We did configure an Exchange Hybrid configuration and now want to let the organization use…
Renew Microsoft Exchange Server Auth Certificate
The Microsoft Exchange Server Auth Certificate is installed when you install an Exchange Server, and it’s 5 years active. Most of the time, you don’t look into that certificate because, within 5 years, you will have a new Exchange Server and decommission the old Exchange Server. What if you accidentally removed the certificate, or it’s giving an error? In this article, we will look at how to renew Microsoft Exchange Server Auth Certificate and check that it’s valid.
Table of contents
- Exchange Server certificates
- Check Microsoft Exchange Server Auth Certificate
- How to renew Microsoft Exchange Server Auth Certificate
- 1. Create new Microsoft Exchange Server Auth Certificate
- 2. Set new certificate for server authentication
- 3. Restart Microsoft Exchange Service Host Service
- 4. Restart IIS (Internet Information Services)
- 5. Remove old Microsoft Exchange Server Auth Certificate
- 6. Rerun Hybrid Configuration Wizard
- 7. Verify Microsoft Exchange Server Auth Certificate validity
- Conclusion
Exchange Server certificates
There are three default certificates created when Installing Exchange Server:
- Microsoft Exchange (self-signed)
- WMSVC or WMSVC-SHA2 (depends on the Exchange Server version) (self-signed)
- Microsoft Exchange Server Auth Certificate (self-signed)
In addition to the above default self-signed certificates, you must install a third-party certificate which you obtain from a certification authority (CA) on the Exchange Server:
Check Microsoft Exchange Server Auth Certificate
Sign in to Exchange Admin Center on-premises. Navigate to servers > certificates. Select the Exchange Server if you have more than one Exchange Server running in the organization. Double-click the Microsoft Exchange Server Auth Certificate.
In our example, we did select the Exchange Server EX01-2016.
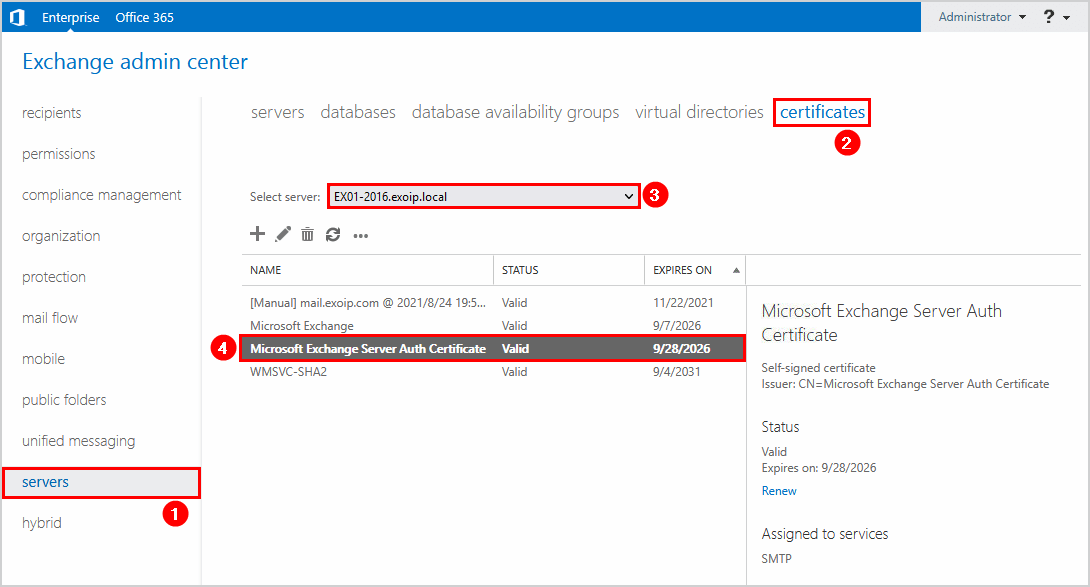
We do see that the certificate thumbprint starts with C4C595.
