The Azure AD Connect synchronization service is not exporting the AD objects and shows the…
Renew certificate in Exchange Hybrid
How to renew a certificate in Exchange Hybrid? You have a new third-party certificate installed on the Exchange Server. Now that you finished that task, you like to remove the old certificate. But you get a message that these certificates are tagged with the Outbound to Office 365 send connector. Why is this happening, and what is the solution?
Table of contents
Invalid Exchange certificate
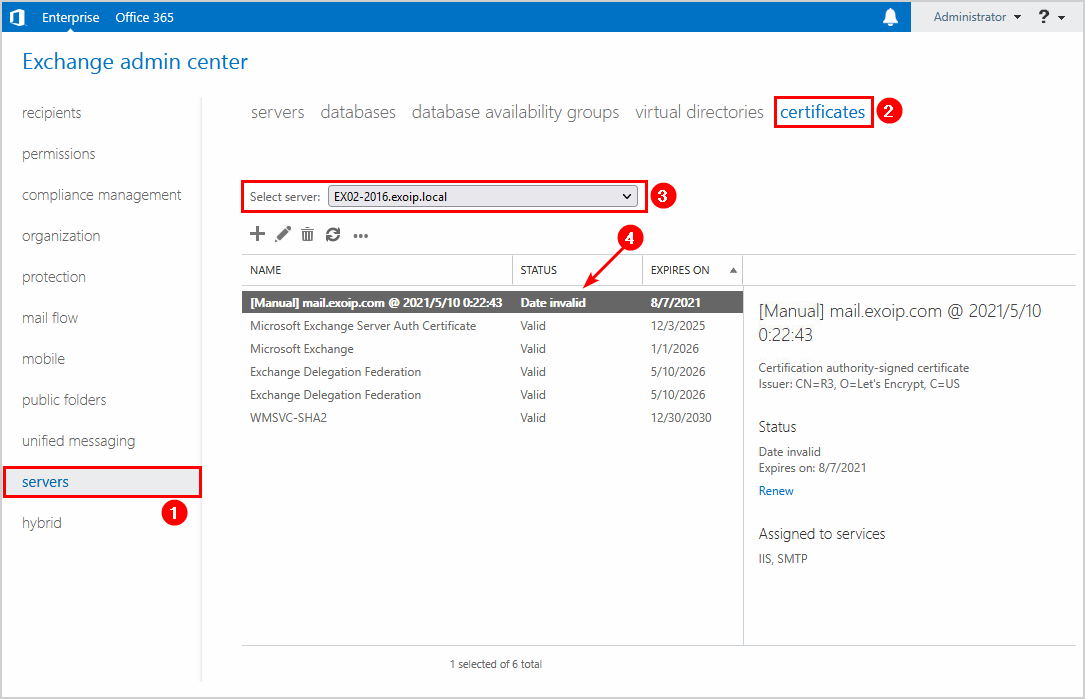
Sign in to the Exchange Server. Navigate to servers > certificates. Select the Exchange Server from the drop-down menu if you have multiple Exchange Servers.
In our example, we have an invalid certificate.
Important: In production environments, you need to renew the certificate before it gets invalid. Otherwise, mail flow will not work.
