How to migrate Azure AD Connect to a new server? You have Azure AD Connect…
Disable basic authentication with Conditional Access
How to disable basic authentication in Office 365 with Conditional Access policy? You want to block basic authentication known as legacy authentication in Azure AD because you have modern authentication in place for Exchange Online and Exchange on-premises. Also, many attacks are coming through basic authentication, and it’s an intelligent choice to block them. This article will learn how to create a Conditional Access policy in Azure AD to disable legacy authentication.
Table of contents
Why you should block basic authentication
Why do you need to block basic authentication when you have Multi-Factor Authentication configured?
For MFA to be effective, you also need to block legacy authentication. It’s because legacy authentication protocols like POP, SMTP, IMAP, and MAPI can’t enforce MFA, making them preferred entry points for adversaries attacking your organization.
The numbers on legacy authentication from an analysis of Azure Active Directory (Azure AD) traffic are clear:
- More than 99 percent of password spray attacks use legacy authentication protocols
- More than 97 percent of credential stuffing attacks use legacy authentication
- Azure AD accounts in organizations that have disabled legacy authentication experience 67 percent fewer compromises than those where legacy authentication is enabled
Single-factor authentication (for example, username and password) is not enough these days. Passwords are bad as they are easy to guess, and we (humans) are bad at choosing good passwords. Passwords are also vulnerable to various attacks, like phishing and password spray. One of the easiest things you can do to protect against password threats is to implement Multi-Factor Authentication (MFA). With MFA, even if an attacker gets in possession of a user’s password, the password alone is not sufficient to successfully authenticate and access the data.
How can you prevent apps using legacy authentication from accessing your tenant’s resources? The recommendation is to block them with a Conditional Access policy. If necessary, you allow only certain users and specific network locations to use apps that are based on legacy authentication.
Block basic authentication with Conditional Access
Follow the below steps to block basic authentication, also known as legacy authentication with Azure AD Conditional Access.
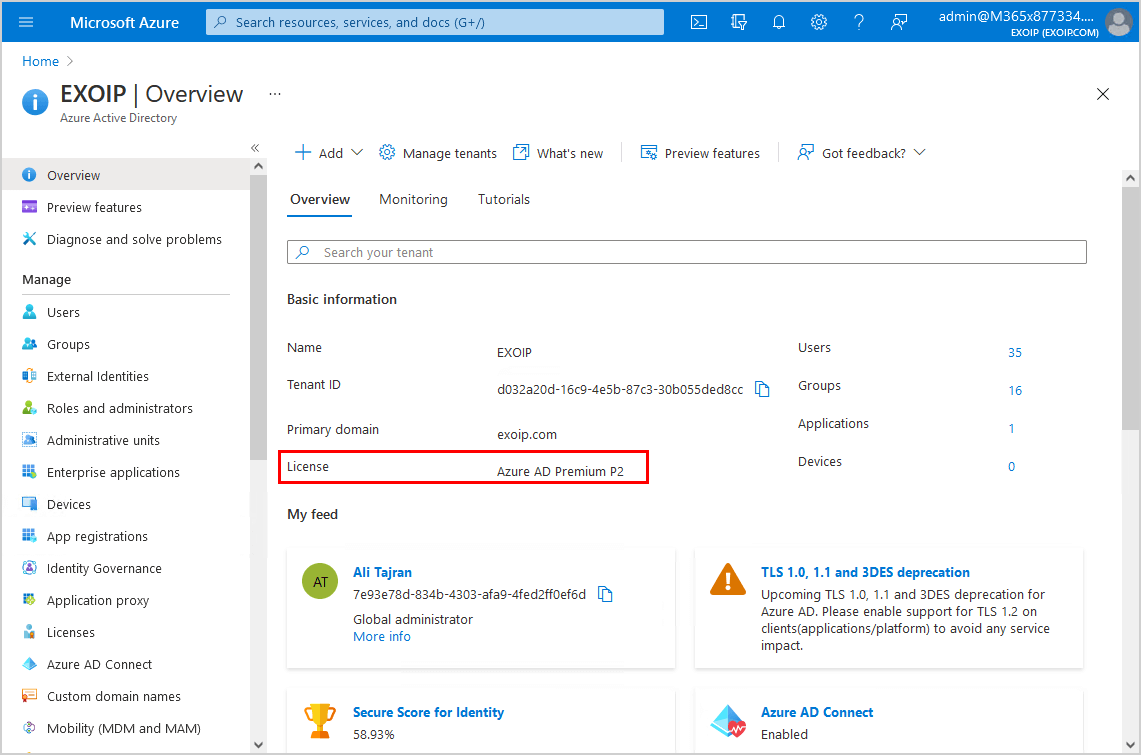
Step 1. Check Azure AD Premium license
Check that you have Azure AD Premium plan 1 or 2. Sign in to Microsoft Azure. In the portal, navigate to Azure Active Directory > Overview. In the example below, there is an Azure AD Premium P2 license.