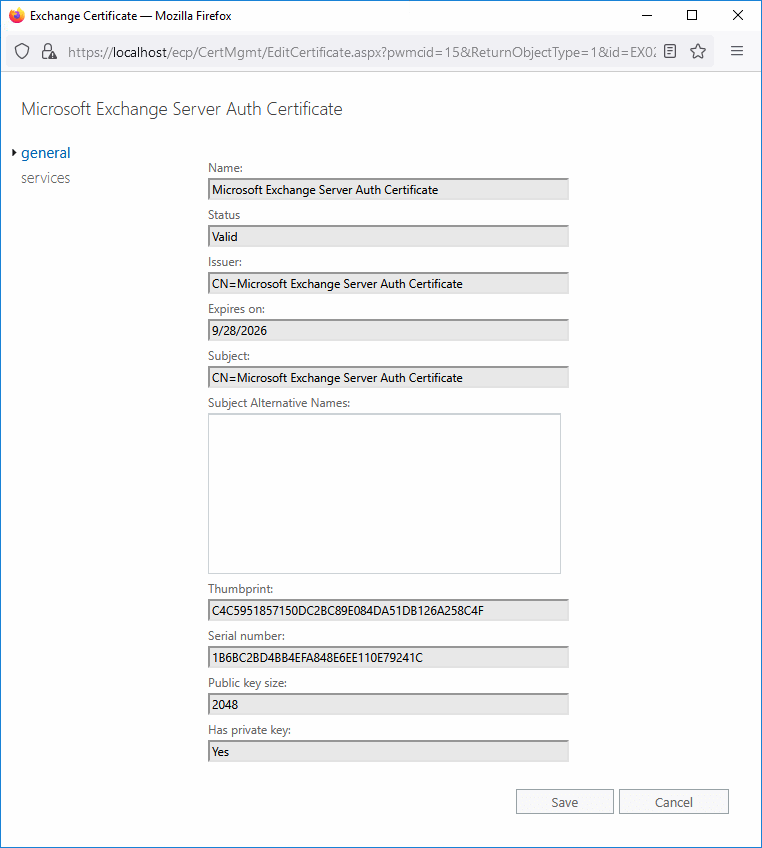
Let’s verify the Exchange Server certificate with Exchange Management Shell.
Run Exchange Management Shell as administrator on Exchange on-premises. Run the command to check the status of the existing OAuth certificate.
(Get-AuthConfig).CurrentCertificateThumbprint | Get-ExchangeCertificate | Format-ListThe below output appears.
AccessRules : {System.Security.AccessControl.CryptoKeyAccessRule,
System.Security.AccessControl.CryptoKeyAccessRule,
System.Security.AccessControl.CryptoKeyAccessRule}
CertificateDomains : {}
HasPrivateKey : True
IsSelfSigned : True
Issuer : CN=Microsoft Exchange Server Auth Certificate
NotAfter : 9/28/2026 10:25:25 PM
NotBefore : 9/28/2021 10:25:25 PM
PublicKeySize : 2048
RootCAType : None
SerialNumber : 1B6BC2BD4BB4EFA848E6EE110E79241C
Services : SMTP
Status : Valid
Subject : CN=Microsoft Exchange Server Auth Certificate
Thumbprint : C4C5951857150DC2BC89E084DA51DB126A258C4FLet’s say the Exchange Server Auth Certificate is corrupt or not valid. Perhaps you don’t see the Exchange certificate with the above steps. In the next step, we will renew the Exchange Server Auth Certificate.
How to renew Microsoft Exchange Server Auth Certificate
Let’s have a look at the steps on how to renew Microsoft Exchange Server Auth Certificate. Run the below commands in Exchange Management Shell.
Note: You can’t remove the Exchange Server Auth Certificate in most cases. That’s ok, and you will be able to remove the old certificate when you create and publish a new Exchange Server Auth Certificate.
1. Create new Microsoft Exchange Server Auth Certificate
Create a new Microsoft Exchange Server Auth Certificate. Run the New-ExchangeCertificate cmdlet.
