We like to create new Microsoft Entra ID users in the company. Going through the…
Move from remember MFA on trusted device to Conditional Access sign-in frequency
You have enabled remember Multi-Factor Authentication on trusted device in Office 365 Multi-Factor Authentication. When you look at the setting, you see that Microsoft recommends using Conditional Access sign-in frequency. Let’s look at how to move from remember Multi-Factor Authentication on trusted devices to Conditional Access sign-in frequency.
Table of contents
Introduction
Moving from Microsoft 365 MFA to Azure Active Directory Conditional Access can be done in three steps:
- Move from per-user MFA to Conditional Access MFA
- Move from MFA trusted IPs to Conditional Access named locations
- Move from remember MFA on trusted device to Conditional Access sign-in frequency (this article)
Conditional Access sign-in frequency
You want to move from remember Multi-Factor Authentication on trusted device to Azure Active Directory Conditional Access sign-in frequency. Before you do that, what are the advantages and disadvantages?
Advantages for Azure Active Directory Conditional Access sign-in frequency:
- Sign-in frequency
- Persistent browser session
- Integrates with Azure AD MFA
Disadvantages for Azure Active Directory Conditional Access sign-in frequency:
- Pay for the subscription
Conditional Access requires Azure AD Premium 1 or 2. We recommend explaining to the customer why they should pay (subscribe) for Azure AD premium. Tell them the benefits and how security will improve. Also, managing will be much easier for the administrators, which will save time.
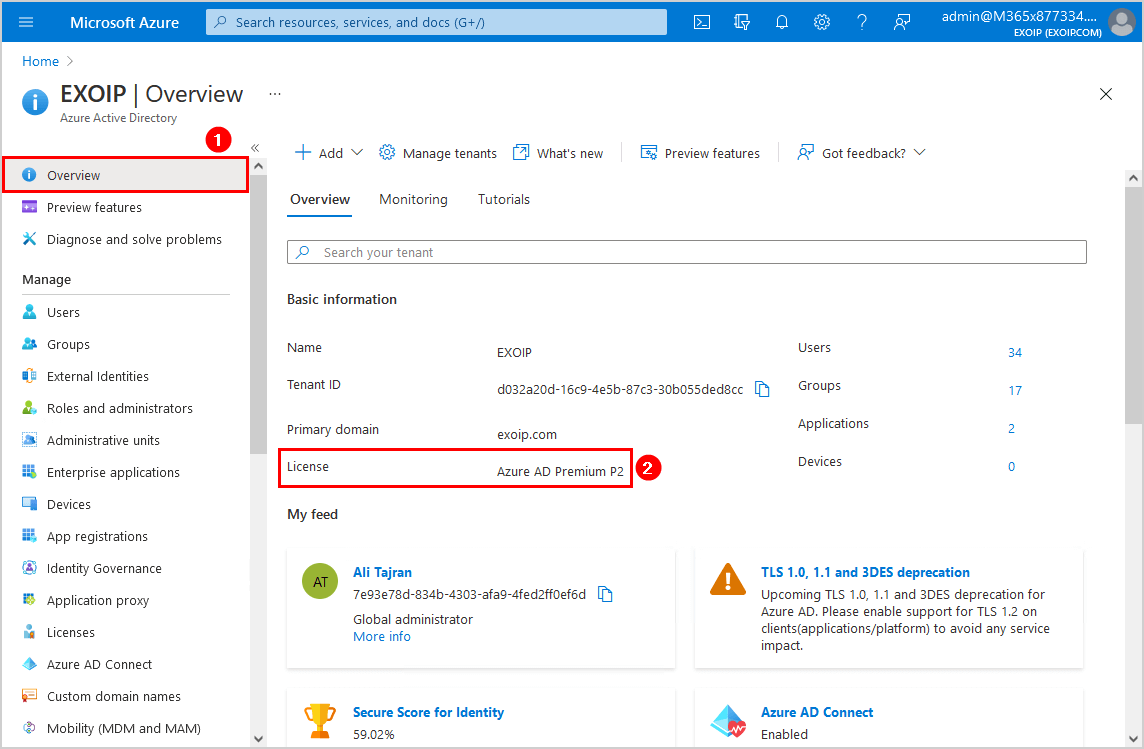
Check Azure AD Premium license
Check that you have Azure AD Premium plan 1 or 2. Sign in to Microsoft Azure. In the portal, navigate to Azure Active Directory > Overview. In the example below, the tenant got the Azure AD Premium P2 license.
