You have a Domain Controller running in the organization. But only one DC running in…
Configure Windows LAPS step by step
Goodbye, Microsoft LAPS, and a big welcome to Windows LAPS. Windows LAPS is finally available for both cloud and on-premises environments. Every administrator should set up Windows LAPS in Active Directory for easier management of the domain-joined device’s local passwords. In this article, you will learn how to install Windows LAPS step by step.
Table of contents
What is Windows LAPS?
Windows Local Administrator Password Solution (Windows LAPS) is a Windows feature that automatically manages and backs up the password of a local administrator account on your Azure Active Directory-joined or Windows Server Active Directory-joined devices. You also can use Windows LAPS to automatically manage and back up the Directory Services Restore Mode (DSRM) account password on your Windows Server Active Directory domain controllers. An authorized administrator can retrieve the DSRM password and use it.
You might already be familiar with the existing Microsoft security product known as Local Administrator Password Solution (LAPS). LAPS has been available on the Microsoft Download Center for many years. It is used to manage the password of a specified local administrator account by regularly rotating the password and backing it up to Active Directory (AD). LAPS has proven to be an essential and robust building block for AD enterprise security on premises. We’ll affectionally refer to this older LAPS product as “Legacy LAPS”.
Windows LAPS doesn’t require you to install legacy LAPS. You can fully deploy and use all Windows LAPS features without installing or referring to legacy LAPS.
Note: The feature is ready to go out of the box. You no longer need to install an external MSI package! Microsoft will deliver future fixes or feature updates via the normal Windows patching processes.
Windows LAPS benefits
Benefits of using Windows LAPS:
- Use Windows LAPS to regularly rotate and manage local administrator account passwords and get these benefits:
- Protection against pass-the-hash and lateral-traversal attacks
- Improved security for remote help desk scenarios
- Ability to sign in to and recover devices that are otherwise inaccessible
- A fine-grained security model (access control lists and optional password encryption) for securing passwords that are stored in Windows Server Active Directory
- Support for the Azure role-based access control model for securing passwords that are stored in Azure Active Directory
Windows LAPS Management
The below options are available to manage and monitor Windows LAPS:
- The Windows Server Active Directory Users and Computers properties dialog
- A dedicated event log channel
- A Windows PowerShell module that’s specific to Windows LAPS
No more dedicated LAPS Management client (LAPS UI) exists, as we had in Legacy Microsoft LAPS.
Windows LAPS requirements
Windows LAPS is available on the following OS platforms with the specified update or later installed:
- Windows 11 22H2 – April 11 2023 Update
- Windows 11 21H2 – April 11 2023 Update
- Windows 10 – April 11 2023 Update
- Windows Server 2022 – April 11 2023 Update
- Windows Server 2019 – April 11 2023 Update
Note: There are no license requirements to use Windows LAPS, and it’s integrated into Windows OS.
Do you want to find which Windows OS Builds are running in the organization? Read the article Export Windows OS build numbers.
How to configure Windows LAPS
To configure Windows LAPS in Active Directory, follow the below steps:
1. Update Windows Server
Ensure that you run Windows Update on all Domain Controllers. If you only update 1x Domain Controller and extend the Active Directory schema (next step), it will throw an error.
Read more: Active Directory health check with PowerShell script »
2. Extend Active Directory Schema
There is no Windows LAPS client to download and install on the Domain Controller like we are used to with Microsoft LAPS because it’s already integrated into Windows Server 2019 and higher.
1. Run PowerShell as administrator on the Domain Controller.
2. Run ipmo LAPS to import the LAPS module.
PS C:\> ipmo LAPS3. Run the gcm -Module LAPS command to verify the LAPS module is loaded.
Note: If there is no output after running above command, you must update your Windows Server to the supported version (see above).