New-ExchangeCertificate -KeySize 2048 -PrivateKeyExportable $true -SubjectName "cn=Microsoft Exchange Server Auth Certificate" -FriendlyName "Microsoft Exchange Server Auth Certificate" -DomainName @()If it asks you to overwrite the certificate that’s already there, press Y and press Enter.
Confirm
Overwrite the existing default SMTP certificate?
Current certificate: 'C4C5951857150DC2BC89E084DA51DB126A258C4F' (expires 9/28/2026 10:25:25 PM)
Replace it with certificate: '67D37D27B8D3583D5FAD32FC294E287D270E3297' (expires 9/29/2026 9:51:32 AM)
[Y] Yes [A] Yes to All [N] No [L] No to All [?] Help (default is "Y"): Y
Thumbprint Services Subject
---------- -------- -------
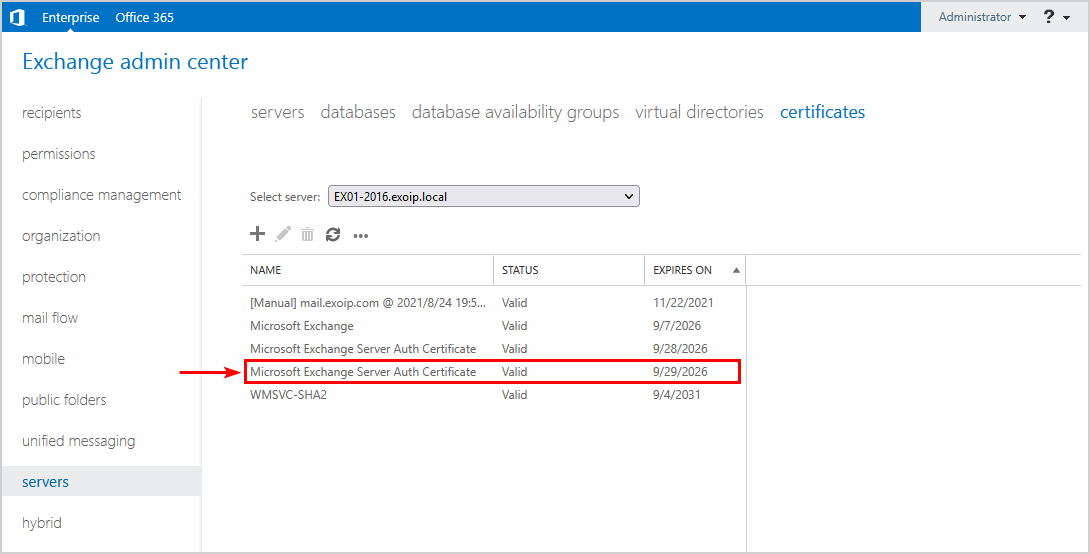
67D37D27B8D3583D5FAD32FC294E287D270E3297 ....S.. CN=Microsoft Exchange Server Auth CertificateCopy the new certificate thumbprint because you need it in the next step. In our case, it’s the certificate thumbprint that starts with 67D37D.
You can verify in Exchange Admin Center that the command created the new Microsoft Exchange Server Auth Certificate.
Note: The certificate will be created on all the Exchange Servers (if you have more than one Exchange Server running in the organization).
2. Set new certificate for server authentication
The Set-AuthConfig parameter defines Microsoft Exchange as a partner application for server-to-server authentication with other partner applications such as Microsoft SharePoint 2013 and Microsoft Lync 2013 or Skype for Business Server 2015.
Paste the certificate thumbprint which you copied in the previous step in the command.
Set-AuthConfig -NewCertificateThumbprint "67D37D27B8D3583D5FAD32FC294E287D270E3297" -NewCertificateEffectiveDate (Get-Date)If you select the current day date, you will get a warning that the new effective date is not 48 hours in the future. Press Y and press Enter.
Confirm
The new certificate effective date is not at least "48" hours in the future and may not be deployed on all necessary servers. Do you wish to continue?
[Y] Yes [A] Yes to All [N] No [L] No to All [?] Help (default is "Y"): YThe PublishCertificate switch specifies that the specified certificate be immediately rolled over as the current certificate. The certificate is deployed immediately to all Client Access servers.
