Every organization knows that security is essential and needs to be solid. Nowadays, every organization…
How to Restrict access to Microsoft Entra admin center
Why do users have access to Microsoft Entra admin center by default? You only want administrators to have access and restrict users to access Microsoft Entra admin center. It’s not relevant for standard users to have access to all kinds of information. In this article, we will look at how to restrict access to Microsoft Entra admin center.
Table of contents
Check current access to Microsoft Entra admin center
Check how it looks like if a user signs in to the Microsoft Entra admin center without restricting access by following the below steps:
- Sign in to Microsoft Entra admin center as a User
- Click on Identity > Overview
- In the Overview screen, the user can see the Microsoft Entra ID organization
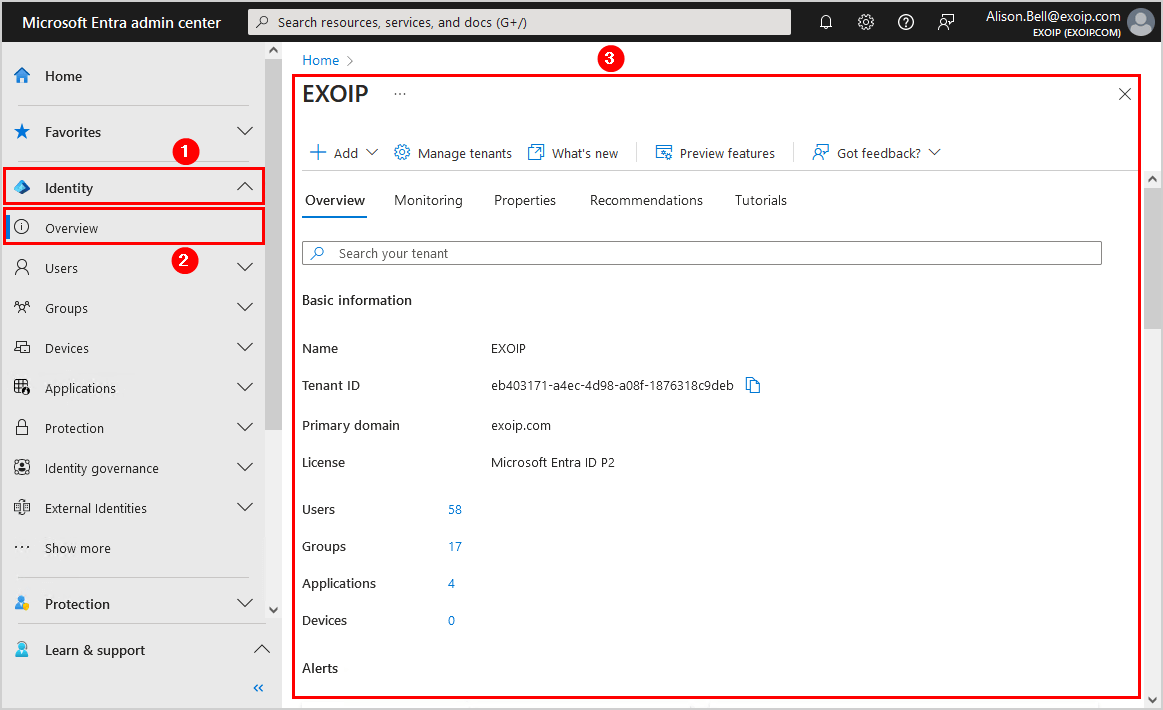
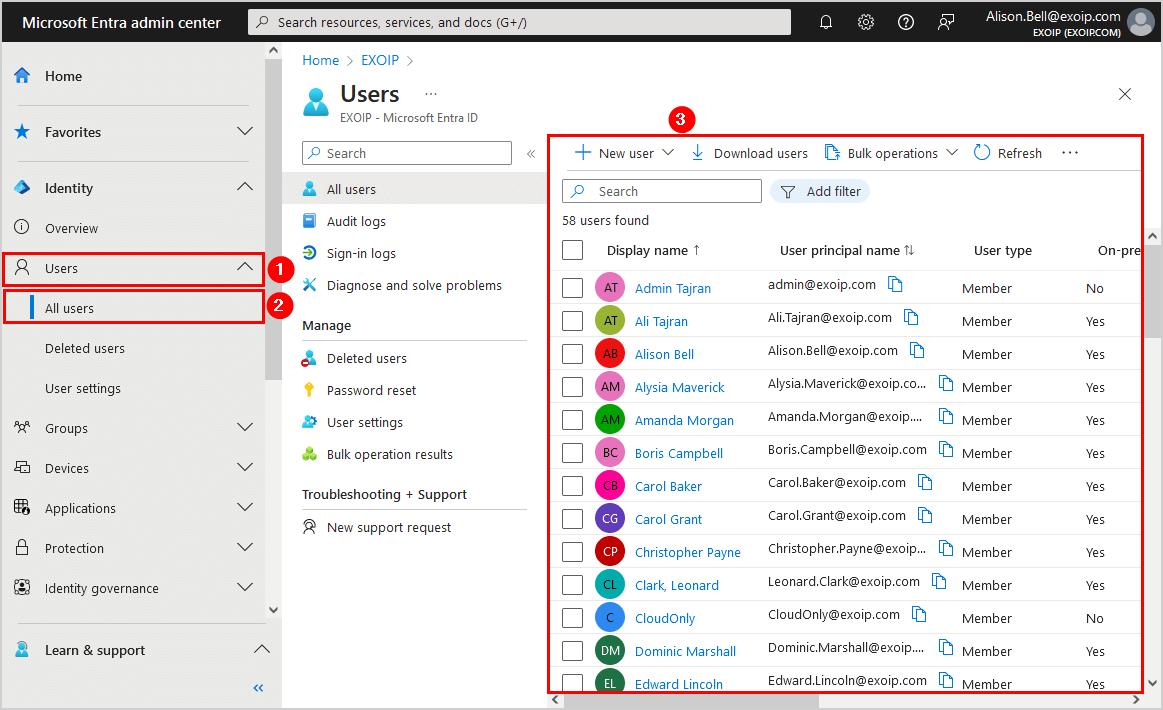
- Click in the menu on Users > All users
- All the users are visible to the user
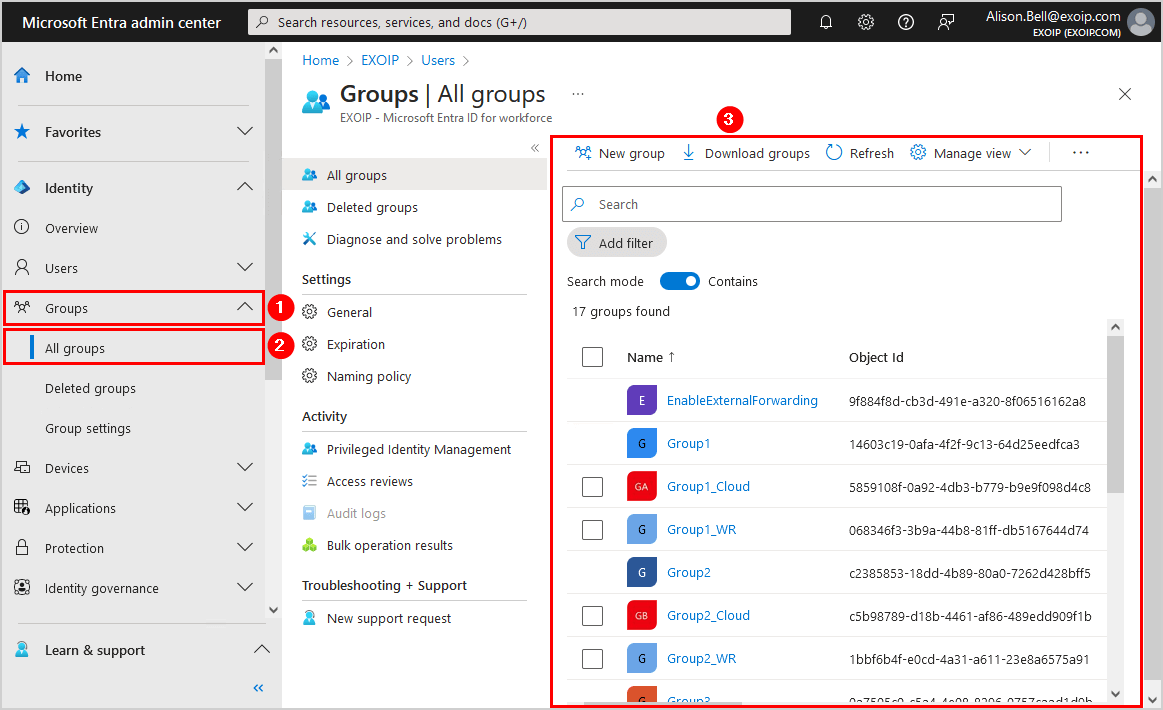
- Click in the menu on Groups > All groups
- All the groups are visible to the user
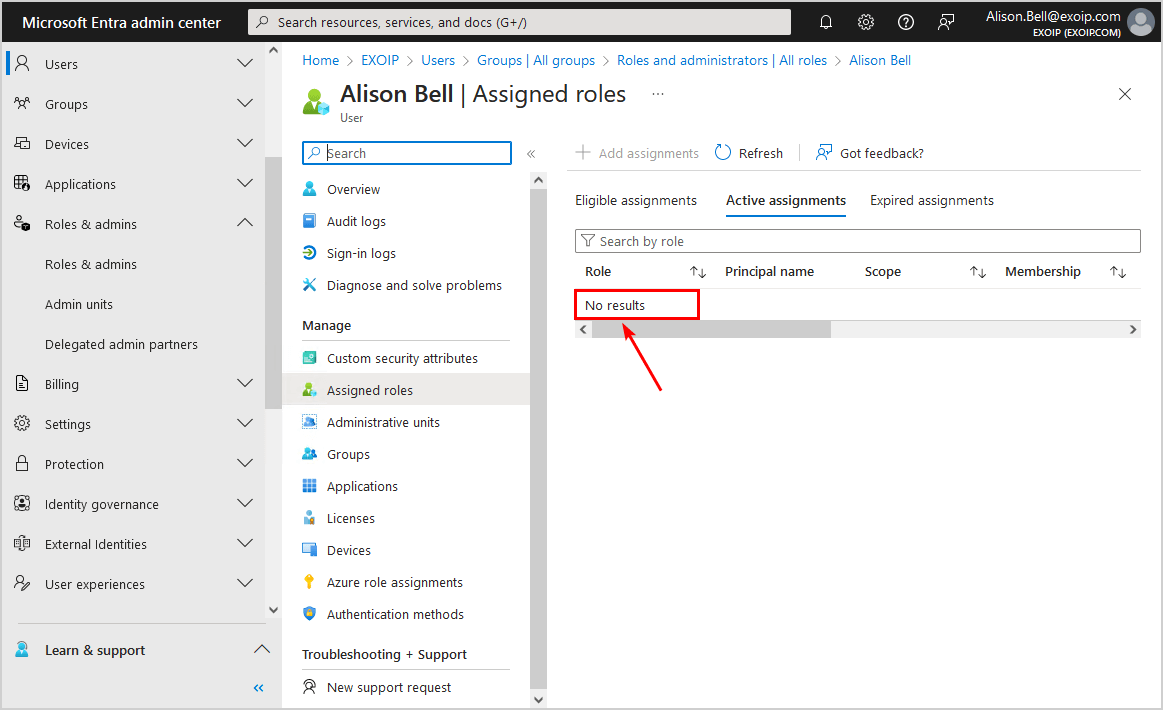
- Click in the menu on Roles & admins > Roles & admins
- Verify the user’s role (in our case, it’s the role User)
