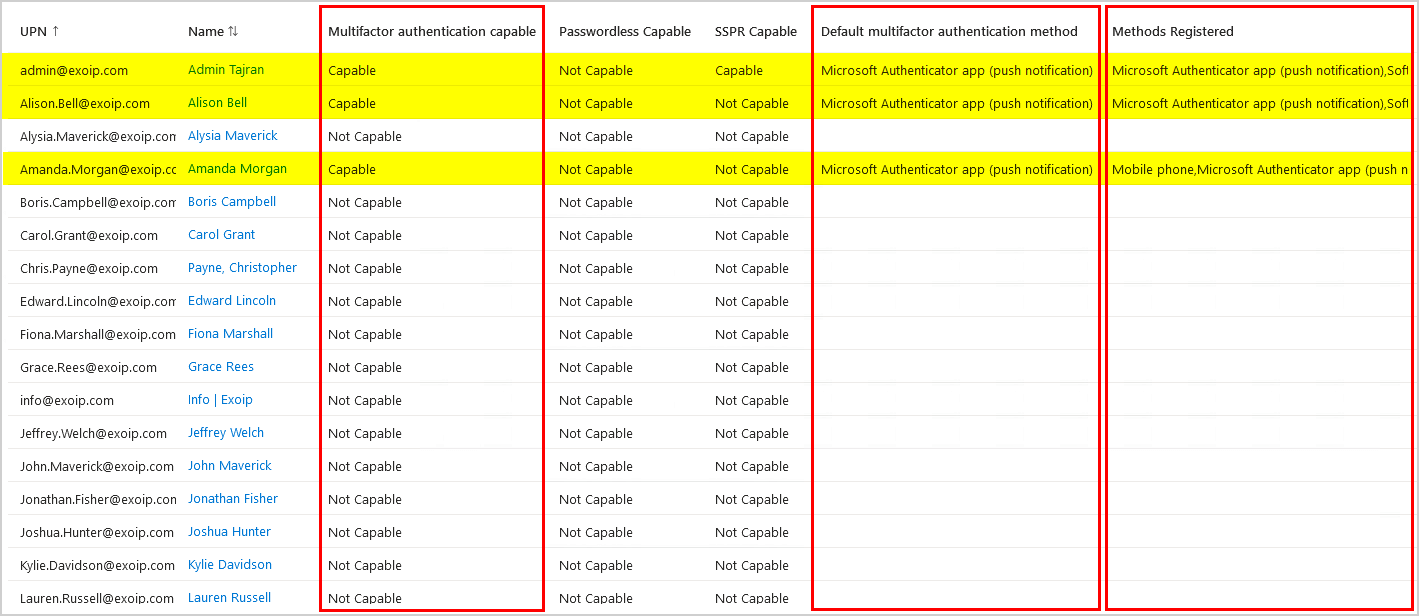
- Check the below columns to get the MFA user account status:
- Multifactor authentication capable
- Default multifactor authentication method
- Methods registered
What if you want to get the same report but with PowerShell? Let’s look at that in the next step.
Get users MFA status with Microsoft Graph PowerShell
An excellent way to get all the users authentication methods is with Microsoft Graph PowerShell.
The Get-AuthenticationMethods.ps1 script will get all the users default MFA method and registered authentication methods and export them to a CSV file.
For every user, it gathers the following information:
- Id
- UserPrincipalName
- IsAdmin
- DefaultMfaMethod
- MethodsRegistered
- IsMfaCapable
- IsMfaRegistered
- IsPasswordlessCapable
- IsSsprCapable
- IsSsprEnabled
- IsSsprRegistered
- IsSystemPreferredAuthenticationMethodEnabled
- LastUpdatedDateTime
Step 1. Prepare Get-AuthenticationMethods PowerShell script
Create two folders on the (C:) drive:
- Temp
- Scripts
Download the Get-AuthenticationMethods.ps1 PowerShell script and place it in C:\scripts folder. The script will export the CSV file to the C:\temp folder.
Ensure the file is unblocked to prevent errors when running the script. Read more in the article Not digitally signed error when running PowerShell script.
Another option is to copy and paste the below code into Notepad. Give it the name Get-AuthenticationMethods.ps1 and place it in the C:\scripts folder.
<#
.SYNOPSIS
Get-AuthenticationMethods.ps1
.DESCRIPTION
Export users authentication methods report from Micrososoft Graph and know which MFA method
is set as default for each user and what MFA methods are registered for each user.