Set-AuthConfig -PublishCertificateThe ClearPreviousCertificate switch clears the certificate saved as the previous certificate in the authorization configuration.
Set-AuthConfig -ClearPreviousCertificate3. Restart Microsoft Exchange Service Host Service
Restart the Microsoft Exchange Service Host Service
Restart-Service "MSExchangeServiceHost"4. Restart IIS (Internet Information Services)
Run the IISReset command to restart IIS.
iisresetAnother way is to recycle the Outlook on the web and EAC application pools.
Restart-WebAppPool "MSExchangeOWAAppPool"
Restart-WebAppPool "MSExchangeECPAppPool"5. Remove old Microsoft Exchange Server Auth Certificate
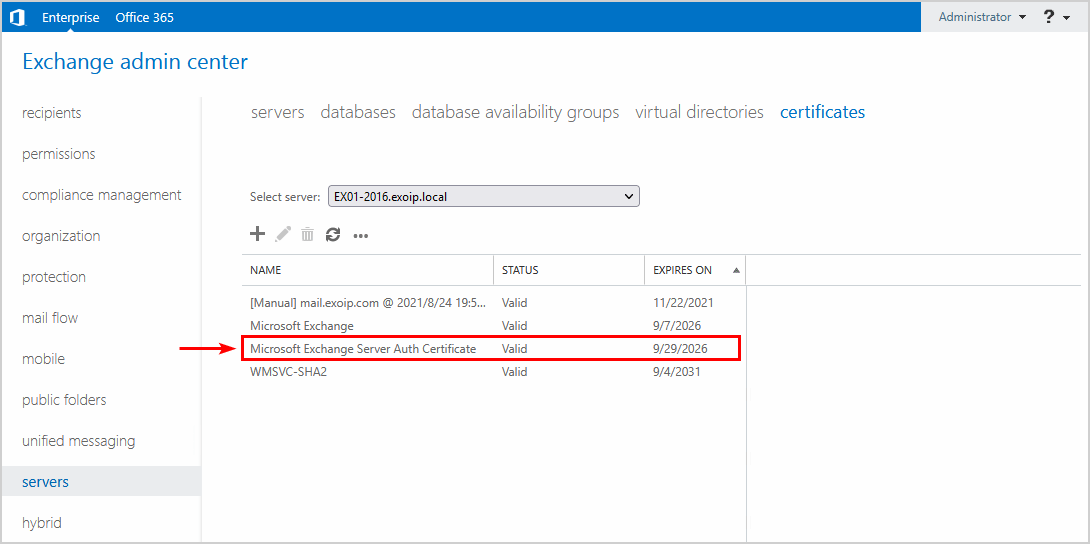
Remove old Microsoft Exchange Server Auth Certificate from Exchange Admin Center or with PowerShell.
Note: Do this on all the Exchange Servers.
You will only have one Microsoft Exchange Server Auth Certificate on each Exchange Server.
