You have a subscription for Azure AD Premium, and you want to take full advantage…
Configure Microsoft Entra Password Protection for on-premises
Microsoft Entra Password Protection is excellent when you want to protect the organization from weak user passwords. That’s because Microsoft constantly analyzes Microsoft Entra security telemetry data looking for commonly used weak or compromised passwords, and maintains a list of globally banned passwords. In this article, you will learn how to configure and enable Microsoft Entra Password Protection for Active Directory on-premises to prevent weak passwords from being used in the organization.
Table of contents
- Introduction
- Microsoft Entra Password Protection
- Microsoft Entra Password Protection license
- Microsoft Entra Password Protection diagram
- How to configure Microsoft Entra Password Protection
- Enable Microsoft Entra password writeback
- Download Microsoft Entra Password Protection required software
- Microsoft Entra Password Protection proxy service prerequisites
- Install and configure Microsoft Entra Password Protection proxy service
- Microsoft Entra Password Protection Audit mode
- Microsoft Entra Password Protection DC agent prerequisites
- Install Microsoft Entra Password Protection DC agent service
- Verify Microsoft Entra Password Protection Audit mode
- Microsoft Entra Password Protection summary report
- Enforce Microsoft Entra Password Protection
- Verify Microsoft Entra Password Protection Enforce mode
- Conclusion
Introduction
In Active Directory, you can enable GPOs that can help you to implement strong passwords in the organization, like:
- Minimum password length
- Minimum password age
- Maximum password age
- Password must meet complexity requirements
- Enforce password history
That doesn’t mean you protect the organization against attacks because administrators and users can create weak passwords, known as well-known passwords, which you don’t want!
There are thousands of well-known passwords that users use daily. Some well-known passwords are:
- Welcome01!
- P@ssw0rd1234
- FerrariRed!@
That’s when Microsoft Entra Password Protection is an excellent feature to deploy in Microsoft Entra ID and on-premises AD. So let’s learn a little bit more about that.
Microsoft Entra Password Protection
Many security guidelines recommend that you don’t use the same password in multiple places, make it complex, and avoid simple passwords like Password123. You can provide your users with guidance on how to choose passwords, but weak or insecure passwords are often still used.
Microsoft Entra Password Protection detects and blocks known weak passwords and their variants. It can also block additional weak terms that are specific to your organization.
Microsoft Entra Password Protection license
See the table below for Microsoft Entra Password Protection licensing.
| Users | Microsoft Entra Password Protection with global banned password list | Microsoft Entra Password Protection with custom banned password list |
|---|---|---|
| Cloud-only users | Microsoft Entra ID Free | Microsoft Entra ID P1 or P2 |
| Users synchronized from on-premises AD DS | Microsoft Entra ID P1 or P2 | Microsoft Entra ID P1 or P2 |
You need Microsoft Entra ID P1 or P2 for users synchronized from on-premises Active Directory Domain Services (AD DS) to work.
Microsoft Entra Password Protection diagram
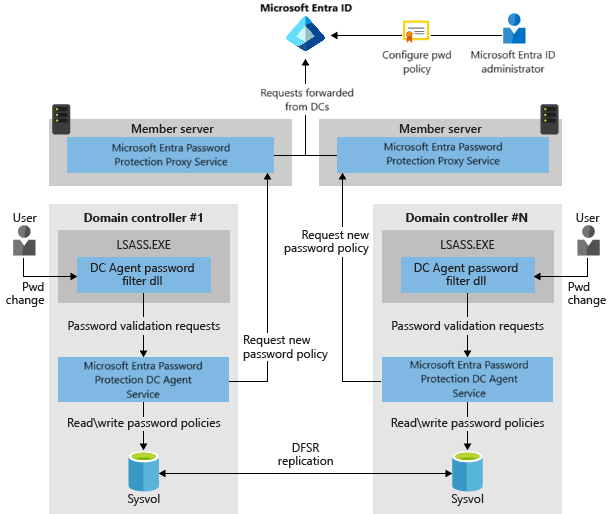
The following diagram shows how the basic components of Microsoft Entra Password Protection work together in an on-premises Active Directory environment.
- A user requests a password change to a Domain Controller.
- The DC Agent password filter dll receives the password validation requests from the OS and forwards them to the Microsoft Entra Password Protection DC Agent Service, installed on the DC. This Agent then validates if the password complies with the locally stored password policy.
- The Agent on the DC every 1 hour locates via the SCP (Service Connection Point) in the forest the Microsoft Entra Password Protection Proxy Service to download a fresh password policy copy from Microsoft Entra ID.
- The Agent on the DC receives the new password policy version from Microsoft Entra through the proxy service and stores it in the Sysvol, enabling this new policy to replicate to all other DCs in the same domain.
