How to set up mount points for Exchange Server? Mount points is a feature in…
Configure Extended Protection in Exchange Server
Many environments have not yet enabled Extended Protection in Exchange Server. While it’s possible for them to enable Extended Protection, they are not aware or informed correctly that they should enable it for security reasons. In this article, you will learn how to configure Extended Protection in Exchange Server.
Table of contents
What is Extended Protection?
Windows Extended Protection enhances the existing authentication in Windows Server and mitigates authentication relay or “man in the middle” (MitM) attacks. This mitigation is accomplished by using security information that is implemented through Channel-binding information specified through a Channel Binding Token (CBT), which is primarily used for SSL connections.
While Extended Protection can be enabled manually on each virtual directory, Microsoft provided the ExchangeExtendedProtectionManagement.ps1 PowerShell script to help accomplish this in bulk.
There are some limitations to be aware of before enabling Extended Protection on Exchange Server. Therefore, you must review the Microsoft documentation (which is kept up to date) and check if you are eligible.
Windows Extended Protection is supported on the below Exchange Server versions:
- Exchange Server 2013
- Exchange Server 2016
- Exchange Server 2019
Note: You need the August 2022 Exchange Server Security Update (SU) release or later installed on the Exchange Server.
Important: Remember to keep the Exchange Server up to date with the latest Exchange Cumulative Update and Exchange Security Update. Subscribe to the newsletter, and don’t miss out on the Exchange Server updates.
Check Extended Protection status
We recommend two methods to check the Extended Protection status on Exchange Server.
Method 1. Exchange Health Checker script
Run the Exchange Health Checker script and create an Exchange Server Health Check report. This will tell you if Extended Protection is enabled on the Exchange Server.
[PS] C:\scripts>Get-ExchangeServer | ?{$_.AdminDisplayVersion -Match "^Version 15"} | .\HealthChecker.ps1; .\HealthChecker.ps1 -BuildHtmlServersReport -HtmlReportFile "ExchangeAllServersReport.html"; .\ExchangeAllServersReport.htmlExtended Protection is not enabled on the Exchange Server, and it shows the security vulnerabilities:
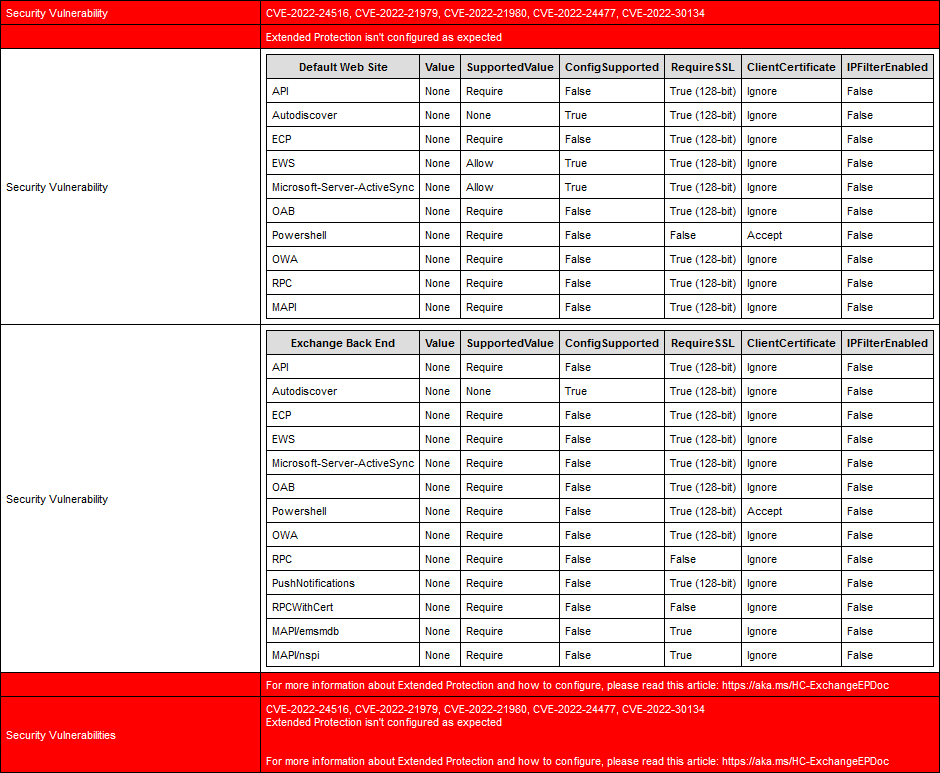
Method 2. Exchange Extended Protection Management PowerShell script
Download ExchangeExtendedProtectionManagement.ps1 PowerShell script and save it in the C:\scripts folder.
