You did remove full access permission from a user or shared mailbox, which is automapped.…
How to disable Group Writeback v2 in Microsoft Entra Connect
Microsoft is discontinuing Group Writeback in June 2024. It’s essential to check if your organization makes use of it. If so, you need to make the necessary changes. In this article, you will learn how to disable Group Writeback v2 in Microsoft Entra Connect.
Group writeback v2 discontinued
The public preview of Group Writeback v2 in Microsoft Entra Connect Sync will no longer be available after June 30, 2024. This feature will be discontinued on this date, and you will no longer be supported in Connect Sync to provision cloud security groups to Active Directory.
The Unified Group Writeback that refers to the original version will keep working, and you can read more about how to set it up in the articles below:
- How to enable Group Writeback in Microsoft Entra Connect Sync
- Configure Microsoft 365 groups in Exchange Hybrid
How to disable Group Writeback v2
To disable Group Writeback v2 in Microsoft Entra Connect Sync, follow the below steps.
Step 1. Get Group Writeback v2 status
Sign in on the Microsoft Entra Connect Server. Run PowerShell administrator and run the Get-ADSyncAADCompanyFeature cmdlet to get the Group Writeback v2 status.
Get-ADSyncAADCompanyFeatureThe PowerShell output shows that GroupWriteBackV2 is enabled because the value is True.
Note: UnifiedGroupWriteback refers to the original version, which will keep working. GroupWritebackV2 refers to the new version that will be discontinued.
PasswordHashSync : True
ForcePasswordChangeOnLogOn : False
UserWriteback : False
DeviceWriteback : False
UnifiedGroupWriteback : True
GroupWritebackV2 : TrueIf the value is False for GroupWritebackV2, you don’t have to go through the steps below, and everything is set. Just update the team and the documentation that Group Writeback v2 in Microsoft Entra Connect Sync is discontinued after June 30, 2024.
Step 2. Get security groups with Group Writeback enabled
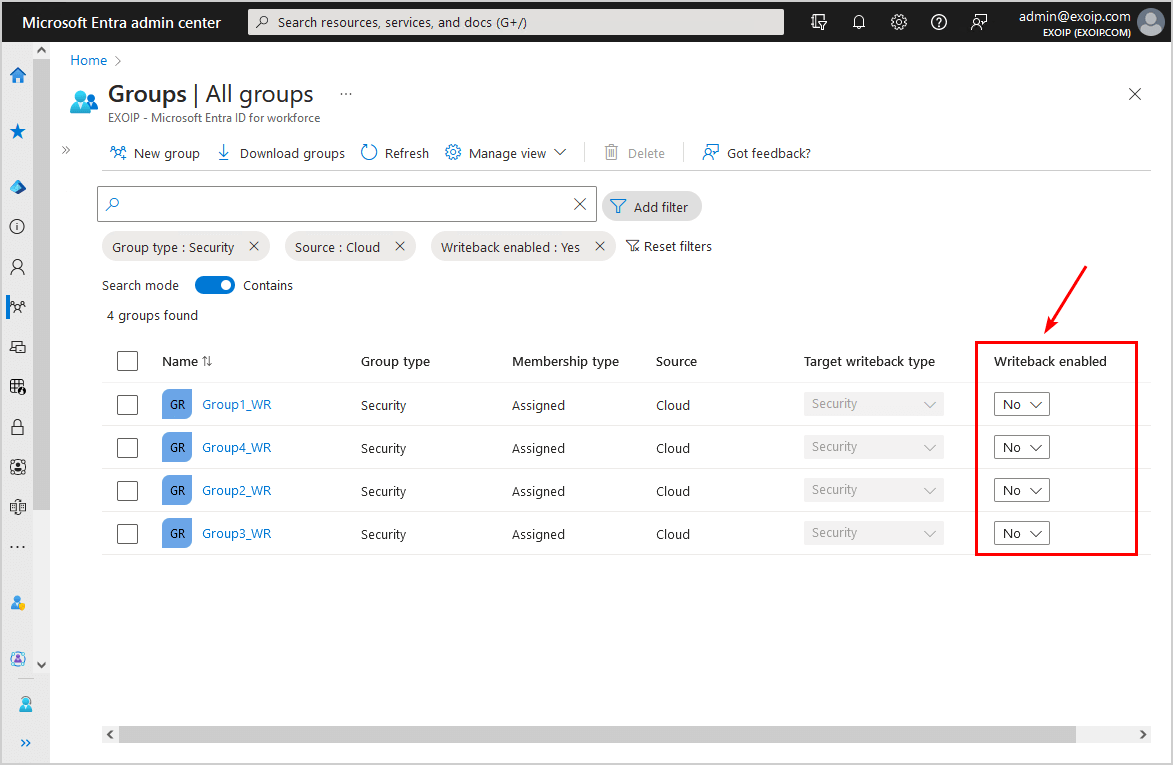
To get a list view of which security groups have Group Writeback v2 enabled, filter them in Microsoft Entra ID.