PS C:\> gcm -Module LAPS
CommandType Name Version Source
----------- ---- ------- ------
Function Get-LapsAADPassword 1.0.0.0 LAPS
Function Get-LapsDiagnostics 1.0.0.0 LAPS
Cmdlet Find-LapsADExtendedRights 1.0.0.0 LAPS
Cmdlet Get-LapsADPassword 1.0.0.0 LAPS
Cmdlet Invoke-LapsPolicyProcessing 1.0.0.0 LAPS
Cmdlet Reset-LapsPassword 1.0.0.0 LAPS
Cmdlet Set-LapsADAuditing 1.0.0.0 LAPS
Cmdlet Set-LapsADComputerSelfPermission 1.0.0.0 LAPS
Cmdlet Set-LapsADPasswordExpirationTime 1.0.0.0 LAPS
Cmdlet Set-LapsADReadPasswordPermission 1.0.0.0 LAPS
Cmdlet Set-LapsADResetPasswordPermission 1.0.0.0 LAPS
Cmdlet Update-LapsADSchema 1.0.0.0 LAPS4. Run the Update-LapsADSchema cmdlet, press A, and follow with Enter.
PS C:\> Update-LapsAdSchema
The 'ms-LAPS-Password' schema attribute needs to be added to the AD schema.
Do you want to proceed?
[Y] Yes [A] Yes to All [N] No [L] No to All [S] Suspend [?] Help (default is "Y"): A3. Check LAPS attributes
To verify that the LapsAdSchema ran successfully, run the Update-LapsAdSchema again with the -Verbose parameter.
PS C:\> Update-LapsAdSchema -VerboseThe end of the output is important, which shows that the LAPS schema is already extended successfully with the attributes:
- msLAPS-PasswordExpirationTime
- msLAPS-Password
- msLAPS-EncryptedPassword
- msLAPS-EncryptedPasswordHistory
- msLAPS-EncryptedDSRMPassword
- msLAPS-EncryptedDSRMPasswordHistory
VERBOSE: The 'computer' classSchema already has a required mayContain: msLAPS-PasswordExpirationTime
VERBOSE: The 'computer' classSchema already has a required mayContain: msLAPS-Password
VERBOSE: The 'computer' classSchema already has a required mayContain: msLAPS-EncryptedPassword
VERBOSE: The 'computer' classSchema already has a required mayContain: msLAPS-EncryptedPasswordHistory
VERBOSE: The 'computer' classSchema already has a required mayContain: msLAPS-EncryptedDSRMPassword
VERBOSE: The 'computer' classSchema already has a required mayContain: msLAPS-EncryptedDSRMPasswordHistory
VERBOSE: The 'computer' classSchema already has all expected LAPS-related mayContains
VERBOSE:
VERBOSE: ProcessRecord completed
VERBOSE:
VERBOSE: EndProcessing started
VERBOSE: EndProcessing completedGo to a Windows 10/Windows 11 AD object properties and select the Attribute tab.
Note: If you don’t see the Attribute Editor tab, click in Active Directory Users and Computers in the menu bar on View and enable Advanced Features.
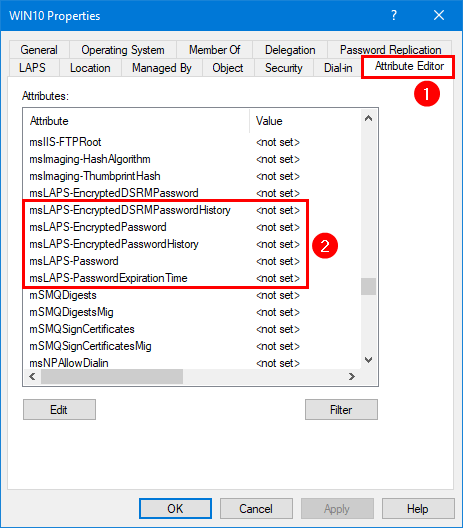
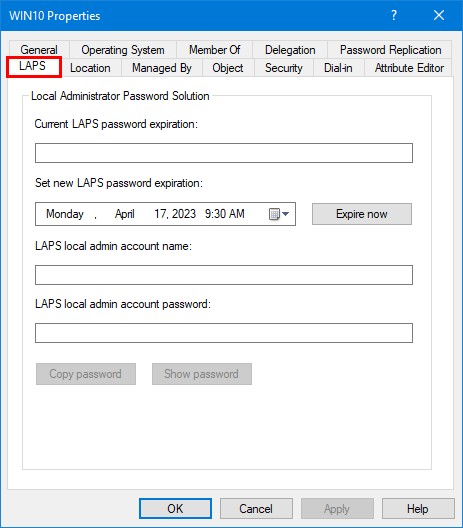
You will also see the LAPS tab, and you can click on it. But it’s empty for now and will populate information once you complete all the steps.
