It's important to go through the Exchange Hybrid test plan checklist before you start to…
Move from per-user MFA to Conditional Access MFA
It’s best to use Conditional Access based MFA when you have Microsoft Entra ID P1 or P2. It will give you more control and flexibility when creating a policy. In this Microsoft tenant, we have per-user MFA enabled. We like to convert from per-user MFA to Conditional Access based MFA. In this article, you will learn how to move from per-user MFA to Conditional Access based MFA step by step.
Table of contents
Introduction
Moving from Microsoft 365 MFA to Microsoft Entra ID Conditional Access can be done in three steps:
- Move from per-user MFA to Conditional Access MFA (this article)
- Move from MFA trusted IPs to Conditional Access named locations
- Move from remember MFA on trusted device to Conditional Access sign-in frequency
Conditional Access MFA
You want to move from per-user MFA to Conditional Access MFA without forcing all your users to re-register. Because asking your users to re-register MFA is a big task, and the IT service desk is not waiting for all these calls. The question is, is it possible to move without re-registering MFA? Yes, it is.
When you configure the Conditional Access Policy, users will not be required to re-register for MFA because disabling per-user MFA doesn’t clear the MFA methods. When you use Conditional Access Policy for MFA, you should not enable per-user MFA; keep them in a disabled state only.
Do you want to know the per-user MFA status for all the users in the organization? In a previous article, we discussed how to Export Office 365 users MFA status with PowerShell.
Check Microsoft Entra ID license
Sign in to Microsoft Entra admin center. Click on Identity > Overview. Check that you have a Microsoft Entra ID P1 or P2 license.
In this example, the tenant got the Microsoft Entra ID P2 license.
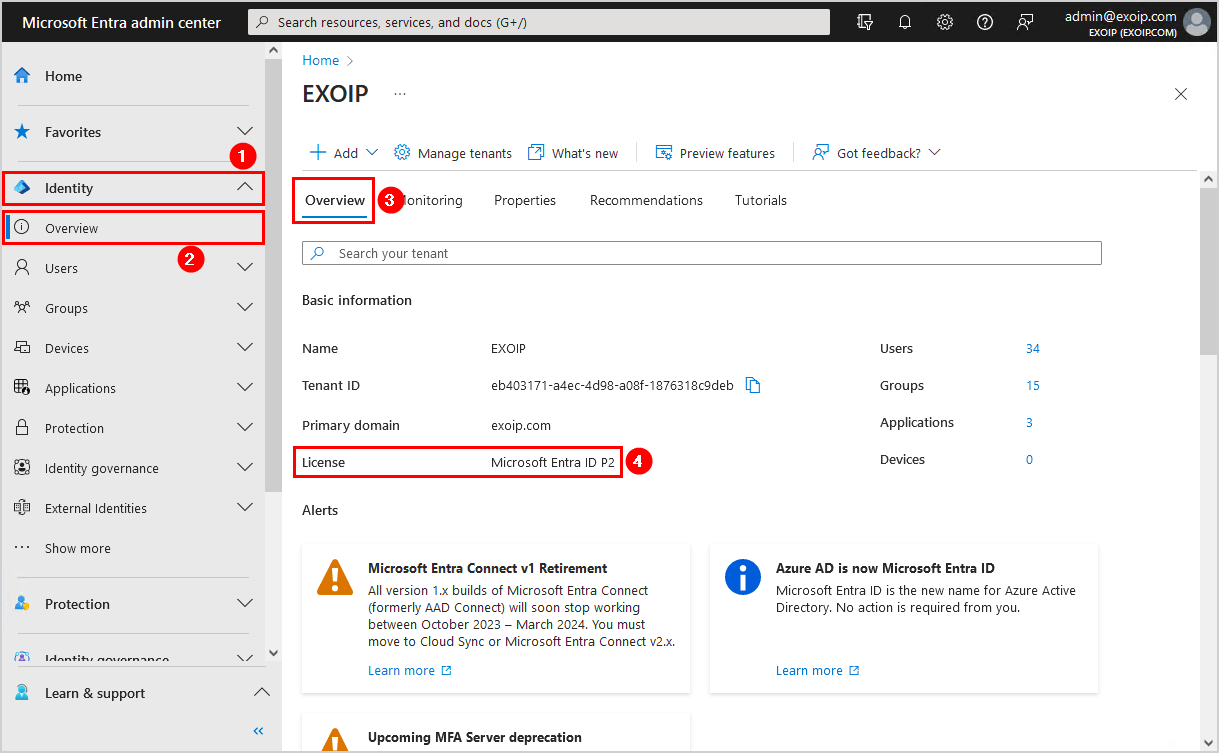
If it shows the license Microsoft Entra ID Free, you will not be able to create a Conditional Access policy. Buy a Microsoft Entra ID P1 or P2 and proceed further.