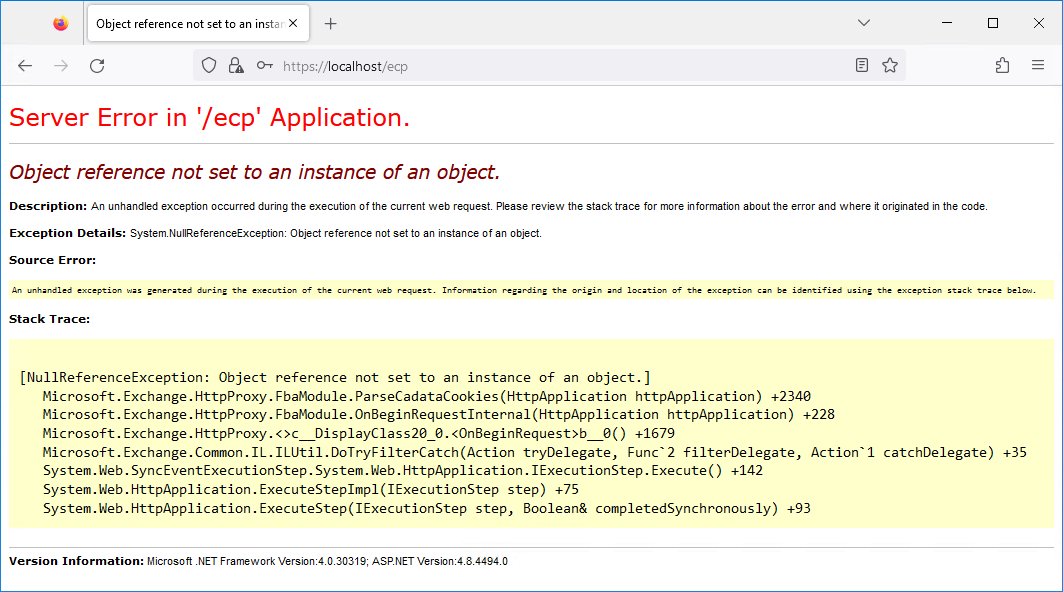
Important: In some environments, it may take a couple of hours for the OAuth certificate to be published.
An ECP error appears when you want to connect to the Exchange Admin Center. After waiting a few hours, you can successfully sign in without getting the error below.
6. Rerun Hybrid Configuration Wizard
If you have an Exchange Hybrid setup, you have to rerun the Hybrid Configuration Wizard to update the changes to Azure Active Directory (Azure AD).
7. Verify Microsoft Exchange Server Auth Certificate validity
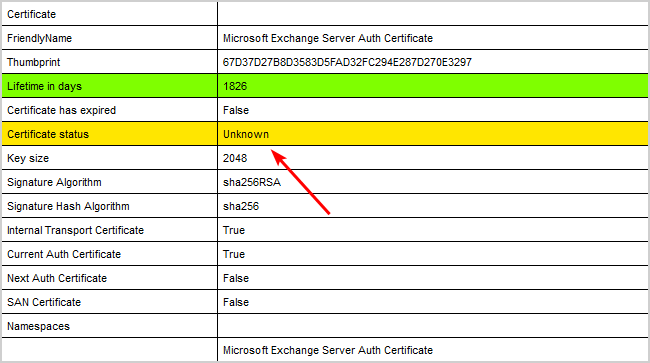
Run the Exchange Server Health Checker script to verify that the Microsoft Exchange Server Auth Certificate status is valid.
This is how it immediately looks after you install the new Exchange Auth certificate. All the certificate statuses appear as Unknown.
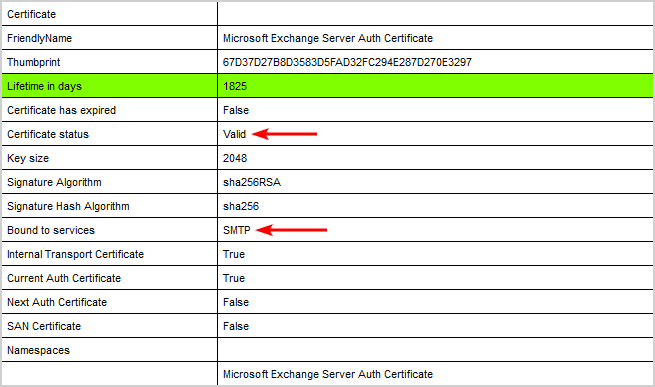
Give it a maximum of 24 hours and run the health checker script again. All the certificate statuses appear as Valid and the Microsoft Exchange Server Auth Certificate is bound to services SMTP.
That’s it!
Read more: Renew certificate in Exchange Hybrid »
Conclusion
We showed how to renew the Microsoft Exchange Server Auth Certificate. First, go through the steps as shown to renew the Auth Certificate. After that, you can remove the old Auth certificate. If you have an Exchange Hybrid deployment, rerun the Hybrid Configuration Wizard. As always, verify that the new Microsoft Exchange Server Auth Certificate is valid by running the Exchange Health Checker script.