4. Set LAPS AD Computer permission
The managed device needs to be granted permission to update its password. This action is performed by setting inheritable permissions on the Organizational Unit (OU) the device is in. The setting will apply to all nested OUs too.
In our example, we want set permissions on the Company OU.
Set the permissions on the Company OU with the Set-LapsADComputerSelfPermission cmdlet.
Note: Do you have computers in other OUs? You need to repeat the below and add the OUs which have computers added to them.
PS C:\> Set-LapsADComputerSelfPermission -Identity "Company"
Name DistinguishedName
---- -----------------
Company OU=Company,DC=exoip,DC=localSuppose it fails because the OU name is used multiple times in Active Directory, then copy the DistinguishedName and place that in the command.
PS C:\> Set-LapsADComputerSelfPermission -Identity "OU=Company,DC=exoip,DC=local"5. Set up LAPS GPO
Configure a GPO for LAPS and enable its settings.
1. Start Group Policy Management on the Domain Controller.
2. Right-click the Desktops OU.
3. Click Create a GPO in this domain, and link it here.
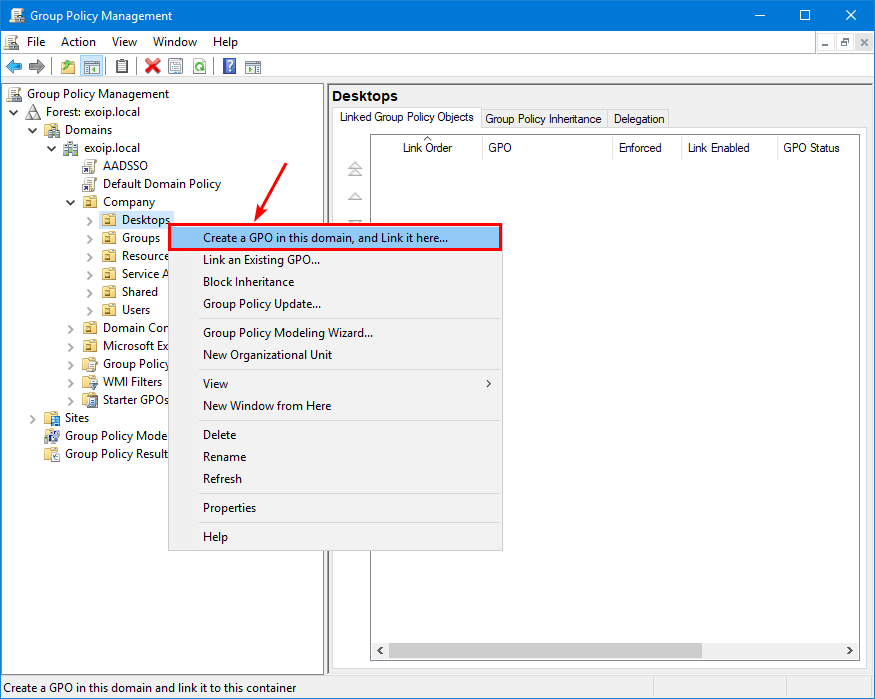
Is the new Group Policy Object (GPO) a user or computer policy? Or will you place user and computer policy settings in the GPO? If it’s a Computer Policy, we recommend placing a C_ before the group policy name. If it’s a User Policy, make it a U_. Do you want to add computer and user policy settings in a new group policy object? Name it CU_.