Install Exchange certificate
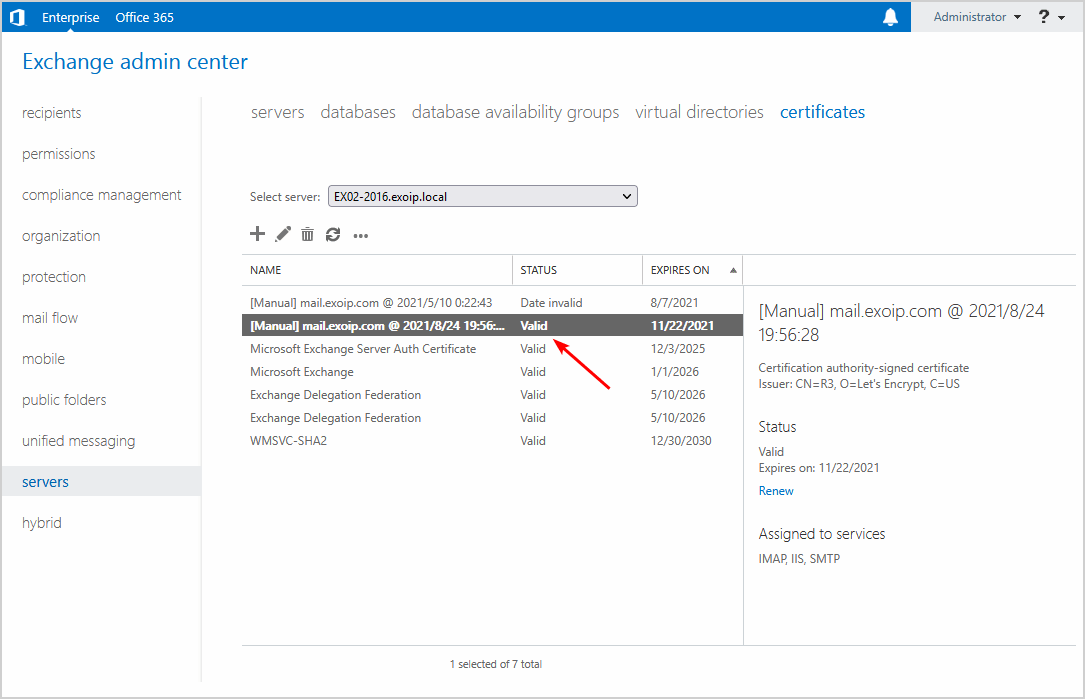
We did install a free Let’s Encrypt certificate on the Exchange Server. Also, we did assign it to the services IMAP, ISS, and SMTP. The certificate shows the status Valid.
Read more: Install Exchange certificate with PowerShell »
These certificates are tagged with following Send Connectors
The new certificate is installed and valid. However, the old certificate is invalid. Let’s remove the old certificate on the Exchange Server to keep everything tidy.
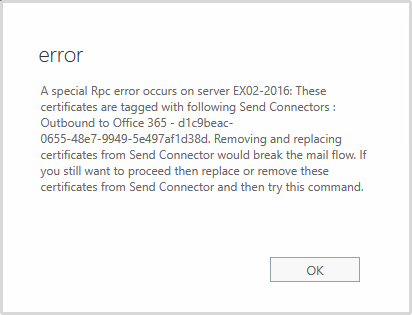
When we want to remove the invalid Exchange certificate, we do get an error.
error
A special Rpc error occurs on server EX02-2016: These certificates are tagged with following Send Connectors : Outbound to Office 365 – d1c9beac-0655-48e7-9949-5e497af1d38d. Removing and replacing certificates from Send Connector would break the mail flow. If you still want to proceed then replace or remove these certificates from Send Connector and then try this command.
Why do we get this error, and what is the solution for removing the certificates that are tagged with the send connector Outbound to Office 365?
Renew certificate in Exchange Hybrid with PowerShell
The solution to this error is that we need to assign the new certificate to the:
- Send connector: Outbound to Office 365
- Receive connector: Default frontend
Important: Do the same steps on the other Exchange Servers.
