You like to offboard a mailbox from Exchange Online to Exchange On-Premises. This time you…
Configure Hybrid Modern Authentication in Exchange on-premises
How to enable Hybrid Modern Authentication (HMA) in Exchange Server on-premises? We want to secure the Exchange on-premises organization with modern authentication instead of basic authentication. This way, we can use MFA for on-premises user mailboxes and not only for user mailboxes in the cloud. In this article, you will learn how to configure Hybrid Modern Authentication step by step in Exchange on-premises.
Table of contents
- Introduction
- Hybrid Modern Authentication prerequisites
- Hybrid Modern Authentication diagram
- Advantages of modern authentication
- How to configure Hybrid Modern Authentication
- Step 1. Enable modern authentication in Exchange Online
- Step 2. Get virtual directory URLs
- Step 3. Get Exchange related SPNs
- Step 4. Add on-premises web service URLs as SPNs
- Step 5. Verify Exchange related SPNs
- Step 6. Verify OAuth virtual directories
- Step 7. Confirm EvoSTS auth server object is present
- Step 8. Enable Hybrid Modern Authentication
- Step 9. Restart Internet Information Services
- Step 10. Outlook registry requirements
- Verify your work
- Conclusion
Introduction
We have an Exchange Hybrid deployment. Most of the mailboxes are in Exchange Online, but we do have mailboxes on-premises. It’s because of company policies. Now that we have mailboxes on-premises, we like the users to authenticate with modern authentication instead of the default basic authentication.
Note: Hybrid Modern Authentication works great with a single Exchange Server or Exchange Server in high availability (load-balanced).
Amanda has a mailbox on-premises, and we can verify that she is connecting with basic authentication in the Outlook desktop application with the below steps:
- Start Outlook
- Hold down the CTRL key and right-click on the Outlook client in the Windows system tray
- Click Connection Status
In the Authn (authentication) column, you will see Nego* as the authentication scheme. It means you use basic authentication.
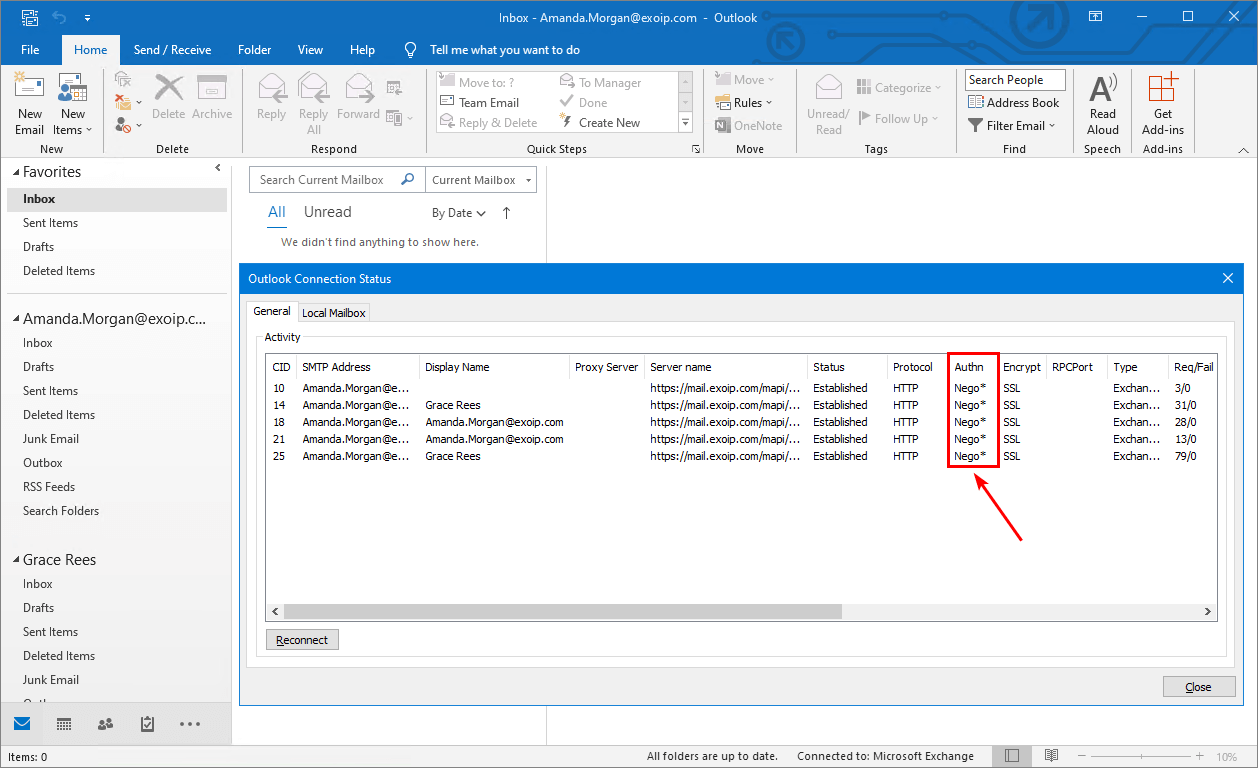
The Authn column needs to show as Bearer*. That’s when you know that Modern Authentication is used.
Hybrid Modern Authentication prerequisites
Before you start to configure Hybrid Modern Authentication, ensure that you have gone through these steps:
- Exchange Hybrid Configuration Wizard*
- Install and configure Azure AD Connect
- Exchange Server 2010 is not running in the organization
- Exchange Server 2013/2016/2019 with latest Cumulative Update installed
*Hybrid Modern Authentication is not supported with the Hybrid Agent. You will need to leverage the Classic Exchange Hybrid Topology and publish AutoDiscover, EWS, ActiveSync, MAPI, and OAB endpoints for Hybrid Modern Authentication to function with various Outlook clients.