- C stands for Computer Policy
- U stands for User Policy
- CU stands for Computer and User Policy
In our example, the GPO is a computer policy, so the name will start with C_.
4. Give the Policy the name: C_LAPS.
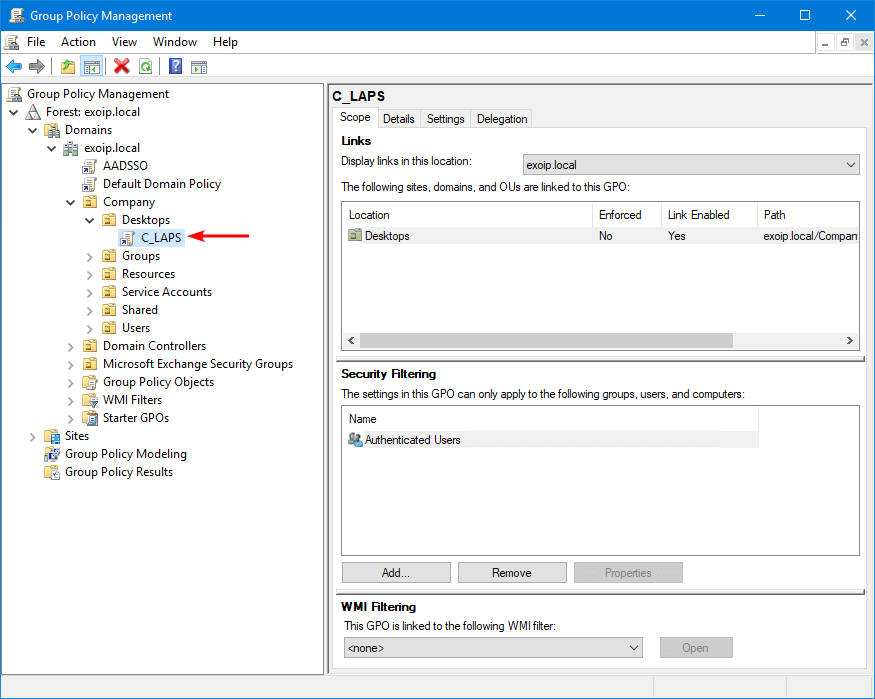
5. Right-click the C_LAPS GPO and click Edit.
6. Navigate to Computer Configuration > Policies > Administrative Templates > System > LAPS.
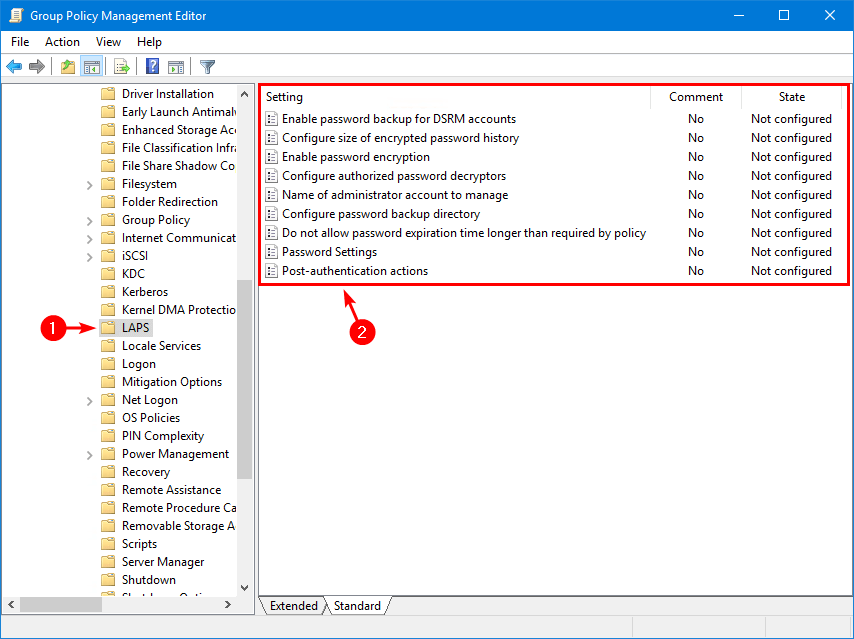
7. Double-click on Configure password backup directory setting.
8. Select Enabled and choose the backup directory Active Directory.
Important: You have to ENABLE the setting and select Active Directory or Azure Active Directory. Otherwise, the local administrator password is not managed and will not work.