Follow these steps:
Step 1. Collect information
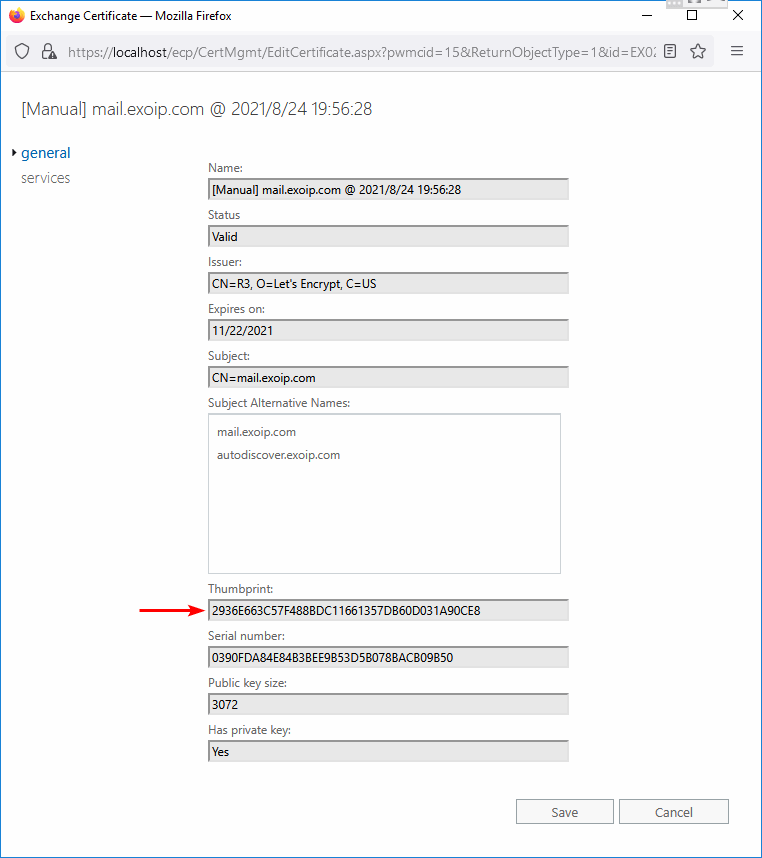
Double-click the new certificate in the Exchange admin center. Copy the Thumbprint.
Go to mail flow > send connectors. Copy the Outbound to Office 365 send connector name. In our example, it’s Outbound to Office 365 – d1c9beac-0655-48e7-9949-5e497af1d38d.
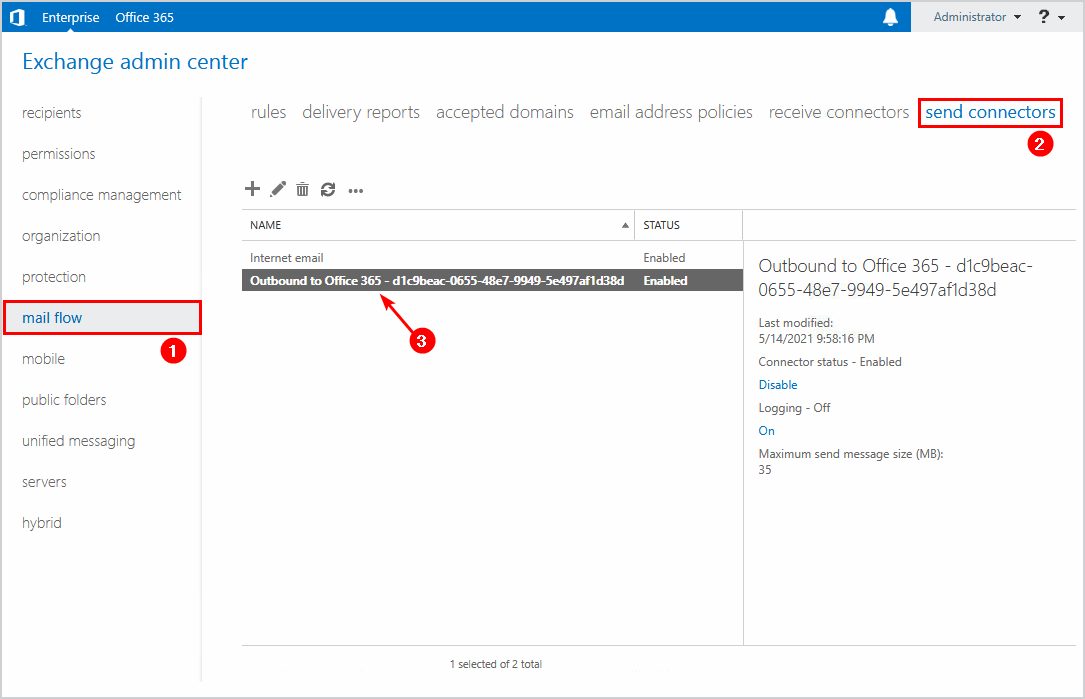
Go to mail flow > receive connectors. Copy the Default Frontend receive connector name. In our example, it’s Default Frontend EX02-2016.
