Users start Outlook for the first time and must go through the Outlook wizard to…
Microsoft 365 security recommendations with PowerShell script
A Microsoft tenant has so many Microsoft admin centers and configuration settings. Checking if the security is on point every time can take much of your time. Everyone wants to have a security baseline so they know where to start or where to look. You can also see it as a security recommendations checklist. In this article, you will learn how to use a PowerShell script to get all the Microsoft 365 security recommendations and what the reports look like.
Table of contents
Secure Cloud Business Applications (SCuBA)
CISA (Cybersecurity and Infrastructure Security Agency) created the Secure Cloud Business Applications (SCuBA) project, which provides guidance and capabilities to secure agencies’ cloud business application environments and protect federal information that is created, accessed, shared, and stored in those environments.
SCuBA will help secure Federal Civilian Executive Branch (FCEB) information assets stored within cloud environments through consistent, effective, modern, and manageable security configurations for the below products:
- Microsoft Defender for Office 365
- Microsoft Azure Active Directory
- Microsoft Exchange Online
- Microsoft Sharepoint and OneDrive for Business
- Microsoft Power BI
- Microsoft Power Platform
- Microsoft Teams
How to get a Microsoft 365 security baseline report
To create a Microsoft 365 security recommendations report, follow these steps:
Step 1. Download ScubaGear
Go to the official ScubaGear GitHub releases page and download the latest version. You need to download the Zip file.
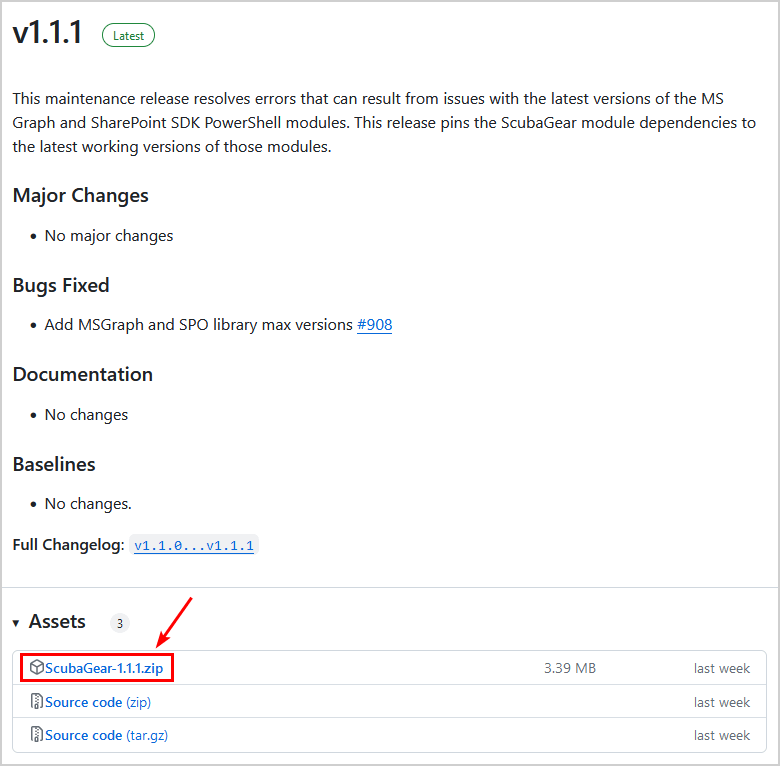
Extract the folder in the Zip file and save it in C:\Temp. It’s best to rename the folder to ScubaGear without the version number.
Step 2. Run ScubaGear SetUp.ps1 PowerShell script
Only PowerShell 5.1 is currently supported. PowerShell 7 may work, but has not been tested. Full PowerShell 7 support will be added in a future release.
Run PowerShell as administrator and run the Set-ExecutionPolicy to RemoteSigned or Unrestricted.
