We have Azure AD Connect V1 running in the organization. We like to upgrade from…
Export Entra ID app registrations Certificates and Secrets expiry report
You need a quick way that shows you all the Entra ID app registrations certificates or secrets and their expiration date. If you don’t renew before that time, the connection to the app will not work anymore. So it’s important not to let the certificates or secrets for the app registrations expire. In this article, you will learn how to export Entra ID app registrations with their certificates and client secrets expiry dates to a report using Microsoft Graph PowerShell.
Table of contents
Check application registration Certificates and Secrets expiration dates in Microsoft Entra
To check if the app registrations certificate or secret has expired, go through the below steps:
- Sign in to Microsoft Entra admin center
- Expand Identity > Applications > App registrations
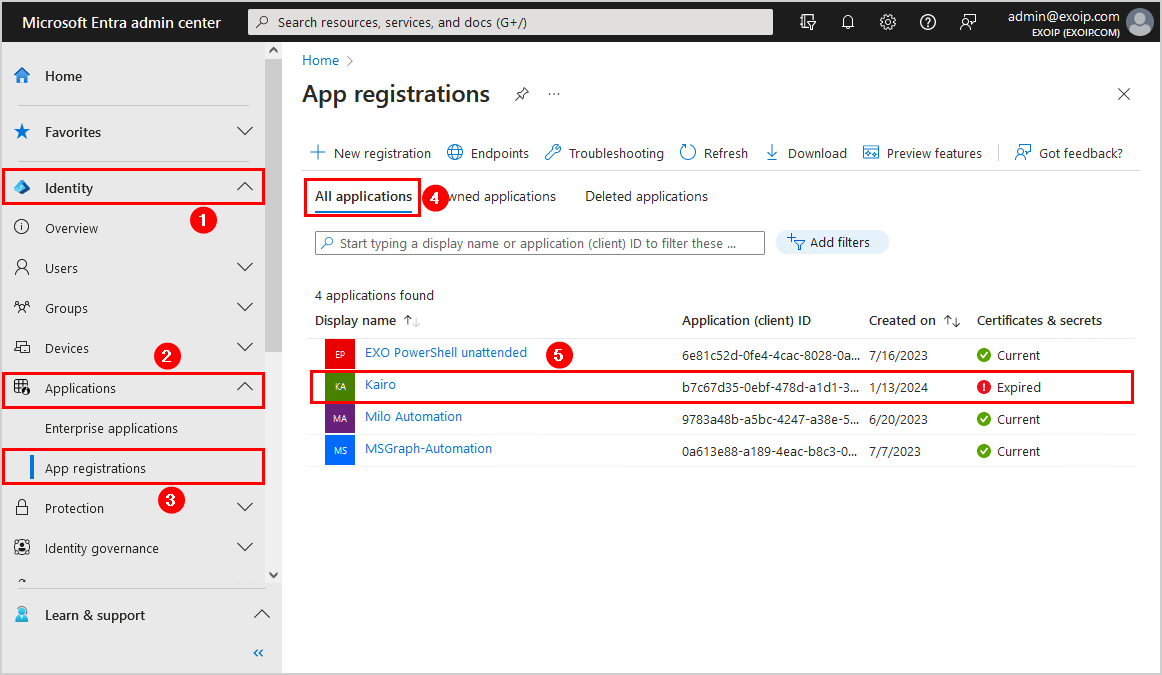
- Select All applications
- Click on the application that you want to check the certificate expiration status for
In our example, we have 4 applications, and the application Kairo shows that the certificate & secrets are expired.