Run Exchange Management Shell as administrator and run the script, including the -ShowExtendedProtection parameter.
The Value and SupportedValue column should be the same values.
In our example, the Value column shows None for all the virtual directories, which means that Extended Protection is not enabled on the Exchange Server.
[PS] C:\>C:\scripts\.\ExchangeExtendedProtectionManagement.ps1 -ShowExtendedProtection
Version 23.05.04.2151
Results for Server: EX01-2019
Default Web Site Value SupportedValue ConfigSupported RequireSSL ClientCertificate IPFilterEnabled
---------------- ----- -------------- --------------- ---------- ----------------- ---------------
API None Require False True (128-bit) Ignore False
Autodiscover None None True True (128-bit) Ignore False
ECP None Require False True (128-bit) Ignore False
EWS None Allow True True (128-bit) Ignore False
Microsoft-Server-ActiveSync None Allow True True (128-bit) Ignore False
OAB None Require False True (128-bit) Ignore False
Powershell None Require False False Accept False
OWA None Require False True (128-bit) Ignore False
RPC None Require False False Ignore False
MAPI None Require False True (128-bit) Ignore False
Exchange Back End Value SupportedValue ConfigSupported RequireSSL ClientCertificate IPFilterEnabled
----------------- ----- -------------- --------------- ---------- ----------------- ---------------
API None Require False True (128-bit) Ignore False
Autodiscover None None True True (128-bit) Ignore False
ECP None Require False True (128-bit) Ignore False
EWS None Require False True (128-bit) Ignore False
Microsoft-Server-ActiveSync None Require False True (128-bit) Ignore False
OAB None Require False True (128-bit) Ignore False
Powershell None Require False True (128-bit) Accept False
OWA None Require False True (128-bit) Ignore False
RPC None Require False False Ignore False
PushNotifications None Require False True (128-bit) Ignore False
RPCWithCert None Require False False Ignore False
MAPI/emsmdb None Require False True Ignore False
MAPI/nspi None Require False True Ignore FalseIn the next step, we will enable Extended Protection on the Exchange Server.
How to enable Exchange Server Extended Protection
Go through the below steps to enable Extended Protection on the Exchange Server.
Important: Do the steps after working hours, even with a DAG configuration. That’s because you need to ensure that Outlook clients can connect successfully after the change.
1. Update to the latest Exchange Server CU/SU.
2. Configure Exchange Server TLS settings.
3. Disable SSL Offloading for Outlook Anywhere.
SSL offloading for Outlook Anywhere is enabled by default and must be disabled for Extended Protection.
[PS] C:>Set-OutlookAnywhere "EX01-2019\RPC (Default Web Site)" -SSLOffloading $false4. Download ExchangeExtendedProtectionManagement.ps1 PowerShell script and save it in the C:\scripts folder.
5. Ensure that the admin is added to the Organization Management group.
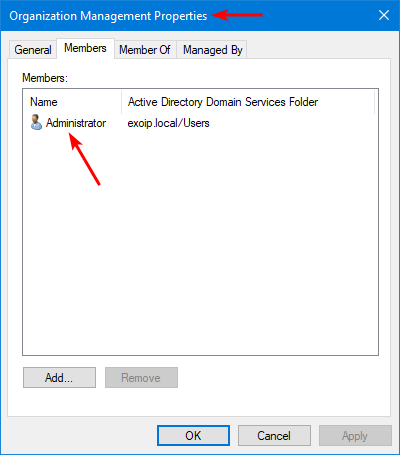
Note: The user must be in Organization Management and must run this script from an elevated Exchange Management Shell (EMS) command prompt. After adding the user to the Organization Management group, sign off and sign in again to have the changes take effect.