Note: Exchange OWA (Outlook Web Access) and ECP (Exchange Control Panel) do not work with modern authentication. To secure that, we will write another article.
We recommend you to:
- Enable modern authentication in Exchange Server on-premises organization (this article)
- Protect Exchange OWA and Exchange ECP (next article)
Hybrid Modern Authentication diagram
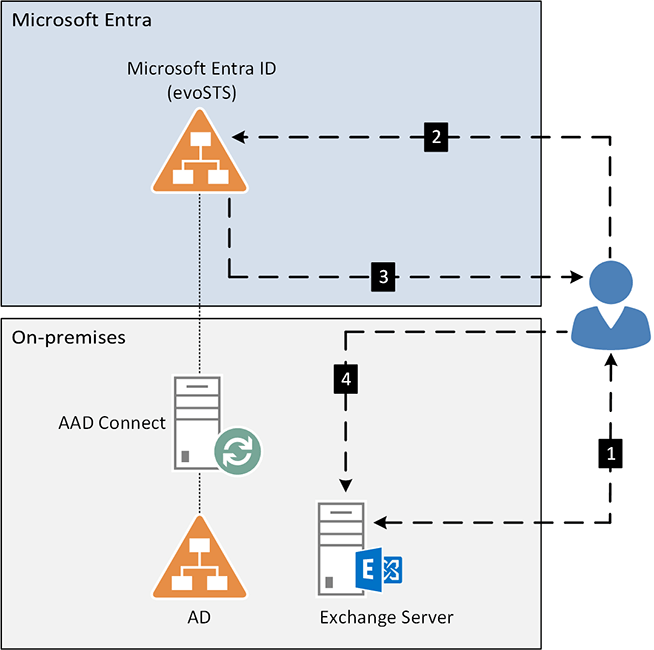
In the diagram below, you can see how the Hybrid Modern Authentication flow looks like after implementation.
- User with on-premises mailbox starts Outlook and connects with autodiscover to Exchange Server. The connection will redirect to the evoSTS URL that you set.
- The Outlook client contacts Microsoft Entra ID, and the modern authentication sign-in prompt appears. The user will authenticate with the same Conditional Access policies set for the Exchange Online application (cloud app).
- After successful authentication, the user will get an Access Token and Refresh Token.
- The user provides the Access Token to the Exchange Server on-premises and gets access to the mailbox.
Advantages of modern authentication
The advantages of configuring modern authentication in Exchange Server on-premises are:
- More secure than basic authentication (classic username and password)
- Configure policies from Microsoft Entra ID (central location)
- Modern look and feel for end-user experience
How to configure Hybrid Modern Authentication
We will go through the steps below and make sure that everything is in place before we enable Hybrid Modern Authentication for the Exchange on-premises organization.
Please have a good look every time you are going to run the cmdlets. That’s because you need to perform the administrative tasks in:
- Exchange Management Shell (Exchange Server on-premises)
- PowerShell (Microsoft Graph PowerShell)
Step 1. Enable modern authentication in Exchange Online
Read more in the article Enable modern authentication in Microsoft 365.
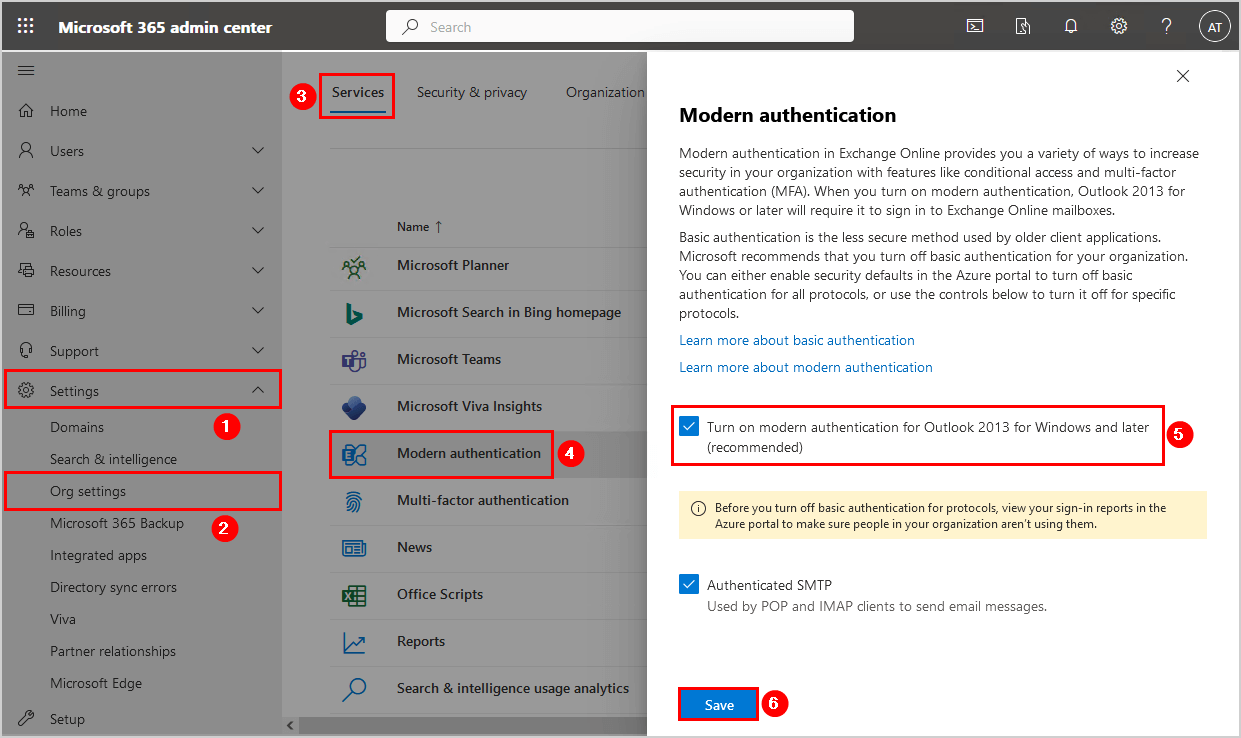
To enable modern authentication in Exchange Online, follow these steps:
- Sign in to Microsoft 365 admin center
- Expand Settings and click on Org settings
- Click on Services in the top bar
- Choose Modern authentication from the list
- Check the box Turn modern authentication for Outlook 2013 for Windows and later (recommended)
- Click on Save
Note: For tenants created before August 1, 2017, modern authentication is turned off by default for Exchange Online and Skype for Business Online.