Sign in to Microsoft Entra admin center. Click on Identity > Groups > All Groups.
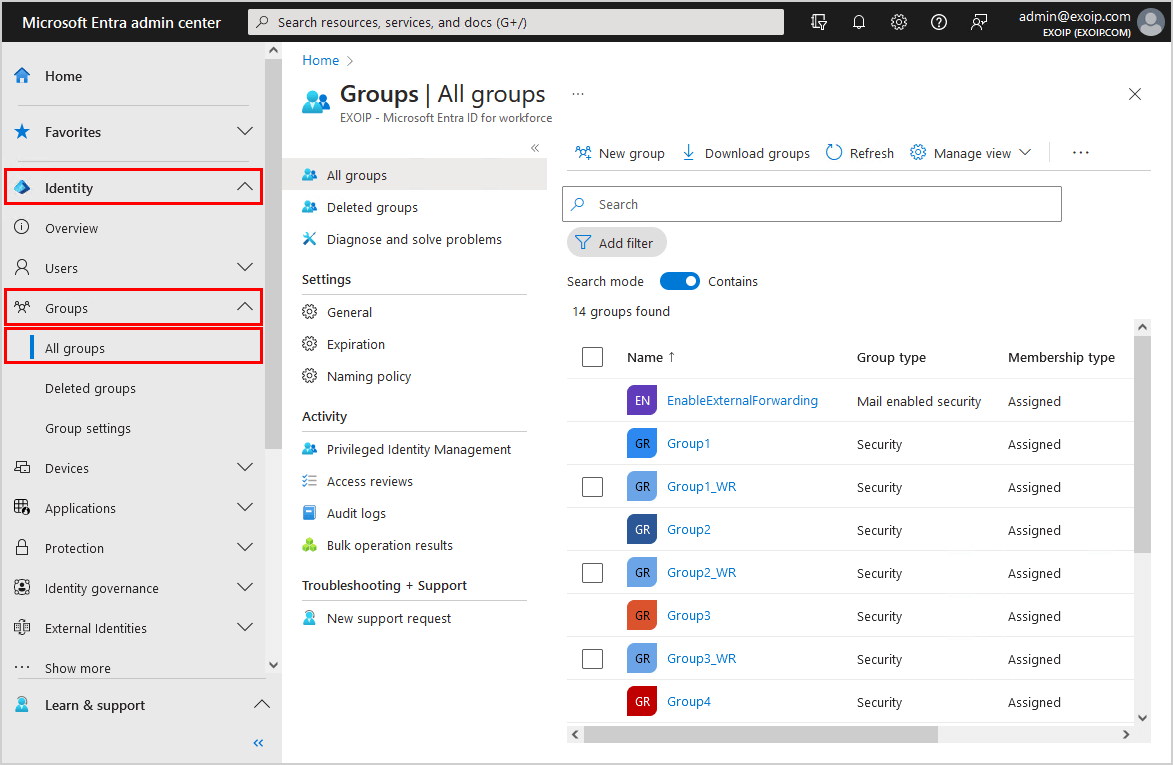
Click Manage view > Edit columns.
