How to check Let's Encrypt certificate status? Let's Encrypt is a great way to secure…
Microsoft Exchange Server vulnerability check
Your Exchange Server infrastructure needs to stay up to date because of vulnerabilities, new features, and bug fixes. The best approach to get an Exchange Server security test is to run the Health Checker PowerShell script. It will scan the Exchange Servers and create a report if there are any vulnerabilities. In this article, you will learn how to do a Microsoft Exchange Server vulnerability check.
The Exchange Server Health Checker script is a PowerShell tool that scans an Exchange Server 2013/2016/2019 organization and evaluates it against a series of best practices and common configuration issues.
Table of contents
Exchange Server Cumulative Updates
You usually download the latest Exchange Server CU and install that. For example, you’re running Exchange 2019 CU7, and you download Exchange Server 2019 CU8, which is the newest version at that time. That does not mean you’re protected against all the known vulnerabilities. That’s when the Security Updates come into action.
With each Exchange CU version, you will have all security fixes, new features, bug fixes, and changes. Sometimes Microsoft doesn’t wait for the next CU because security is essential. That’s why they release Security Updates.
Microsoft will eventually add these Security Updates in the next CU. If you install a new Exchange Server, you should always install the latest CU and check for Security Updates available to install.
Note: The Exchange Server Cumulative Updates are cumulative. You do not need to install all the CUs in sequential order but can install the latest CU only.
Exchange Server Security Updates
Microsoft Security Updates are also known as Microsoft patch Tuesday. Every second week of the month, Microsoft releases patches for all Microsoft products. One of these products is Exchange Server. If there is no Microsoft Exchange Security Update available at that time, it means all is okay, and you don’t need to patch.
Note: The Exchange Server Security Updates are cumulative. If you are running the CU that the SU can be installed on, you do not need to install all the SUs in sequential order but can install the latest SU only.
Go to the Microsoft Security Update Guide for all the Security Updates. Filter on product family Exchange Server.
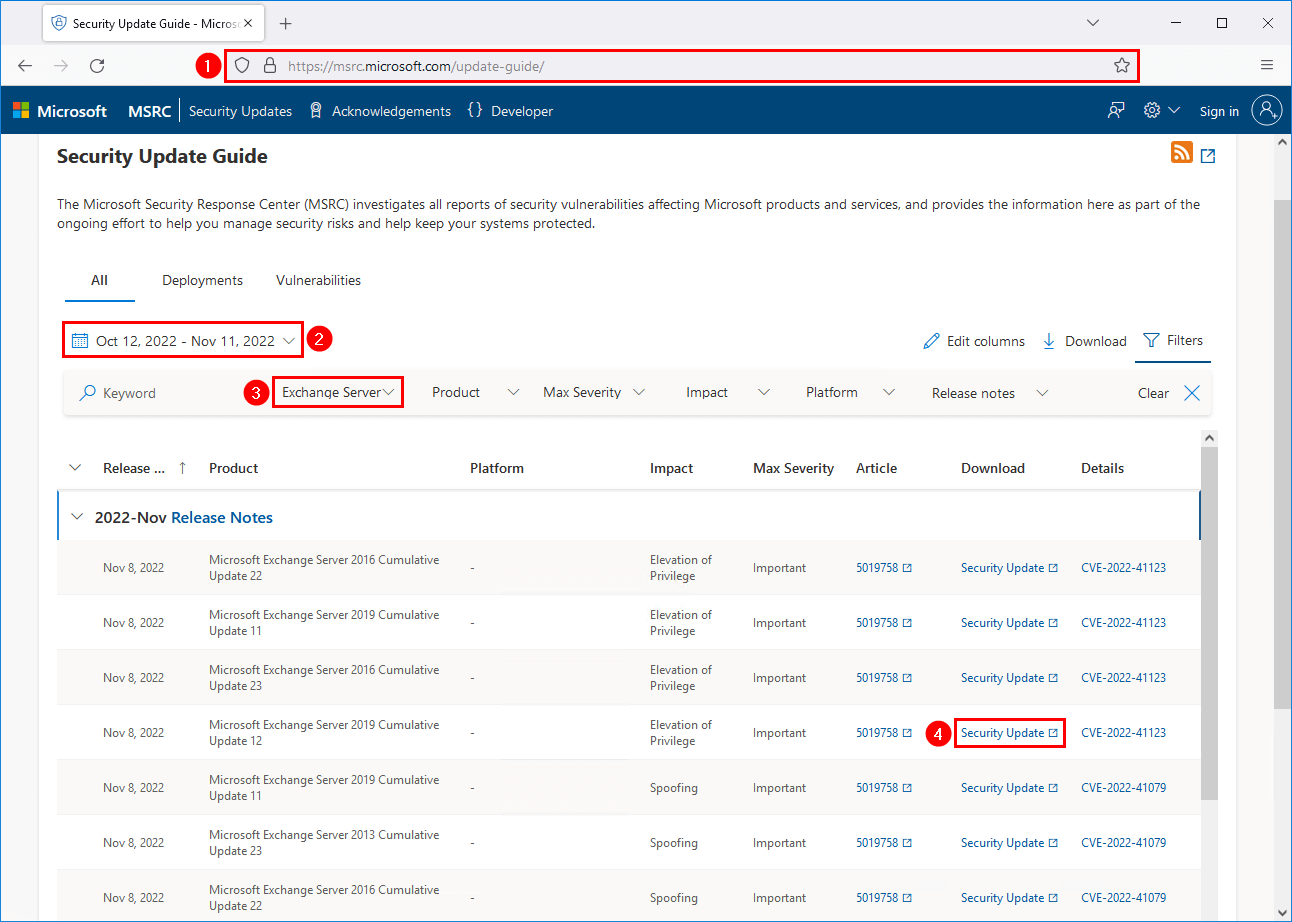
The Microsoft Security Response Center (MSRC) investigates all reports of security vulnerabilities affecting Microsoft products and services. It provides the information here as part of the ongoing effort to help you manage security risks and help keep your systems protected.