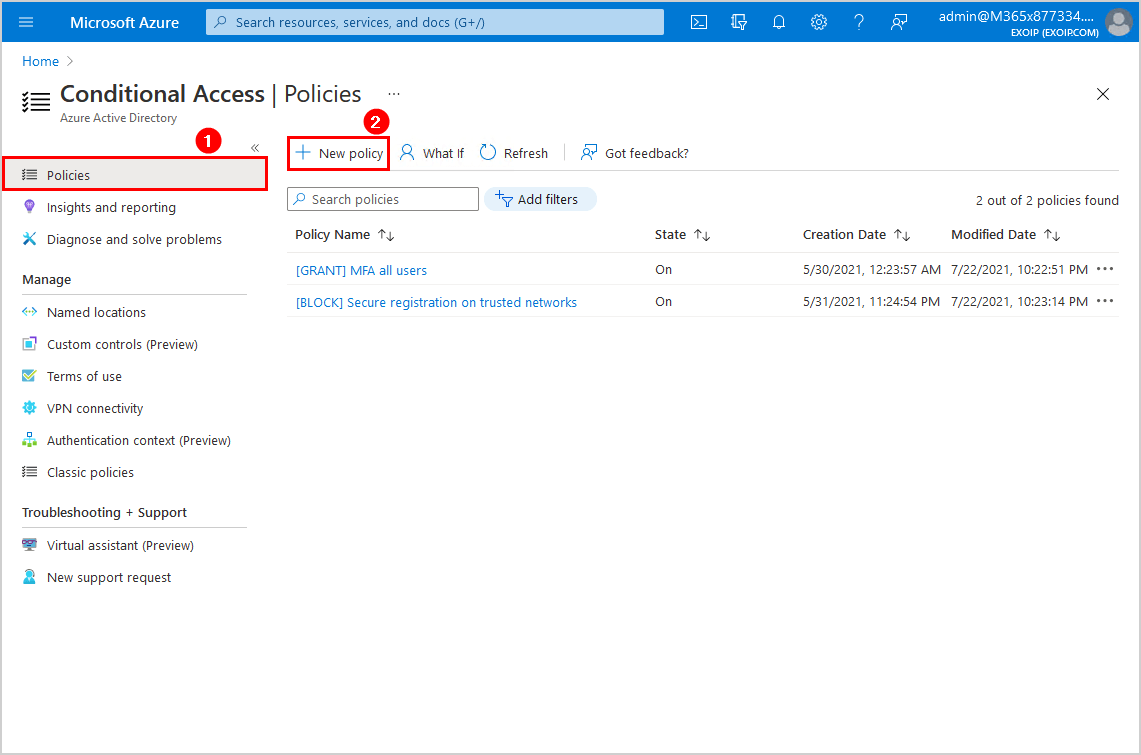
Step 2. New policy
Create a Conditional Access policy to force block basic authentication for all the users. You can select only a selected group of users. But, we recommend disabling basic authentication for all users.
Browse to Active Directory > Security > Conditional Access. Click New policy.