.LINK
www.alitajran.com/get-mfa-status-entra/
.NOTES
Written by: ALI TAJRAN
Website: www.alitajran.com
LinkedIn: linkedin.com/in/alitajran
.CHANGELOG
V1.00, 10/12/2023 - Initial version
#>
# Export path for CSV file
$csvPath = "C:\Temp\AuthenticationReport.csv"
# Connect to Microsoft Graph
Connect-MgGraph -Scopes "User.Read.All", "Group.Read.All", "UserAuthenticationMethod.Read.All", "AuditLog.Read.All"
try {
# Fetch user registration detail report from Microsoft Graph
$Users = Get-MgBetaReportAuthenticationMethodUserRegistrationDetail -All
# Create custom PowerShell object and populate it with the desired properties
$Report = foreach ($User in $Users) {
[pscustomobject]@{
Id = $User.Id
UserPrincipalName = $User.UserPrincipalName
UserDisplayName = $User.UserDisplayName
IsAdmin = $User.IsAdmin
DefaultMfaMethod = $User.DefaultMfaMethod
MethodsRegistered = $User.MethodsRegistered -join ','
IsMfaCapable = $User.IsMfaCapable
IsMfaRegistered = $User.IsMfaRegistered
IsPasswordlessCapable = $User.IsPasswordlessCapable
IsSsprCapable = $User.IsSsprCapable
IsSsprEnabled = $User.IsSsprEnabled
IsSsprRegistered = $User.IsSsprRegistered
IsSystemPreferredAuthenticationMethodEnabled = $User.IsSystemPreferredAuthenticationMethodEnabled
LastUpdatedDateTime = $User.LastUpdatedDateTime
}
}
# Output custom object to GridView
$Report | Out-GridView -Title "Authentication Methods Report"
# Export custom object to CSV file
$Report | Export-Csv -Path $csvPath -NoTypeInformation -Encoding utf8
Write-Host "Script completed. Report exported successfully to $csvPath" -ForegroundColor Green
}
catch {
# Catch errors
Write-Host "An error occurred: $_" -ForegroundColor Red
}- Line 22: Edit the CSV file path
Note: If you want to check the MFA status for a specific group, replace lines 27, 28, and 29 with the code below. Add the group’s unique identifier after the -GroupId parameter.
try {
# Fetch group members
$GroupMembers = Get-MgGroupMember -GroupId "62dee815-d5c9-44ce-9085-e17f2c80734d" -All
# Extract Ids from group members
$GroupMemberIds = $GroupMembers.Id
# Fetch user registration detail report from Microsoft Graph for group members
$Users = Get-MgBetaReportAuthenticationMethodUserRegistrationDetail -All | Where-Object { $GroupMemberIds -contains $_.Id }Step 2. Install Microsoft Graph PowerShell
Run Windows PowerShell as administrator and Install Microsoft Graph PowerShell.
Install-Module Microsoft.Graph -ForceInstall-Module Microsoft.Graph.Beta -AllowClobber -ForceImportant: Always install the Microsoft Graph PowerShell and Microsoft Graph Beta PowerShell modules. That’s because some cmdlets are not yet available in the final version, and they will not work. Update both modules to the latest version before you run a cmdlet or script to prevent errors and incorrect results.
Step 3. Connect to Microsoft Graph PowerShell
Connect to Microsoft Graph PowerShell.
Connect-MgGraph -Scopes "User.Read.All", "UserAuthenticationMethod.Read.All", "AuditLog.Read.All"Enter your global administrator credentials and accept the Microsoft Graph permissions request.
Step 4. Run Get-AuthenticationMethods PowerShell script
Get all the users authentication methods with PowerShell. Run the below command to run the script Get-AuthenticationMethods.ps1.
c:\scripts\.\Get-AuthenticationMethods.ps1An Out-GridView will show columns with all the users and their information.