6. Change the path directory to the scripts folder and run the PowerShell script to enable Extended Protection on Exchange Server.
[PS] C:\>cd C:\scripts
[PS] C:\scripts>.\ExchangeExtendedProtectionManagement.ps17. The output will show information about enabling Extended Protection. Press Y and Enter.
Version 23.05.04.2151
Enabling Extended Protection
Extended Protection is recommended to be enabled for security reasons. Known Issues: Following scenarios will not work
when Extended Protection is enabled.
- SSL offloading or SSL termination via Layer 7 load balancing.
- Exchange Hybrid Features if using Modern Hybrid.
- Access to Public folders on Exchange 2013 Servers.
You can find more information on: https://aka.ms/ExchangeEPDoc. Do you want to proceed?
[Y] Yes [A] Yes to All [N] No [L] No to All [S] Suspend [?] Help (default is "Y"): Y8. The script will process the prerequisites tasks, create a backup for applicationHost.config, and configure Extended Protection.
The following servers have the TLS Configuration below
EX01-2019
RegistryName Location Value
------------ -------- -----
SchUseStrongCrypto SOFTWARE\Microsoft\.NETFramework\v2.0.50727 1
SystemTlsVersions SOFTWARE\Microsoft\.NETFramework\v2.0.50727 1
SchUseStrongCrypto SOFTWARE\Microsoft\.NETFramework\v4.0.30319 1
SystemTlsVersions SOFTWARE\Microsoft\.NETFramework\v4.0.30319 1
SchUseStrongCrypto SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v2.0.50727 1
SystemTlsVersions SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v2.0.50727 1
SchUseStrongCrypto SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v4.0.30319 1
SystemTlsVersions SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v4.0.30319 1
DisabledByDefault SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client 1
Enabled SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client 0
DisabledByDefault SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server 1
Enabled SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server 0
DisabledByDefault SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client 1
Enabled SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client 0
DisabledByDefault SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server 1
Enabled SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server 0
DisabledByDefault SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client 0
Enabled SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client 1
DisabledByDefault SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server 0
Enabled SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server 1
TLS prerequisites check successfully passed!
All servers that we are trying to currently configure for Extended Protection have RPC (Default Web Site) set to false for SSLOffloading.
EX01-2019: Backing up applicationHost.config.
EX01-2019: Successful backup to C:\Windows\System32\inetSrv\config\applicationHost.cep.20230505220519.bak
EX01-2019: Successfully updated applicationHost.config.
Successfully enabled Extended Protection: EX01-2019
Do you have feedback regarding the script? Please email ExToolsFeedback@microsoft.com.Extended Protection is successfully enabled.
Verify Extended Protection enabled status
Ensure everything is set correctly and create a new Exchange Server Health Check report.
There are no more Security vulnerabilities for Extended Protection. It shows Extended Protection Enabled (Any VDir) with the value True.