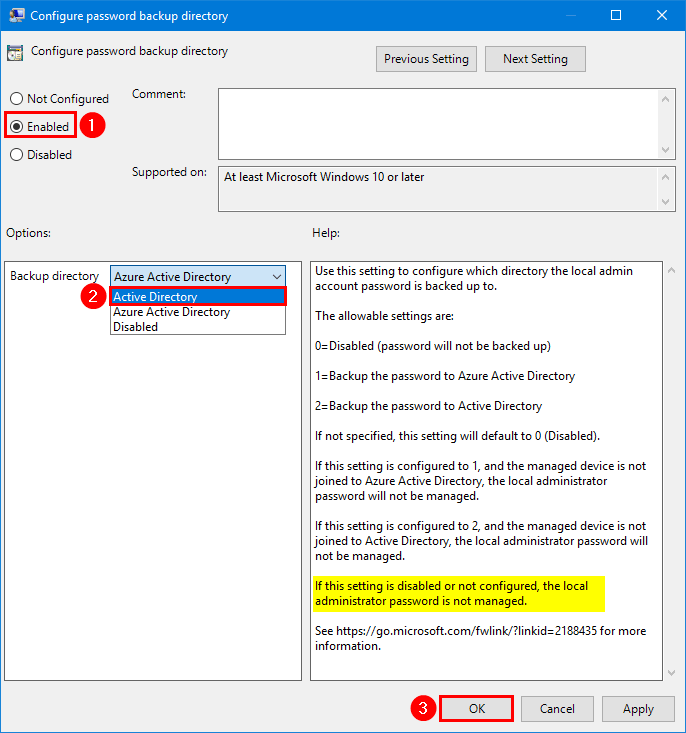
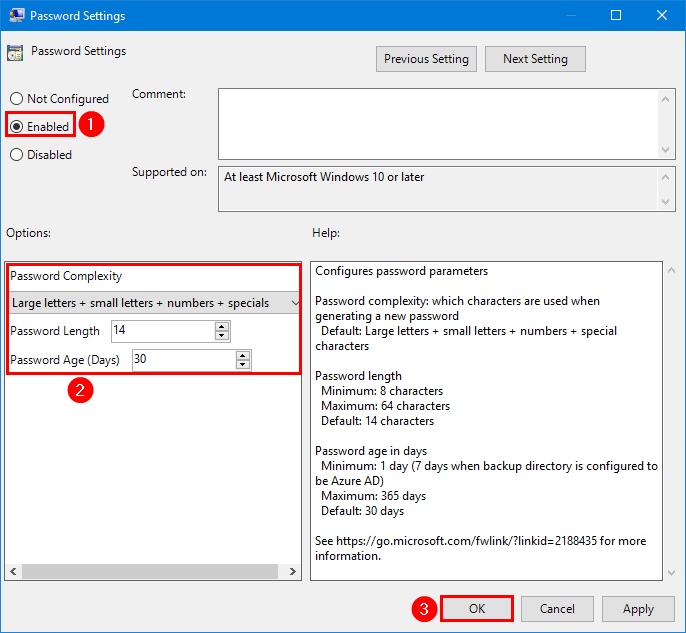
9. Double-click on Password Settings setting.
10. Select Enabled and configure the password complexity.
11. Double-click on Name of administrator account to manage setting.
12. Select Enabled and insert the administrator account name lapsadmin.
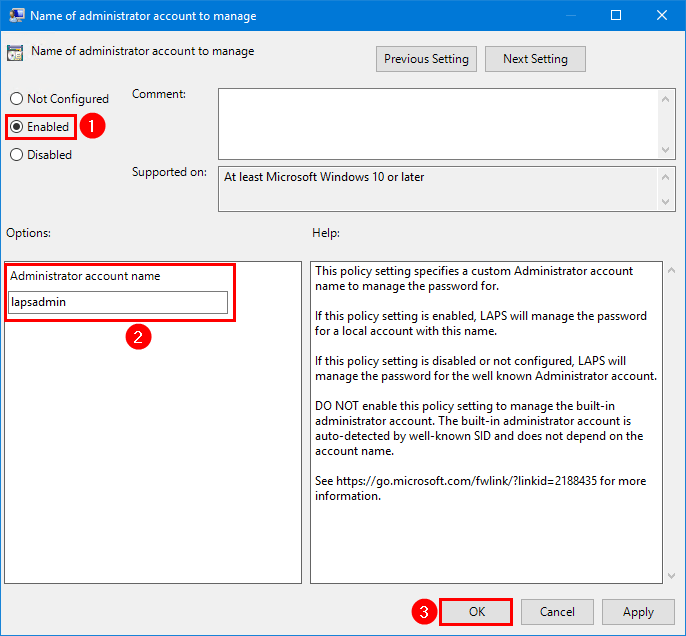
13. This is what the LAPS GPO state looks like.