- Click on Your Role
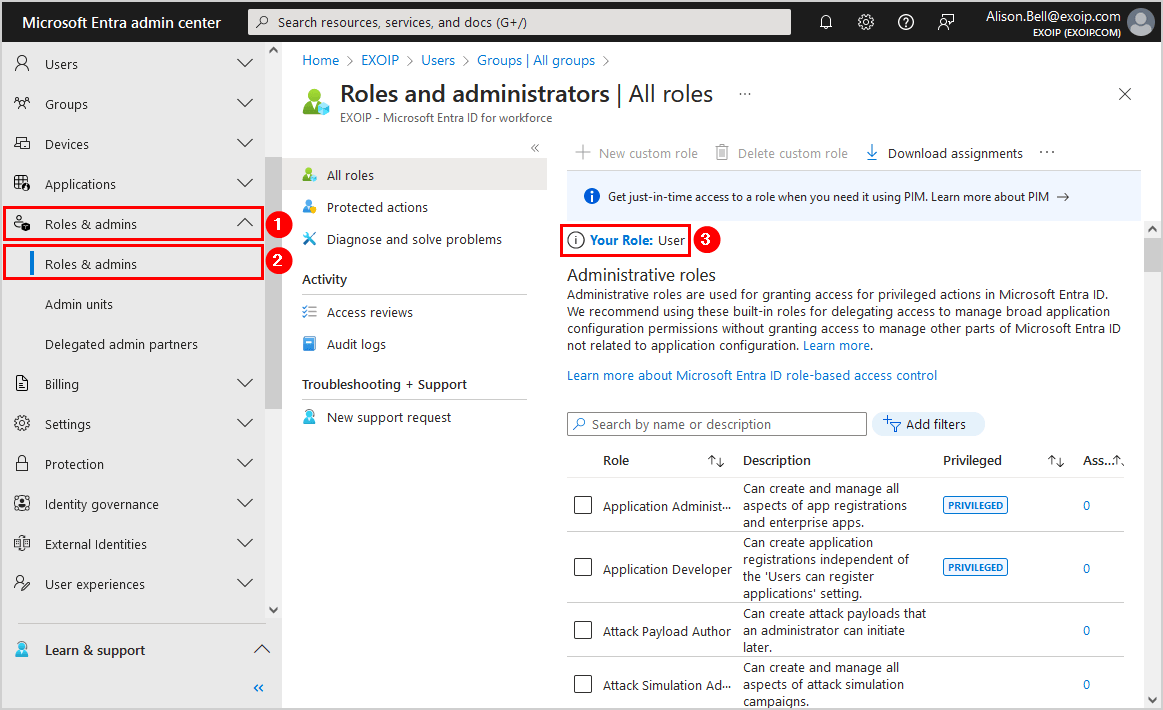
- The user does not have any roles assigned
In the next step, we will look at restricting users from accessing the Microsoft Entra admin center.
Restrict access to Microsoft Entra admin center
To restrict users from accessing the Microsoft Entra admin center, follow these steps:
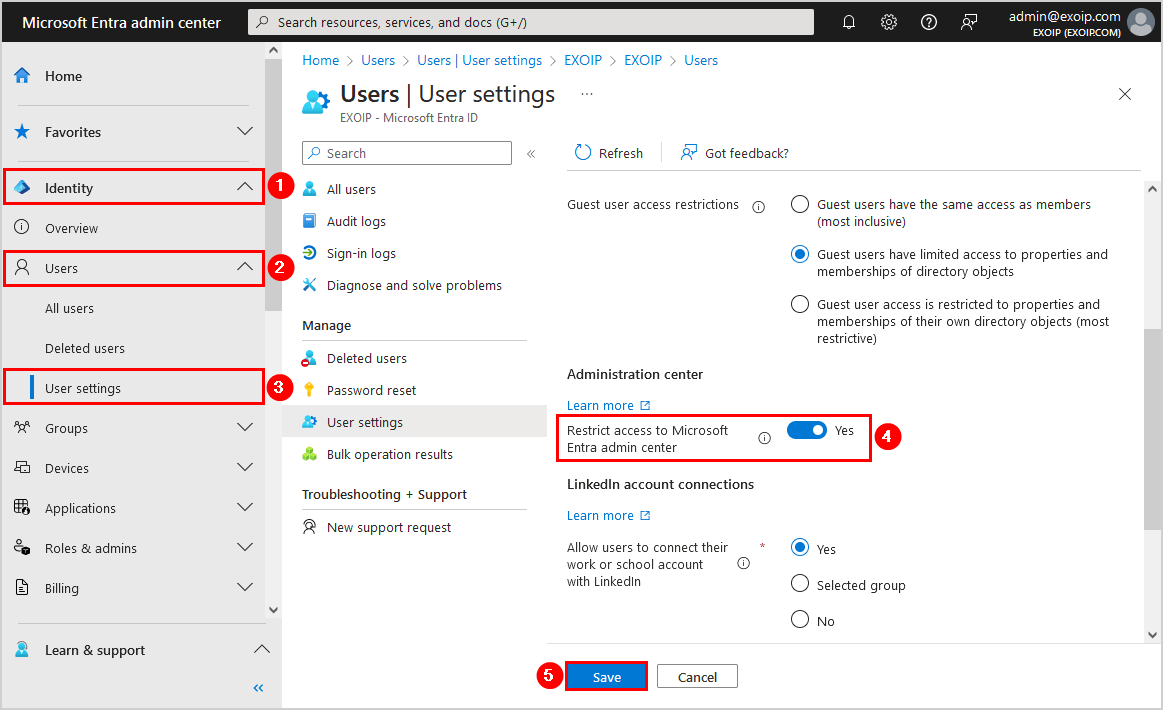
- Sign in to Microsoft Entra admin center as a Global Administrator
- Click on Identity > Users > User settings
- Go to the setting Restrict access to Microsoft Entra admin center and set it to Yes
- Click Save
Give the setting a few minutes to apply the changes on Microsoft’s servers.