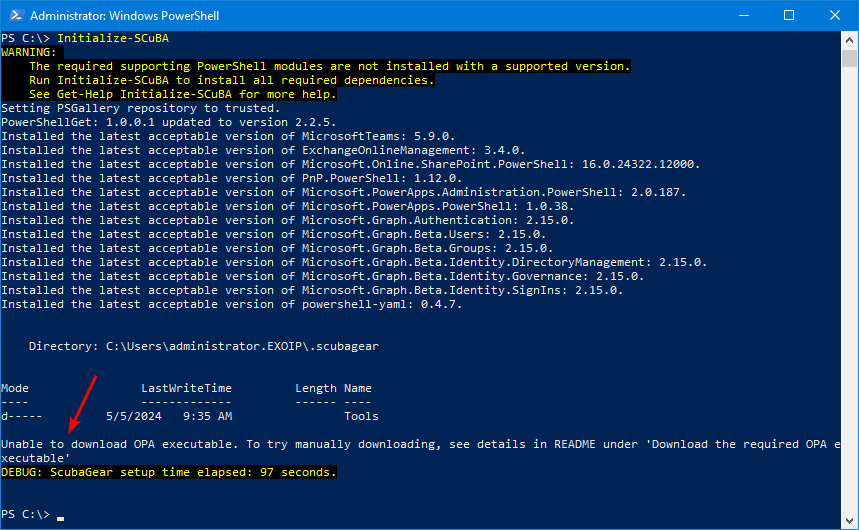
Set-ExecutionPolicy UnrestrictedTo install the module dependencies, open a new PowerShell 5.1 terminal and run SetUp.ps1 from the ScubaGear folder.
C:\Temp\ScubaGear\.\SetUp.ps1You can get the below error at the end:
Unable to download OPA executable. To try manually downloading, see details in README under ‘Download the required OPA executable’.
We will fix that error by manually downloading the OPA executable and placing the file in the correct folder.
Step 3. Download OPA executable
Download the OPA executable from here and paste it into C:\Temp\ScubaGear.

Check the downloaded OPA version.
C:\Temp\ScubaGear\.\opa_windows_amd64.exe versionThis is how the output looks.
Version: 0.61.0
Build Commit: ea7a3e13c8fdceadeb199904facb4990fcb010f8
Build Timestamp: 2024-01-25T13:06:02Z
Build Hostname: c86b8b609133
Go Version: go1.21.5
Platform: windows/amd64
WebAssembly: availableStep 4. Run ScubaGear PowerShell script
Import the ScubaGear module into your session
Import-Module -Name "C:\Temp\ScubaGear\.\PowerShell\ScubaGear"Run the script against all products and create a report.
Invoke-SCuBA -OPAPath "C:\Temp\ScubaGear\" -OutPath "C:\Temp\ScubaGear\"Run the script against Microsoft Entra ID and create a report.
Invoke-SCuBA -OPAPath "C:\Temp\ScubaGear\" -ProductNames aad -OutPath "C:\Temp\ScubaGear"Run the script against multiple products and create a report.
Invoke-SCuBA -OPAPath "C:\Temp\ScubaGear\" -ProductNames aad, exo, teams -OutPath "C:\Temp\ScubaGear"Note: You will get a couple of Microsoft sign-in prompts where you have to enter your Microsoft 365 global administrator credentials. This is needed to retrieve the information from all the Microsoft products.
Step 5. Check Microsoft 365 security baseline report
An HTML report will appear automatically. If not, open the report from the folder.