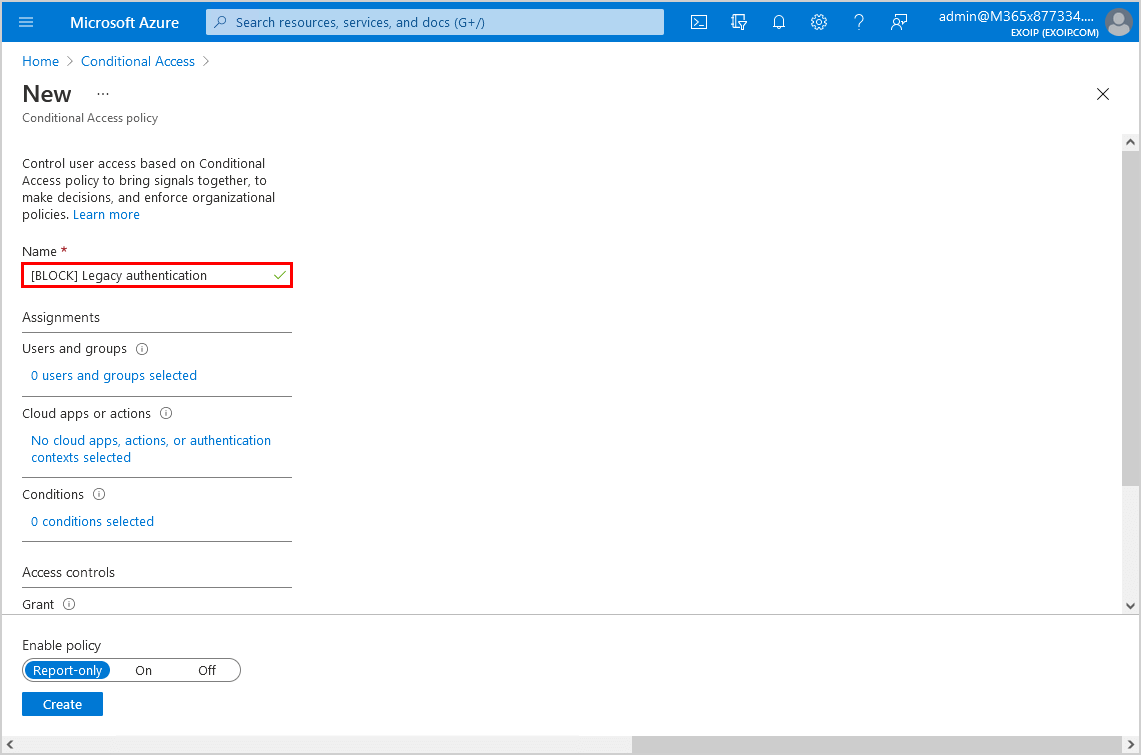
Step 3. Name
Give it the name [BLOCK] Legacy authentication.
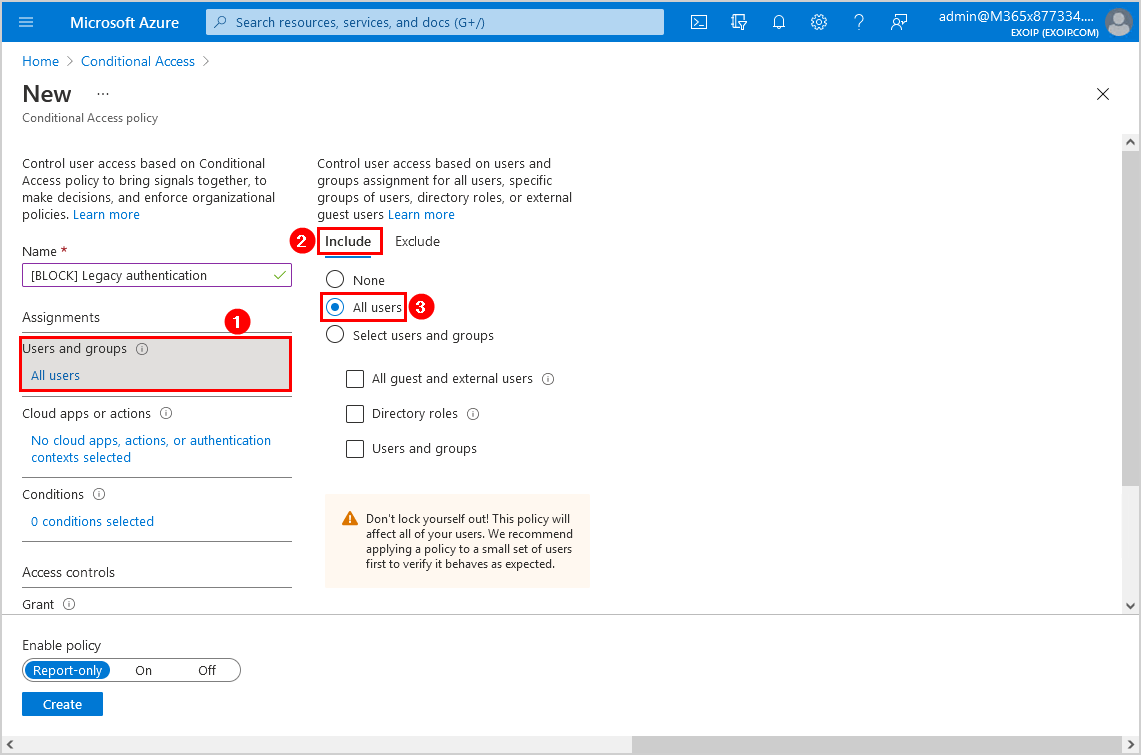
Step 4. Assignments
Click Users and groups and follow with Include. Select All users.