Check per-user MFA status
Let’s check the per-user MFA status for the users. Click on Users > All users > … > Per-user MFA.
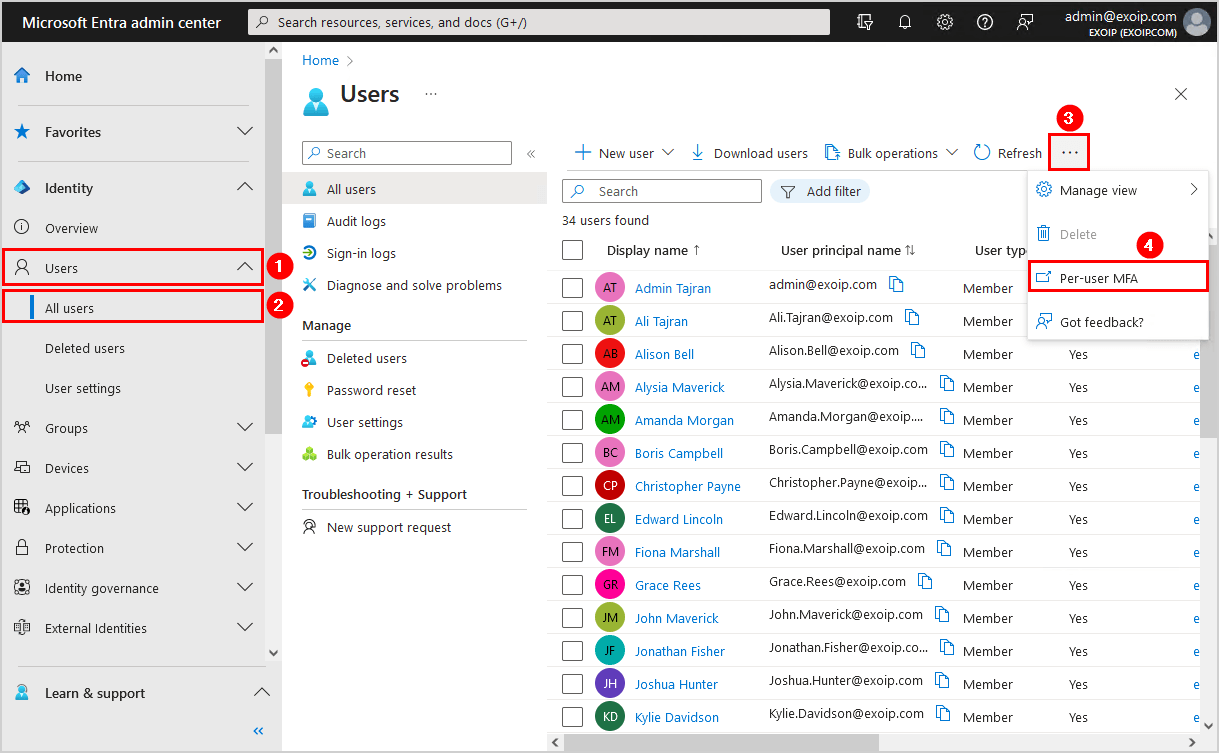
A new page will open, showing all the users and their multi-factor auth status. In our example, we have users with the MFA status enabled, enforced, and disabled.
Important: Disable per-user MFA for all users when enabling MFA using Conditional Access.