Verify no access to Microsoft Entra admin center
Check that the user access to the Microsoft Entra admin center is restricted by following the below steps:
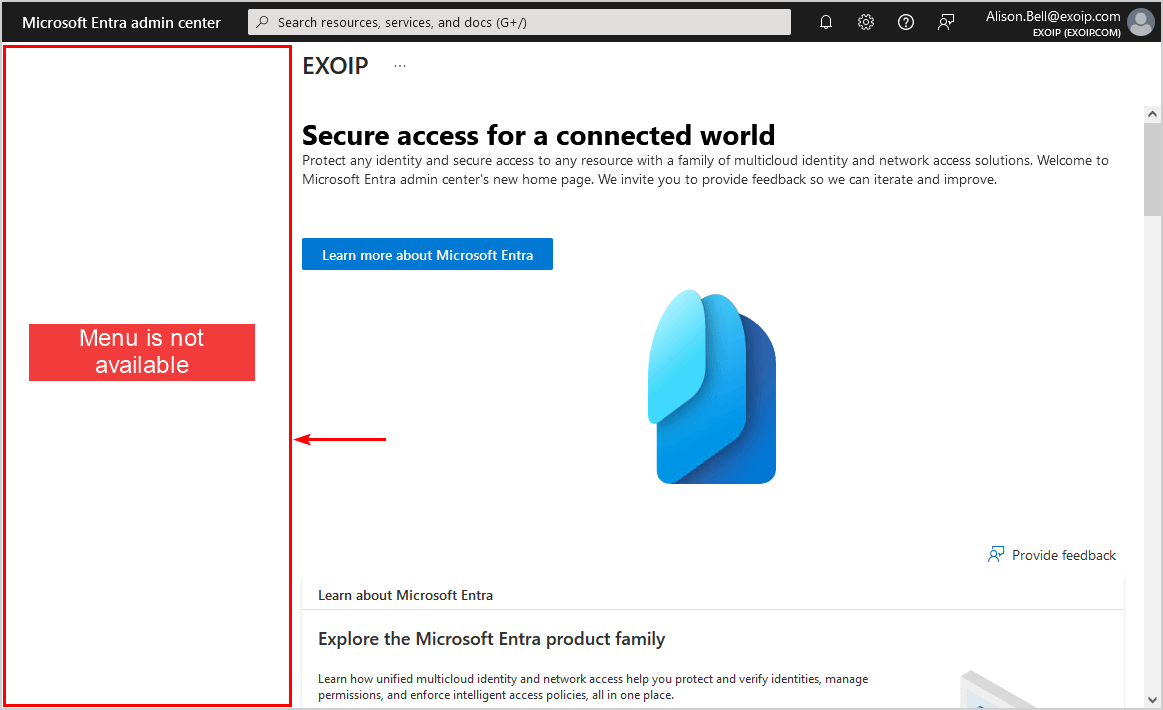
- Sign in to Microsoft Entra admin center as a User
- The sidebar menu is not available
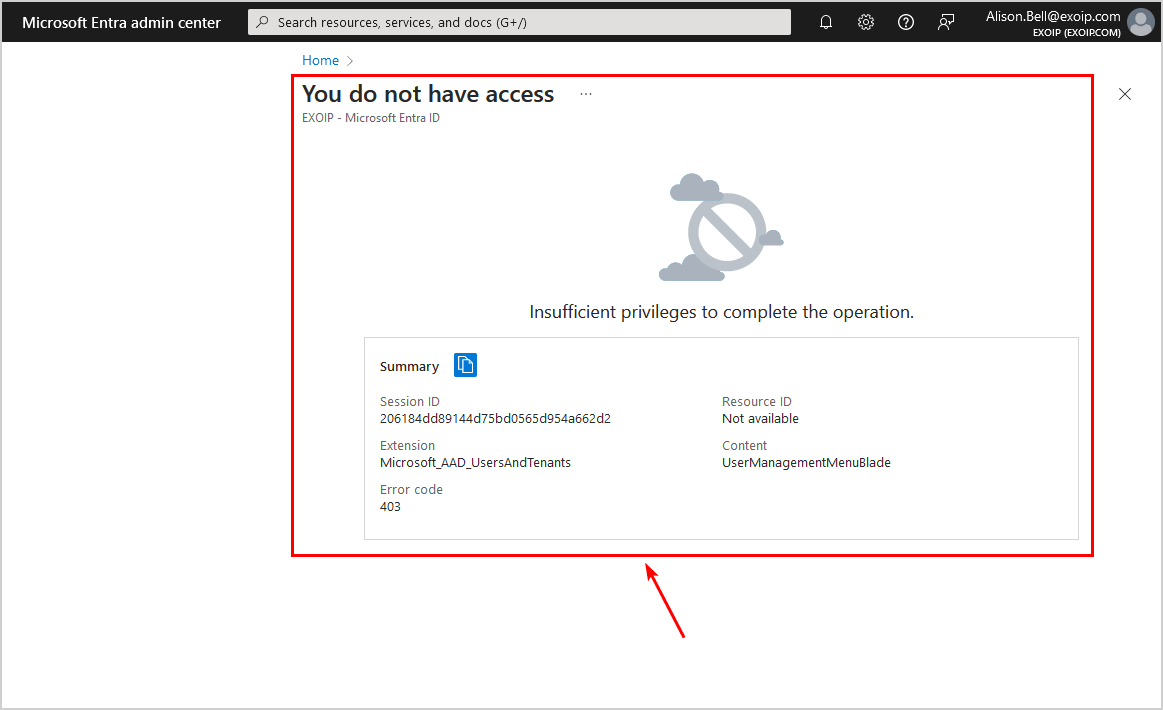
- Go to a direct link in Microsoft Entra admin center (for example, All users)
- The You do not have access message appears
Verify access to PIM (Privileged Identity Management)
You can access the PIM blade, even if you have restrictions everywhere else in the Microsoft Entra admin center. So you can always manage your privileged access.