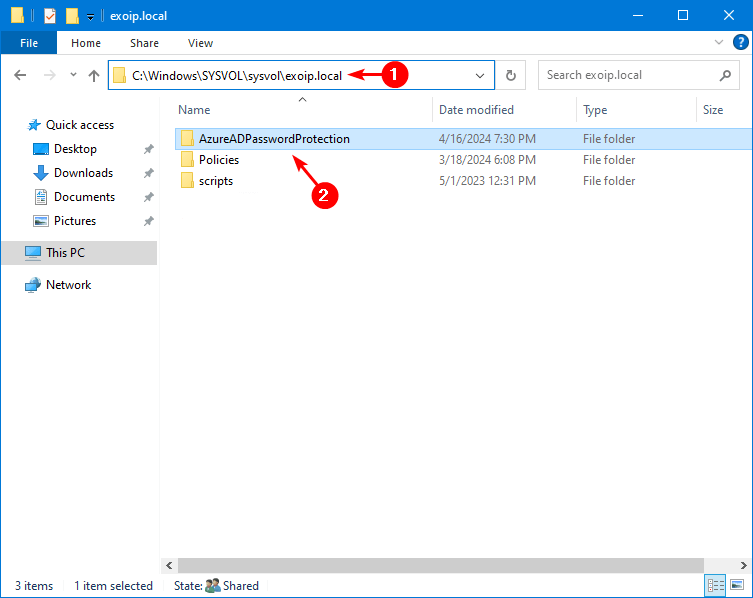
The Microsoft Entra Password Protection policies are stored in Sysvol.
How to configure Microsoft Entra Password Protection
We will go through the steps below and ensure that everything is in place before we enable Microsoft Entra Password Protection for on-premises Active Directory.
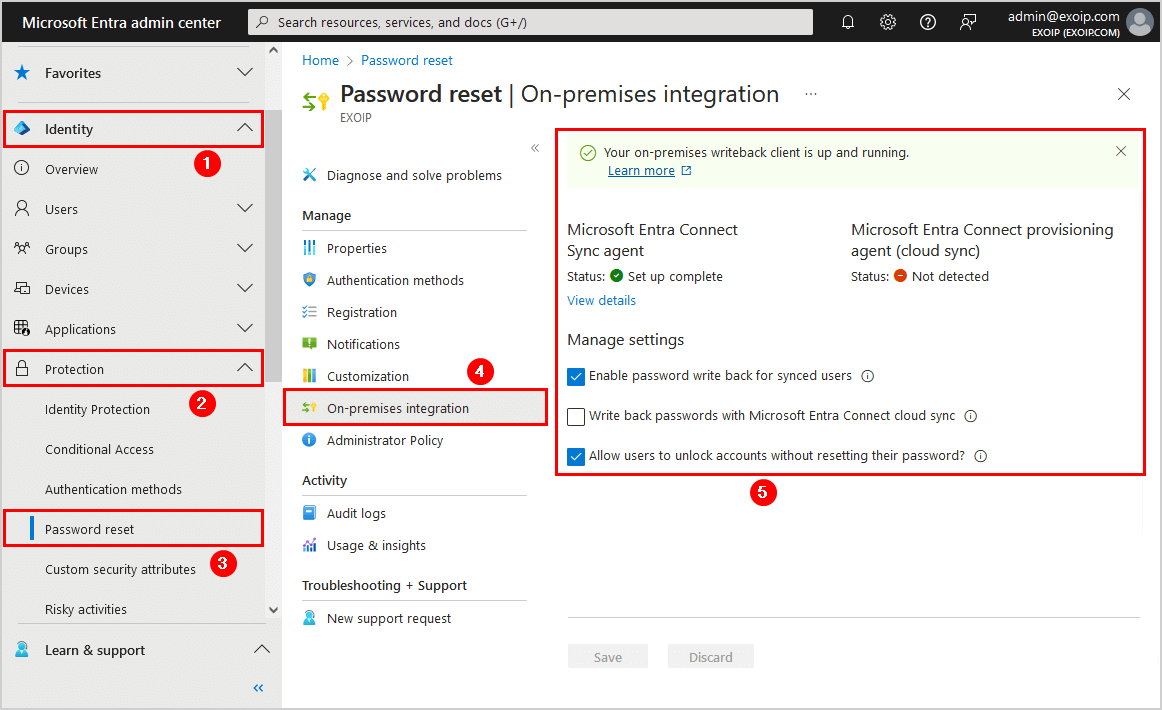
Enable Microsoft Entra password writeback
Read more in the article: Enable Self-Service Password Reset.
Ensure that you see the message Your on-premises writeback client is up and running and that the feature Enable password write back for synced users is enabled.