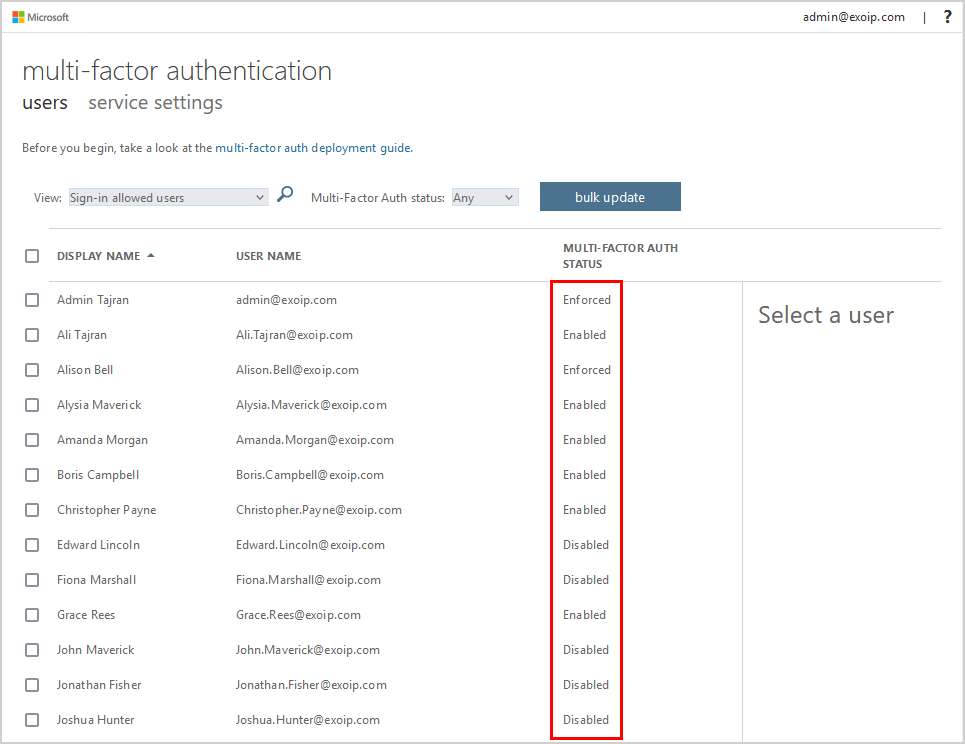
Disable per-user MFA for all users
To disable per-user MFA for all the users, you need to use the per-user MFA portal. Unfortunately, there is no way to do it with PowerShell anymore.
Disable per-user MFA for all the users and verify that all the users show the MFA status disabled.