Did you enjoy this article? You may also like Install Exchange certificate with PowerShell. Don’t forget to follow us and share this article.


Hi, I need some help after I renewed the auth cert when I run get-exchangeCertificate the result I get is empty, do I need to wait 24 hour?? Because last time when we do this it does not need that long.
Yes, you have to wait a maximum of 24 hours before the results appear.
I wrote about it in the article How to fix Get-ExchangeCertificate shows the blank output.
Question:
I have 5 Exchange 2016 servers (Non-Hybrid). I generated a new certificate on one server, but I said N to the replacement.
The new certificate shows up on the Server I created it on. Will this certificate replicate to the other 4 servers without me saying Y to the replacement portion of the command? It has been roughly 36 hours and the new certificate still does not exist on the other 4 servers.
Thanks!
If you say N to the first part (“Create new Microsoft Exchange Server Auth Certificate”) and do NOT overwrite the existing Default SMTP certificate, the new certificate will NOT replicate to other Exchange servers in the cluster. I tested this because when I created a new Auth Cert, I said NO to overwriting and let it sit for several days. It never replicated. I deleted that certifcate and created a new one, this time overwriting the Default, within 12 hours the new certificate was replicated to all server.
My hope was that I could create a new cert without overwriting, have it replicate, THEN set it to the Default and overwrite once it was in place on all servers. It will not work this way (although it might if you manually export and import on each server).
Hi Ali,
I have followed your nice procedure and HealthCheck is showing for all Certificates:
Certificate status: Unknown.
I have restarted server and have run script again and same result:
Certificate status: Unknown.
Please kindly assist, if possible.
# Version 24.03.12.1700
Give it 24 hours and rerun the Health Checker script to check again. All the certificate statuses will appear “Valid”. I updated the article.
Thanks a lot, Ali! You are the best! 😉
Now it shows all certs as Valid.
Hi Ali!
Could You tell please, if it is allowed to simply – Renew existing certificate via MMC.EXE console? Will it work in this way?
Checked via MMC – it is not possible for Self-signed certificate. So, need to follow Ali’s procedure.
Hi Ali
You well deserve a good reputation that you have built for yourself and thank you for your useful and inclusive articles.
Regarding the steps you provided to “Renew Microsoft Exchange Server Auth Certificate” though, we were originally planning to re-run HCW at the end when the customer advised their re-running HCW in their exchange environment (Classic Hybrid with Exchange 2013) is known to fail and they rather not have to run that for this Cert renewal. I found in one of the comments here what I had found in a reddit article that to work around having to run HCW, we can instead follow step 3 and 4 from https://learn.microsoft.com/en-us/exchange/configure-oauth-authentication-between-exchange-and-exchange-online-organizations-exchange-2013-help#step-3-export-the-on-premises-authorization-certificate
And I didn’t see your comment on that. I was wondering if you approve of such approach and if not what would be the consequence of not running HCW at all in this scenario?
Hi Ali,
Thank you for the excellent post.
Current Status:
I am in hybrid mode with 2 relay servers. Currently, all services are running on the SAN certificate, including IMAP, POP, IIS, and SMTP. The current “Microsoft Exchange Server Auth Certificate” is used for the SMTP service.
The “Microsoft Exchange Server Auth Certificate” cert will expire an month after my SAN cert gets renewed.
Question 1: Can I renew the “Microsoft Exchange Server Auth Certificate” for 5 years by adding “(Get-Date).AddYears(5)” to the command in the post? The command in the post will renew it for 24 hours.
New-ExchangeCertificate -KeySize 2048 -PrivateKeyExportable $true -SubjectName “cn=Microsoft Exchange Server Auth Certificate” -FriendlyName “Microsoft Exchange Server Auth Certificate” -DomainName @() -NotAfter (Get-Date).AddYears(5)
Question 2: When renewing the “Microsoft Exchange Server Auth Certificate,” will it take over the SAN services for SMTP, or will it just go on top of the existing certificate?