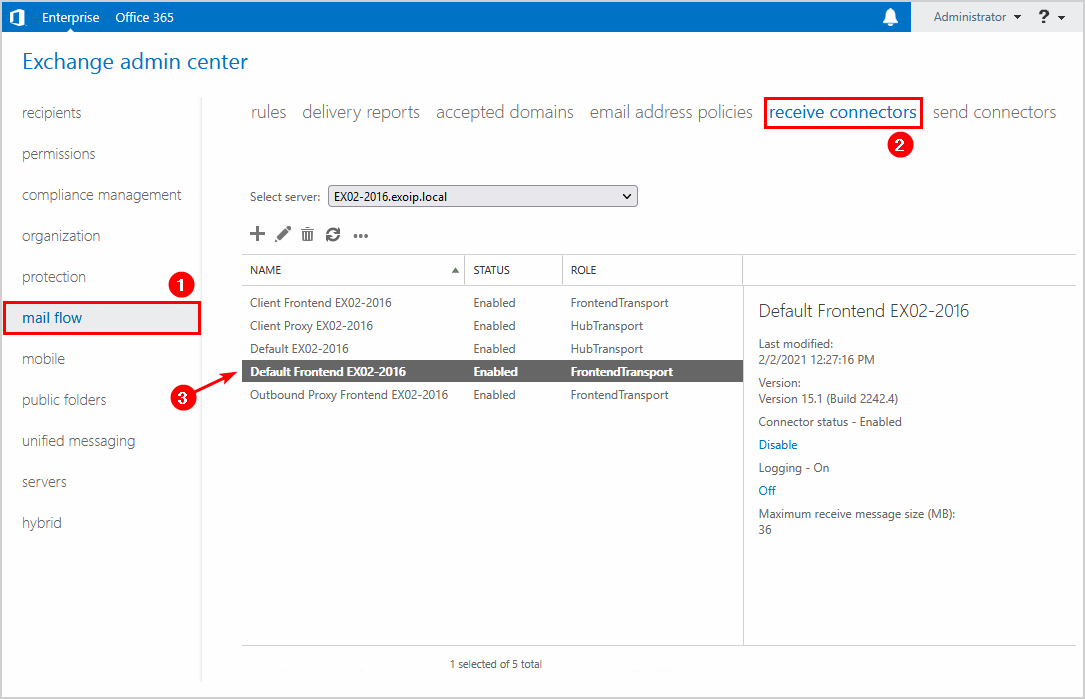
Step 2. Set the new certificate
Run Exchange Management Shell as administrator. Get the Exchange certificate with the thumbprint that you copied in the previous step.
PS] C:\>Get-ExchangeCertificate -Thumbprint "2936E663C57F488BDC11661357DB60D031A90CE8"
Thumbprint Services Subject
---------- -------- -------
2936E663C57F488BDC11661357DB60D031A90CE8 I..WS.. CN=mail.exoip.comStore the value to the $TLSCert variable.
[PS] C:\>$TLSCert = Get-ExchangeCertificate -Thumbprint "2936E663C57F488BDC11661357DB60D031A90CE8"Store the certificate issuer and certificate subject values to the $TLSCertName variable.
[PS] C:\>$TLSCertName = "<I>$($TLSCert.Issuer)<S>$($TLSCert.Subject)"Run the Set-SendConnector cmdlet, including the TlsCertificateName parameter. Fill in the Exchange Server name\send connector name that you copied in the previous step.
[PS] C:\>Set-SendConnector "Outbound to Office 365 - d1c9beac-0655-48e7-9949-5e497af1d38d" -TlsCertificateName $TLSCertNameRun the Set-ReceiveConnector cmdlet, including the TlsCertificateName parameter. Fill in the Exchange Server name\receive connector name that you copied in the previous step.