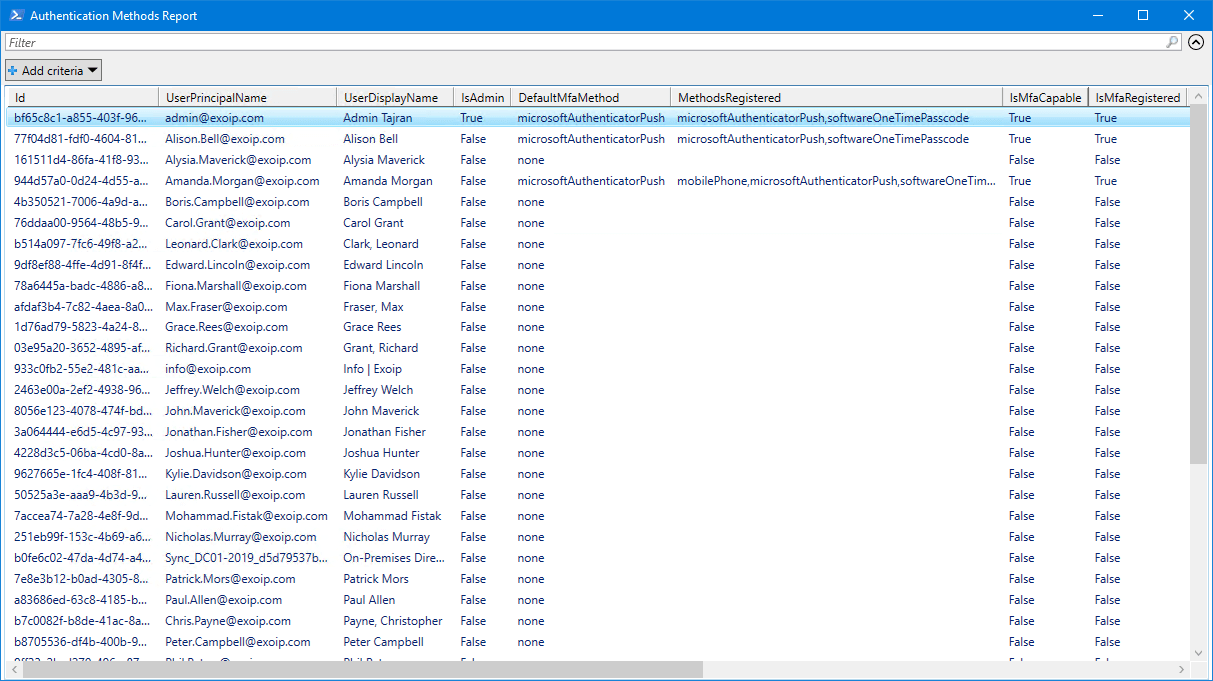
Step 5. Open Authentication Methods report
The Get-AuthenticationMethods.ps1 PowerShell script exports all users authentication methods to CSV file. Find the file AuthenticationReport.csv in the path C:\temp.
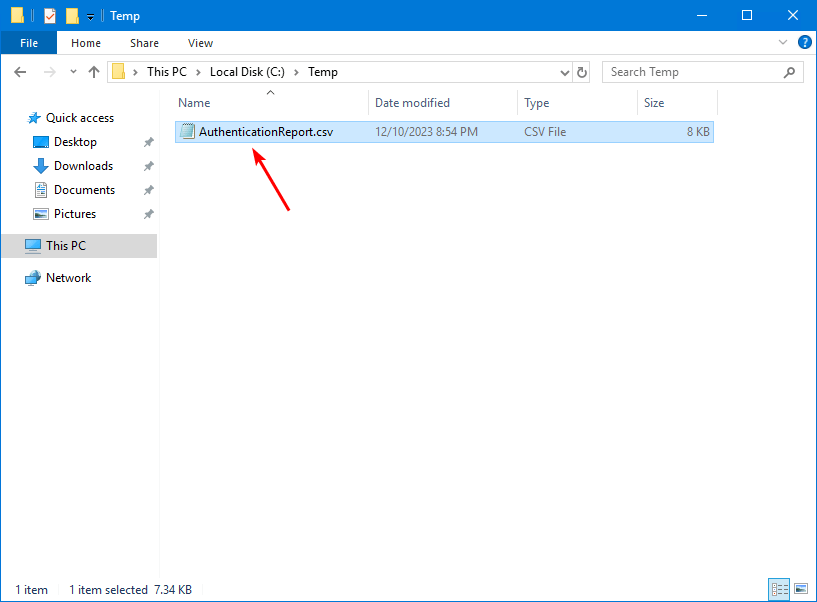
Open the CSV file with your favorite application. In our example, it’s Microsoft Excel.