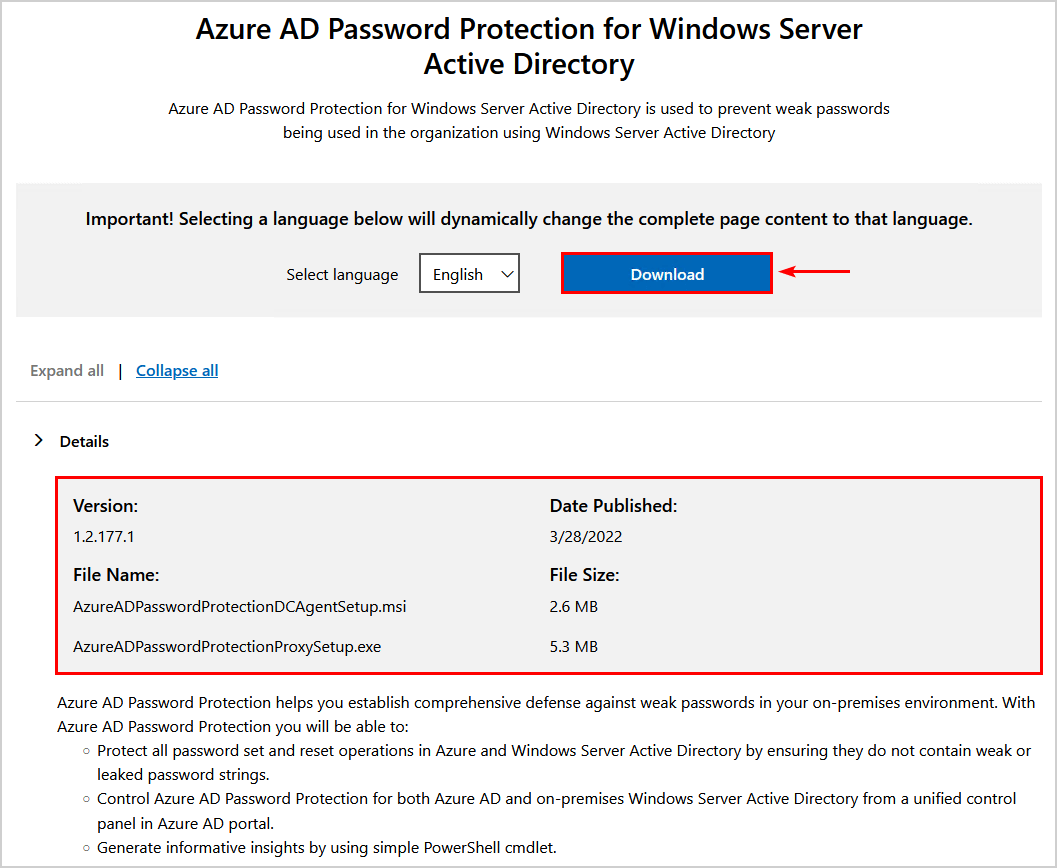
Download Microsoft Entra Password Protection required software
There are two required installers for an on-premises Microsoft Entra Password Protection deployment:
- Microsoft Entra Password Protection proxy (AzureADPasswordProtectionProxySetup.msi)
- Microsoft Entra Password Protection DC agent (AzureADPasswordProtectionDCAgentSetup.msi)
Download both installers from the Microsoft Download Center.
Now that we have both the required installers, we can go to the next step.
Microsoft Entra Password Protection proxy service prerequisites
The following requirements apply to the Microsoft Entra Password Protection proxy service:
- Windows Server 2012 R2 or later.
- .NET 4.7.2 installed or higher.
- Do not install on a RODC (Read-Only Domain Controller).
- Allow outbound TLS 1.2 HTTP traffic.
- A Global Administrator account is required to register the Microsoft Entra Password Protection proxy service for the first time in a given tenant.
- Network access to the endpoints: https://login.microsoftonline.com, https://enterpriseregistration.windows.net, and https://autoupdate.msappproxy.net.
The Microsoft Entra Password Protection proxy service does upgrade automatically. The automatic upgrade uses the Microsoft Entra Connect Agent Updater service, which is installed side by side with the proxy service.
Install and configure Microsoft Entra Password Protection proxy service
Install Microsoft Entra Password Protection proxy service on a member server in your on-premises AD DS environment. In addition, you can use a dedicated member server for the proxy service. Once installed, the Microsoft Entra Password Protection proxy service communicates with Microsoft Entra ID to maintain a copy of the global and customer banned password lists for your Microsoft Entra tenant.
Note: Do not install the proxy service on a Domain Controller (DC) or Read-Only Domain Controller (RODC).
We recommend at least two Microsoft Entra Password Protection proxy servers per forest for redundancy. In our example, we will install it on the member server AP-01 (application server).
Place the AzureADPasswordProtectionProxySetup.msi in the C:\install folder. Then, run Command Prompt as administrator and start the installer AzureADPasswordProtectionProxySetup.msi.
C:\Install\AzureADPasswordProtectionProxySetup.msiGo through the Microsoft Entra Password Protection Proxy Bundle Setup. When finished, click on Close.
Verify that the Microsoft Entra Password Protection Proxy appears in Programs and Features.
Run Windows PowerShell (64-bit) as administrator. Import the module AzureADPasswordProtection.
Import-Module AzureADPasswordProtectionCheck that the Microsoft Entra Password Protection proxy service is running.
Get-Service AzureADPasswordProtectionProxy | flThe result will show a Status of Running.
Name : AzureADPasswordProtectionProxy
DisplayName : Azure AD Password Protection Proxy
Status : Running
DependentServices : {}
ServicesDependedOn : {SAMSS, KEYISO, RPCSS}
CanPauseAndContinue : False
CanShutdown : False
CanStop : True
ServiceType : Win32OwnProcessThe proxy service is running on the machine but doesn’t have credentials to communicate with Microsoft Entra ID. Register the Microsoft Entra Password Protection proxy server with Microsoft Entra ID using your Global Administrator credentials. Do that on every Microsoft Entra Password Protection proxy server.