[PS] C:\>Set-ReceiveConnector "EX02-2016\Default Frontend EX02-2016" -TlsCertificateName $TLSCertNameYou can get a warning as output when you run the Set-SendConnector and Set-ReceiveConnector cmdlets. That’s because the new certificate’s Issuer field and certificate’s Subject field are the same as the old certificate.
In our example, we did add a new Let’s Encrypt certificate. But the old certificate is also from Let’s Encrypt. That’s why we did get the below error.
WARNING: The command completed successfully but no settings have been modified.
When you see the above warning, you don’t have to worry. But you should delete the old certificate. Unfortunately, it will not let you delete it in the Exchange admin center because it still thinks it’s connected to both connectors.
View the certificates in the MMC snap-in, and delete the invalid certificate in the Personal store. An excellent way to identify the certificate is by checking the Expiration Date.
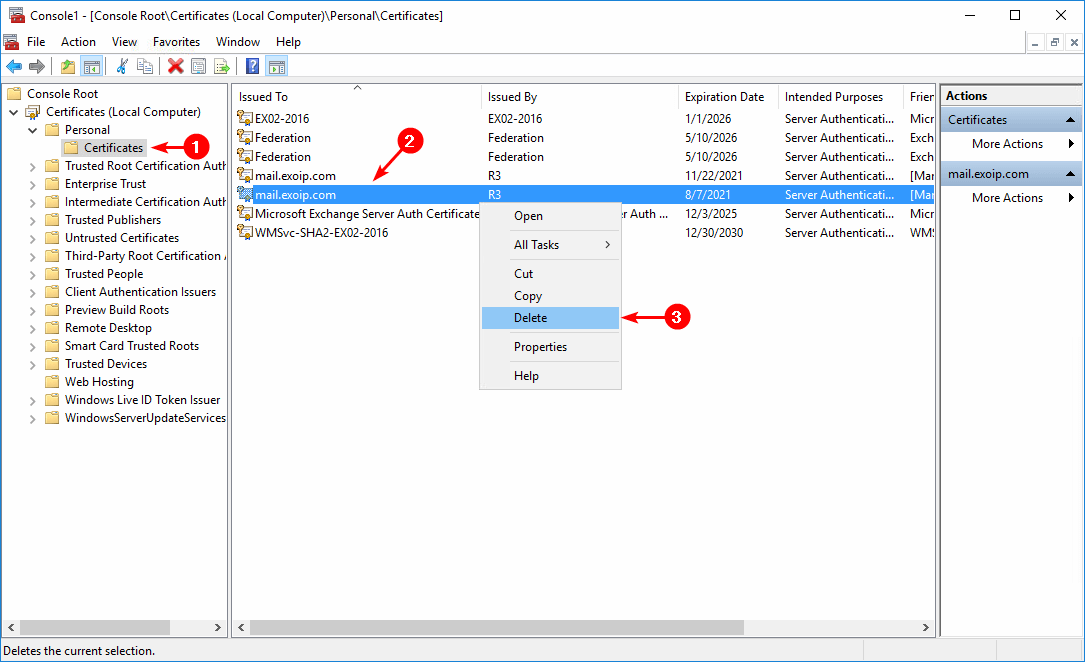
Go back to the Exchange admin center. Refresh the page or click the refresh icon in the toolbar. The old certificate is removed successfully, and the new certificate is still available.