Remember multi-factor authentication on trusted device
Verify first that the setting remember multi-factor authentication on trusted device is enabled. If yes, you will copy the number of days that are set and disable the setting.
Verify remember multi-factor authentication on trusted device
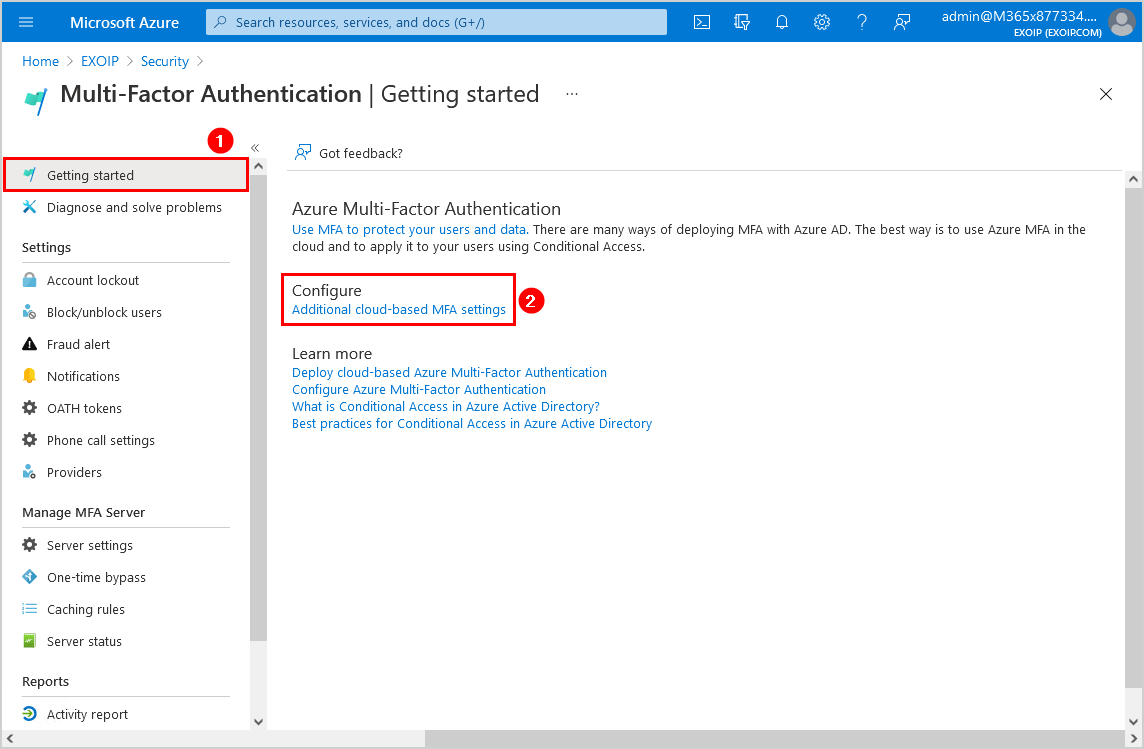
Navigate to Azure Active Directory > Security > Conditional Access > MFA > Getting started. Click on Additional cloud-based MFA settings.
Another way is to go directly to the Additional cloud-based MFA settings page.