Note: There might be a noticeable delay after you run the below cmdlet for the first time. Unless a failure is reported, don’t worry about this delay.
Register-AzureADPasswordProtectionProxy -AccountUpn 'admin@exoip.com'Register the on-premises Active Directory forest with the necessary credentials to communicate with Microsoft Entra ID by using the Register-AzureADPasswordProtectionForest PowerShell cmdlet.
Note: If multiple Microsoft Entra Password Protection proxy servers are installed in your environment, it doesn’t matter which proxy server you use to register the forest. This step is run once per forest.
The cmdlet requires either Global Administrator or Security Administrator credentials for your Microsoft Entra tenant. It also requires on-premises Active Directory Enterprise Administrator privileges. You must also run this cmdlet using an account with local administrator privileges. The Microsoft Entra ID account used to register the forest may be different from the on-premises Active Directory account.
Note: There might be a noticeable delay after you run the below cmdlet for the first time. Unless a failure is reported, don’t worry about this delay.
Register-AzureADPasswordProtectionForest -AccountUpn 'admin@exoip.com'Microsoft Entra Password Protection Audit mode
Verify that Microsoft Entra Password Protection is set on Audit mode before going to the next step and installing the Microsoft Entra Password Protection DC agent service. By default, it’s set to Audit mode.
Note: If Microsoft Entra Password Protection is set to Audit mode, the attempt will only be logged (event log).
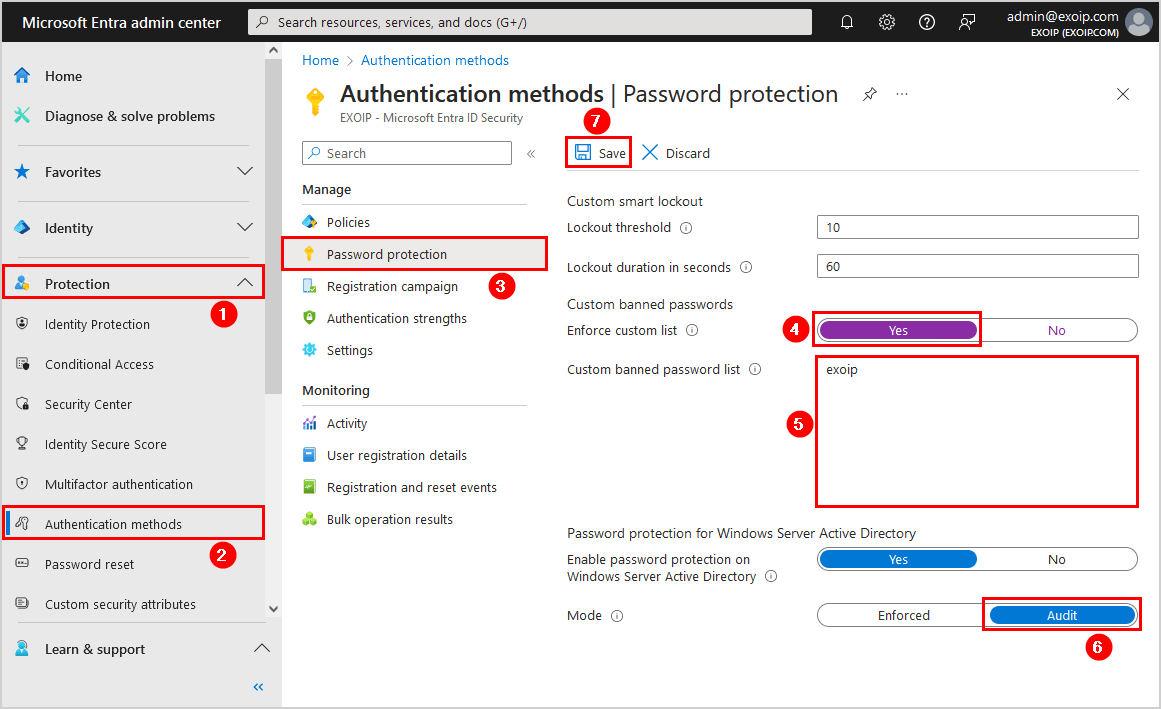
Sign in to the Microsoft Entra admin center. Navigate to Protection > Authentication methods > Password protection. Another way is to search at the top for Password Protection.
We recommend enabling the feature Enforce custom list and adding the company name. Ensure that the mode Audit is active. Click Save.
Microsoft Entra Password Protection DC agent prerequisites
The following requirements apply to the Microsoft Entra Password Protection DC agent:
- Windows Server 2012 R2 or later.
- .NET 4.7.2 installed or higher.
- Do not install on a RODC (Read-Only Domain Controller).
- Distributed File System Replication (DFSR) for sysvol replication. If your domain isn’t already using DFSR, you must migrate from RFS (File Replication System – the predecessor to DFSR) to DFSR before installing Microsoft Entra Password Protection.
The Microsoft Entra Password Protection DC agent does not upgrade automatically. Instead, a manual upgrade is accomplished by running the latest version of the AzureADPasswordProtectionDCAgentSetup.msi software installer. The latest version of the software is available on the Microsoft Download Center.
Install Microsoft Entra Password Protection DC agent service
Install Microsoft Entra Password Protection DC agent service on the on-premises Domain Controllers. In our example, we only have one domain controller in the organization.