Note: Every user can access the Privileged Identity Management (PIM) blade.
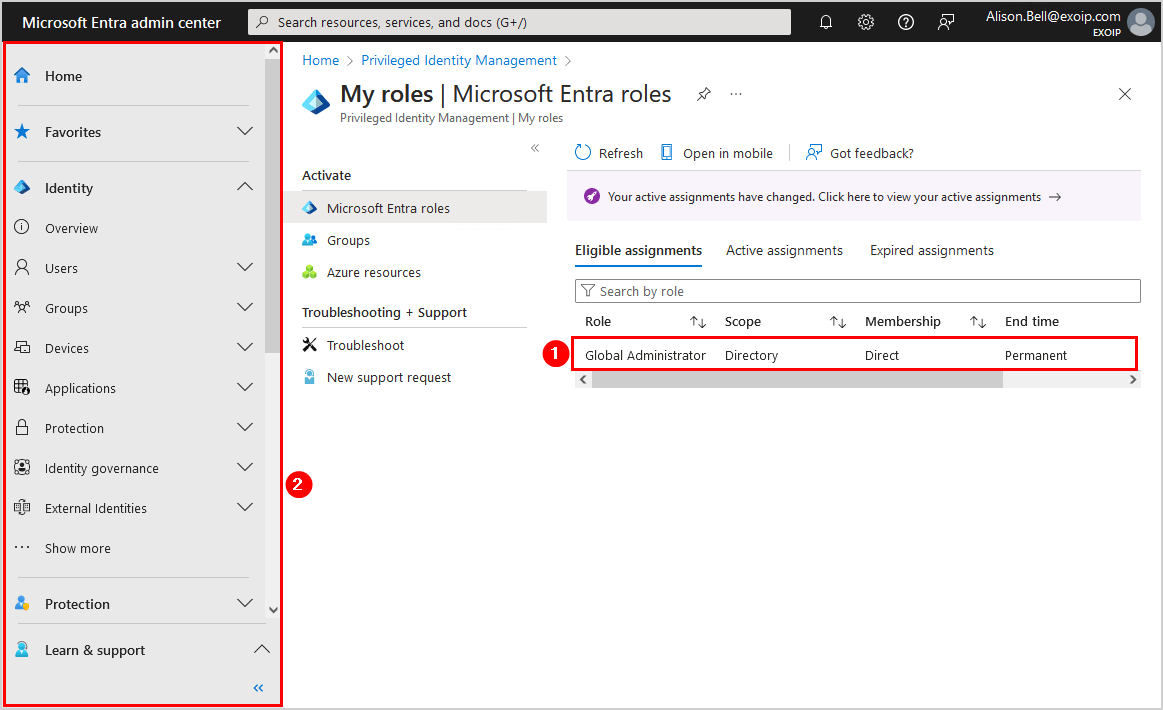
Let’s look at activating the Global Administrator role using PIM:
- Sign in to the PIM blade as a User
- Click My roles
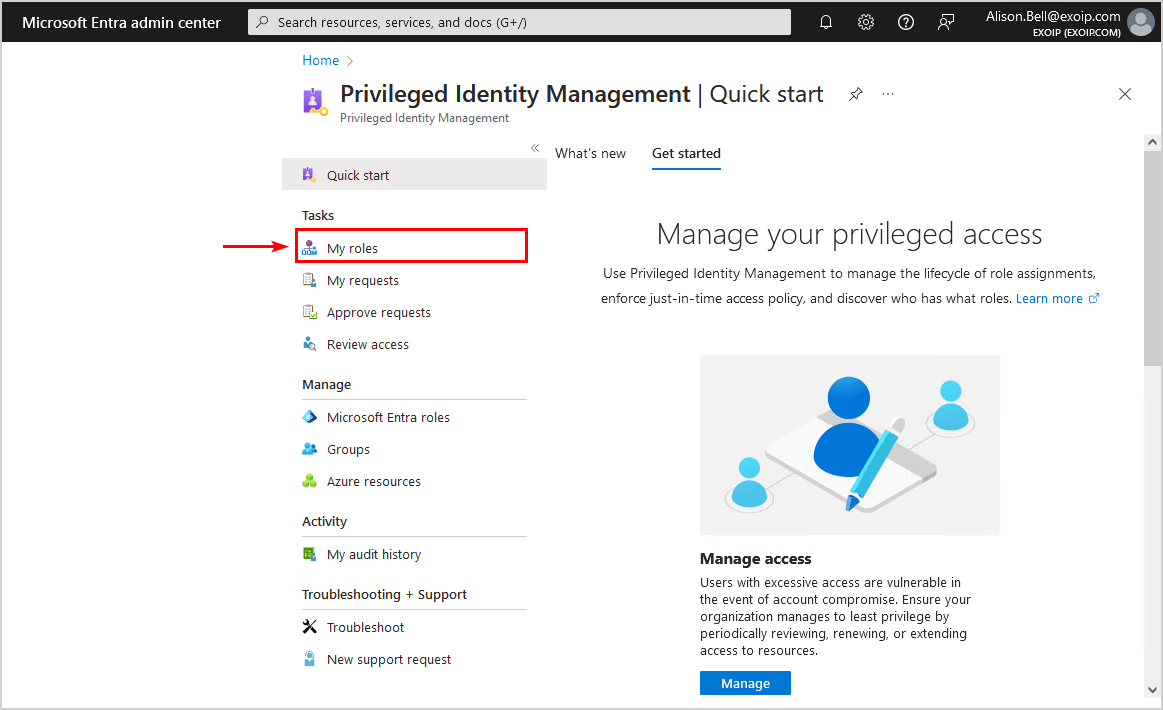