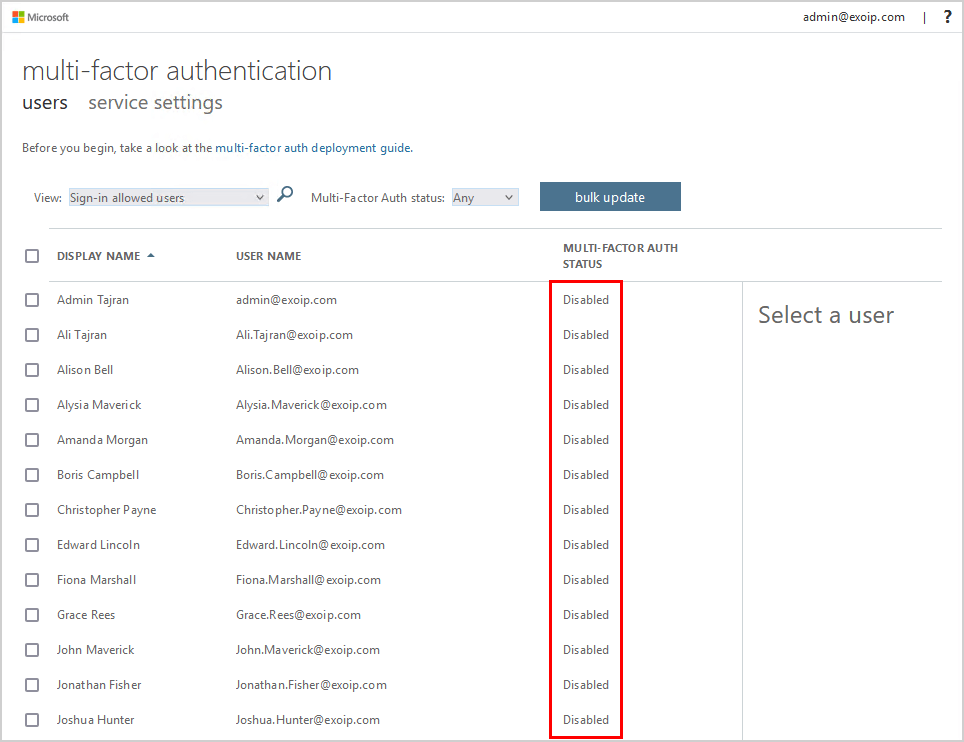
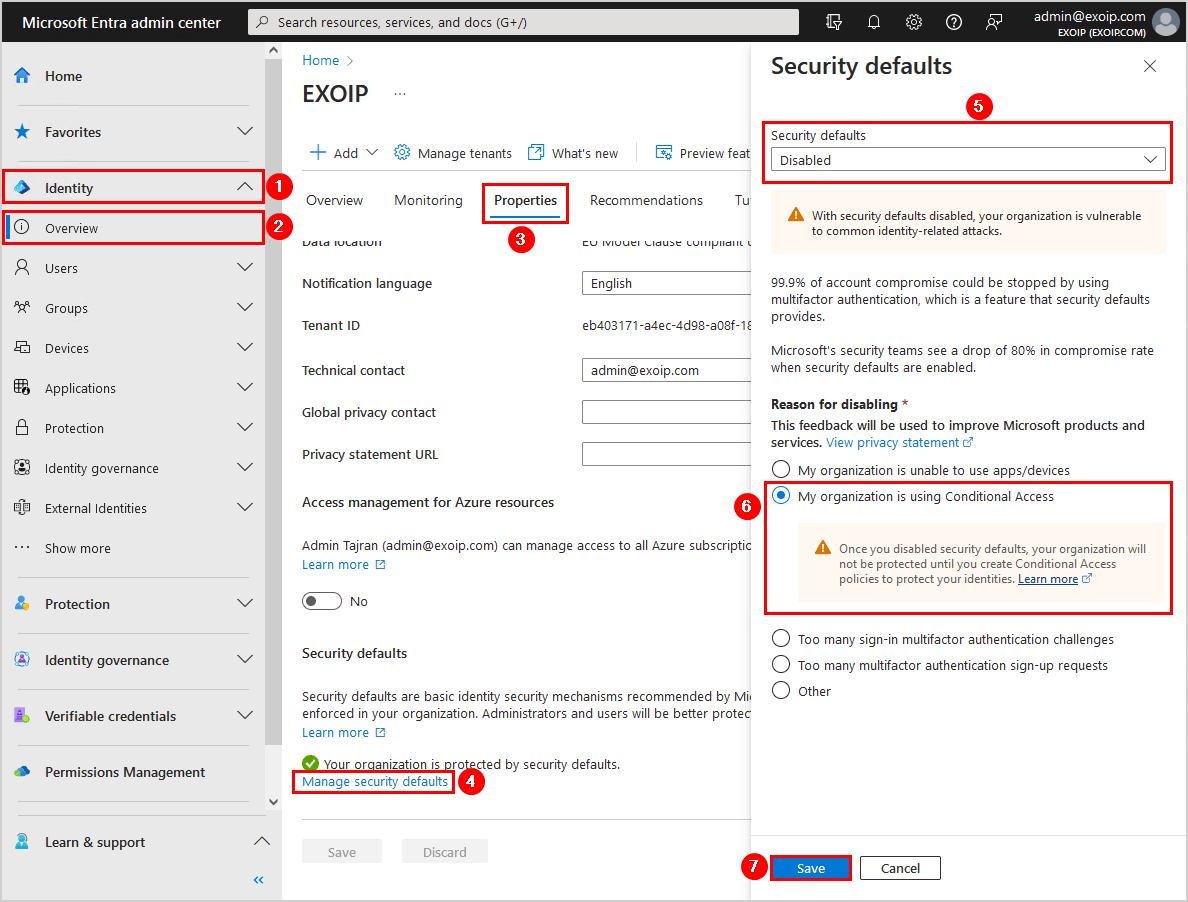
Disable security defaults in Microsoft Entra ID
You need to disable security defaults in Microsoft Entra ID. Otherwise, you can’t enable the Conditional Access policy in the next step.