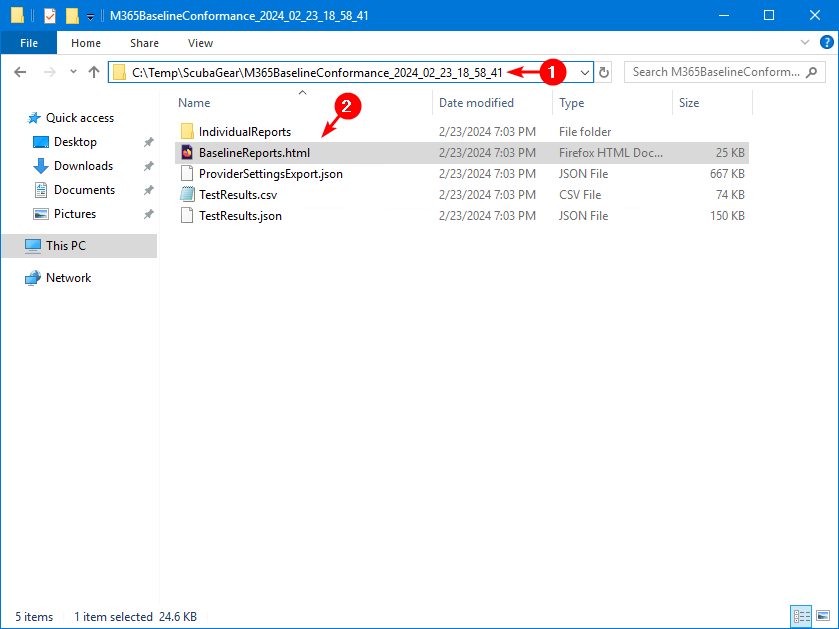
The report shows the Microsoft products and the details in numbers. Click on a product to view all the details with the information.
In our example, we will click on Exchange Online.
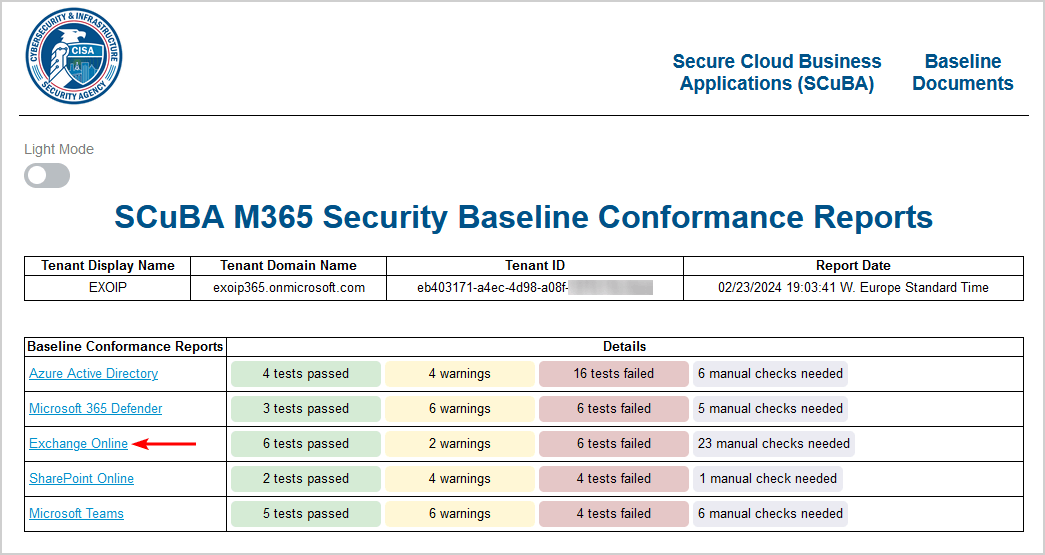
The Exchange Online Baseline Report shows everything in excellent detail.