Question 3: Do I have to run the hybrid config wizard? The reason I am asking is that I checked Exchange Online 365, and the connectors inbound and outbound are pointing to the SAN certificate. I verified this by running the following commands:
Connect-ExchangeOnline
Get-OutboundConnector “Outbound” | Format-List
Get-InboundConnector “Inbound” | Format-List
Please let me know your thoughts and recommendations.
Best regards,
1. Run the command shown in the article, and it will set the Auth certificate expiration date to 5 years.
2. No, it will not take over your SAN certificate.
3. Yes, rerun the HCW so it will replace the Auth certificate in Microsoft Entra ID. It has nothing to do with your SAN certificate.
Hi Ali thank you for your responds! can I get your comment on #3 please.
Currently: in my environment the 3part SAN cert is set for transport.
1- thats good then, I just run the command it will do a 5 year cert
2- I am good!
3- Need more information : “Do we still need to run the HCW after updating the internal certificate, specifically the ‘Microsoft Exchange Server Auth Certificate,’ even though we are using a third-party SAN certificate for the ‘Transport Certificate’?”
You’re welcome, Rob.
3. Yes.
Great article from you, as always. Thank you very much.
Hi Ali,
I used the renew option on EAC for this certificate…everything seems like it is working but I get an alert when I log into the EAC
The Certificate ” on server EX01 has expired. View Details
It takes me to the certificate page and shows the certificate as valid.
Hi Ali, love your work. Since i have a cluster with 2 exchange servers, do i run this on each server or just 1?
Only on one Exchange Server. The certificate will replicate on the other Exchange Server.
Dear Mr Ali,
Thanks for the great article,
We are doing migration from 2016 dag to 2019 dag in same domain but in different sites, we are started migrating the mailboxes, but as noticed now Exchange Auth Certificate is about to expire.
So the question is if we renew Auth Certficate at 2016 ( since mail flow is still from 2016 as migration is going on) and publish, so will it be replicated at 2019 dag Client access servers as well? If not then what should we do either export or import or any work around?
Hello Ali .. Thank you for helping us to know how to update the Federation Certificate in Exchange 2016 hybrid environment, very kind.
Hello Ali ,
I try to generate new Microsoft exchange server Auth certificate with this command : >New-ExchangeCertificate -KeySize 2048 -PrivateKeyExportable $true -SubjectName “cn=Microsoft Exchange Server Auth Certificate” -FriendlyName “Microsoft Exchange Server Auth Certificate” -DomainName @()
But i ran into this issue : A special Rpc error occurs on server : Access is denied
Note : the user login is admin and I run exchange management shell as administrator
please need help
You will need to right click and run the shell as “Administrator”
The AD user needs to be part of the management role/group for exchange servers.
Ali,
thanks for the amazing detailed step by step doc.
Hi Ali,
When I try to renew the Exchange server auth certificate using the command New-ExchangeCertificate -KeySize 2048 -PrivateKeyExportable $true -SubjectName “cn=Microsoft Exchange Server Auth Certificate” …. it gives the thumbprint of the exchange server certificate as default SMTP instead of the Exchange Server Auth Certificate. Now how can I renew the exchange server auth certificate. How the exchange server certificate became the default SMTP in my exchange server?.
This can happen and is completely normal.
You must assign the Exchange Server Auth Certificate to the Exchange Server SMTP service with PowerShell. It’s not possible to do it through the Exchange admin center because the SMTP service is most likely greyed out.
1. Assign the Exchange Server Auth Certificate to the Exchange Server SMTP service with PowerShell.
2. Set the new Exchange Server Auth Certificate, and it will recognize the old Exchange Server Auth Certificate when asking if you want to overwrite it.
Proceed further with the steps in the article.
Many thanks for your reply Ali,
Any logs that I can look at to confirm the “Microsoft Exchange Server Auth Certificate” renewal done successfully.
At the “Overwrite the existing default SMTP certificate?” step, I chose “No” because it asked do you want to replace current SMTP certificate bec I already have a cert for SMTP..will this affect anything?
You have to go through this step, and it’s safe.
Verify the current and new certificate thumbprints that are shown in the output. They both need to be Microsoft Auth certificates and not any other certificate.