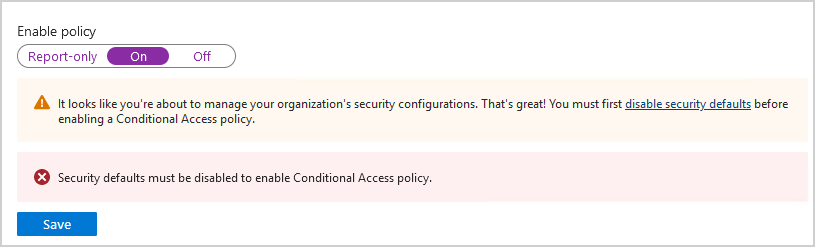
To disable security defaults in Microsoft Entra ID, follow these steps:
- Click on Identity > Overview > Properties
- Select Manage security defaults
- Set security defaults to Disabled
- Select a reason for disabling security defaults
- Click Save
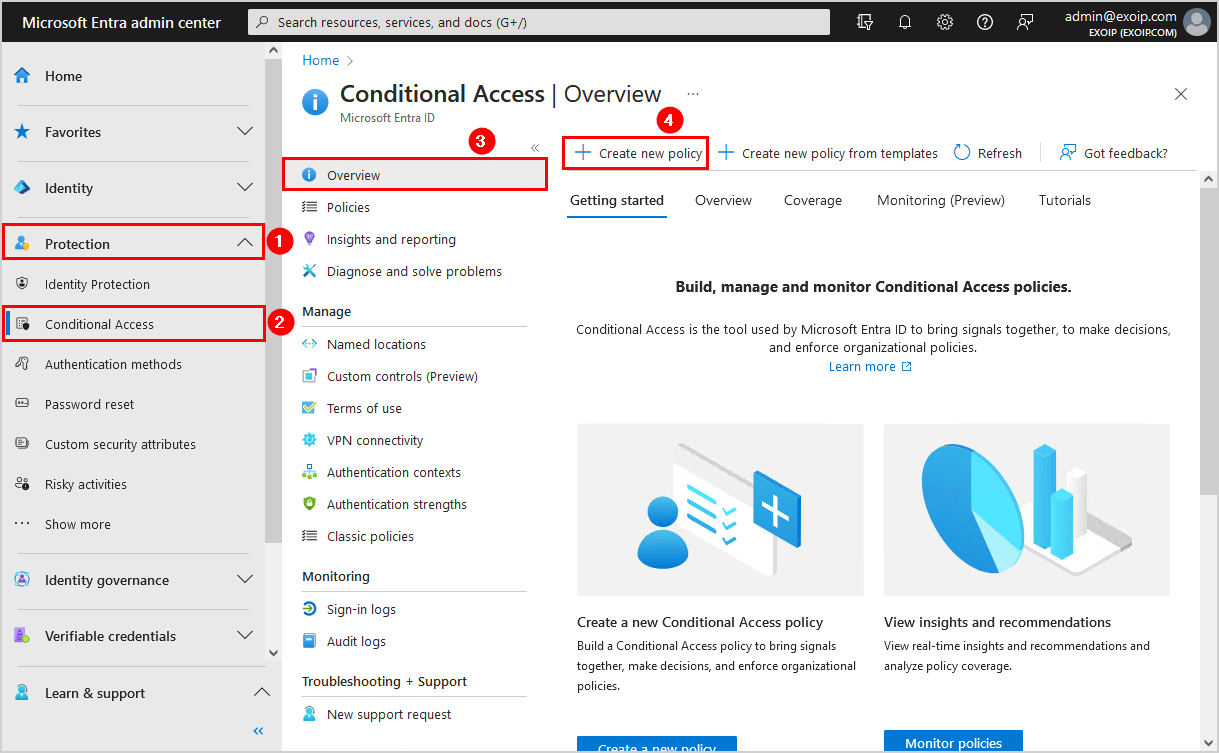
Create MFA Conditional Access policy
In the previous step, you disabled per-user MFA for all users. If you sign in with a user account, it will not ask for MFA anymore. What you need to do is create an MFA Conditional Access policy.
Navigate to Protection > Conditional Access > Overview > Create new policy.
Fill in the below:
- Name: [GRANT] Require MFA all users
- Users: All users
- Target resources: All cloud apps