Step 5. Cloud apps or actions
Click Cloud apps and follow with Include. Select All cloud apps.
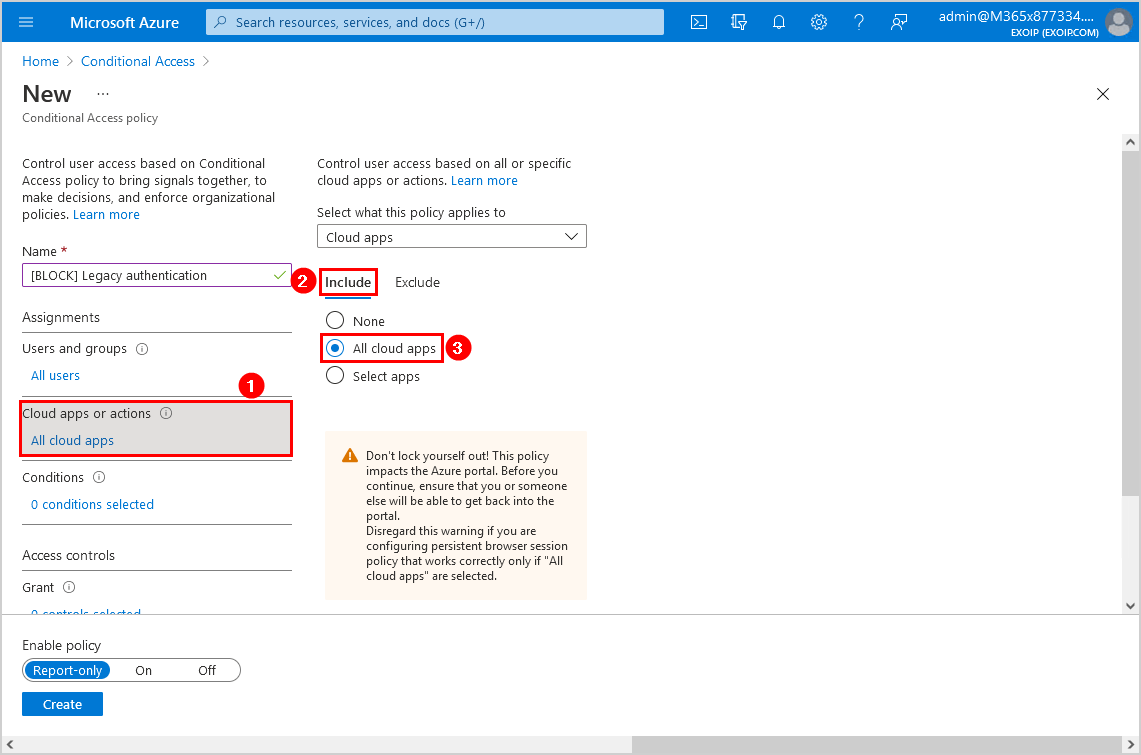
Step 6. Conditions
Click Conditions and follow with Client apps. Click on Yes. Select Exchange ActiveSync clients and Other clients.