- Select Activate
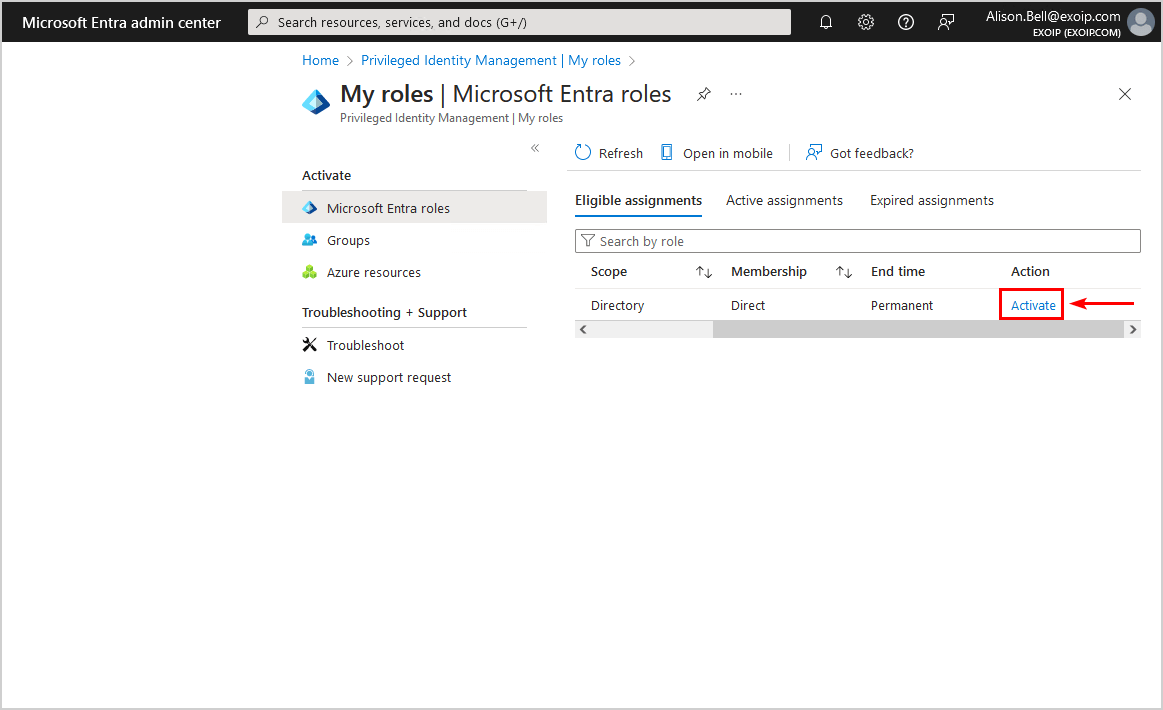
- Fill in a reason
- Click Activate
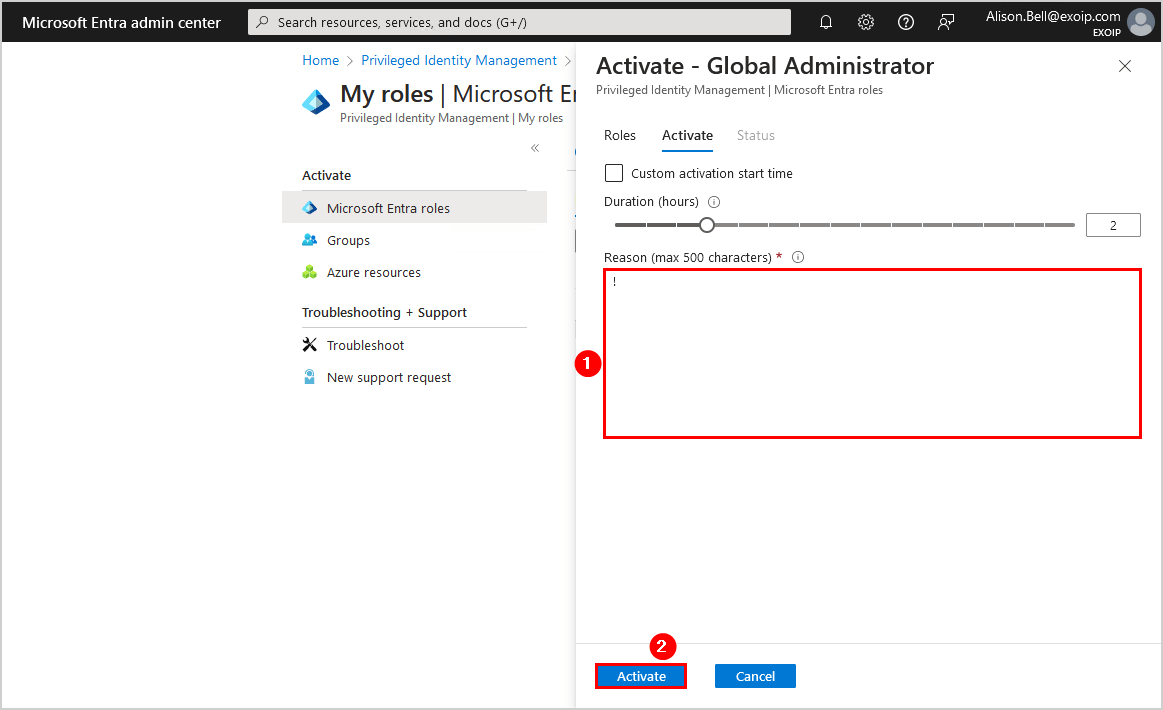
- It will process the request, activate the role, and refresh automatically once it is complete
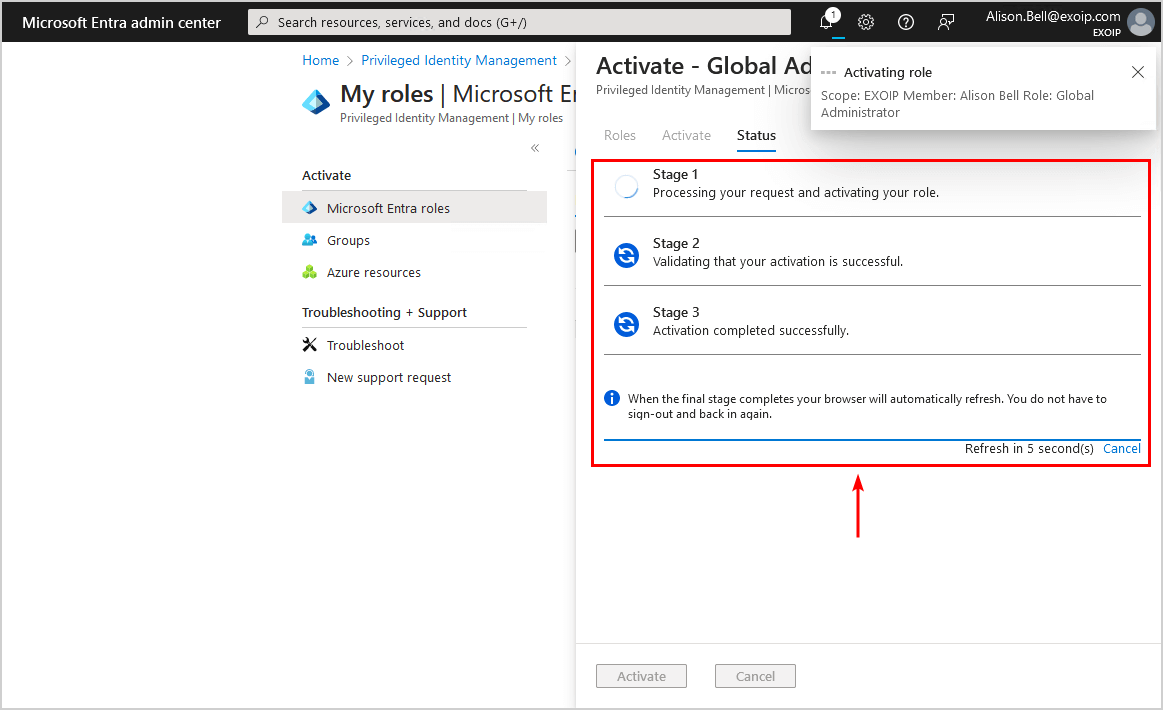