- Grant: Grant access, require multifactor authentication, require one of the selected controls
- Enable policy: On
Click Create.
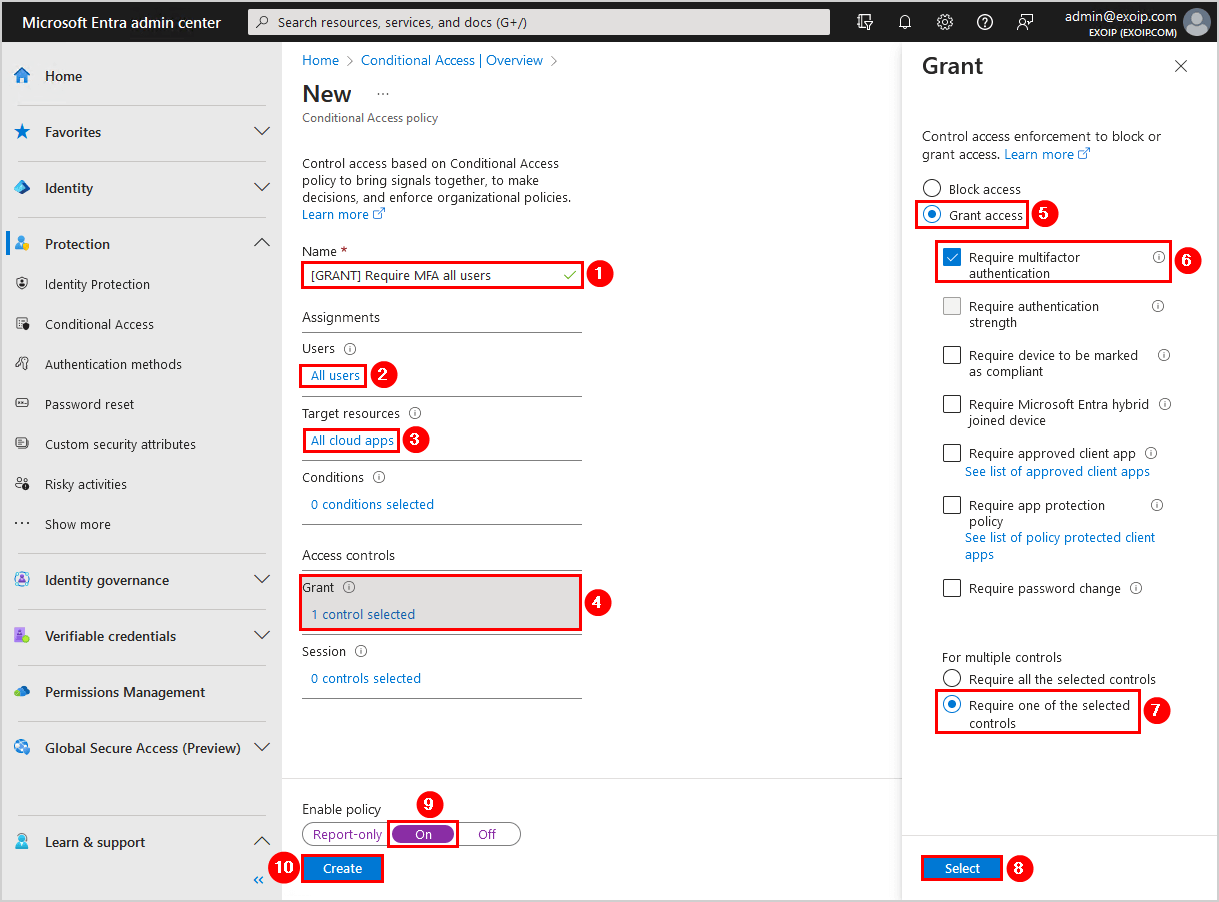
The Conditional Access policy to require MFA for all users is in place. You did successfully move from per-user MFA to Conditional Access based MFA. The last step is to verify the changes are working.
Note: It can take a couple of minutes before the Conditional Access policy change takes effect. So wait 5-10 minutes before you do a test.
Verify your work
Sign in to the Microsoft 365 portal with an account that already has MFA configured. The account will get an MFA prompt without setting up MFA from scratch.
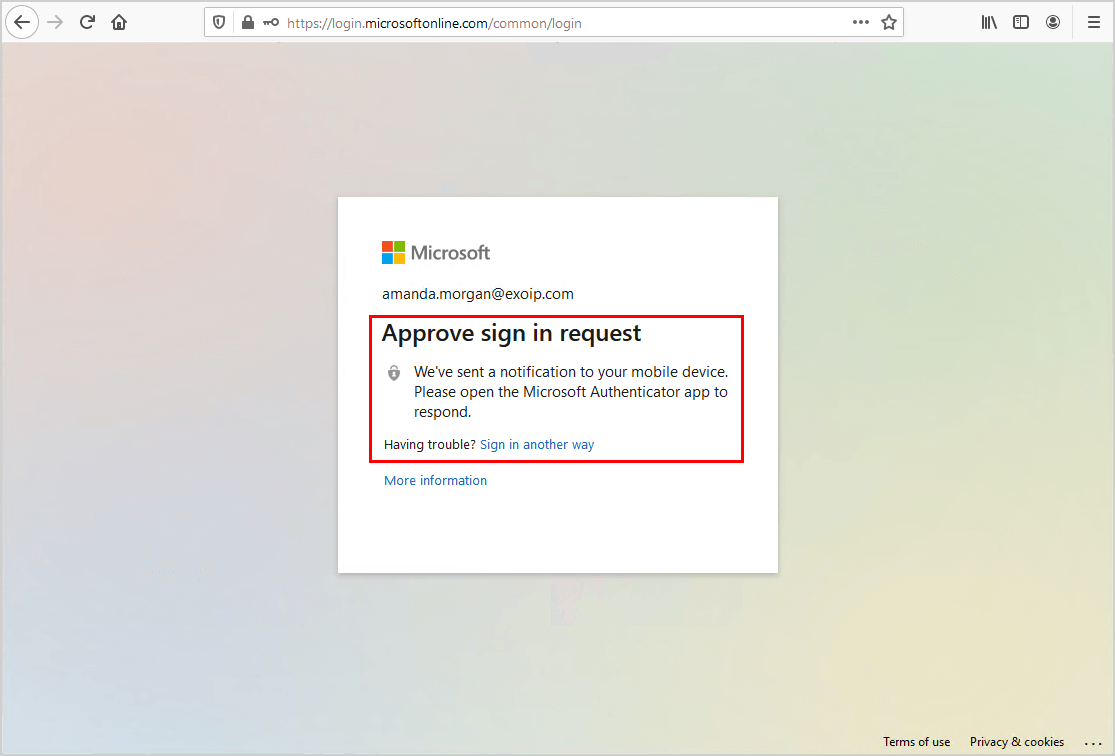
Users who do not have MFA enabled or newly created users will be asked to go through the MFA setup when they sign in.