Step 2. Get virtual directory URLs
Start Exchange Management Shell as administrator on your Exchange Server on-premises. Run the four cmdlets to retrieve the virtual directory URLs.
Get-MapiVirtualDirectory | fl server,*url*
Get-WebServicesVirtualDirectory | fl server,*url*
Get-ClientAccessServer | fl Name, AutodiscoverServiceInternalUri
Get-OABVirtualDirectory | fl server,*url*The results appear in the output below after running every command. Make a note of all the internal and external URLs because you will need to add these URLs in one of the next steps.
In our example, we have the same name for internal and external URLs. We recommend configuring it like this as it will simplify a lot. If you didn’t, you would see internal addresses that end with .local or .lan in the output.
# Get-MapiVirtualDirectory | fl server,*url*
Server : EX01-2016
InternalUrl : https://mail.exoip.com/mapi
ExternalUrl : https://mail.exoip.com/mapi
Server : EX02-2016
InternalUrl : https://mail.exoip.com/mapi
ExternalUrl : https://mail.exoip.com/mapi
# Get-WebServicesVirtualDirectory | fl server,*url*
Server : EX01-2016
InternalNLBBypassUrl :
InternalUrl : https://mail.exoip.com/EWS/Exchange.asmx
ExternalUrl : https://mail.exoip.com/EWS/Exchange.asmx
Server : EX02-2016
InternalNLBBypassUrl :
InternalUrl : https://mail.exoip.com/EWS/Exchange.asmx
ExternalUrl : https://mail.exoip.com/EWS/Exchange.asmx
# Get-ClientAccessServer | fl Name, AutodiscoverServiceInternalUri
WARNING: The Get-ClientAccessServer cmdlet will be removed in a future version of Exchange. Use the
Get-ClientAccessService cmdlet instead. If you have any scripts that use the Get-ClientAccessServer cmdlet, update them
to use the Get-ClientAccessService cmdlet. For more information, see http://go.microsoft.com/fwlink/p/?LinkId=254711.
Name : EX01-2016
AutoDiscoverServiceInternalUri : https://autodiscover.exoip.com/Autodiscover/Autodiscover.xml
Name : EX02-2016
AutoDiscoverServiceInternalUri : https://autodiscover.exoip.com/Autodiscover/Autodiscover.xml
# Get-OABVirtualDirectory | fl server,*url*
Server : EX01-2016
InternalUrl : https://mail.exoip.com/OAB
ExternalUrl : https://mail.exoip.com/OAB
Server : EX02-2016
InternalUrl : https://mail.exoip.com/OAB
ExternalUrl : https://mail.exoip.com/OABStep 3. Get Exchange related SPNs
Run PowerShell as administrator and connect to Microsoft Graph PowerShell. Sign in with your Microsoft 365 global administrator credentials.
Connect-MgGraph -Scopes "Application.Read.All", "Application.ReadWrite.All"Run the Get-MgServicePrincipal cmdlet to get the Exchange related URLs in the cloud for the application 00000002-0000-0ff1-ce00-000000000000.
Get-MgServicePrincipal -Filter "AppId eq '00000002-0000-0ff1-ce00-000000000000'" | select -ExpandProperty ServicePrincipalNamesTake note of (and screenshot for later comparison) the output of this command, which should include an https://autodiscover.yourdomain.com and https://mail.yourdomain.com URL, but mostly consist of SPNs that begin with 00000002-0000-0ff1-ce00-000000000000/.
00000002-0000-0ff1-ce00-000000000000/mail.exoip.com
00000002-0000-0ff1-ce00-000000000000/autodiscover.exoip365.mail.onmicrosoft.com
00000002-0000-0ff1-ce00-000000000000/exoip365.mail.onmicrosoft.com
00000002-0000-0ff1-ce00-000000000000/autodiscover.exoip.com
00000002-0000-0ff1-ce00-000000000000/exoip.com
00000002-0000-0ff1-ce00-000000000000/autodiscover.exoip.local
00000002-0000-0ff1-ce00-000000000000/exoip.local
00000002-0000-0ff1-ce00-000000000000/outlook.office365.com
00000002-0000-0ff1-ce00-000000000000/mail.office365.com
00000002-0000-0ff1-ce00-000000000000/outlook.com
00000002-0000-0ff1-ce00-000000000000/*.outlook.com
00000002-0000-0ff1-ce00-000000000000
https://ps.compliance.protection.outlook.com
https://outlook-sdf.office.com/
https://outlook-sdf.office365.com/
https://outlook.office365.com:443/
https://outlook.office.com/
https://outlook.office365.com/
https://outlook.com/
https://ps.protection.outlook.com/
https://outlook-tdf.office.com/
https://outlook-tdf-2.office.com/
https://ps.outlook.comMost likely, the https:// URLs from your on-premises (step 2) are missing. Therefore, we will need to add those specific records to this list in the next step.