- The completion is successful, and all the options, including the sidebar menu, are available in Microsoft Entra admin center
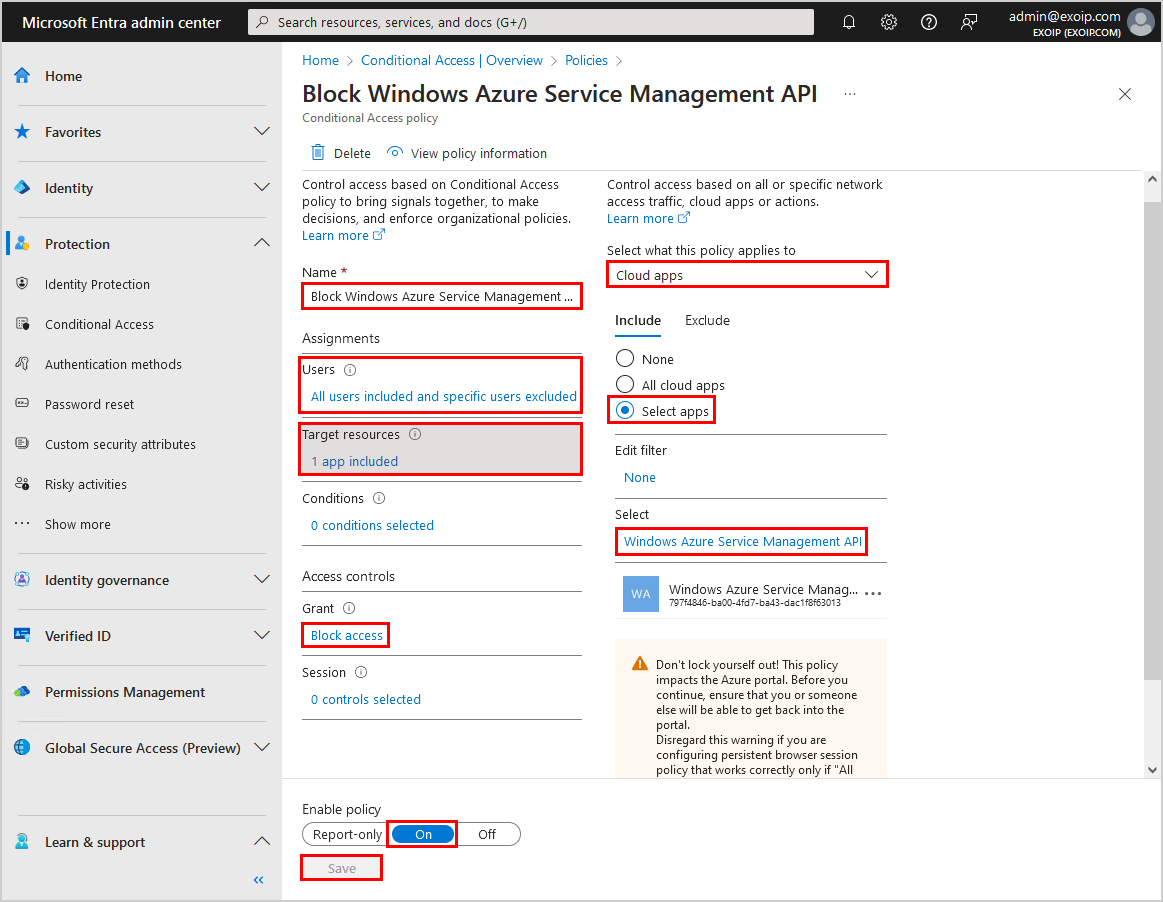
Block user access with Conditional Access policy
Using the Restrict access to Microsoft Entra admin center switch is not a security measure.