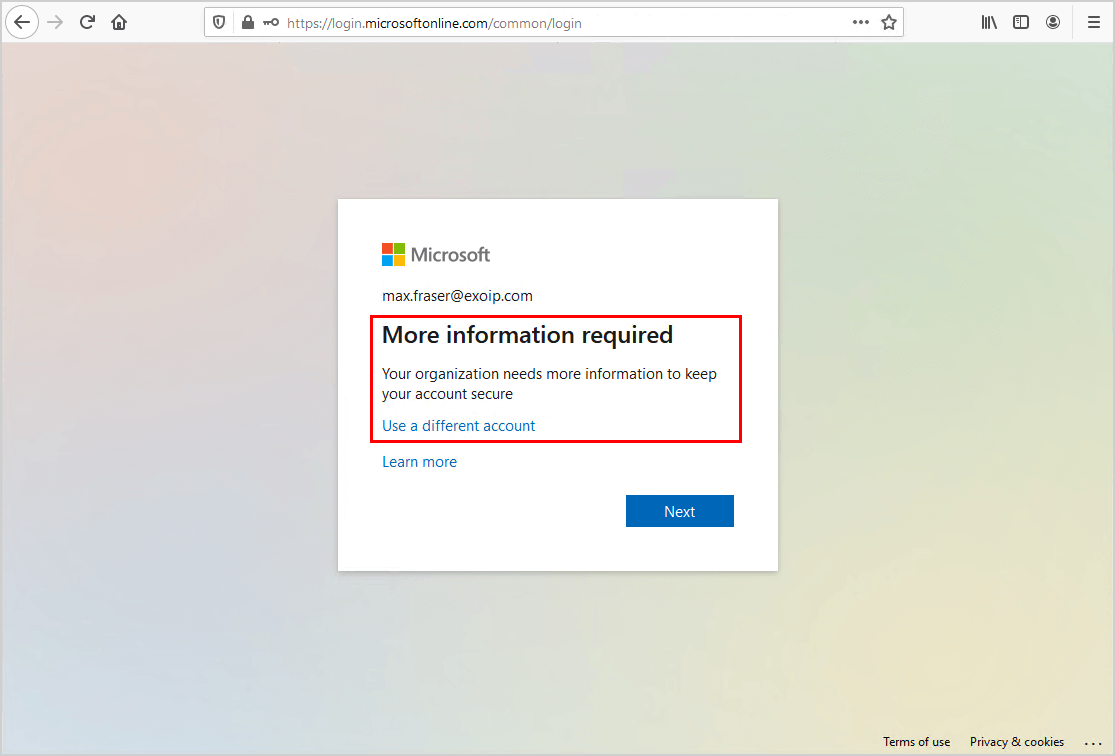
From now on, you will manage MFA from the Microsoft Entra admin center. That’s great because there are many more Conditional Access policy options you can look into and enable per organization requirements.
Note: Always enable MFA for users! It will protect the accounts from attacks and compromised passwords. It adds another layer of protection that helps organizations.
Read more: Add tag to external emails in Microsoft 365 for extra security »
Conclusion
You learned how to move from per-user MFA to Conditional Access MFA. First, go to the per-user MFA portal and disable per-user MFA for all users. After that, turn off security defaults and create a Conditional Access policy in Microsoft Entra. As of last, test and verify that MFA works when signing in.
Did you enjoy this article? You may also like Add users to group with PowerShell. Don’t forget to follow us and share this article.



nice tech article sharing to resolve confusion between per-user MFA and CA MFA, thanks
What happens if you leave the “Per User” MFA in place while enabling the Conditional Access Policy?