Place the AzureADPasswordProtectionDCAgentSetup.msi in the C:\install folder on the Domain Controller. Then, run Command Prompt as administrator and start the installer AzureADPasswordProtectionDCAgentSetup.msi.
C:\install\AzureADPasswordProtectionDCAgentSetup.msiGo through the installation wizard and click on Finish.
Click on Yes to restart the Domain Controller. If you only have one DC in the environment, schedule a restart.
Verify that the Microsoft Entra Password Protection DC Agent shows in Programs and Features.
Run Windows PowerShell (64-bit) as administrator. Check on which Domain Controllers the Microsoft Entra Password Protection DC Agent is installed.
Get-AzureADPasswordProtectionDCAgentAll the information appears in the output.
ServerFQDN : DC01-2022.exoip.local
SoftwareVersion : 1.2.177.1
Domain : exoip.local
Forest : exoip.local
PasswordPolicyDateUTC : 4/16/2024 5:32:02 PM
HeartbeatUTC : 4/16/2024 5:30:59 PM
AzureTenant : exoip.comVerify Microsoft Entra Password Protection Audit mode
Once you enable Microsoft Entra Password Protection Audit mode for on-premises Active Directory, an event will register when a password is reset or changed. For example, it will show if new passwords set by the administrators, helpdesk, or the users are rejected or accepted.
To see it in action and verify it’s working. Let’s reset a password in Active Directory for a test user. First, create a strong password. After that, reset the password again, but this time with a weak password.
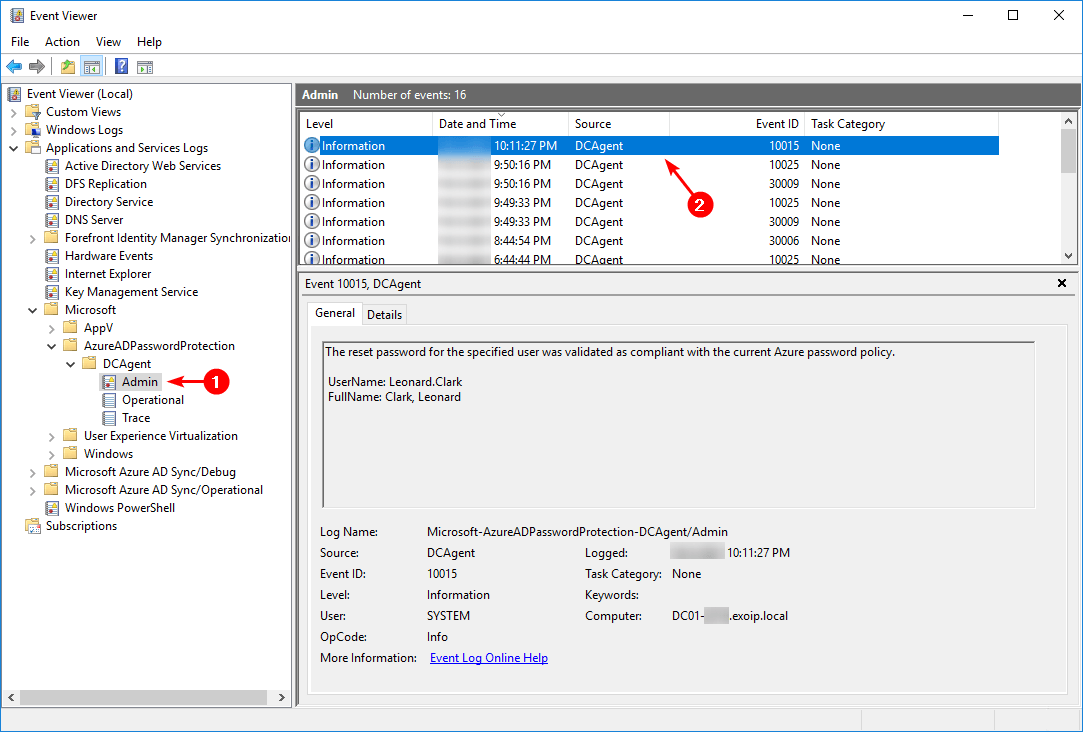
Microsoft Entra Password Protection DC agent event logs
Start Event Viewer on the Domain Controller. Navigate to Applications and Services Logs > Microsoft > AzureADPasswordProtection > DCAgent > Admin.