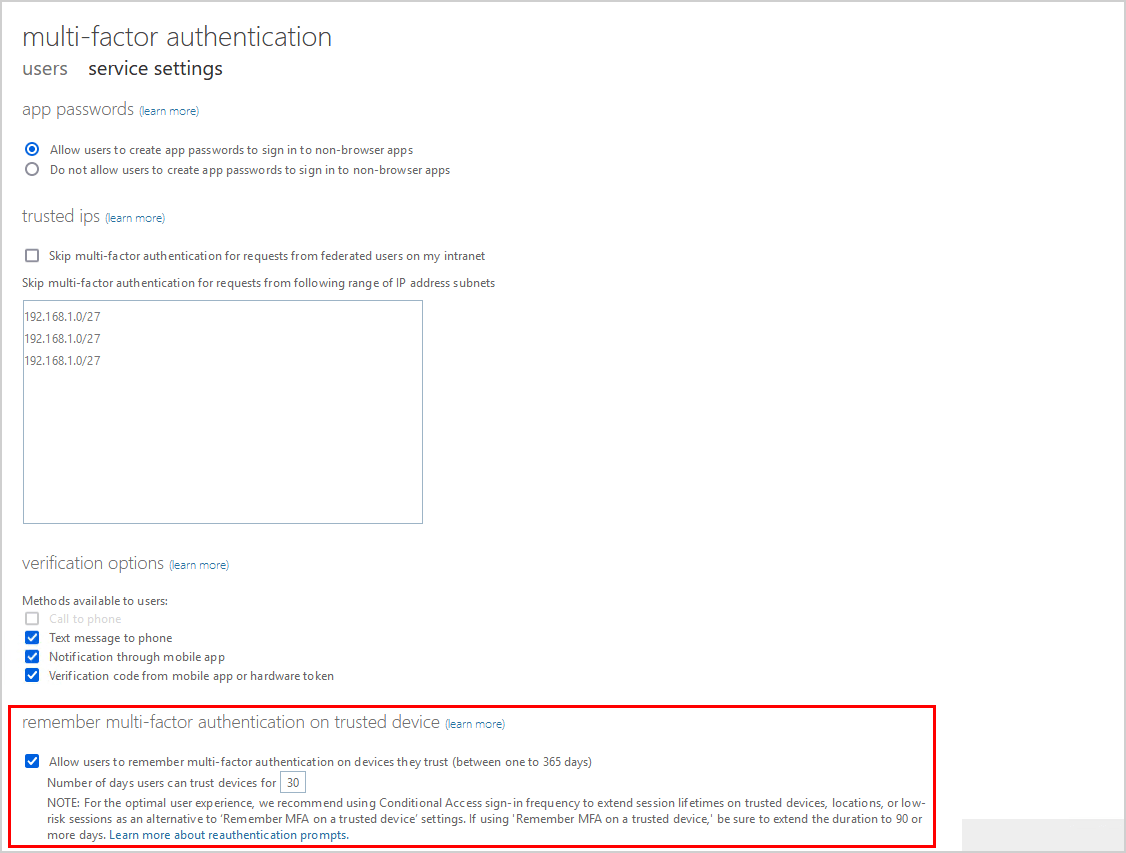
A new page will show up. Go to the section remember multi-factor authentication on trusted device. Check if the setting Allow users to remember multi-factor authentication on trusted device is enabled.
In our example, the number of days users can trust devices for is 30 days.
Note: For the optimal user experience, we recommend using Conditional Access sign-in frequency to extend session lifetimes on trusted devices, locations, or low-risk sessions as an alternative to ‘Remember MFA on a trusted device’ settings. If using ‘Remember MFA on a trusted device,’ be sure to extend the duration to 90 or more days.
