Microsoft automatically enables security defaults in new Microsoft 365 tenants to protect you from phishing…
Prevent MFA fatigue attacks in organization
Many MFA fatigue attacks happen worldwide, and it’s the news everywhere. Organizations are scared that users give access to attackers when they get an MFA request notification and press approve by accident. So how to prevent MFA fatigue attacks? In this article, you will learn how to protect the organization from MFA fatigue attacks.
Table of contents
MFA fatigue attacks
MFA fatigue attacks, also known as MFA bombing, is a strategy used by hackers to get around Multi-Factor Authentication when breaking into user accounts.
Hackers use stolen, leaked, or guessed credentials for their login attempt, and the account owner is continuously bombarded with prompts asking them to verify their identity. This barrage continues until they slip up, are worn down psychologically, or the attacker moves on.
Read more on how to protect the organization from using leaked/breached passwords:
- Secure Active Directory passwords from breaches
- Configure Microsoft Entra Password Protection for on-premises
How to prevent MFA fatigue attacks
Protect the organization from MFA fatigue attacks and enable the below Microsoft Authenticator features in Azure AD:
1. Enable Azure MFA number matching
Read more in the article Enable Azure MFA number matching.
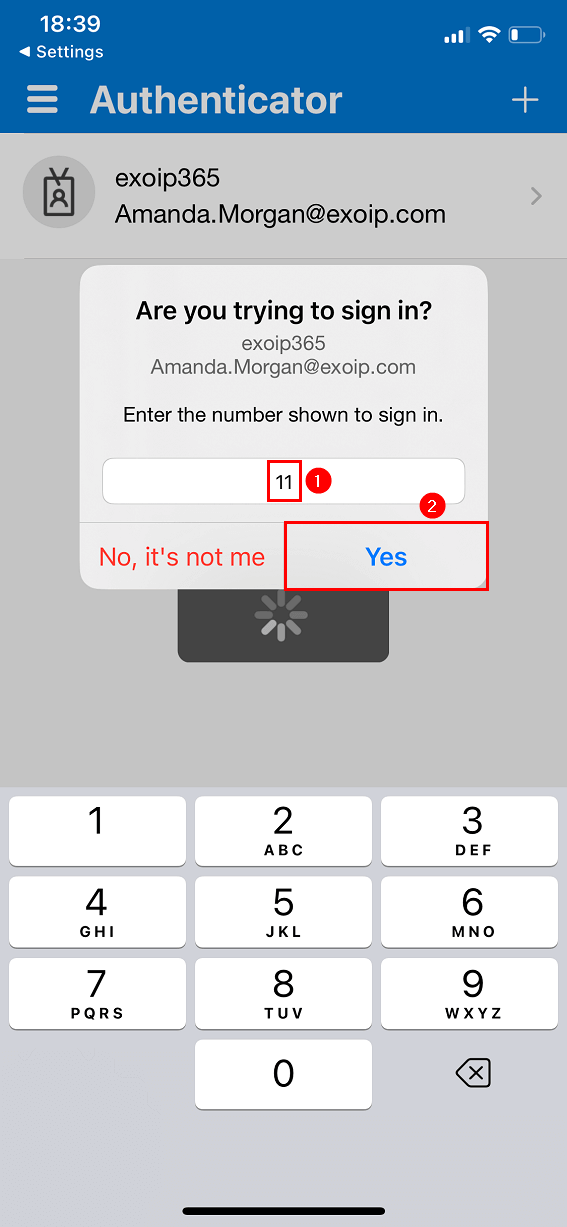
Require number matching for push notifications is a feature in Azure AD. It presents users with a number when they respond to an MFA push notification using the Authenticator app. They need to type that number into the app to complete the approval.
Note: Microsoft will enable Azure MFA number matching by default for all tenants from February 27, 2023.
The below screen shows how it looks in the Microsoft Authenticator app for the user.
2. Enable Azure MFA application name
Read more in the article Enable Azure MFA application name.