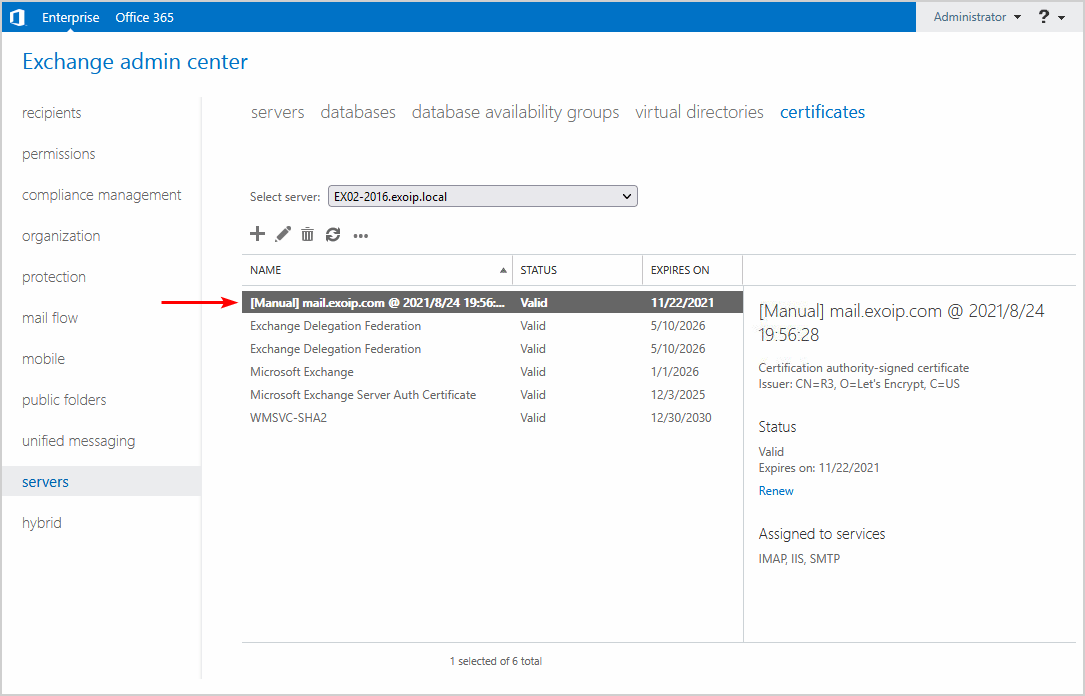
Step 3. Restart IIS
Restart the Internet Information Services (IIS) on the Exchange Server.
[PS] C:\>iisresetRenew certificate in Exchange Hybrid with Office 365 Hybrid Configuration Wizard
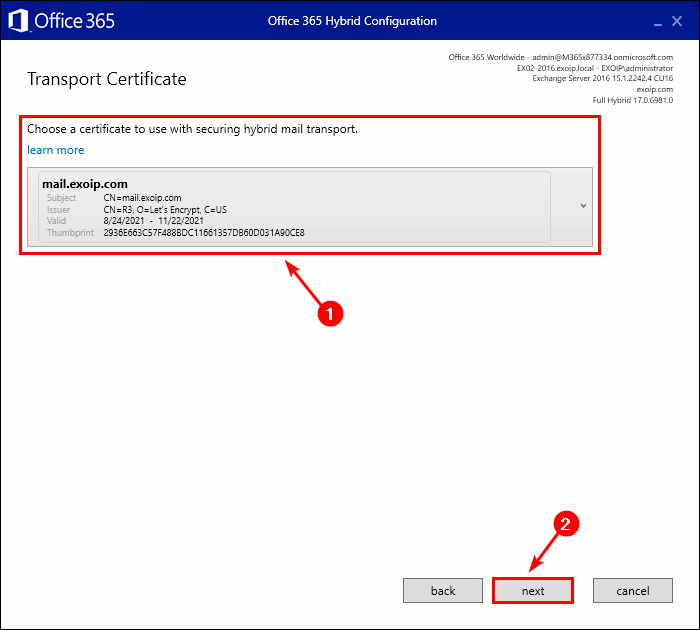
Another way to renew the Exchange Hybrid certificate is to rerun the Hybrid Configuration Wizard. Connect in the first step with your credentials and go through the setup wizard by clicking the Next button.
You will see the Transport Certificate window in the setup wizard. Choose the new certificate. Click next.
Click on update.
The Office 365 Hybrid Configuration Wizard configured the new certificate for both the send connector and receive connector.
That’s it!
Keep reading: Renew Microsoft Exchange Server Auth Certificate »
Conclusion
You learned how to renew the Exchange Hybrid certificate. Collect the new certificate information and run the commands to set the TLS certificate on the send connector and receive connector. Another way is to rerun the Office 365 Hybrid Configuration Wizard and select the new certificate.