Hi Ali,
I renewed the Auth Certificate and was going with the HCW rerun. Once I got to the Transport certificate selection, I got only one cert available. the WNsvc-something.
I’m missing my SSL wildcard certificate that I previously used to setup hybrid. It’s valid and visible from the Exchange shell and GUI. It was visible about 3 weeks ago in HCW when I had to rerun the wizard before the renewal.
Is there a way to get around this problem?
Does the replace of the certificate affect share point on prem or Skype for business on prem ?
Hi Ali, Good Post, in my case i have a DAG environment with two servers, on that case i should do the process in one server and export the certificate to the another one? or apply the the process in both servers?
i see that the thumbprint of the expired certificate is the same in both servers
Create the Microsoft Exchange Server Auth Certificate on one Exchange Server, and it will automatically be available on all the other Exchange Servers.
Hi Ali
Thank you for this detailed procedure.
Thanks, Ali, this was super helpful! Big respect mate.
Helped me a lot! Thank you very much for your great explanation!
Ali, your documentation is way better than anything provided on Microsoft’s site – THANK YOU!
Any chance you have one for the “Exchange Delegation Federation” Certificate Renewal?
The Microsoft Documentation has a different Subject name, using “Microsoft Federation Gateway” (Exchange 2013) and we have “Exchange Delegation Federation” (Exchange 2016):
https://learn.microsoft.com/en-us/exchange/renew-the-federation-certificate-exchange-2013-help#replace-an-expired-federation-certificate
Don’t run the hybrid wizard if you have made changes to for example your send-connectors regarding Office 365 mail flow. The wizard will just create the default and remove the custom changes you made.
Instead follow step 3 and 4 from https://learn.microsoft.com/en-us/exchange/configure-oauth-authentication-between-exchange-and-exchange-online-organizations-exchange-2013-help#step-3-export-the-on-premises-authorization-certificate
Great tutorial Ali
How do I have only one Microsoft Exchange Server Auth Certificate as for now I have 3 of them and the server doesn’t like the main certificate
Hi Jean,
Follow the article to create a new Microsoft Exchange Server Auth Certificate. After that, remove the old Microsoft Exchange Server Auth Certificates.
Hello Ali,
thank you very much for your courses , they are awesome 🙂
I have a Wildcard certificate and i want to renew it.
Since I use this certificate for the whole Organization, assuming that I make the certificate request through another server, how do you think I should renew the certificate in the most error-free way?
According to my research, i have to first delete my old certificate and import my new certificate and assign the services…
Thank you advance for your advices
Best regards
Hi Emre,
Glad that you like the courses.
1. Make a backup of the old certificate
2. Import the new certificate
3. Specify the Exchange services that you want to assign this new certificate to
4. Remove the old certificate
You can use these articles:
– How to export certificate in Exchange Server
– How to import certificate in Exchange Server
If it’s an Exchange Hybrid, you also need to update the send connector and receive connector. More on that in the article: Renew certificate in Exchange Hybrid.
Hi Ali,
thank you very much for four advices, i will do it.
But if I want to assign IIS service after importing the new certificate, I think I will have a problem. I cannot assign IIS to two certificates at the same time, even temporarily. I guess I should unassign the IIS service from the old certificate first.
When you assign the services to the new certificate, it will overwrite the old certificate. That’s how it works.
Ensure that you apply the changes from Exchange Management Shell or Exchange Admin Center and not directly from Internet Information Services (IIS) Manager.
Ali rocks!
Hi,ALI,I found that after running the New-ExchangeCertificate command on exchange01, only after the certificate was generated in exchange01, and after performing the following steps, it was prompted that the fingerprint was not found in exchange02.
~thanks Mate. its very usefull. i was stuck for last one day on this issue. Thanks its resolved now.
Appreciated.
Thanks for your detailed explanation. Your knowledge is mind-blowing.
Thanks for your remarkable Help always.. 🙂
Thanks for the excellent explanation again Ali!
This is very helpful!
Greetz from Cor
You’re welcome, Cor. Glad that you find it helpful.