The correct way is to create a Conditional Access policy and target Windows Azure Service Management API that blocks non-administrators access.
This will target the following:
- Azure Resource Manager
- Azure portal
- Microsoft Entra admin center
- Azure Data Lake
- Application Insights API
- Log Analytics API
Sign in to Microsoft Entra admin center as a user. The You don’t have access to this message appears.
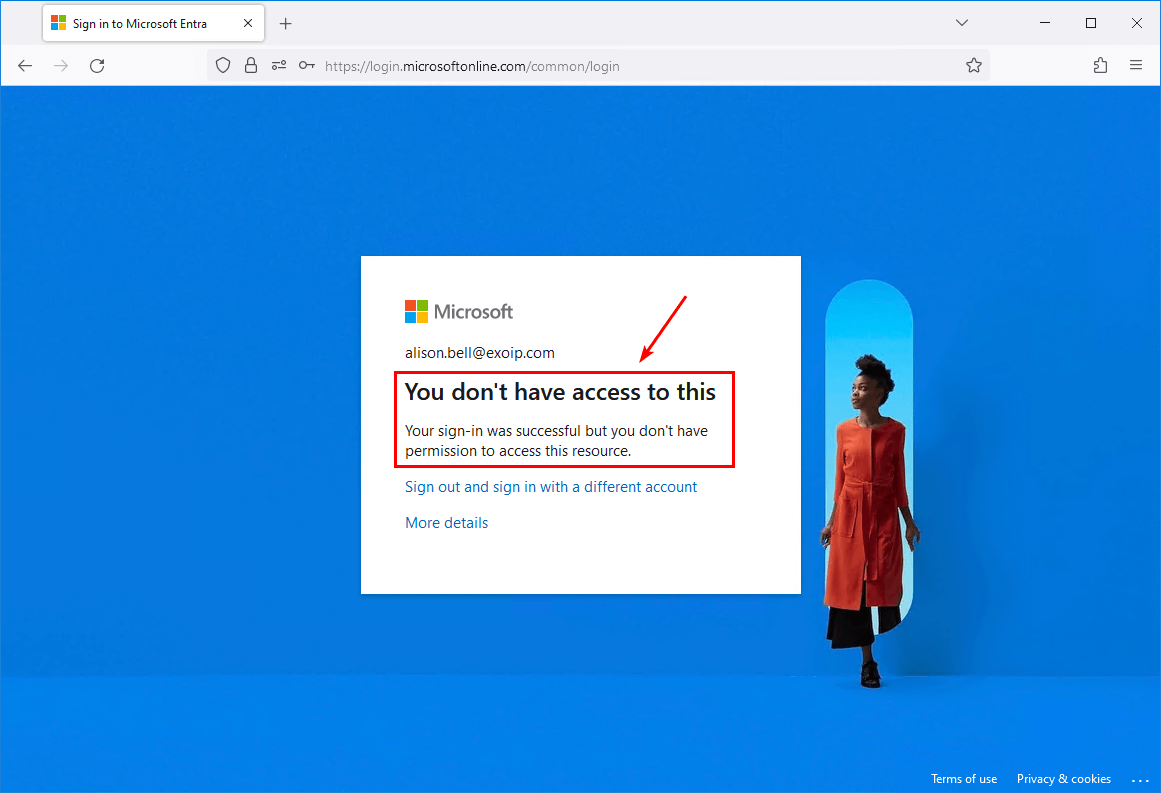
That’s it!
Read more: Install and configure Azure AD Connect »
Conclusion
You learned how to restrict access to Microsoft Entra admin center. The option is by default set to No. But we highly recommend setting it to Yes and restrict user access to Microsoft Entra admin center for non-administrator accounts.
The next time you manage a Microsoft Entra tenant or create a new Microsoft tenant, check the restrict access to Microsoft Entra admin center setting and ensure to turn it on.
Did you enjoy this article? You may also like Microsoft 365 disable stay signed in prompt. Don’t forget to follow us and share this article.



Hi have you run into an issue where you blocked the Windows Azure Service Management API, but then users cannot sign into office 365 portal? It says they don’t have access to this app even though it should only block admin portals
That’s correct. It should only block the admin portals. I have the CA policy applied, and all users can sign in to the Microsoft 365 portal.
I find the behavior of the option “Restrict access to Microsoft Admin center” really weird.
You don’t see the menu. But you can login on the portal and if you scroll down you can acces All Groups and All Devices for instance. I would expect that shouldn’t be the case also.
That’s correct. Microsoft should disable that when you enable the setting “Restrict access to Microsoft Admin center”. Unfortunately, that’s not the case.
Set up a Conditional Access policy and block it from there (as shown in the article). That’s the best method to block non-administrators access.