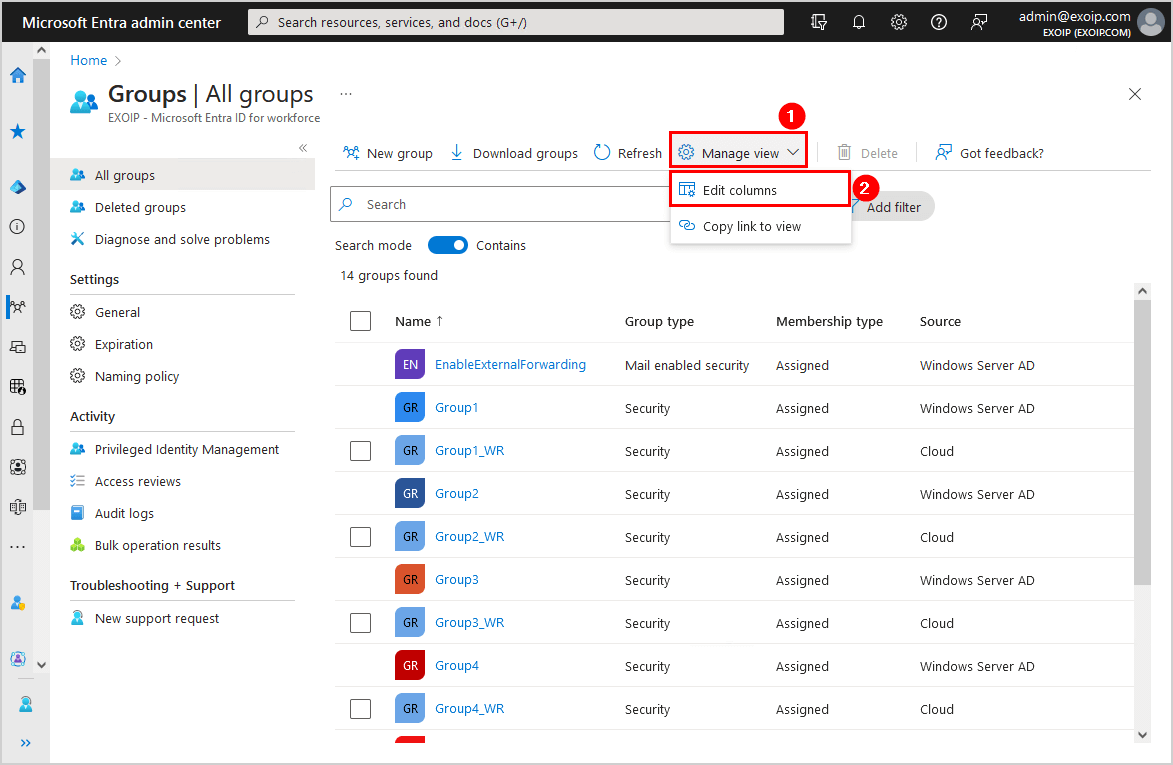
Check both columns Target writeback type/Writeback enabled. Click Save.
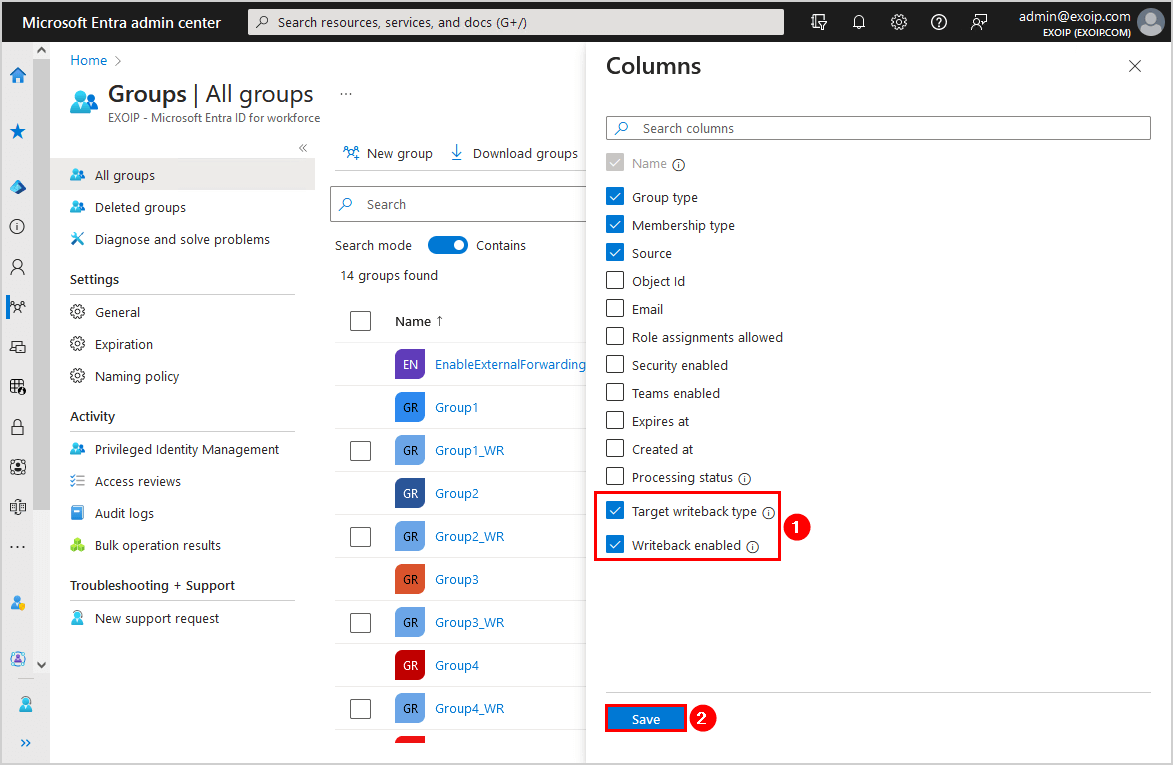
Filter the groups to show only the AAD groups:
- Click on Add filter
- Select Filter – Group type and Value – Security
- Click on Apply