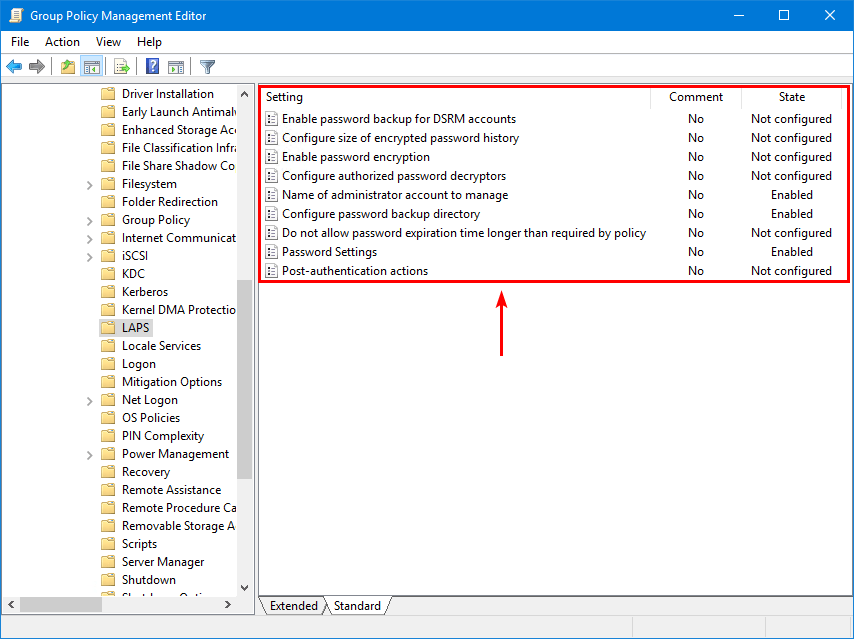
6. Create local admin account
In the previous step, we did enable the Name of administrator account to manage setting and set the administrator account name: lapsadmin.
The LAPS GPO will not create your local administrator account on all the machines. That’s something you have to take care of with another GPO, a PowerShell script, or another choice.