Microsoft Entra ID password policy rejects password
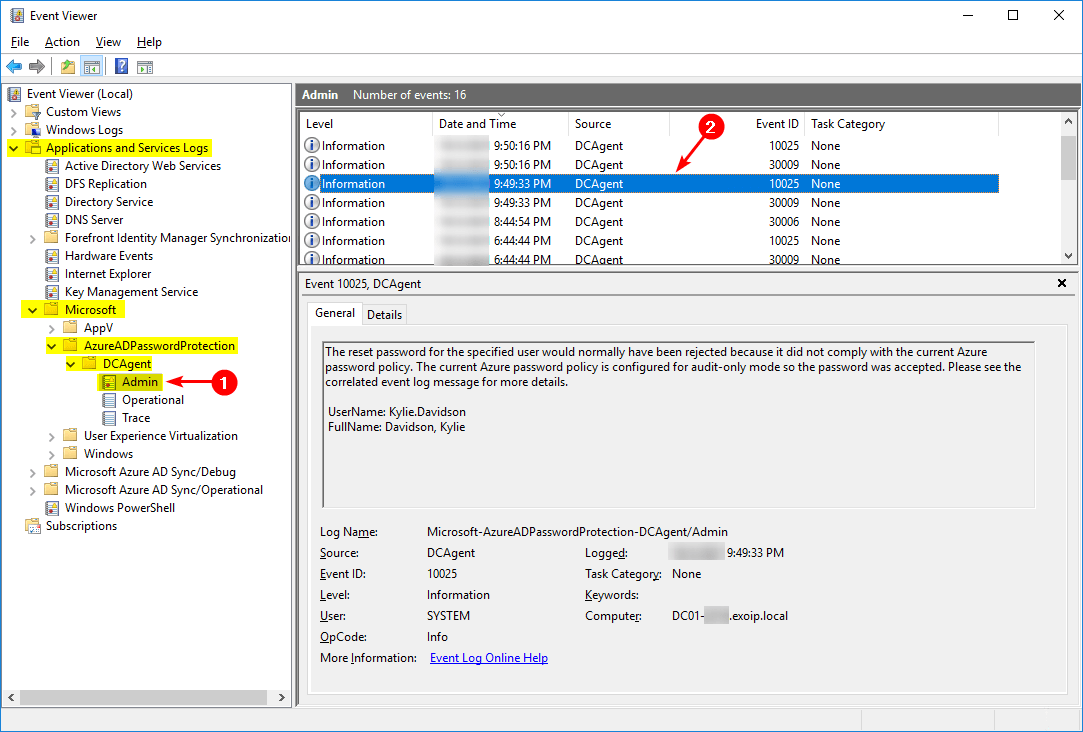
When Microsoft Entra ID rejects the password, it will show the event ID 10025 and event ID 30009.
Event 10025, DCAgent
The reset password for the specified user would normally have been rejected because it did not comply with the current Azure password policy. The current Azure password policy is configured for audit-only mode so the password was accepted. Please see the correlated event log message for more details.
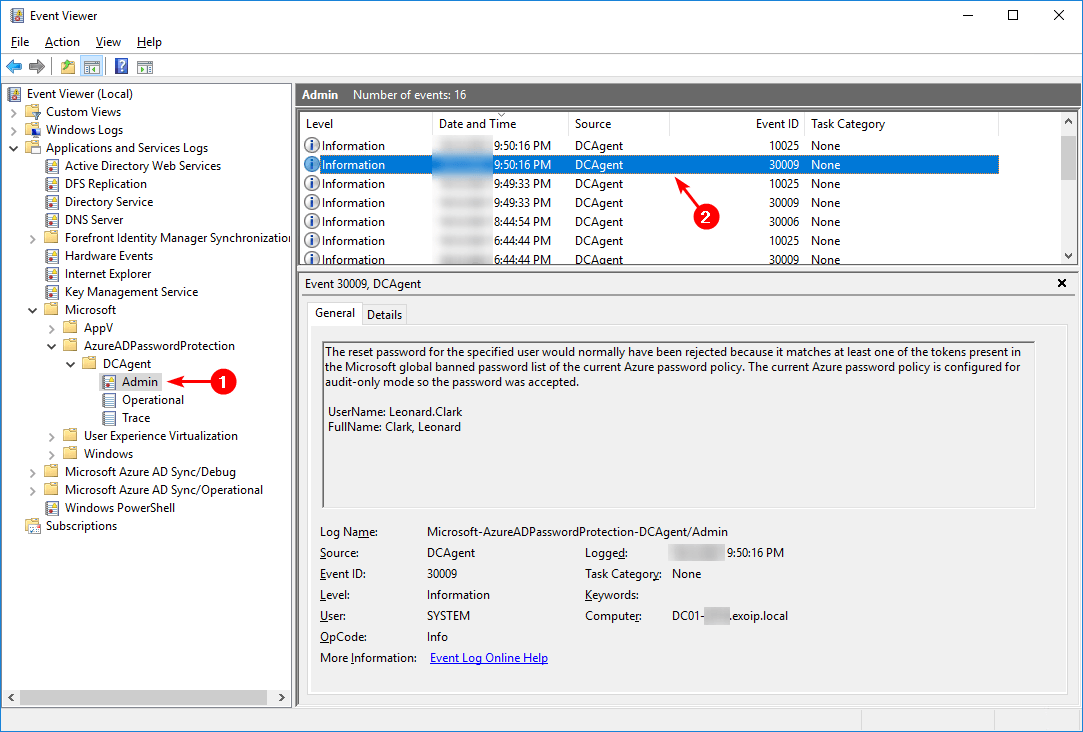
Event 30009, DCAgent
The reset password for the specified user would normally have been rejected because it matches at least one of the tokens present in the Microsoft global banned password list of the current Azure password policy. The current Azure password policy is configured for audit-only mode so the password was accepted.
Microsoft Entra password policy accepts password
When Microsoft Entra ID validates the password as compliant, it will show the event ID 10015.