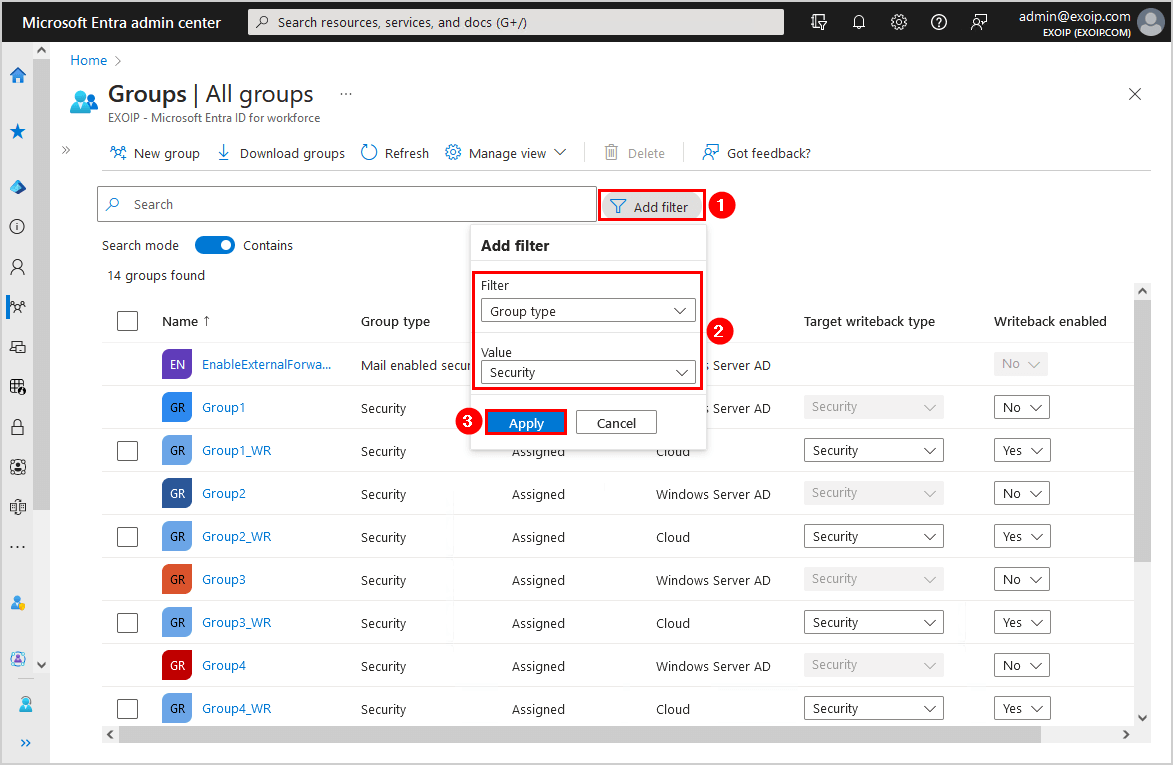
- Click on Add filter
- Select Filter – Source and Value – Cloud
- Click on Apply
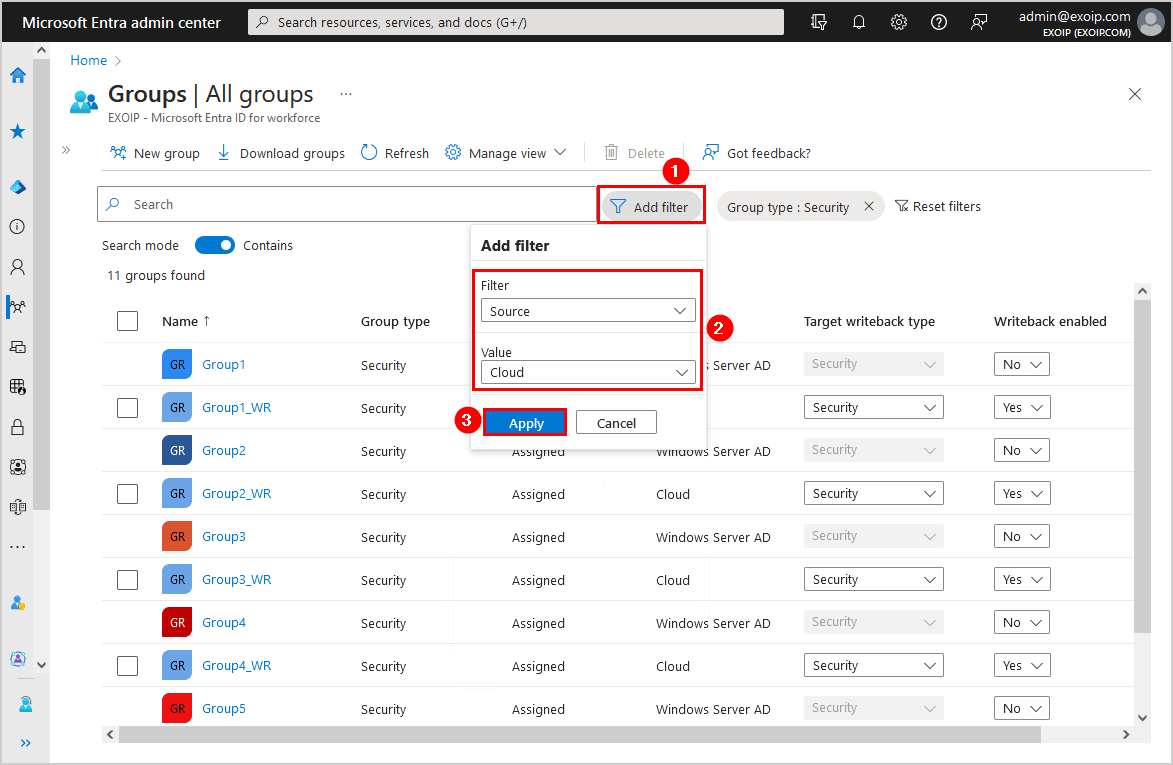
- Click on Add filter
- Select Filter – Writeback enabled and Value – Yes
- Click on Apply
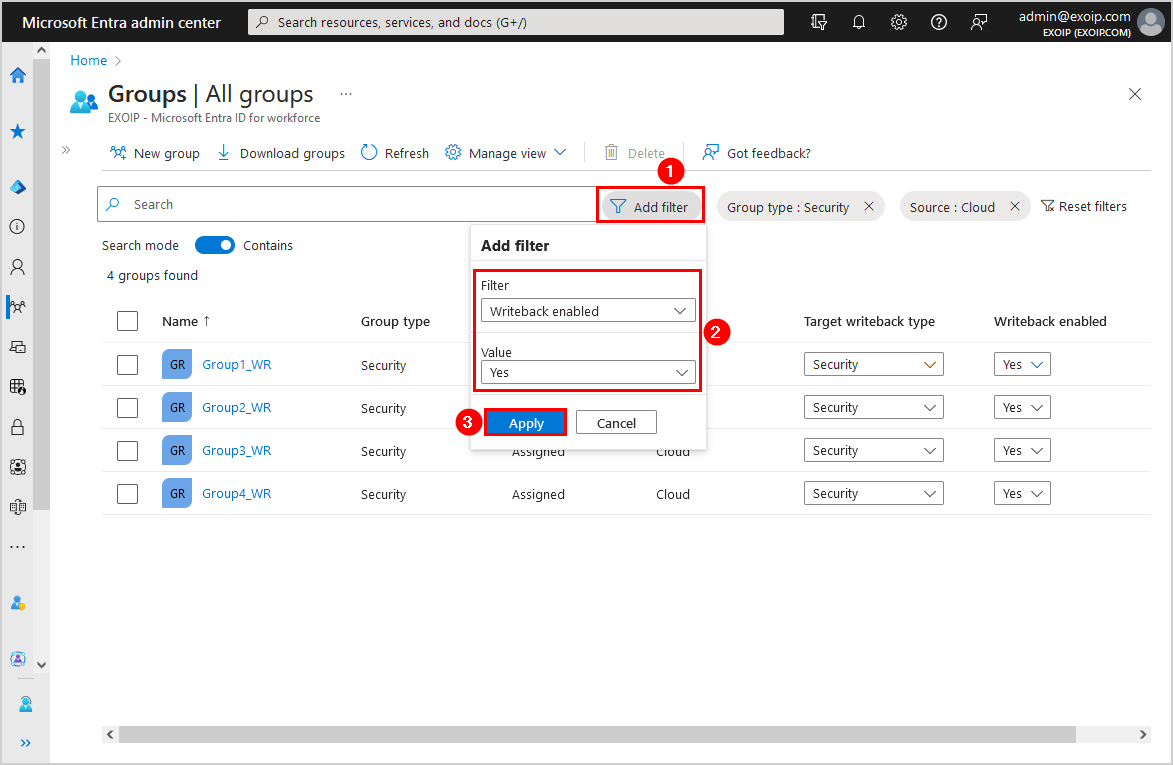
This is how it looks when you have set the three filters.
Another way to check is with Microsoft Graph PowerShell.
Run Windows PowerShell as administrator and Install Microsoft Graph PowerShell.
Install-Module Microsoft.Graph -ForceInstall-Module Microsoft.Graph.Beta -AllowClobber -ForceImportant: Always install the Microsoft Graph PowerShell and Microsoft Graph Beta PowerShell modules. That’s because some cmdlets are not yet available in the final version, and they will not work. Update both modules to the latest version before you run a cmdlet or script to prevent errors and incorrect results.
Run the script below.