Important: Disable all the other local admin accounts and ensure that only the lapsadmin account is enabled for security purposes.
This is what it will look like on a computer.
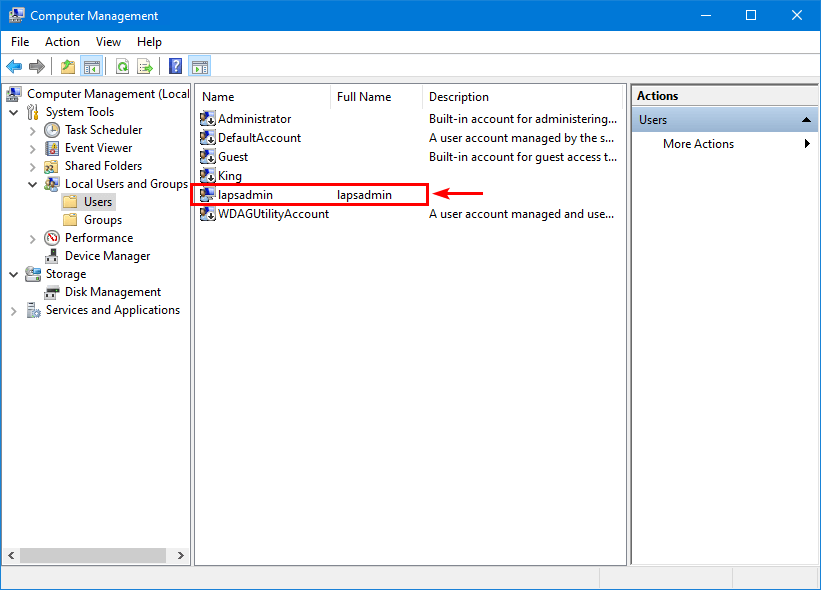
Note: After completing all the above steps, restart the domain-joined Windows computer to have the changes take effect.
The Windows LAPS configuration is successfully completed.
Get LAPS password
Now let’s see how to retrieve the LAPS Password in GUI and PowerShell.
Get LAPS password with GUI
Get the LAPS password directly from the Active Directory Users and Computer console.
1. Start Active Directory Users and Computers.
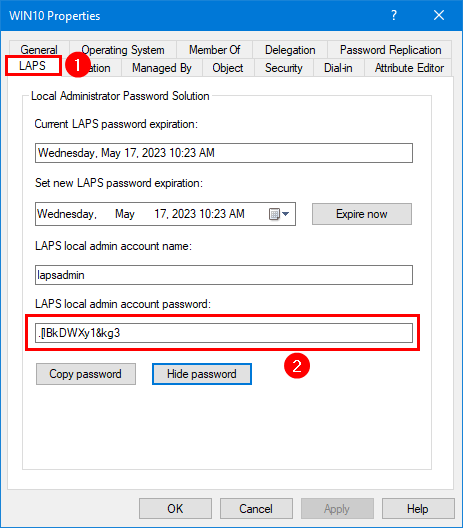
2. Go to the AD computer object properties.
3. Select the tab LAPS.
You will see that the fields are now filled in and are not empty anymore. It means that Active Directory connected with the Windows computer and synchronized the information.
4. Click on Show Password.
Get LAPS password with PowerShell
An excellent way to get the LAPS password and information is with PowerShell.
1. Run PowerShell as administrator
2. Run the Get-LapsADPassword cmdlet and fill in the target computer, including the -AsPlaintText parameter.
PS C:\> Get-LapsADPassword "WIN10" -AsPlainText
ComputerName : WIN10
DistinguishedName : CN=WIN10,OU=Desktops,OU=Company,DC=exoip,DC=local
Account : lapsadmin
Password : .[lBkDWXy1&kg3
PasswordUpdateTime : 4/17/2023 10:23:46 AM
ExpirationTimestamp : 5/17/2023 10:23:46 AM
Source : EncryptedPassword
DecryptionStatus : Success
AuthorizedDecryptor : EXOIP\Domain AdminsSign in with LAPS password
Always test if everything works as you expect and test the LAPS local admin account password.