Patch Exchange Server immediately
Download and install Security Updates immediately on the Exchange Servers. If you wait or don’t, a significant chance of a live attack can take place. Check if you are compromised later.
Important: You must patch the Exchange Server first and investigate later. Don’t do it the other way around.
As long it’s not Microsoft 365 – Exchange Online, you need to install Cumulative Updates and Security Updates. An Exchange Server can be the:
- Exchange on-premises
- Exchange Hybrid
- Exchange in Azure
Now that you’re up to date between Cumulative Updates and Security Updates, let’s look at how to check if the Exchange Server is vulnerable or already patched.
Exchange Server vulnerability check
There is a good chance that you want to know if all Exchange Servers are patched. You don’t want to have an Exchange Server that is vulnerable (in a risk state). The best way is to run the Exchange Health Checker Powershell script and generate a report. Read more on that in the article to make yourself familiar with the script.
The authors add Microsoft security vulnerabilities in the Health Checker script once they are out. Remember to download the latest script version every time you want to check for Exchange Server security checks and best practices.
At the moment of writing, the latest release of the Health Checker script is version 3.3.2. In that release, they added security vulnerabilities results to the HTML Report for quick detection, which is an excellent addition to the script.
Download Health Checker PowerShell script
Download and place the HealthChecker.ps1 PowerShell script on the Exchange Server C:\scripts folder. If you don’t have a scripts folder, create one.
Ensure that the file is unblocked to prevent any errors when running the script. Read more in the article Not digitally signed error when running PowerShell script.
Create Exchange Servers report
Run Exchange Management Shell as administrator. Change the path to the scripts folder.
[PS] C:\>cd C:\scripts
[PS] C:\scripts>Verify the signature before running the script with the Get-AuthenticodeSignature cmdlet.
[PS] C:\scripts>Get-AuthenticodeSignature -FilePath ".\HealthChecker.ps1" | ft -AutoSize
Directory: C:\scripts
SignerCertificate Status Path
----------------- ------ ----
AFBF0B8B6A18F7E23CCA1DDCD0AC1A55B4035173 Valid HealthChecker.ps1Run the cmdlet to create a report for all Exchange Servers. It will run the HTML report and open it automatically.
[PS] C:\scripts>Get-ExchangeServer | ?{$_.AdminDisplayVersion -Match "^Version 15"} | .\HealthChecker.ps1; .\HealthChecker.ps1 -BuildHtmlServersReport -HtmlReportFile "ExchangeAllServersReport.html"; .\ExchangeAllServersReport.htmlIf the report does not open automatically, you can find the report in the C:\scripts folder.
Check Exchange Servers report for vulnerabilities
The HTML Report will show as below screen. All looks great because the environment got two Exchange Servers with the mailbox role. Both of them are on Exchange 2019 CU12 and patched. The column Security Vulnerabilities shows both Exchange Servers as None.

If you’re not up to date or not patched, it will show you that you’re vulnerable. What you can do is download and patch the vulnerability with the appropriate Security Update. The Exchange Team will most likely release the security patch only for the latest or the last two Cumulative Updates.
Do you see red or yellow warnings in the Exchange Server report? Look into it and fix it!
It’s important to have the Exchange Servers up to date as it will simplify pushing the Security Updates. When new security patches are rolling out, you don’t have to update to the latest CU and patch, which takes much more time than immediately patching because you are already on the latest CU.
Read more: March 2021 Exchange Server Security Updates »
Conclusion
You learned how to check for Microsoft Exchange Server vulnerabilities with the PowerShell HealthChecker.ps1 script. Secure the Exchange Server with the latest Cumulative Updates and Security Updates once they are released. After that, check if you are compromised with the guidelines that Microsoft provides.
Did you enjoy this article? You may also like Check Exchange health mailboxes. Don’t forget to follow us and share this article.



Hello there,
I have upgraded Exchange 2016 from CU 21 to CU23. After that I have installed the security update (KB5030877)
I ran latest HealthChecker and it is still reporting the following;
CVE-2022-24516, CVE-2022-21979, CVE-2022-21980, CVE-2022-24477, CVE-2022-30134
——————————————–
[PS] C:\scripts>.\Get-ADversions.ps1
RangeUpper: 15334
ObjectVersion (Default): 13243
ObjectVersion (Configuration): 16223
Update:
I did the steps in the link (below) and CVEs are closed.
https://www.alitajran.com/extended-protection-exchange-server/
I have upgraded Exchange 2016 from CU 16 to CU21. After that I have installed the security update (KB5004779). rebooted the server. I ran latest HealthChecker and it is still reporting the following, any guidance to mitigate this would be much appreciated.
The report shows that you didn’t extend the AD schema. Check your Exchange schema version and verify.
Exchange 2016 CU21 schema should be on version:
rangeUpper: 15334
objectVersion (Default): 13241
objectVersion (Configuration): 16221