# Connect to MgGraph with necessary scope
Connect-MgGraph -Scopes "Group.ReadWrite.All"
Get-MgBetaGroup -All |
Where-Object {
$_.writebackConfiguration.onPremisesGroupType -eq "universalSecurityGroup" -and
$_.writebackConfiguration.isEnabled -eq $true
} |
Select-Object DisplayName, @{
Name = "WriteBackEnabled"
Expression = { $_.writebackConfiguration.isEnabled }
}, @{
Name = "OnPremisesGroupType"
Expression = { $_.writebackConfiguration.onPremisesGroupType }
} |
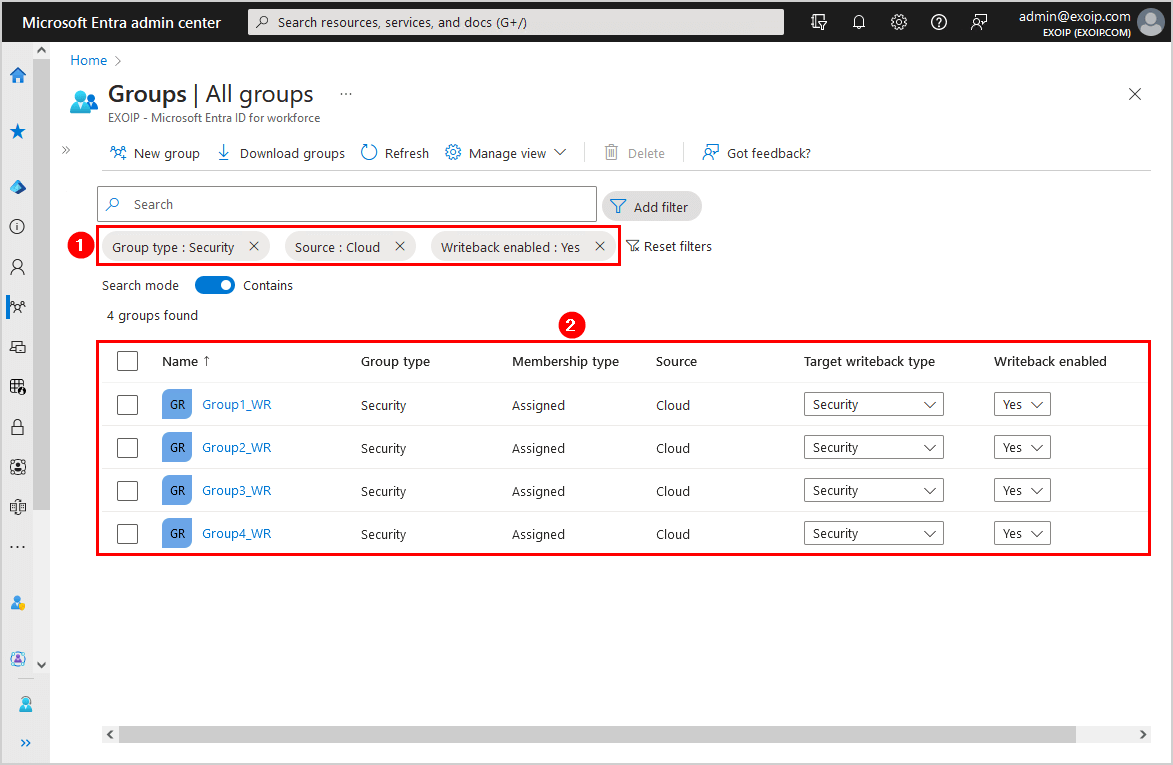
Sort-Object DisplayNameThe output shows the cloud security groups with writeback enabled.
DisplayName WriteBackEnabled OnPremisesGroupType
----------- ---------------- -------------------
Group1_WR True UniversalSecurityGroup
Group2_WR True UniversalSecurityGroup
Group3_WR True UniversalSecurityGroup
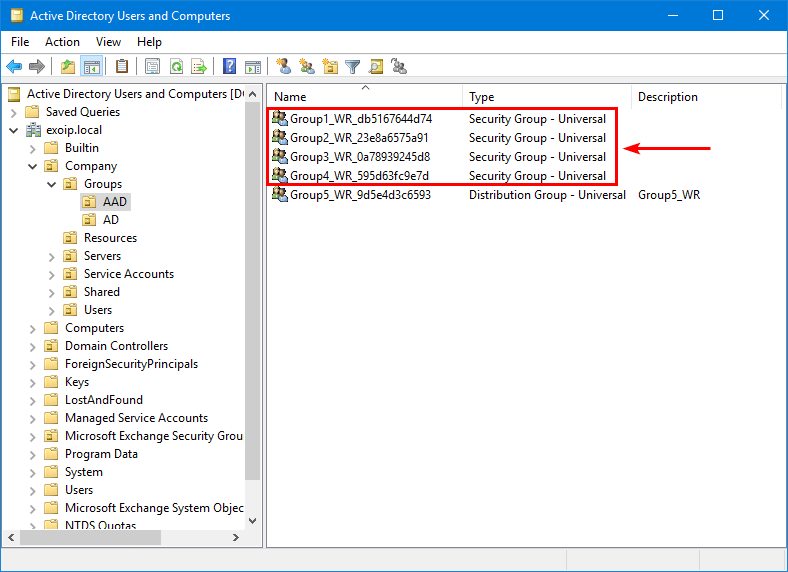
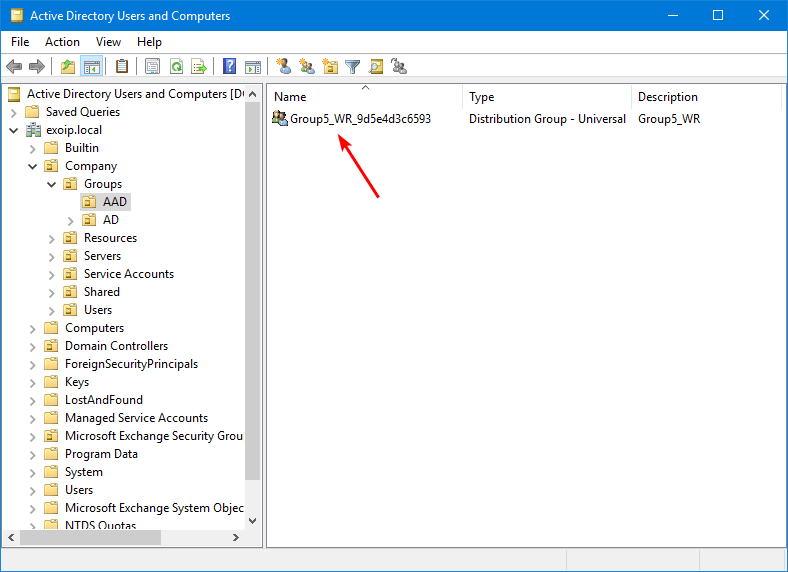
Group4_WR True UniversalSecurityGroupYou can also check the cloud security groups with writeback enabled in Active Directory on-premises. Start Active Directory Users and Computers and check for Security Group type.
Step 3. Disable Group Writeback for cloud security groups
In the filtered groups list, disable all the Writeback enabled for the cloud security groups by changing the value to No.
It’s faster and recommended to do it with PowerShell. Run the script below.
# Connect to MgGraph with necessary scope
Connect-MgGraph -Scopes "Group.ReadWrite.All"
# List all cloud security groups with writeback enabled
$Groups = Get-MgBetaGroup -All |
Where-Object {
$_.writebackConfiguration.onPremisesGroupType -eq "universalSecurityGroup" -and
$_.writebackConfiguration.isEnabled -eq $true
}
# Disable writeback for cloud security groups
foreach ($Group in $Groups) {