Step 4. Add on-premises web service URLs as SPNs
If you don’t see your internal and external MAPI/HTTP, EWS, ActiveSync, OAB, and Autodiscover records in this list, you must add them using the command below in Microsoft Graph PowerShell.
In this example, the URLs are https://mail.exoip.com/ and https://autodiscover.exoip.com/. Replace the URLs with your own.
$x = Get-MgServicePrincipal -Filter "AppId eq '00000002-0000-0ff1-ce00-000000000000'"
$ServicePrincipalUpdate = @(
"https://mail.exoip.com/",
"https://autodiscover.exoip.com/"
)
Update-MgServicePrincipal -ServicePrincipalId $x.Id -ServicePrincipalNames $ServicePrincipalUpdateStep 5. Verify Exchange related SPNs
Verify that you added the new records by running the Get-MgServicePrincipal cmdlet in Microsoft Graph PowerShell.
Get-MgServicePrincipal -Filter "AppId eq '00000002-0000-0ff1-ce00-000000000000'" | select -ExpandProperty ServicePrincipalNamesLook through the output. Compare the before list/screenshot against the new list of SPNs. You might also take a screenshot of the new list for your records. If you were successful, you would see the two new URLs in the list.
Going by our example, the list of SPNs will now include the specific URLs https://mail.exoip.com/ and https://autodiscover.exoip.com/. See it at the top of the list.
https://autodiscover.exoip.com/
https://mail.exoip.com/
00000002-0000-0ff1-ce00-000000000000/mail.exoip.com
00000002-0000-0ff1-ce00-000000000000/autodiscover.exoip365.mail.onmicrosoft.com
00000002-0000-0ff1-ce00-000000000000/exoip365.mail.onmicrosoft.com
00000002-0000-0ff1-ce00-000000000000/autodiscover.exoip.com
00000002-0000-0ff1-ce00-000000000000/exoip.com
00000002-0000-0ff1-ce00-000000000000/autodiscover.exoip.local
00000002-0000-0ff1-ce00-000000000000/exoip.local
00000002-0000-0ff1-ce00-000000000000/outlook.office365.com
00000002-0000-0ff1-ce00-000000000000/mail.office365.com
00000002-0000-0ff1-ce00-000000000000/outlook.com
00000002-0000-0ff1-ce00-000000000000/*.outlook.com
00000002-0000-0ff1-ce00-000000000000
https://ps.compliance.protection.outlook.com
https://outlook-sdf.office.com/
https://outlook-sdf.office365.com/
https://outlook.office365.com:443/
https://outlook.office.com/
https://outlook.office365.com/
https://outlook.com/
https://ps.protection.outlook.com/
https://outlook-tdf.office.com/
https://outlook-tdf-2.office.com/
https://ps.outlook.comStep 6. Verify OAuth virtual directories
Now verify OAuth (modern authentication) is correctly enabled in Exchange on-premises on all virtual directories that Outlook might use. Run the cmdlets in Exchange Management Shell.
Get-MapiVirtualDirectory | fl server,*url*,*auth*
Get-WebServicesVirtualDirectory | fl server,*url*,*oauth*
Get-OABVirtualDirectory | fl server,*url*,*oauth*
Get-AutoDiscoverVirtualDirectory | fl server,*oauth*The results appear in the output below after running every command.
# Get-MapiVirtualDirectory | fl server,*url*,*auth*
Server : EX01-2016
InternalUrl : https://mail.exoip.com/mapi
ExternalUrl : https://mail.exoip.com/mapi
IISAuthenticationMethods : {Ntlm, OAuth, Negotiate}
InternalAuthenticationMethods : {Ntlm, OAuth, Negotiate}
ExternalAuthenticationMethods : {Ntlm, OAuth, Negotiate}
Server : EX02-2016
InternalUrl : https://mail.exoip.com/mapi
ExternalUrl : https://mail.exoip.com/mapi
IISAuthenticationMethods : {Ntlm, OAuth, Negotiate}
InternalAuthenticationMethods : {Ntlm, OAuth, Negotiate}
ExternalAuthenticationMethods : {Ntlm, OAuth, Negotiate}
# Get-WebServicesVirtualDirectory | fl server,*url*,*oauth*
Server : EX01-2016
InternalNLBBypassUrl :
InternalUrl : https://mail.exoip.com/EWS/Exchange.asmx
ExternalUrl : https://mail.exoip.com/EWS/Exchange.asmx
OAuthAuthentication : True
Server : EX02-2016
InternalNLBBypassUrl :
InternalUrl : https://mail.exoip.com/EWS/Exchange.asmx
ExternalUrl : https://mail.exoip.com/EWS/Exchange.asmx
OAuthAuthentication : True
# Get-OABVirtualDirectory | fl server,*url*,*oauth*
Server : EX01-2016
InternalUrl : https://mail.exoip.com/OAB
ExternalUrl : https://mail.exoip.com/OAB
OAuthAuthentication : True
Server : EX02-2016
InternalUrl : https://mail.exoip.com/OAB
ExternalUrl : https://mail.exoip.com/OAB
OAuthAuthentication : True
# Get-AutoDiscoverVirtualDirectory | fl server,*oauth*
Server : EX01-2016
OAuthAuthentication : True
Server : EX02-2016
OAuthAuthentication : TrueIf OAuth is missing from any server and any of the four virtual directories, you need to add it using the relevant commands before proceeding:
- Set-MapiVirtualDirectory
- Set-WebServicesVirtualDirectory
- Set-OABVirtualDirectory
- Set-AutodiscoverVirtualDirectory
Step 7. Confirm EvoSTS auth server object is present
Return to the on-premises Exchange Management Shell. Run the cmdlet and validate that your on-premises has an entry for the evoSTS (a Security Token Service used by Microsoft Entra ID) authentication provider.