Event 10015, DCAgent
The reset password for the specified user was validated as compliant with the current Azure password policy.
Microsoft Entra Password Protection summary report
Get a summary report showing how many new passwords sets are validated and how many are failed.
Get-AzureADPasswordProtectionSummaryReportThe output appears.
DomainController : DC01-2022.exoip.local
PasswordChangesValidated : 0
PasswordSetsValidated : 4
PasswordChangesRejected : 0
PasswordSetsRejected : 0
PasswordChangeAuditOnlyFailures : 0
PasswordSetAuditOnlyFailures : 3
PasswordChangeErrors : 0
PasswordSetErrors : 0The next step, which is the last step, is to switch from Audit mode to Enforced mode.
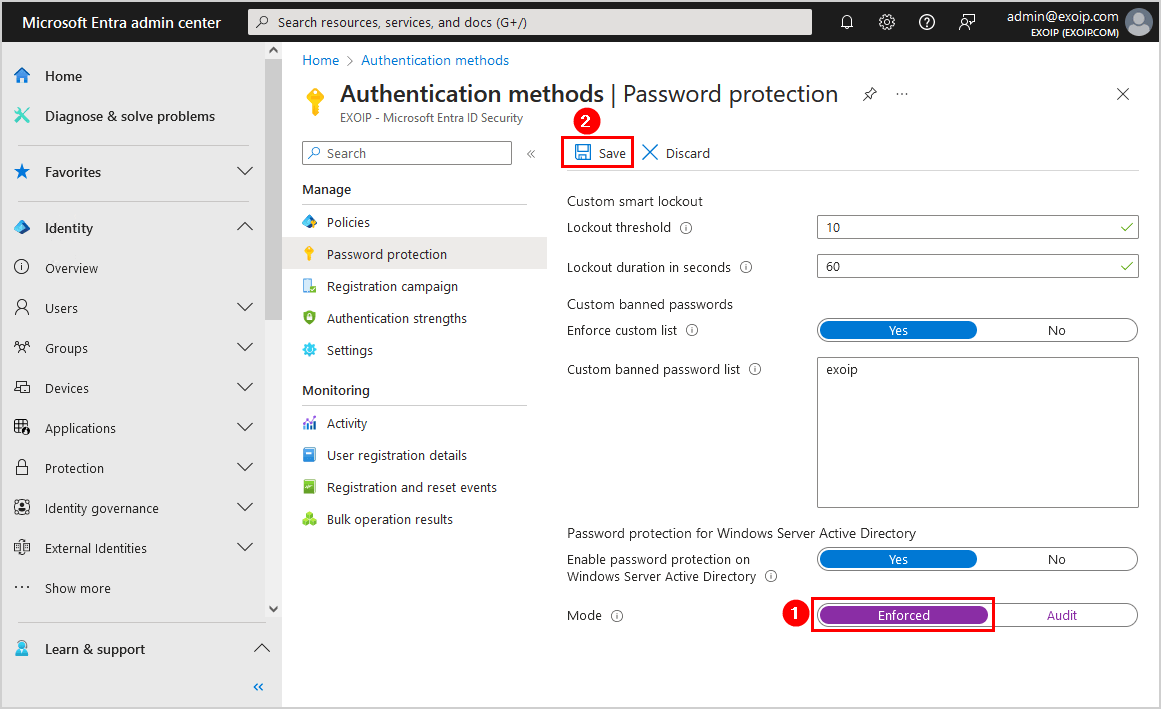
Enforce Microsoft Entra Password Protection
Sign in to the Microsoft Entra admin center. Navigate to Protection > Authentication methods > Password protection. Another way is to search at the top for Password Protection.
Note: If set to Enforce, users will be prevented from setting banned passwords, and the attempt will be logged.
Enable the mode Enforce. Click Save.
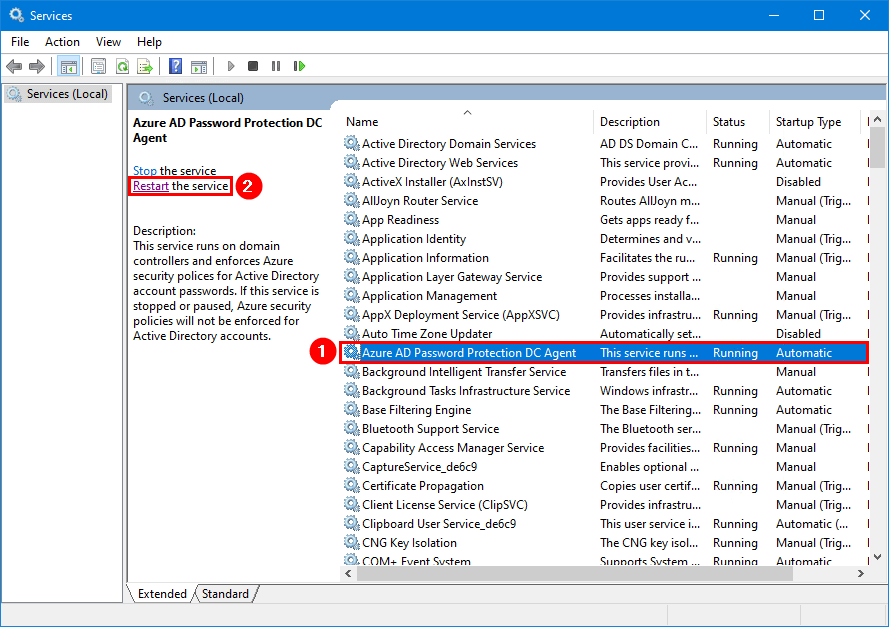
Restart the Microsoft Entra Password Protection DC Agent on all the Domain Controllers.