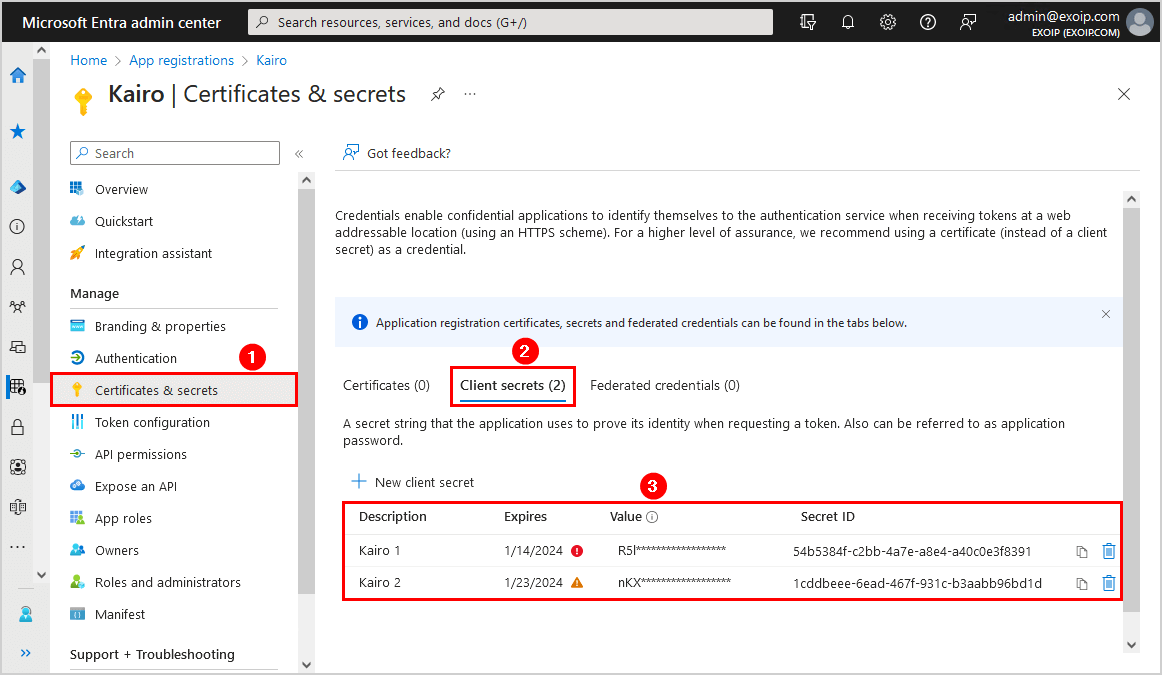
- Click Certificates & secrets
- Select Certificates or Client secrets
In our example, the application Kairo only has clients secrets and no certificates. One client secret is expired (red), and the other one expires soon (orange).
To Renew the client secret in Microsoft Entra ID, we need to create a new client secret and delete the expired client secret.
Going through all the applications and checking the certificate or client secret expiration date, including their status, takes time. So, the best way is to run a PowerShell script that creates a report with all the information.
Let’s look at the PowerShell script in the next step.
Get Entra ID app registrations Certificates and Secrets expiration dates with PowerShell
A great way to get all the app registrations with their certificates and secrets expiration dates is with Microsoft Graph PowerShell.
The Get-AppCertSecStatus.ps1 script will get all the app registrations in Microsoft Entra ID and gather the following details:
- ApplicationName
- CredentialName
- SignInType
- CreatedDateTime
- StartDateTime
- EndDateTime
- ExpireStatus
- AuthType
- DaysLeft
- Owner
- OwnerID
Step 1. Prepare Get-AppCertSecStatus PowerShell script
Create two folders on the (C:) drive:
- Temp
- Scripts
Download the Get-AppCertSecStatus.ps1 PowerShell script and place it in C:\scripts folder. The script will export the CSV file to the C:\temp folder.
Ensure the file is unblocked to prevent errors when running the script. Read more in the article Not digitally signed error when running PowerShell script.
Another option is to copy and paste the below code into Notepad. Give it the name Get-AppCertSecStatus.ps1 and place it in the C:\scripts folder.
<#
.SYNOPSIS
Get-AppCertSecStatus.ps1
.DESCRIPTION
Export Entra ID app registrations certificates and secrets expiration date.