Get-AuthServer | where {$_.Name -like "EvoSts*"} | fl Name,DomainName,IssuerIdentifier,Realm,TokenIssuingEndpoint,Enabled,IsDefault*Your output should show an AuthServer with a Name that starts with EvoSts, and the Enabled state value should be True. If you don’t see this, you should download and run the most recent version of the Hybrid Configuration Wizard.
In our output, we have two evoSts authentication servers. That’s because we have our on-premises configured with two tenants.
Name : EvoSts - 5af53ad5-4ce1-4406-bf3f-b8c796cf17b8
DomainName : {exoip365.onmicrosoft.com}
IssuerIdentifier : https://sts.windows.net/fe15bfe6-36b2-4c9d-bf42-51b995f8e9af/
Realm : fe15bfe6-36b2-4c9d-bf42-51b995f8e9af
TokenIssuingEndpoint : https://login.windows.net/common/oauth2/token
Enabled : True
IsDefaultAuthorizationEndpoint : False
Name : EvoSts - d1c9beac-0655-48e7-9949-5e497af1d38d
DomainName : {exoip.com}
IssuerIdentifier : https://sts.windows.net/d032a20d-16c9-4e5b-87c3-30b055ded8cc/
Realm : d032a20d-16c9-4e5b-87c3-30b055ded8cc
TokenIssuingEndpoint : https://login.windows.net/common/oauth2/token
Enabled : True
IsDefaultAuthorizationEndpoint : FalseStep 8. Enable Hybrid Modern Authentication
If you have more than one evoSts authentication server, you need to know which one you want to set as default. In Microsoft Graph PowerShell, run the cmdlet to retrieve the organization ID.
Get-MgOrganization | select DisplayName, IdIn our example, the organization ID ends with d8cc. We need to set EvoSts – d1c9beac-0655-48e7-9949-5e497af1d38d as default authorization endpoint.
DisplayName Id
----------- --
EXOIP d032a20d-16c9-4e5b-87c3-30b055ded8ccIn Exchange Management Shell, run the two cmdlets to enable modern authentication on the Exchange on-premises organization.
Set-AuthServer -Identity "EvoSts - d1c9beac-0655-48e7-9949-5e497af1d38d" -IsDefaultAuthorizationEndpoint $true
Set-OrganizationConfig -OAuth2ClientProfileEnabled $trueIf the Exchange on-premises version is Exchange 2016 (CU18 or higher) or Exchange 2019 (CU7 or higher) and hybrid was configured with HCW downloaded after September 2020, run the following command in the Exchange Management Shell on-premises.
Change the identity (copy from step 7) and domain name to your own.
Set-AuthServer -Identity "EvoSts - d1c9beac-0655-48e7-9949-5e497af1d38d" -DomainName "exoip.com" -IsDefaultAuthorizationEndpoint $true
Set-OrganizationConfig -OAuth2ClientProfileEnabled $trueStep 9. Restart Internet Information Services
You can restart the Internet Information Services (IIS) on the Exchange Servers to speed up the process.
iisresetStep 10. Outlook registry requirements
Make sure that you have one of the below Outlook clients running that support modern authentication. Outlook 2010 is not supported, and it will not work. Upgrade your Outlook client to a version that supports modern authentication.
| Outlook version | Modern auth support | EnableADAL reg key required | AlwaysUseMSOAuthForAutodiscover reg key required |
|---|---|---|---|
| Outlook 2010 | No | Not available | Not available |
| Outlook 2013 | Yes | Yes | Yes |
| Outlook 2016 | Yes | No | Yes |
| Outlook 2019 | Yes | No | Yes |
| Outlook 365 | Yes | No | Yes |
Microsoft recommends that users force Outlook to use modern authentication by setting the DWORD value of the following registry key to 1.
HKEY_CURRENT_USER\Software\Microsoft\Exchange\AlwaysUseMSOAuthForAutoDiscover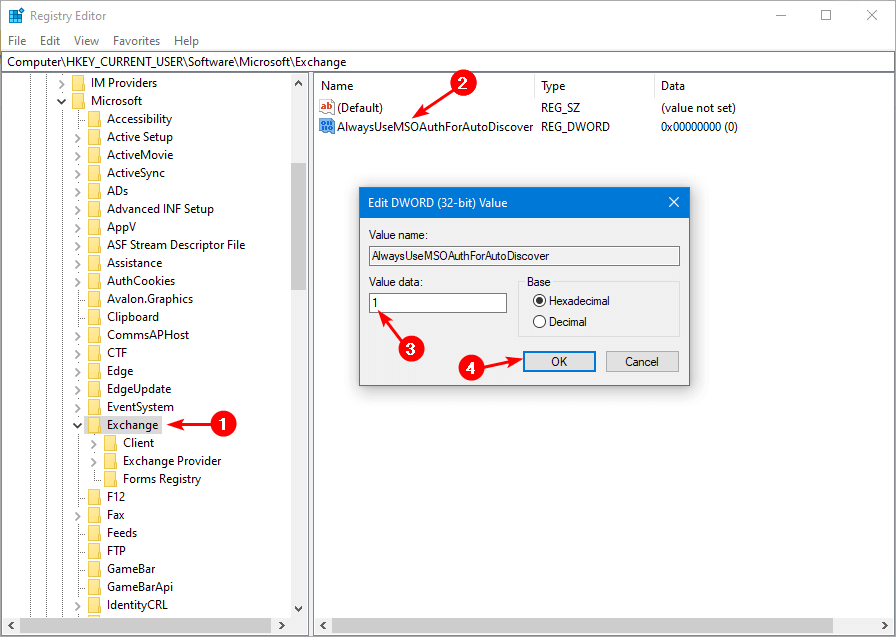
If you have Outlook 2013, you need to add two more DWORD values. Add the DWORD value to 1 in the following registry subkeys:
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\15.0\Common\Identity\EnableADAL
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\15.0\Common\Identity\VersionVerify your work
Once you enable Hybrid Modern Authentication, a client’s next login will use the new auth flow. Note that just turning on Hybrid Modern Authentication won’t trigger a reauthentication for any client, and it might take a while for Exchange to pick up the new settings. That’s why an iisreset on the Exchange Server(s) in the previous step will speed it up.