Did you enjoy this article? You may also like How to export certificate in Exchange Server. Don’t forget to follow us and share this article.



I’m a little confused. If I install the new certificate, assign services, reset iis and run the Hybrid Wizard do I need to run the commands for the send and receive connectors or does the hybrid wizard take care of that.
I did accidently used the Set-ReceiveConnector “Client Frontend” Command and set it with to the new certificate aswell.
I am not sure if thats caused my current issue.
Currently I receive in outlook a certificate error (Using EX Hybrid 2016)
Also our Outlook 2010 clients can’t connect to exchange.
2nd question:
Do I need to assign IIS service to the newest certificate?
Thanks for your help
Hi Ali, Thanks for your article, you made the life easier.
I have a hybrid exchange 365, I renewed the exchange on-prem certificate and updated the send/receive connectors, do I need to do anything else on exchange online?
I followed your article and resolved issue with send connector.
clear and Simple to follow your Instructions.
Heaps of Thank you
I just renewed my wildcard cert and added IIS and SMTP services to it. I then Reran the HCW, which if I am reading this correctly, means I can just go into Cert Mgr and delete the old cert. Do you have to run the commands to update the send and receive connectors if you run HCW and select the new cert HCW?
Hi. We are renewing Exchange 2016 SSL in a hybrid I=environment. We followed all steps but now only O365 users can’t send emails. They can only receive emails. All on-premises accounts emails are working fine. Maybe the trick is that we have a Symantec email protector who acts as a email gateway?
Thanks for good writeup.
Nice writeup! This will help a lot of exchange admins.
My two cents.
1) Running the HCW does NOT delete the old certificate, that still needs to be done manually
2) Take care of the HCW settings because they could differ from the last run (mine did!)
3) If you made a manual adjustment to the Send Connector, you have to do it again! (again, personal experience with the TlsAuthLevel\TlsDomain properties)
4) If you do not see any (valid) certs in the HCW, it seems validity checks have to be valid (visible in the ECP cert tab) AND the Root CA Type has to be 3rd Party.
Check this last part with:
Get-ExchangeCertificate | Format-List FriendlyName,Subject,CertificateDomains,Thumbprint,Services,RootCAType
Thanks for this!
Hi Ali!
Is it possible to use wildcard certificate for hybrid SMTP configuration?
Yes, that’s completely fine.
We need to do this next month. I have very little experience of certificates and not a great deal in Exchange to be honest.
We have 6 server set up load balanced. Three sites with 2 servers each.
Can I renew the cert on one server / one site without without breaking the whole system.
I’d like to take one server down, snapshot the vm. Do what we need to do on the load balancer and then test before doing it on other servers. Is this feasible at all?
Should I not get it right first time, is it easy enough to roll back to the old cert?
Very clear instructions, thank you so much!
We use letsencrypt. How should the certificate renewal process with exchange 2010 to hybrid configuration?
TLS does not appear to be enabled on the Send and Receive connector.
When I look with Get-HybridConfiguration, the thumbprint information of the last certificate that letsencrypt updated shows.
We can’t complate the Hybrid Configuration tool, but we get the error remove-organizationrelationship -i “O365 to On-premises* HCW8099 at the last stage. I think there is an authorization problem, we are trying to solve it with a ticket.
Thank you! This article solved my production issue this morning. I did not have to do the IIS Reset though.
Everything worked like a charm. Thanks for this article much appreciated mate!
Hi Ali,
Ok question how can I check if the send and receive connector are using the renewed SSL Cert?
Our SSL was renewed back in Nov 2022 and currently mail flow is working fine but when we go to delete this expired SSL we get the same error message as in this post. Now I dont know what process was followed back in Nov as the tech that did the work has left the company.
Is it ok for me to run commands from this post, even if the send connectors are already using the new SSL certificate, this wont break anything? Or becuase mail flow is working between On-Prem and O365 it i safe to just go aheead and delete the expired SSL without running the commands
Everything worked like a charm.
Keep up your good work, save me a lot of time.
Thank you.