.LINK
www.alitajran.com/export-entra-id-app-registrations-certificates-secrets/
.NOTES
Written by: ALI TAJRAN
Website: www.alitajran.com
LinkedIn: linkedin.com/in/alitajran
.CHANGELOG
V1.00, 01/14/2024 - Initial version
#>
# CSV file path to export
$CsvPath = "C:\temp\AppRegistrationsReport.csv"
# Connect to MgGraph with necessary scopes
Connect-MgGraph "Directory.Read.All", "Application.Read.All"
# Create an array
$Results = @()
# Get properties
$Properties = @(
'AppId',
'DisplayName',
'PasswordCredentials',
'KeyCredentials',
'Id',
'SignInAudience',
'CreatedDateTime'
)
# Get Applications
$Apps = Get-MgApplication -All -Property $Properties | Select-Object $Properties
foreach ($App in $Apps) {
# Get Owner information
$Owner = Get-MgApplicationOwner -All -ApplicationId $App.Id
$Username = if ($Owner) { $Owner.AdditionalProperties.userPrincipalName -join ';' } else { "N/A" }
$OwnerID = if ($Owner) { $Owner.Id -join ';' } else { "N/A" }
# Check application for client secret
if ($null -ne $App.PasswordCredentials) {
foreach ($Creds in $App.PasswordCredentials) {
# Calculate days left until expiration
$DaysLeft = ($Creds.EndDateTime - (Get-Date)).Days
# Create custom object for client secret results
$AppObject = [PSCustomObject]@{
ApplicationName = $App.DisplayName
CredentialName = $Creds.DisplayName
SignInType = $App.SignInAudience
CreatedDateTime = $App.CreatedDateTime
StartDateTime = $Creds.StartDateTime
EndDateTime = $Creds.EndDateTime
ExpireStatus = if ($Creds.EndDateTime -lt (Get-Date)) { "Expired" } else { "Not expired" }
AuthType = "Client_Secret"
DaysLeft = $DaysLeft
Owner = $Username
OwnerID = $OwnerID
}
# Output results to array
$Results += $AppObject
}
}
# Check application for certificate
if ($null -ne $App.KeyCredentials) {
foreach ($Cert in $App.KeyCredentials) {
# Calculate days left until expiration
$DaysLeft = ($Cert.EndDateTime - (Get-Date)).Days
# Create custom object for certificate results
$AppObject = [PSCustomObject]@{
ApplicationName = $App.DisplayName
CredentialName = $Cert.DisplayName
SignInType = $App.SignInAudience
CreatedDateTime = $App.CreatedDateTime
StartDateTime = $Cert.StartDateTime
EndDateTime = $Cert.EndDateTime
ExpireStatus = if ($Cert.EndDateTime -lt (Get-Date)) { "Expired" } else { "Not expired" }
AuthType = "Certificate"
DaysLeft = $DaysLeft
Owner = $Username
OwnerID = $OwnerID
}
# Output results to array
$Results += $AppObject
}
}
}
# Sort the results based on DaysLeft
$Results = $Results | Sort-Object -Property DaysLeft
# Export to CSV file
$Results | Export-Csv $CsvPath -Encoding utf8 -NoTypeInformation
# Out-GridView
$Results | Out-GridView -Title "Microsoft Entra ID app registrations report"- Line 21: Edit the CSV file path
Step 2. Install Microsoft Graph PowerShell
Run Windows PowerShell as administrator and Install Microsoft Graph PowerShell.
Install-Module Microsoft.Graph -ForceInstall-Module Microsoft.Graph.Beta -AllowClobber -ForceImportant: Always install the Microsoft Graph PowerShell and Microsoft Graph Beta PowerShell modules. That’s because some cmdlets are not yet available in the final version, and they will not work. Update both modules to the latest version before you run a cmdlet or script to prevent errors and incorrect results.
Step 3. Run Get-AppCertSecStatus PowerShell script
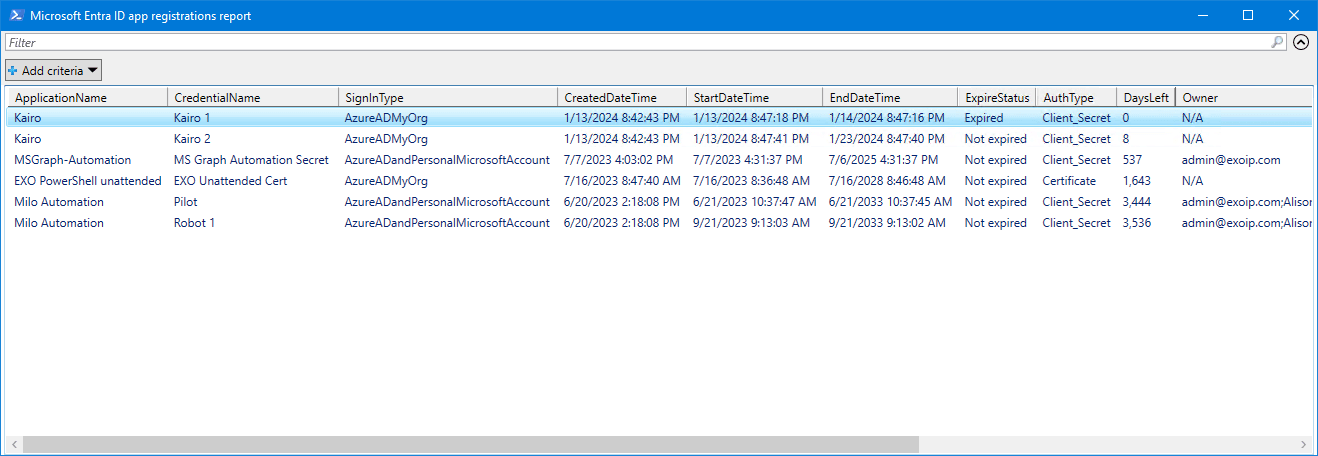
Get all the Entra ID app registrations certificates and secrets expiry dates, including their status, with PowerShell.