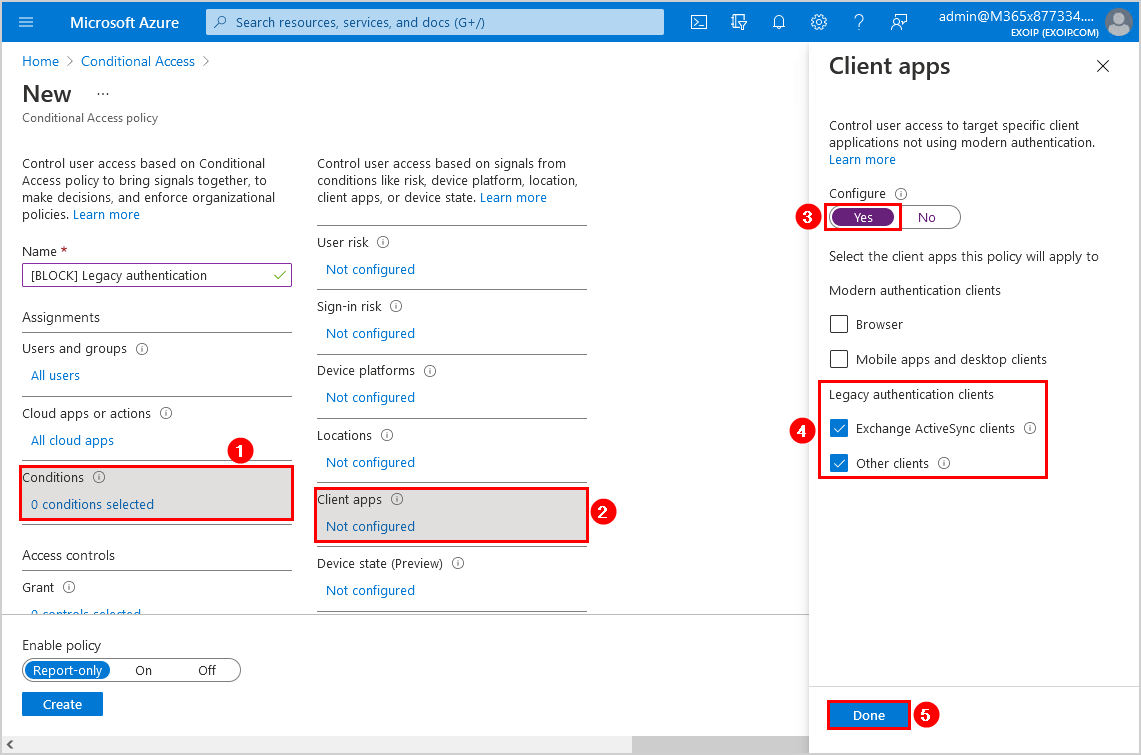
Step 7. Grant
Click Grant. Select Block access. Click on Select.
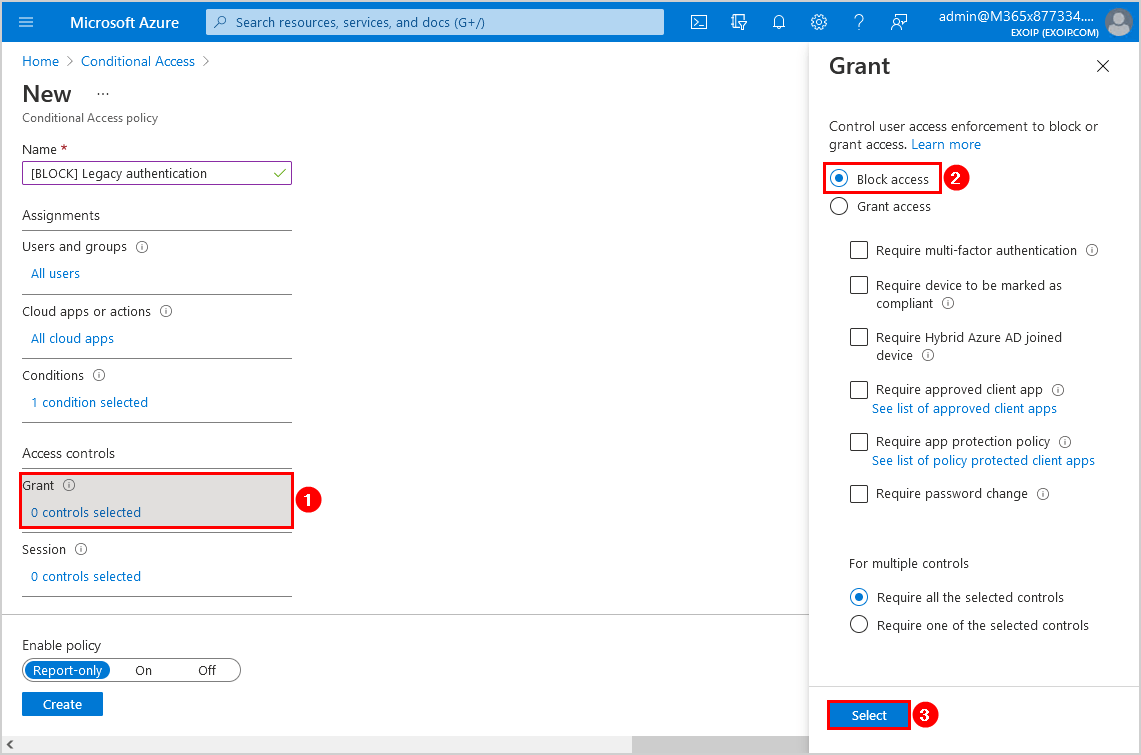
Step 8. Enable policy
Click the On switch to enable the