Important: To have the changes apply immediately, restart the DC agents on all the Domain Controllers.
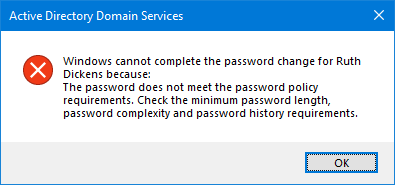
Verify Microsoft Entra Password Protection Enforce mode
Go to Active Directory Users and Computers and change a user password to a weak or compromised password. After you click on OK, the below error message appears:
Active Directory Domain Services
Windows cannot complete the password change for Ruth Dickens because:
The password does not meet the password policy requirements. Check the minimum password length, password complexity and password history requirements.
You successfully set up Microsoft Entra Password Protection for Active Directory on-premises.
Read more: Force password sync with Azure AD Connect »
Conclusion
You learned how to configure Microsoft Entra Password Protection for on-premises Active Directory. First, follow the steps to configure Microsoft Entra Password Protection in Audit mode. Then, after everything is in place and you are satisfied, switch from Audit mode to Enforced.
Microsoft Entra Password Protection for on-premises uses the same global and custom banned password lists that are stored in Microsoft Entra ID, and does the same checks for on-premises password changes as Microsoft Entra ID does for cloud-based changes.
If you don’t have a Microsoft Entra tenant (cloud) and only have an on-premises environment, follow the steps in the article How to Secure Active Directory passwords from breaches. This configuration will use the Have I Been Pwned password list to protect the on-premises from weak, breached, and well-known passwords.
Did you enjoy this article? You may also like Upgrade Azure AD Connect to V2.x. Don’t forget to follow us and share this article.


Hi Ali,
We configured Microsoft Entra Password Protection and set banned passwords, works fine. But when Admin or delegated users access AD locally can set any passwords including passwords from the banned list.
How we can restrict admin users or delegates to prevent the use of the banned list of passwords? if they access AD locally. Kindly advise.
Admins or delegated users should be unable to set any weak/compromised passwords, including the custom banned password list.
I just tested it in AD, and I am not able to set weak or custom banned passwords for the users. An error appears that the password does not meet the password policy requirements.
Try restarting the below services on all the servers they are running:
– Azure AD Password Protection DC Agent (this service is important to restart)
– Azure AD Password Protection Proxy service
Hi Ali, curious that you say flat out not to install the proxy service on DCs alongside the DC Agent for a compact solution if the solution traffic is initiated outbound only and if off-host firewall ACLs are in place to limit targets to MS endpoint URLs/IPs only. Surely this is a customer decision based on appropriate network risk mitigation controls and understanding and MS is simply trying to avoid customer exposure with their “standard line” re direct DC > external connections.
Regards, Leigh.
You NEVER want to add anything directly on a DC if it is internet-facing. Even if the firewall rules are locked down to the required endpoints. That’s best practice. That’s why a proxy is called for. AD stores passwords unsalted and in plain text. That’s by design. Keep the risk to a minimum by not adding configurations not supported by Microsoft.
Hi Ali,
What are roll back steps to remove the “Microsoft Entra Password Protection for on-premises”?
Is simply uninstalling the proxy service application is enough? or do we need deregister the server/service?
Do we also need to remove the sysvol entries? if not the last downloaded custom list will still be enforced/audited by the DC right?
Thanks in advance.
Regards,
Krishna.
Thanks for great explanation. instead of preparing new server for proxy. Can I install the proxy agent on AD Connect server?
Yes, you can install the proxy service on the AD Connect server or any member server. Just don’t install it on the Domain Controller or Read-Only Domain Controller.
Timely article, I have implemented this myself last week.
Do you know if there is any way to see the passwords that failed the validation?
Currently in audit mode, which we intend to run for 3 months to gain an understanding of users trying to set passwords that would fail before we implement it live. I can already see a few audit events for failed but passed anyway. Whilst I get for security that the password should not be revealed in the event logs being able to implement a company wide training with “these passwords would fail” would be a good thing before we switch to live
It’s not possible to check which passwords failed the validation.
In order to implement this Microsoft Entra Password Protection – Does there need to be syncing between the On-Premise AD and the Microsoft Entra ID, like with Microsoft Entra Connect Sync? I have been asked to implement this feature, but the customer currently has no syncing at all between the Microsoft Entra ID and the On-Premise AD, will this a problem? Thanks for all the help.
No, you don’t need Microsoft Entra Connect.
But, you should advise them to implement Microsoft Entra Connect. Integrating your on-premises directories with Microsoft Entra ID makes your users more productive by providing a common identity for accessing both cloud and on-premises resources.