Run the below command to run the script Get-AppCertSecStatus.ps1.
c:\scripts\.\Get-AppCertSecStatus.ps1An Out-GridView will show all the information you need.
Step 4. Open Entra ID app registrations report
The Get-AppCertSecStatus.ps1 PowerShell script exports all app registrations with their certificate and client secret expiration status to CSV file.
Find the file AppRegistrationsReport.csv in the path C:\temp.
Open the CSV file with your favorite application. In our example, it’s Microsoft Excel.
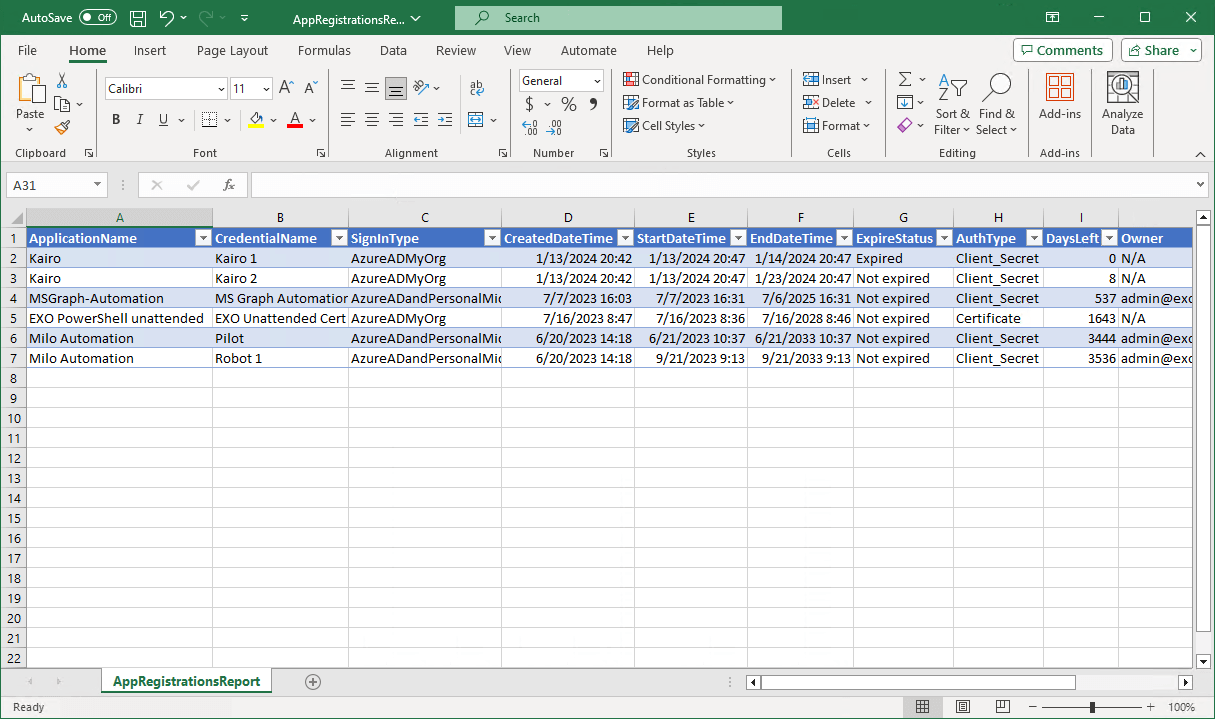
The Entra ID app registrations certificates and client secrets expiry report looks great.
Read more: Configure Exchange Online Certificate Based Authentication for unattended scripts »
Conclusion
You learned how to export Entra ID app registrations certificates and secrets with Microsoft Graph PowerShell. Run the script, and it will collect all the information and export it to a CSV file report. Ensure that you renew the certificate or client secret before it expires so the connection to the app will remain intact.
Did you enjoy this article? You may also like Export Microsoft 365 inactive users report. Don’t forget to follow us and share this article.


Great article. Thank you for sharing this valuable knowledge
Nice article. Is there any way to see the apps over tenants we are delegated admins?
Thank you
Hello Ali,
Thanks for this excellent blog. I have a question can we have this integrated with a Logic App and scheduled this which would be great. Need your inputs and suggestions on this.