You can hold down the CTRL key and right-click the Outlook client in the Windows system tray. Click Connection Status. Look for the client’s SMTP address against an Authn type of Bearer*, representing the bearer token used in OAuth.
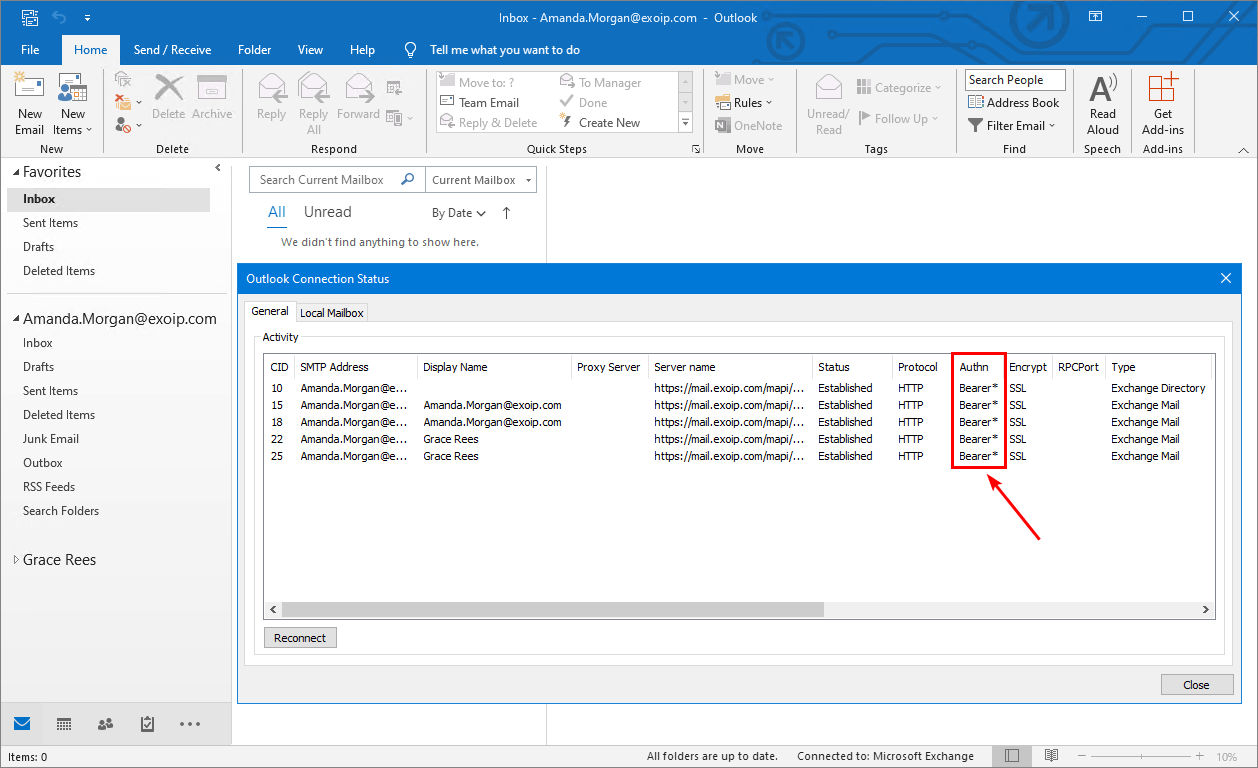
You did successfully configure Hybrid Modern Authentication in the Exchange on-premises organization.
Read more: Hybrid Configuration Wizard fails to connect »
Conclusion
You learned how to configure Hybrid Modern Authentication in Exchange on-premises. Follow the steps to configure OAuth between Exchange Online and Exchange on-premises.
Did you enjoy this article? You may also like Outlook prompts for password after migration to Office 365. Don’t forget to follow us and share this article.


Hi Sir,
If i want to enable MFA to Exchange Onpremise, i can configure the same this case?
Hi!
I have mapihttp disabled at org level in Exchange on prem. It’s also $null at all casmailboxes on prem. Almost all my mailboxes are in Exchange online, except for a few who are on prem. My internal Autodiscover (SCP) point to Exchange on prem. My plan is to deploy HMA for pilot users at step 1 and then for all users in step 2. Is it possible to enable mapihttp on user level (for pilot users) who’s mailbox is in Exchange online? I want those users outlook clients to use HMA when do Autodiscover request to Exchange on prem on internal network. I know that the Autodiscover respons will redirect them online.
Thank you, Ali, for such a great article. I have question and need your guidance. We have an exchange hybrid environment. On-prem we have a parent domain and a child domain. Both domains have separate exchange environment in co-existence. We have a single Microsoft Entra ID for where they both are getting synced. The on-prem virtual directories for both on-prem exchange are different, except for the Autodiscover which is pointing to the parent exchange domain. I need your assistance to understand following:
1. We want to implement HMA in parent exchange, but i guess since the Autodiscover is pointing to the parent domain, then we might need to apply HMA on the child exchange domain as well?