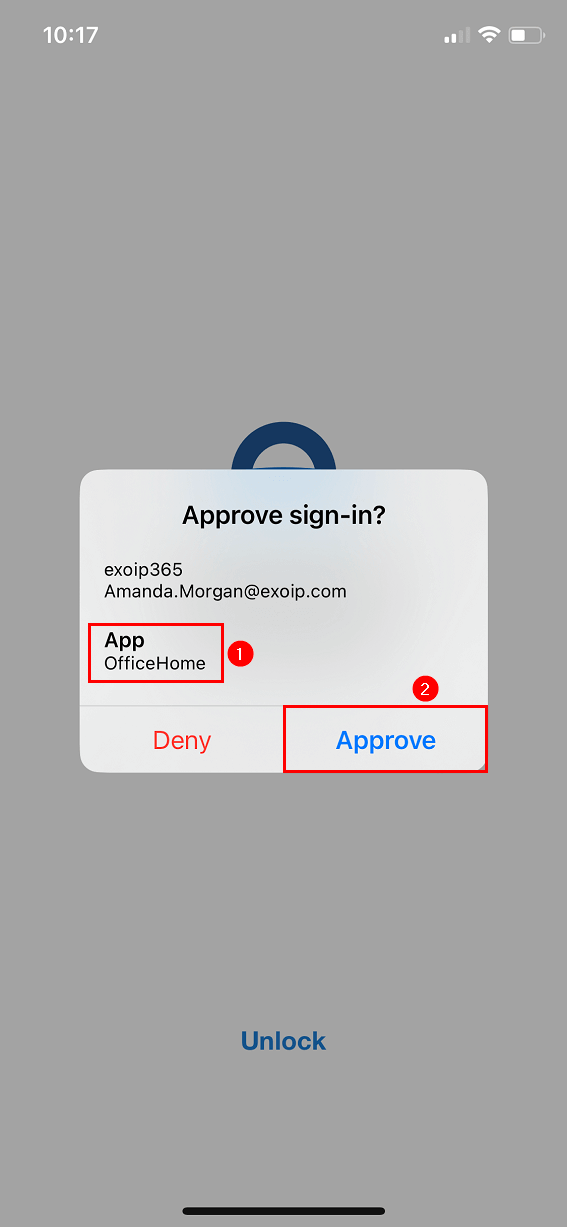
Show application name in push and passwordless notifications is a feature in Azure AD. When a user receives a passwordless phone sign-in or MFA push notification in Microsoft Authenticator, they’ll see the name of the application that requests the approval where the sign-in originated from.
The below screen shows how it looks in the Microsoft Authenticator app for the user.
3. Enable Azure MFA geographic location
Read more in the article Enable Azure MFA geographic location.
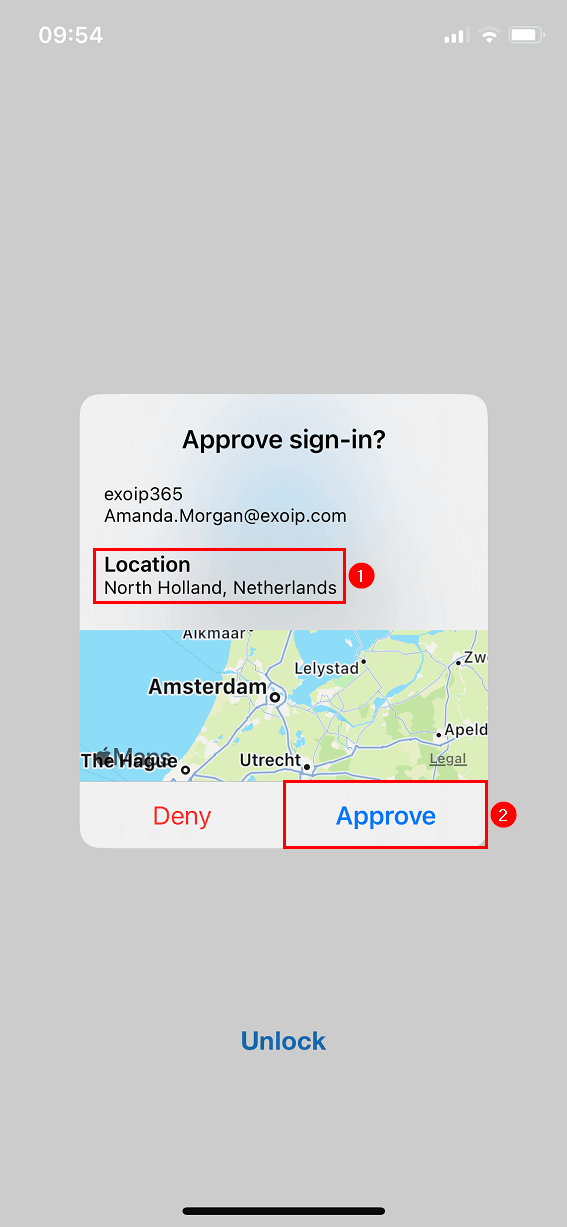
Show geographic location in push and passwordless notifications is a feature in Azure AD. When a user receives a passwordless phone sign-in or MFA push notification in Microsoft Authenticator, they’ll see the geographic location based on the IP address that requests the approval where the sign-in originated from.
The below screen shows how it looks in the Microsoft Authenticator app for the user.
That’s it!
Read more: Add tag to external emails in Microsoft 365 for extra security »
Conclusion
You learned how to prevent MFA fatigue attacks. Improve MFA security by enabling all these features. It’s a straightforward process that helps security tremendously in the organization. Don’t wait, and do it now!
Did you enjoy this article? You may also like Export disabled users from Active Directory. Don’t forget to follow us and share this article.



This Post Has 0 Comments