policy. Select I understand that my account will be impacted by this policy. Proceed anyway. Click Create.
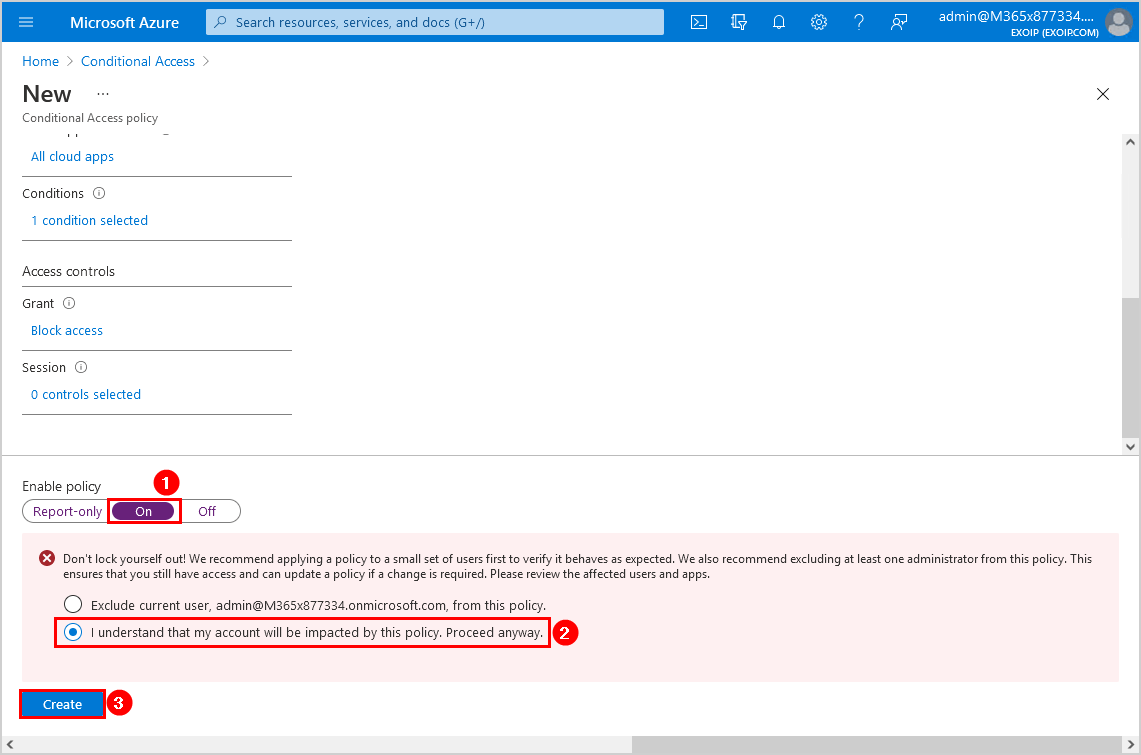
The policy shows up in the Conditional Access policies list.