2. If we are applying HMA on both Parent and child domain, then do we need to add virtual directories of both domain as SPN in Microsoft Entra ID?
3. Once HMA is implemented, we know that that outlook will then connect to Microsoft Entra ID for authentication, we have some sites where internet is completely blocked, this means those users won’t be able to connect. What specific URLs/IP needs to be allowed so that those sites can explicitly connect to Microsoft Entra ID for authentication.
Hello Ali,
Thanks for this great article. I have a question for you. What will be the user experience one the HMA is enabled on on-prem Exchange? Will there be any impact on users on PC or mobile?
Thank you,
^ Def would like to know this too!
Thank you for the detailed articles!
I have a home lab with on-prem exchange server and would like to setup modern authentication with. I have a Microsoft Entra ID account to sync my users, but do I need an office 365 tenant account? If so, is there a free or “testing” type account?
Thanks!
Josh
You can get the trial or purchase atleast one mailbox license and should be good.
Hi Ali, great write up, i have a question, with the upcoming deprecation of basic auth in Exchange online, we have a hybrid setup with exchange 2016 (latest cu). the exchange on prem is not running HMA (oauth2), does this need to be enabled on all directories before MS october 2022 deprecation of basic auth? will our hybrid be affected?
Appreciate any advice.
Basic authentication deprecation is for Exchange Online (EXO) and not for Exchange on-premises (EX). So it will work fine.
But, it’s recommended to go through the article and configure HMA for Exchange on-premises because it offers a more secure authentication method.
top lad, many thanks for the advice, do you know if the deprecation would affect Lync on prem which is in a split-domain hybrid? if it is using legacy auth?
Hi Ali,
Thanks for the post, i have an exchange 2016 setup with CU 19, full hybrid classic is there and every thing is working as described in your article.
I have one question, can we enable MFA using a conditional policy for outlook users having an on premise mailbox and if yes can please share some details?
Microsoft documents it is possible however i did not see any details about it and most of the internet articles are still talking about the Intune connector which is no longer available.
Thank you.
Go through the article Configure Azure AD Multi-Factor Authentication. After that, the users with an on-premises mailbox need to validate with MFA.
Hi Ali.
I followed your manual yesterday, without the iisreset (changes should be active today).
But today, Outlook 2019 still connects with basic auth to our Exchange 2019 on premise.
Registry-Key is set.
All Adresses for owa etc. are correct.
ModernAuth on Exchange is enabled.
Any idea, why outlook still connects with basic auth?
Thank you.
Seem’s i’ve missed to set “-IsDefaultAuthorizationEndpoint $true” yesterday.
Acitvated it this morning and a view minues later, get a call “my outlook does’nt work”.
I checked that and if i try to start outlook in that usersession, outlook brings up a window with “this feature ist deactivated by administrator”. But on my Client, with he Outlook registry-key set, i got that Microsoft-Window for Authentication.
So, if i set the authendpoint $true, employees can’t use Outlook with basic auth anymore.
Maybe thats what it should be, but in this article i understand it works parallel.
And, with the reg-key set, my outlook again connects with basic auth.
Sorry for my bad english.
How about the Autodiscover as it could be pointing to the local Exchange in your environment..
I appreciate this article. It’s very close to the official MS setup docs but made a few steps more clear.
I’m wondering, with HMA in place, does Microsoft Entra ID resolve Exchange SPNs using internal or external DNS? Once I implement HMA, can I remove my Exchange URLs from my external DNS provider? I already have OWA secured behind Microsoft Entra ID Application Proxy using a different URL, so that is not a factor.
I’m following up after a bit of testing. It looks like Microsoft Entra ID resolves HMA SPNs using external DNS. In fact, after the initial HMA handshake and auth token is provided, Microsoft Entra ID really just points the client to your Exchange external URL (rather than proxying the connection).
This means I was unable to remove the Exchange external URL as I’d hoped. Instead, I did two things:
* I used IIS IP Address Restrictions to restrict the OWA/ECP virtual directories to local IPs only, which allows Microsoft Entra ID Application Proxy to continue to work (it uses a local agent) but prevents others from connecting directly to OWA over the internet
* I manually disabled legacy auth on the following directories, which prevents legacy connections to Exchange:
– disabled basic auth for ActiveSync
– disabled Windows auth for EWS
– disabled Windows auth for MAPI
– disabled Windows auth for OAB
This seems to achieve the desired behavior with minimal issues. AAD-AP still works, Teams calendar sync still works. The only issue is that mailbox migrations do not work, since MRS is trying to connect to EWS using Windows auth. I’m opening a ticket with Microsoft to see if MRS can use modern authentication.
Hi Kyle
Thanks for your great comment to Ali’s article you notice disabling basic auth. I am still wondering why the article doesn’t go into disabling the legacy authentication methods. Without disabling those methods, OAUTH won’t secure the access from attackers outside the network.
We are providing access to on perm and online exchange mailboxes to our customers using HMA in a split way. External incoming connections to EWS and EAS gets to a subset of virtuell directories using OAUTH as the only authentication method. An internal request to EWS goes to a different subset of virtuell directories where OAUTH is enabled, but legacy authentication methods are still allowed to ensure non modern auth applications still work. To the same subset the Exchange Online migration endpoint accessing the /ews/mrsproxy.svc path we route to. This ensue migrations are still working.
Now I am coming to my question (to you and maybe Ali if he reads it). I hope someone has an helpful idea.