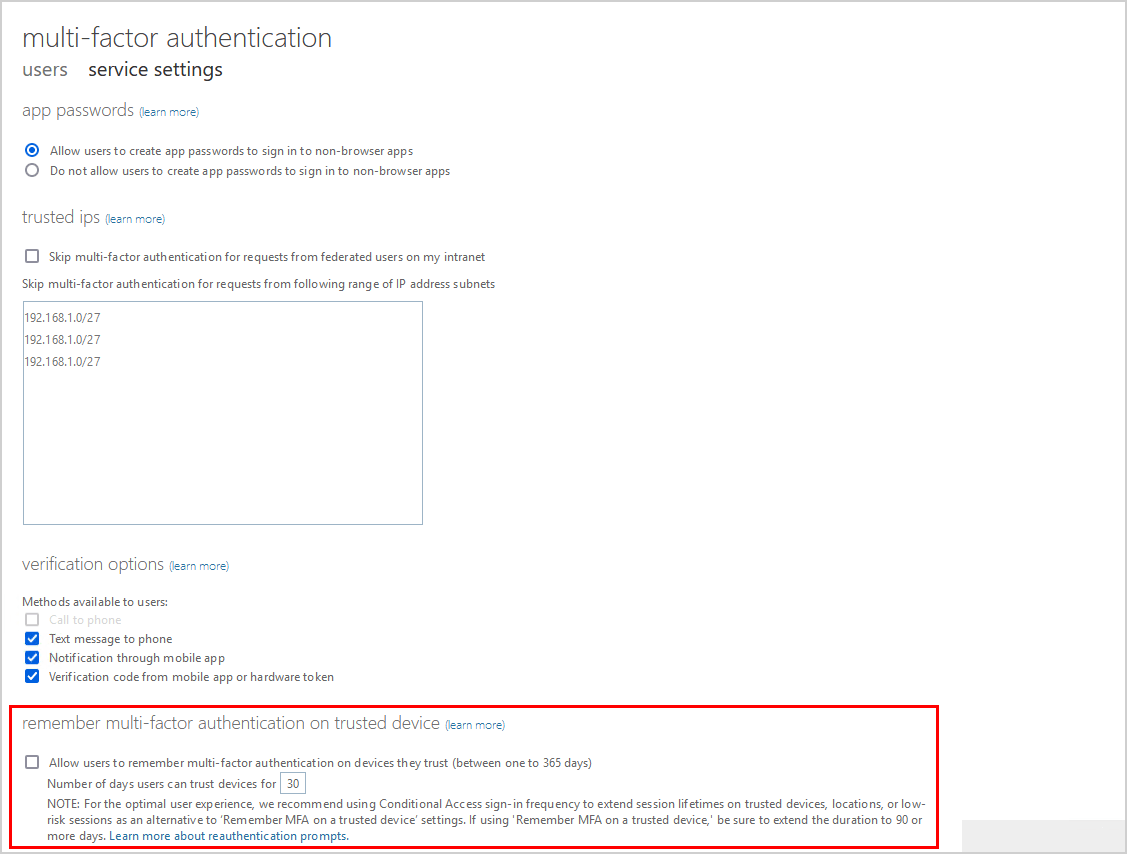
Uncheck remember multi-factor authentication on trusted device
Copy the number of days and save it to Notepad. After that, uncheck Allow users to remember multi-factor authentication on devices they trust (between one to 365 days). Click on Save (it’s down below).
The unchecked setting will look like this.
Enable Conditional Access sign-in frequency
Sign in to the Azure portal. Navigate to Azure Active Directory > Security > Conditional Access. Click on the MFA policy to edit the policy. Another option is to create a new policy for the sign-in frequency setting.
If you don’t have an MFA policy, read the article Configure Azure AD Multi-Factor Authentication.