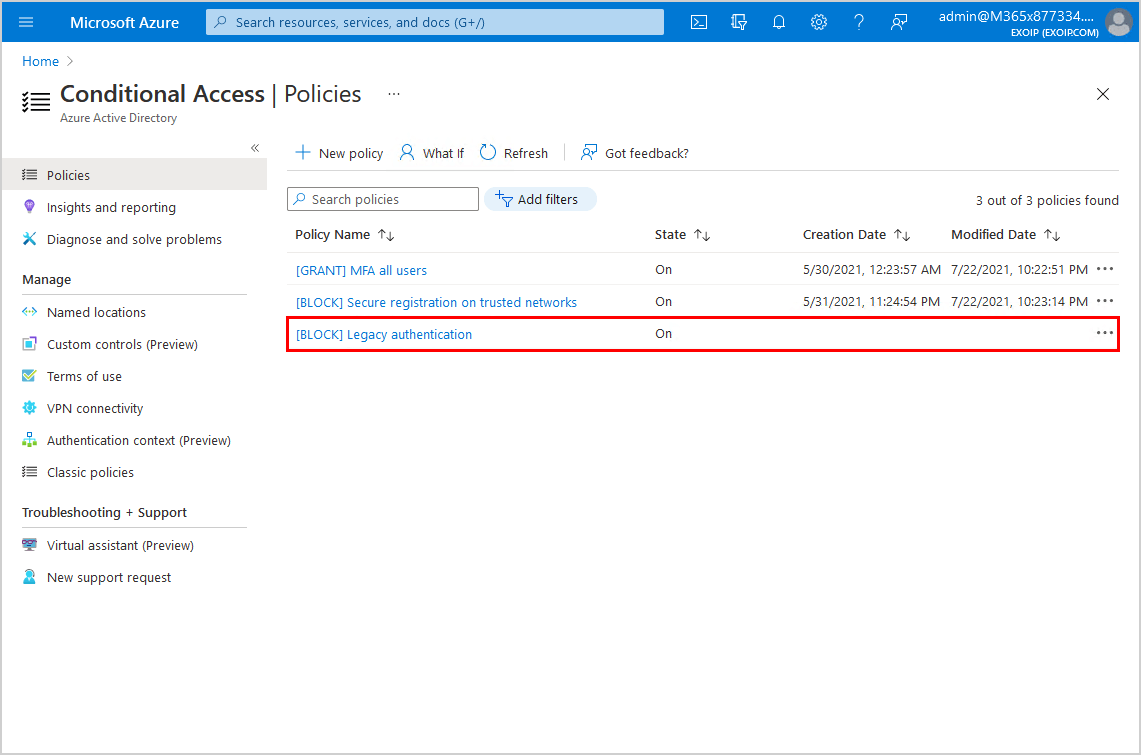
It can take up to 24 hours for the [BLOCK] Legacy Authentication policy to go into effect.
Read more: Configure Hybrid Modern Authentication in Exchange on-premises »
Conclusion
In this article, you learned how to disable basic authentication with Conditional Access. It’s essential to create the policy and secure the organization from attacks. If some applications or printers need to connect with basic authentication, you can add the users in the exclude group or add the location to the exclusion list. That way, they can still use basic authentication.
Did you enjoy this article? You may also like Add Exchange Online License to mailbox in Exchange Hybrid. Don’t forget to follow us and share this article.



Fun fact… CA policies are applied only AFTER the 1st factor of authenication meaning attackers can still attempt basic auth and could confirm passswords. You should still apply exchange auth polices for pre-auth protection.
The important point here is CA polices are not enough to protect against basic authenication. A major gochta and important for federated users.
https://learn.microsoft.com/en-us/azure/active-directory/conditional-access/block-legacy-authentication#prerequisites
True.
This needs to be applied:
https://learn.microsoft.com/en-us/exchange/clients-and-mobile-in-exchange-online/disable-basic-authentication-in-exchange-online
Hi Ali,
I have tried this and after 24 hours still some of my test users can login using legacy authentication. In the sign-in logs I could see “failure” in line with the CA but both matched the conditions of CA (user and client apps). Except under Access control it only shows Block > block with a red x
thanks
Hi,
It is difficult to tell why the test users can still sign in with legacy authentication without seeing the logs. Create a support ticket with Microsoft, and let’s see if they can figure it out with you.