Instead of running the HCW again for an expired hybrid cert, would just running the set-hybridconfiguration -tlscertificatename work instead? Was just curious.
Hi Ali ,
do I need to re-run commands again if I get this WARNING: The command completed successfully but no settings have been modified after deleting old certificate from MMC ???
No.
So there isnt really a need to run HCW, correct? as long as I run the ps cmdlet to bind the cert to services?
That’s correct.
as long as the subject on the cert remains the same… otherwise you need to update the receive connector
We are running Exchange Server 2016 and followed these excellent directions. Thank you. One question though is when I run Get-HybridConfiguration the tlscertificate is not updated to the new cert. Is this normal following the update of the connectors without running the HCW?
Nice write up Ali. I currently import LE certs with Import-ExchangeCertificate and the assign services using
Just wondering if that would work rather than using Set-SendConnector and Set-ReceiveConnector cmdlets?
You need to run the Set-SendConnector and Set-ReceiveConnector after enabling the Exchange Certificate.
Another way is to rerun the HCW after you run your command (shown in the article).
I am getting error while trying to rerun the HCW
Could not HTTP/S connect to host outlook.office365.com:443
When rerunning the Office 365 Hybrid Configuration Wizard, all of the settings will remain the same as when it was setup? Just click through it, with the exception of adding the new certificate in the Transport Certificate window?
Yes and no.
Most of it, yes. But I experienced myself that for example ‘Centralized mailtransport’ was unchecked, while I had it checked before.
So do take care!!
Hi Ali,
With regards SSL, do we need to keep the DigiCert webmail certificate once hybrid is gone or can we replace it with one from our own CA? So in essence once we are down to the last server, do we still need external SSL?
Thanks
If the Exchange Hybrid server is only for management purposes and there is no mail flow, you don’t need to use any certificates anymore.
I recommend not publishing the Exchange Hybrid server to the internet and removing/disabling the firewall ports from/to Exchange Server.
Read more in the article Keep last Exchange Server in organization.
I have two certificates for two different domain names on the server and in Exchange. How can I tell which certificate is currently used by the two connectors?
Thanks for this – I guess running the hybrid config wizard is the easiest and fastest way of doing this.
Is it true that if i run the hybrid configuration wizard i won’t have to manually setup the following:
– manually setup the services to the new cert (SMTP, IIS, POP, IMAP)
– manually setup the cert on the relevant connectors
– delete the old certificate
thank you!
Not true.
You have to renew the Exchange Server certificate first (which is a third-party certificate). After that, configure Exchange Hybrid to use the new certificate with PowerShell or rerun the HCW.
Hi Ali – thanks for reply! So request for .req via exchange admin centre, renew via third party. go back to exchange admin centre and complete the pending request to upload the new certificate and give it the appropriate services such as SMTP,IIS,POP,IMAP and then rerun exchange hybrid? do i need to restart IIS at any point if going by the wizard? thanks!~
That’s the correct approach.
You have to restart IIS after assigning the new third-party certificate to the services. Read more in the article How to create certificate in Exchange Server.
The changes apply when rerunning the HCW, and you don’t have to reset IIS. But, if you do see any certificate mismatches, you can apply iisreset afterward.
Thanks Ali! great write up.
Normally I get a contractor to renew our exchange SSL cert but this time I did it in house.
Thanks again.
Hi,
Do we need to update the other Receive connectors or just the Default Frontend connector in a Hybrid setup when renewing the certificate?
Only the Default Frontend recieve connector.
Thank you for the article, just one question – if you’re doing it the “manual” way is there any requirement to also use the Set-HybridConfiguration to set the TlsCertificateName property aswell?
No, the commands in the article are all you need.
Many thanks Ali.
This article was easy to follow and well put together.
Thanks Ali, highest praise!!! All your articles are well researched and quite detailed. These days whenever I need to check sth quickly about exchange, I always look if your website has it covered, no dissapointments 🙂 Keep up good work!
Hi Ali,
Thank you very much for this article. It helped me a lot.
Keep up the good work!
Kind regards
Juan
Thanks for this article and actually many of your other article on this site are excellent and have helped me.