I would like to test a few accounts prior to rolling out the entire company.
You absolutely should test it out before migrating them all.
1. Create a Conditional Access policy and set it up only for a few accounts.
2. Disable per-user MFA for the accounts you set up in the CA policy.
If you do it like the above steps, nothing will happen. But if you enable the CA policy for the users that have per-user MFA enabled, you will see that the users can get the Microsoft sign-in prompt repeatedly while signing in. Also, they cannot complete the MFA installation when they want to set it up for the first time.
There are definitely other issues that will appear regarding MFA because you are enabling two different MFA configurations in the background.
Hi Ali,
When disabling per-user MFA, will it just set the user as “Disabled” in Per-User MFA or will it also remove the authentication methods from the accounts?
Also can we disable it for one user? as a test before doing for all users?
Many thanks, great blog you have here, always 100% relevant with excellent info and great design also.
Glad to hear that and thanks.
No, it will not remove the authentication methods.
It’s written in the article: “users will not be required to re-register for MFA because disabling per-user MFA doesn’t clear the MFA methods.”
Yes, you can disable per-user MFA only for a single user. Make sure that you exclude these users that have per-user MFA enabled from the Conditional Access policy. Also, try it out first with a group (Pilot) before you deploy it to the rest.
FYI you have a line at the bottom of the article saying to always enable MFA for users after just saying to disable it for all users. Might confuse some admins 🙂
It’s added because you should enable MFA for all users. If you enable per-user MFA or enable MFA through Conditional Access. In the end, it’s “MFA”.
Any advice on moving from Security Defaults managed MFA to Conditional Access?
(I had a bit of a bumpy experience with a client, quite a few users’ MFA stopped working)
Follow the steps in the article, and you should be good.
Do you know of a way to check if the users are being enabled? Like a script?
Use the script in the article Export Office 365 users MFA status with PowerShell.
Note that the PowerShell script can’t identify the MFA status if enabled through Security Defaults or Conditional Access. That’s because Microsoft did not provide a way for that.
Thanks for a great post. I decided to exclude my trusted office locations from this CA policy however, this meant that new users aren’t prompted to register for MFA the first time they sign in like they were with per-user MFA.
I would like to make sure they are at least registered so that when they leave the office they are set up. It would also be great to have this automated so that we don’t have to tell them to visit aka.ms/mysecurityinfo. Can you think of the best way to handle this?
My reasoning around excluding trusted locations is so that multi-function printers can send email without MFA auth and so that users don’t get MFA notification fatigue and hit approve all the time.
Hi Ali, Thank you.!
Can I, leave some users in User-Based MFA and others in CA rule while we make the transfer?
Yes, you can.
Make sure that you exclude these users that have per-user MFA enabled from the Conditional Access policy. Also, try it out first with a group (Pilot) before you deploy it to the rest.
Hi Ali, Thanks a lot.!!
I have a doubt… What happen if i have an user with MFA-per user enabled and added in that Conditional Access rule.
It’s not recommended to have per-user MFA enabled and Conditional Access for the same user. You will have issues with MFA authentication.
For example, you have Intune and want to sign in to set up the device for the first time. Unfortunately, this will not work, and it will not let you go through the step.
I recommend using Conditional Access (premium) and only using per-user MFA (basic) when you don’t have a Microsoft Entra ID P1/P2 license.
Fixed an issue with Microsoft Entra joined devices and conditional access conditions not working. I was trying to exclude MFA for Microsoft Entra hybrid joined devices. Seems User-Based MFA and Conditional Access do not coexist very well….
Due to the fact the test users were user-based enforce, no condition in Conditional Access will exclude the user on a Hybrid Joined devices for MFA. Turning off user based solved the issue! Thanks Ali!!! Great post.
You’re welcome, Stephen.
Hi,
this doesn’t work for me, and i’m confused as to why….
If i disable MFA for a specific user then apply a CA policy their account then shows as “enforced” right? However when the users opens outlook (desktop app) it constantly asks for a password and never accepts the correct one. IF, however i change their MFA status to “enabled” it allows the password for outlook through without constantly prompting for it.
Any advice on this please?
Hi,
When you disable per-user MFA and apply the CA policy, the per-user MFA will stay disabled. It should not show as enforced.
Check that modern authentication is enabled. If not, enable modern authentication in Microsoft 365.
Per-user MFA overwrites the CA policy. That’s why it’s working when you enable per-user MFA.
Thanks!
You’re welcome, Rasheedah.