Outlook for Android/iOS is able to access the mailbox using OAUTH. The native iOS Mail client also connects without any problem after allowing access globally for the app “Apple Internet Accounts”. After doing so for the GMAIL app as well the native GMAIL client on android devices connects to Exchange Online Mailboxes, but not to Onprem mailboxes. Any idea where this can come from?
Thanks for your support in advance.
Cheers
Michael
Hi Ali,
thank you for your courses. They are very helpful.
I have not a Exchange Online Configuration but i want to configure for my Users MFA for the Outlook Web Access. I want to this through Microsoft Entra ID Application Proxy. I have P1 license.
What would you think about this ?
That’s an excellent solution.
Hi there!
We are using on-prem exchange and wants to enable modern auth.
What would the impact be on end user PC/Mobile?
Is it possible to enable it to a specific users?
Hi Ali. I’ve always been helped by your posts.
Thanks to your article, I was able to use MFA when setting up Outlook.
I have a question.
In the article below, the Mobile outlook app supports HMA. And MS gave a guide to block EAS.
https://learn.microsoft.com/en-us/exchange/clients/outlook-for-ios-and-android/use-hybrid-modern-auth?view=exchserver-2019
If block EAS, it will be able to use HMA in Oulook App. (+Conditional Access)
However, it does not work in native apps of iOS and Android.
What I want is for users to require MFA when using on mobile. EXO can do this, Onpremise doesn’t.
Is it possible?
Hi,
Are you saying that Hybrid Modern Auth does not work with native iOS and Android apps?
Regards,
Sam
Hi Ali,
first let me thank you for that awesome article.
I am tryin to find the next article for “Exchange OWA (Outlook Web Access) and ECP (Exchange Control Panel) do not work with modern authentication. To secure that, we will write another article.”
Is this one not published yet, or am i blind 🙂
Thank you very much.
Kind reagards
Paolo
Thanks Ali, great write-up.
Could you confirm that if we move use modern auth with on-premise exchange, we still have the option to use basic auth for domain-joined computers?
Ideally, we would like a split approach where devices off the network connect in via Microsoft Entra ID and modern auth, whilst domain joined computers continue to authenticate directly with Exchange like they did.
Ali,
Thank you for the leg work here! Good work! Exciting prospect for those who cannot move mailboxes to the cloud. I just want to confirm that this pattern can work when Microsoft Entra ID is delegating to an external IdP like Okta for authentication. Note, we are hoping to delauth to Okta and naturally delauth to AD and apply a sign on policy that prompts for MFA.
Thoughts?
Best Regards,
Bryan
we do have skype for business on-prem and UM role enabled on the exchange 2016 on-prem . Do we need to enable skype for business on-prem for HMA in-order to ensure functionality doesn’t break
Our initial requirement is to set up conditional access policies for mobile devices via intune, we only have exchange on-prem at moment and we don’t intend to make changes on the skype for business
It’s recommended that the HMA state be the same across Skype for Business and Exchange (and their online counterparts) to reduce the number of prompts. That’s because Skype for Business and Exchange work close with each other.
Configure HMA for both Exchange and Skype for Business. You have to set it in four places:
-EX (Exchange Server on-premises)
-EXO (Exchange Online)
-SFB (Skype for Business)
-SFBO (Skype for Business Online)
Hi ALI TAJRAN,
Thanks for the great article.
I have 2 questions.
In on-premises Exchange with basic authentication, could you please explain how it works, authenticating user’s AD credentials, when users open Outlook without them entering their AD credentials how Outlook validates their credentials auto? Also explaining the traffic flow for basic authentication.
Second question was when modern authentication was enabled for on-premises users there was an issue observed where users were prompted with Microsoft sign-in option when they opened Outlook so modern authentication change was rolled back. Why this could occur?
Appreciate your feedback for these questions.
Thanks.
Dinesh
Hi Dinesh. This is the similar thing I am facing right now for a customer. Do you happen to find the answer of this scenario?
Hello,
Thanks you for such a great article.
Question.
If my company still uses activesync clients in office 365 and on-premise, will we harm them because they still have to use basic authentication with their mobile devices?
No, it will not affect the users.
When you enable modern authentication, you allow its use. It doesn’t mean that basic authentication doesn’t work anymore. Your existing basic authentication client will continue to work.
From there, you can start to identify the basic authentication clients and start moving them to modern authentication.
Hello, thank you for this great guide. I have one question: Does it affect user when i activate Modern Authentication in Exchange Online? (In your guide the Step 1.) Because i would first activate it and see what happens for some time before continuing. And already disable some legacy protocols.
Thanks a lot!
Hi Edmund,
No, it will not affect the users.
When you enable modern authentication, you allow its use. It doesn’t mean that basic authentication doesn’t work anymore. Your existing basic authentication client will continue to work.
From there, you can start to identify the basic authentication clients and start moving them to modern authentication.
Great to hear that, thank you very much for this information. You have a really great site with great guides just perfect for people like me who starts to work more with O365. Keep on going 🙂
Hi Ali, just wanted to update you after i implemented this guide in our system.
It worked well and you were right with the existing clients. Thanks a lot for this! BR Edmund
For this to work properly, do I have to point the AutoDiscover DNS record to the on-premise Exchange instead of Office 365?
If you have mailboxes in Office 365 only, you don’t need to enable Hybrid Modern Authentication on-premises. You might want to verify that modern authentication is enabled in the tenant.
Do you have:
-Mailboxes on-premises? Autodiscover needs to point to the on-premises Exchange Server.
-Mailboxes in Office 365 only? Autodiscover needs to point to Office 365.
-Mailboxes on-premises and in Office 365? Autodiscover needs to point to the on-premises Exchange Server.
Read more: Autodiscover URL in Exchange Hybrid.