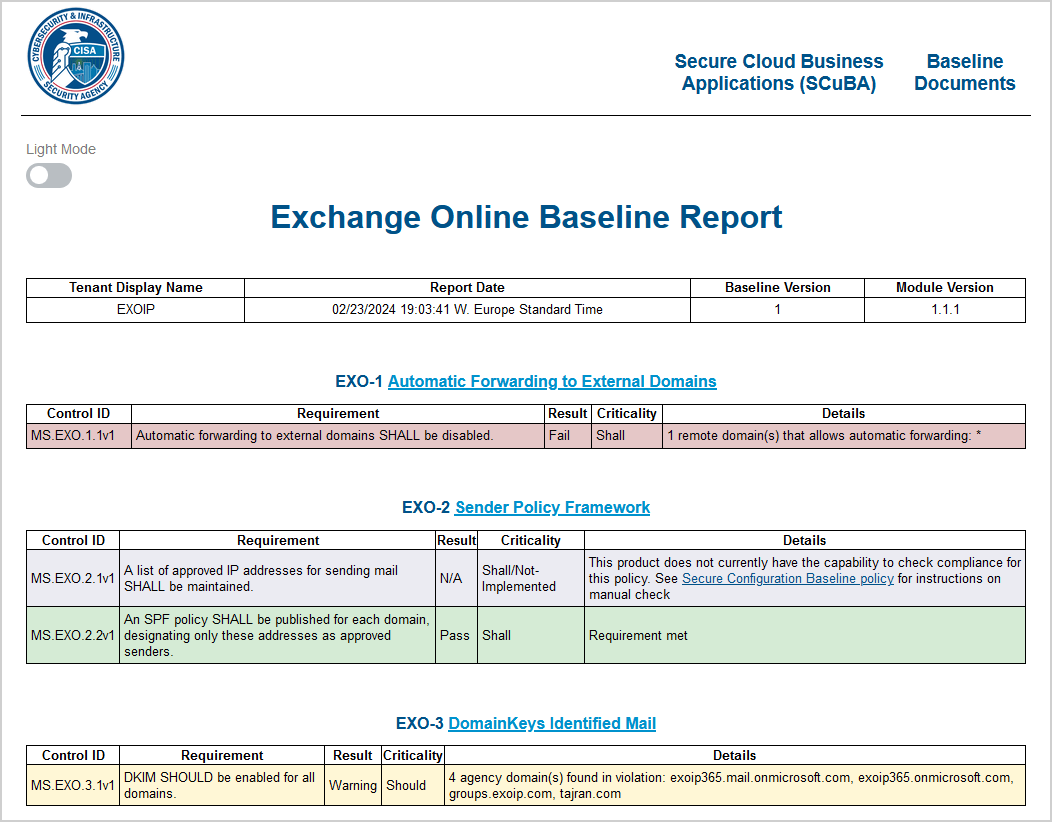
Look into it and fix what you can so the tests will pass the next time you run the report. Don’t immediately adjust every setting so the results will pass. Every organization is different, and you need to approach this carefully.
Disconnect SCuBA session
Disconnect from all the Microsoft sessions after you finish, or if you want to run it against another tenant.
Disconnect-SCuBATenantThat’s it!
Read more: Office 365 Recommended Configuration Analyzer »
Conclusion
You learned how to check the Microsoft 365 security recommendations with the CISA SCuBA PowerShell script. You can create your own PowerShell script, but that takes time, and you need to keep it up to date with the highest standards, which is difficult because it’s changing so fast.
The CISA team provides this script with new features and bug fixes so you will be up to date with the latest security changes to protect your Microsoft 365 organization. Best of all, it’s completely free. It’s a script that I can recommend using against your Microsoft 365 tenant to secure your environment.
Did you enjoy this article? You may also like How to Restrict access to Microsoft Entra admin center. Don’t forget to follow us and share this article.



Ali,
You are too good.
Thanks a lot.
Would it be possible to granularize permissions and use roles other than global administrator?
The minimum user roles needed for each product are described below:
Azure Active Directory – Global Reader
Defender for Office 365 – Global Reader (or Exchange Administrator)
Exchange Online – Global Reader (or Exchange Administrator)
Power Platform – Power Platform Administrator with a “Power Apps for Office 365” license
Sharepoint Online – SharePoint Administrator
Microsoft Teams – Global Reader (or Teams Administrator)
Thanks a lot for this script.
Because of you, I became so much better in tech the last years. Keep posting great stuff!
I followed the steps and it works great. The more engineers that work in a tenant, the more settings get changed!
I created the report. The next step is to look into it closely and change where applicable.
Thanks!
Hello Derek,
Could you please share the steps to import module. I am using the above steps but it is failing.
Really usefull for small business, thanks for the sharing
Thanks for this it’s a good check in addition to to others like Purple Knight.