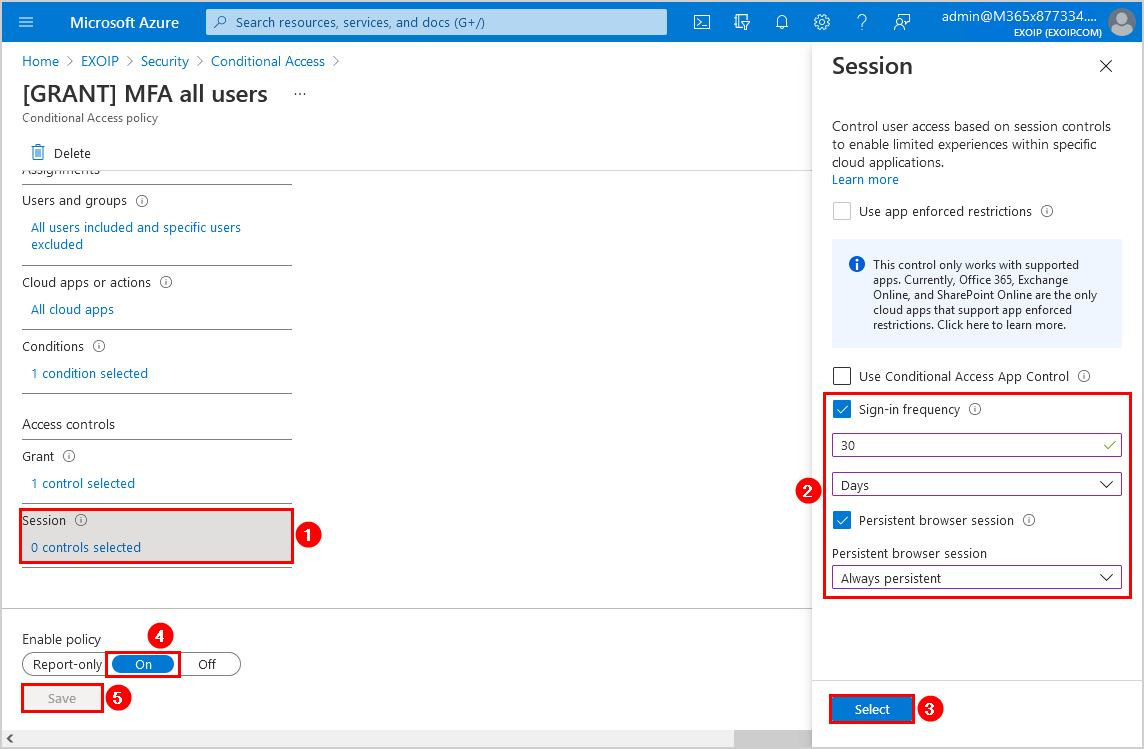
In the Conditional Access policy, navigate to Session. Enable Sign-in frequency and insert the days that you copied in the previous step. In our example, it’s 30 days. Enable Persistent browser session and choose in the dropdown menu for Always persistent. Click on Select.
Ensure that you enable the policy. Click on Save.
That’s it!
Read more: Conditional Access MFA breaks Azure AD Connect synchronization »
Conclusion
In this article, you learned how to move from remember MFA on trusted device to Conditional Access sign-in frequency. Check if the setting Allow users to remember multi-factor authentication on devices they trust (between one to 365 days) is configured and copy the number of days. After that, uncheck the setting.
Create a new Conditional Access policy or edit an existing Conditional Access policy. Enable the sign-in frequency setting to extend session lifetimes and add the number of days that you copied. As of last, verify your work and sign in with a test account.
Did you enjoy this article? You may also like How to Restrict access to Microsoft Entra admin center. Don’t forget to follow us and share this article.


Always Persistent does not work when I include AADJ in the CA. I want to set “Remain Sign-In” only on enrolled devices. Would you know how to do it? Thank you
I had followed this method of disabling the MFA on trusted device, and have a conditional access policy of 90 day frequency with always persistent browser, however this doesn’t work with properly. I’ve had to go back and re-enable the trusted device sign in
Right this doesn’t work. I had to enable ‘remember multi-factor authentication on trusted device’ and then set the number of days.
Hi,
I am just wondering something.
As I was setting this up (we already have MFA functional) but once set the session control option “Persistent Browser Session” to Always persistent it gives me an error while saving “Invalid session control”.
Would you know what would cause this message?
Hope you are able to answer!
Good article – just wondered what is the default if neither of these settings are enabled. No tick in MFA remember on trusted devices and nothing set in the conditional policy. Just discovered a client with that set and dont want to necessarily change it but would like to set it with a time range so its clearer.
Just looked harder and the Policy says
“The default setting is a rolling window of 90 days, i.e. users will be asked to re-authenticate on the first attempt to access a resource after being inactive on their machine for 90 days or longer.”
So I guess that is what they have now.
Nice! Keep up the good work bro!
Thanks bro!