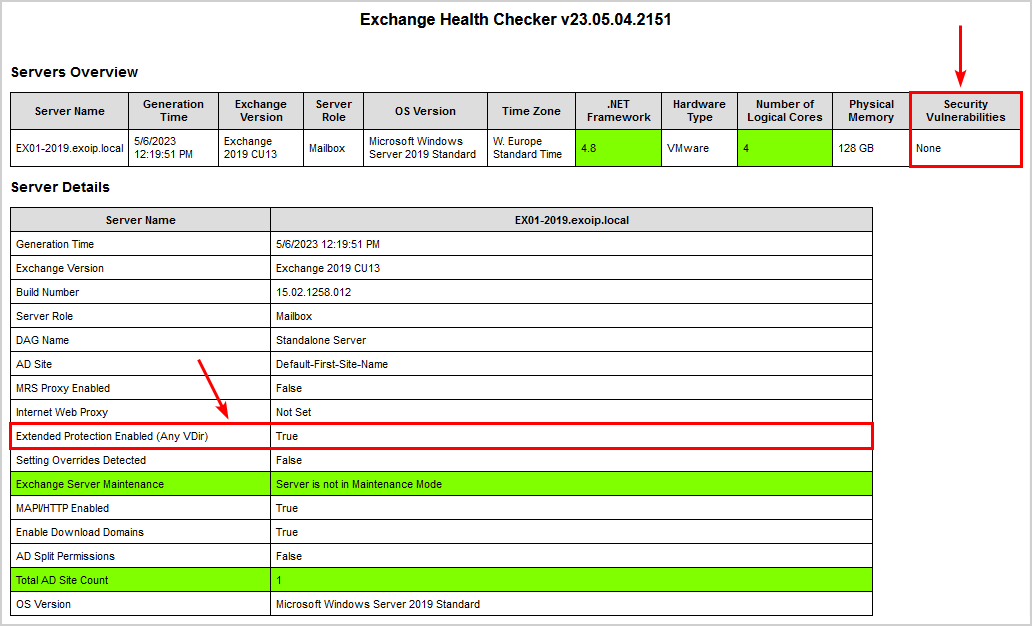
Another way is to check it with the PowerShell script. This is how it looks.
The Value and SupportedValue column shows the same values. This means that Extended Protection is enabled on the Exchange Server.
[PS] C:\>C:\scripts\.\ExchangeExtendedProtectionManagement.ps1 -ShowExtendedProtection
Version 23.05.04.2151
Results for Server: EX01-2019
Default Web Site Value SupportedValue ConfigSupported RequireSSL ClientCertificate IPFilterEnabled
---------------- ----- -------------- --------------- ---------- ----------------- ---------------
API Require Require True True (128-bit) Ignore False
Autodiscover None None True True (128-bit) Ignore False
ECP Require Require True True (128-bit) Ignore False
EWS Allow Allow True True (128-bit) Ignore False
Microsoft-Server-ActiveSync Allow Allow True True (128-bit) Ignore False
OAB Require Require True True (128-bit) Ignore False
Powershell Require Require True False Accept False
OWA Require Require True True (128-bit) Ignore False
RPC Require Require True True (128-bit) Ignore False
MAPI Require Require True True (128-bit) Ignore False
Exchange Back End Value SupportedValue ConfigSupported RequireSSL ClientCertificate IPFilterEnabled
----------------- ----- -------------- --------------- ---------- ----------------- ---------------
API Require Require True True (128-bit) Ignore False
Autodiscover None None True True (128-bit) Ignore False
ECP Require Require True True (128-bit) Ignore False
EWS Require Require True True (128-bit) Ignore False
Microsoft-Server-ActiveSync Require Require True True (128-bit) Ignore False
OAB Require Require True True (128-bit) Ignore False
Powershell Require Require True True (128-bit) Accept False
OWA Require Require True True (128-bit) Ignore False
RPC Require Require True True (128-bit) Ignore False
PushNotifications Require Require True True (128-bit) Ignore False
RPCWithCert Require Require True True (128-bit) Ignore False
MAPI/emsmdb Require Require True True (128-bit) Ignore False
MAPI/nspi Require Require True True (128-bit) Ignore False
Extended Protection is successfully configured on the Exchange Server.
Rollback Exchange Extended Protection
This syntax rolls back the Extended Protection configuration for all the Exchange Servers that are online where Extended Protection was previously configured.
[PS] C:\scripts>.\ExchangeExtendedProtectionManagement.ps1 -RollbackType "RestoreIISAppConfig"This syntax rolls back the Extended Protection mitigation of IP restriction for the EWS Backend virtual directory of all the Exchange Server that are online where Extended Protection was previously configured.