Update-MgBetaGroup -GroupId $Group.Id -WritebackConfiguration @{isEnabled = $false }
}Step 4. Disable Group Writeback v2 in Microsoft Entra Connect Sync
Sign in on the Microsoft Entra Connect Server. Start Windows PowerShell and run the below command to disable the Group Writeback v2 feature in the tenant.
Set-ADSyncAADCompanyFeature -GroupWritebackV2 $falseNow run a Force sync in Microsoft Entra Connect.
Start-ADSyncSyncCycle -PolicyType InitialGive it a few minutes to sync the data between AD on-premises and Entra ID.
Step 5. Verify security groups are removed from AD on-premises
Verify that the security groups don’t appear in Active Directory on-premises. The Microsoft 365 cloud groups should still be available.
That’s it!
Read more: Migrate Azure AD Connect to new server »
Conclusion
You learned how to disable Group Writeback v2 in Microsoft Entra Connect. Follow the steps to disable Group Writeback for the cloud security groups and update your documentation. If you want to use the Group Writeback feature for security groups, you must look into Microsoft Entra Cloud Sync.
Did you enjoy this article? You may also like Find Azure AD Connect accounts. Don’t forget to follow us and share this article.



Is there any difference to just disable it from ad connect wizard ?
There is no option to disable Group Writeback v2 through the Microsoft Entra Connect wizard.
Disabling the “Group Writeback” feature from the Microsoft Entra Connect wizard will disable Group Writeback v2 and Unified Group Writeback.
You don’t want to do this because Unified Group Writeback will keep working and is not being discontinued.
Following the steps described in this guide ensures you only turn off Group Writeback v2.