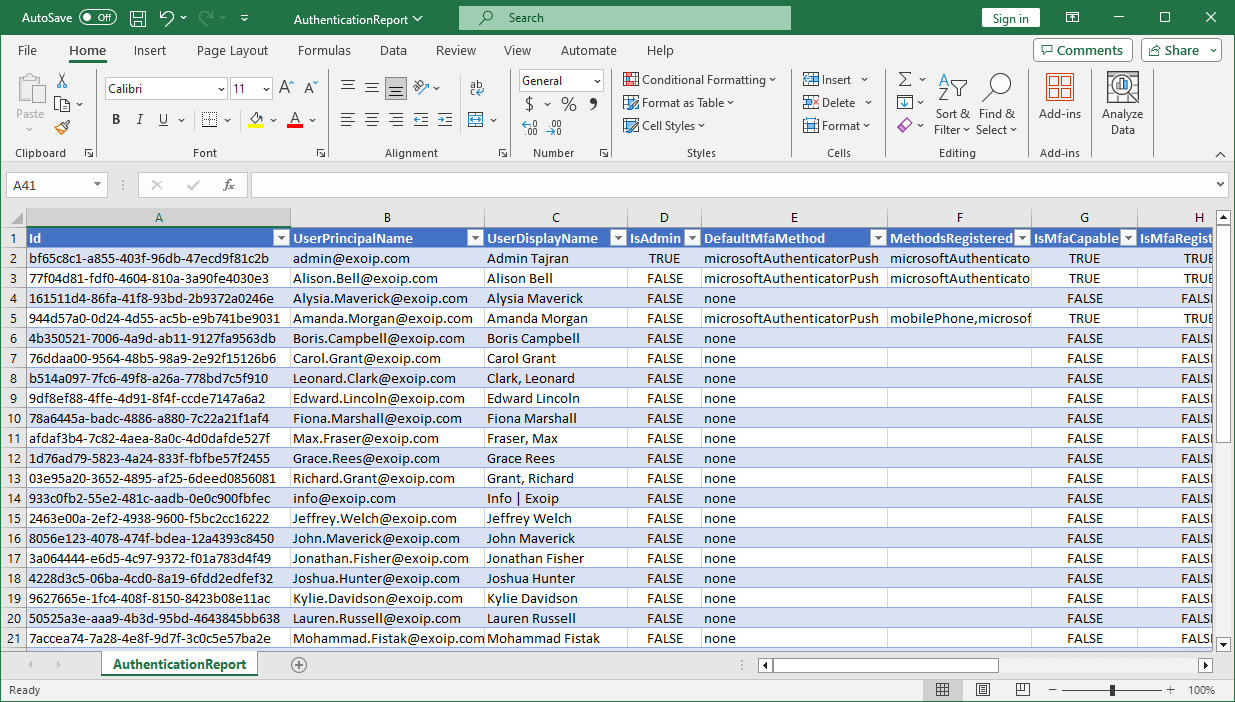
That’s it!
Multi-Factor authentication FAQs
There will be questions about when the status Capable and Not Capable appear for the user account in the list. Here are the main questions that you might have and their answers.
What is the difference between Capable and Not Capable?
- Capable: MFA is set up for the user account
- Not Capable: MFA is not set up for the user account
When does Multi-Factor Authentication appear as Capable?
It will show as Capable if the user completes the MFA wizard configuration. So as long as the user didn’t finish the MFA setup, it will appear as Not Capable.
If you enable or enforce per-user MFA for the user, and the user didn’t configure MFA, it still shows as Not Capable. The same applies if you configure MFA Conditional Access and add the user to the policy. If the user does not configure MFA, it shows as Not Capable.
Do per-user MFA and Conditional Access MFA appear in the list?
Yes, per-user MFA and Conditional Access MFA users and their authentication methods will appear in the list.
Important: Disable per-user MFA for all users when enabling MFA using Conditional Access.
Note: For the user accounts that show as Not Capable, contact the users and remind them to go through the MFA setup wizard.
Read more: Secure MFA and SSPR registration with Conditional Access »
Conclusion
You learned how to get MFA status in Microsoft Entra and PowerShell. Having the authentication methods section in the Microsoft Entra admin center is excellent. This helps the administrators who want to avoid using PowerShell to get the MFA status information.
Every user must configure Multi-Factor Authentication, and by looking at the user registration details in authentication methods, you can quickly identify which MFA methods are used and who still needs to configure MFA.
Did you enjoy this article? You may also like Conditional Access MFA breaks Azure AD Connect synchronization. Don’t forget to follow us and share this article.

Hi Ali,
THX for you Script, works Well 🙂
I have the following problem in a tenant
The list of users is not updated, it seems that the tenant does not reanalyze which users are ready for MFA
In the report, the date for “LastUpdatedDateTime” is now 18 days old
Are you aware of this problem and do you know how to trigger the analysis manually?
Hi Florian,
I can confirm this for all my tenants.
You might want to send them a support request so they can look into this.
There is no way to trigger a refresh manually. While this is an excellent feature to have!
Hi Ali,
thanks for this very useful script!
Question: is there a way I can target one specific Entra ID Group? I plan to use groups to manage the enablement waves, and it would be awesome if I could target Entra ID waves in form of groups.
Thanks again for your work!!
That’s possible.
I updated the article with the code that you can use to target a specific Microsoft Entra ID group.
Ali, that works like a charm!!! Thanks a lot!!
Now I can define my migration wave in form of a security group, query this security group using your script and, once communicated, bulk export the group contents into a CSV, and use that same CSV for adding the users to the Security Group that I manage to drive the migration. Thanks a lot!!
Hi,
defaultMethod was removed as output from MS?
have you found any workaround? I am trying to find a workaround at the moment.
The “Default multifactor authentication method” still appears in the Microsoft Entra admin center and PowerShell.
Once again, Ali Tajran coming to my rescue! Thank you!
According to per user MFA list, all the users are showing as disabled but when checked your method in azure portal, i have a values under methods registered. How this is possible?
Disabling users does not remove their authentication methods. The methods registered from per-user MFA will stay, and they can keep using them when you migrate over to Azure Conditional Access.
More information: Move from per-user MFA to Conditional Access MFA.