[PS] C:\scripts>.\ExchangeExtendedProtectionManagement.ps1 -RollbackType "RestrictTypeEWSBackend"That’s it!
Read more: Enable PowerShell serialization payload signing in Exchange Server »
Conclusion
You learned how to configure Extended Protection in Exchange Server. First, ensure that the prerequisites are met. Next, run the PowerShell script. The script will tell you if there is a missing configuration and will abort. If everything looks good, it will enable Extended Protection on all the virtual directories. Suppose you have issues, it’s easy to revert the Extended Protection changes with the PowerShell script.
Did you enjoy this article? You may also like Limit access to/from port 25 on Exchange Server. Don’t forget to follow us and share this article.


Hi Ali,
How to best practice enable Extend Protection on DAG Server? need all server state on Maintenance Mode? in my experience, When enable Extend protection in server 1 then i see configuration [extend protection] running on all server [organization level].
Same problem , outlook clients wont conect to server . How to disable or proper configure this ?
Hi,
Before switching to CU14, we were using a business application for which a service account had the applicationimpersonation role in exchange and could create appointments in users’ calendars. Since CU14, this no longer works. I’ve certainly missed something, so does the activation of extended protection via the CU14 installation no longer provide for this use of the applicationimpersonation role?
Thank you very much.
Is someone facing issues accessing Exchange Web Services (EWS) with error 401? Ever since I activated Extension Protection, whenever I try to access EWS, it prompts for authentication and does not accept it, returning error 401.
I have Exchange 2016 on-premises.
Did you figure this out?
we also facing 401 on EWS after updating Exchange 2019 to CU14
As SSL offloading is not supported when you enable extended protection, it is advisable to check the antivirus software installed on your clients. Some antivirus programs have encrypted connection scanning that performs SSL termination on clients. In my case, I excluded autodiscover.example.com and yourexchange.example.com, and this solved the problem.
Since I have activated Exchange Extended Protection, Outlook (Outlook 2013, 2019 and Office365) cannot be started at random intervals. The error message “Microsoft Outlook cannot be started. The Outlook window cannot be opened. This folder group cannot be opened. Error logging on to Microsoft Exchange”
Extended Protection has been set up exactly as described. Health Check was performed, TLS was adjusted,…
I would be very grateful for your help.
Thanks ALI,
nice post.
Do you know why with “Set-OrganizationConfig -EnableDownloadDomains $true” all previews for images and Office documents works and PDF file preview is not more available?
Thanks and have a good one!
Paolo Caparrelli
GOLINE SA
I enabled Extended Protection and everything works fine on Exchange 2016. No issues with Outlook clients.
I should have listened and enabled this when you told us. Right now I finally did it. Love the work you do, Ali!
In our Setup Exchange uses 2 different Certificates:
Cert 1: From internal PKI. It is used on both Exchange servers and internal load balancers. This part is supported as I ubderstand.
Cert 2: From external public CA: It is used on the external access to OWA.
Will external users still be able to use OWA, that uses another certificate?
enabling windows extended protection, didnt work, after doiing it, we had several outlook clients where came the famous popup with authentication und client could not start outlook anymore.
with rollback, it works again
i dont know exactly what is wrong, perhaps something with NTLM , i suppose (old ntlm v1 not working with extended protection)
if someone have ideas, or already have this case, thank for hint
pierre
Which version of Outlook experienced the issue?
Check the Outlook connection by using CTRL+R-click on the Outlook icon in the Notification Center (by the clock, lower-right) selecting “Connection Status…”.
The Outlook Connection Status should be helpful in troubleshooting. I can’t remember the details, but I think there was an issue with some Connection Protocols.
One person reported:
“I found the cause of the password prompt in Outlook was one setting in our AV. Once I disabled “encrypted connections scanning” the problem went away.”
https://www.reddit.com/r/exchangeserver/comments/y7n21m/i_applied_the_extended_protection_script_and/
Are you running a single server, or a DAG?
Did you check Event Viewer logs on the client and Exchange server(s) while troubleshooting the issue?