Sign in with the local admin account lapsadmin and the password that appears in LAPS for the computer.
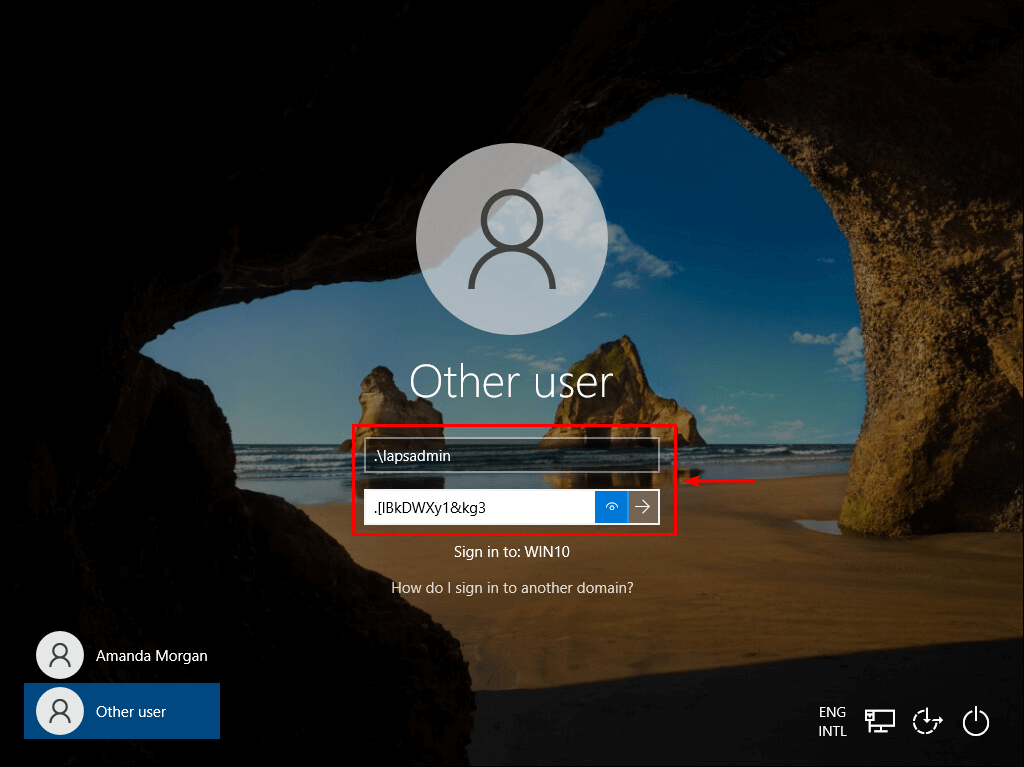
We are successfully signed into the Windows 10 computer, with the Local Administrator Password generated from Active Directory (LAPS).
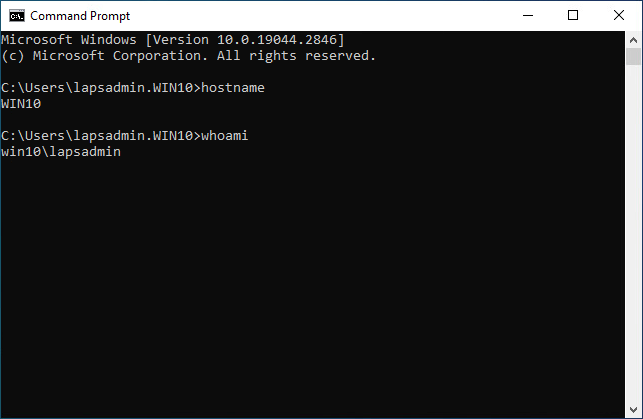
Reset Windows LAPS password
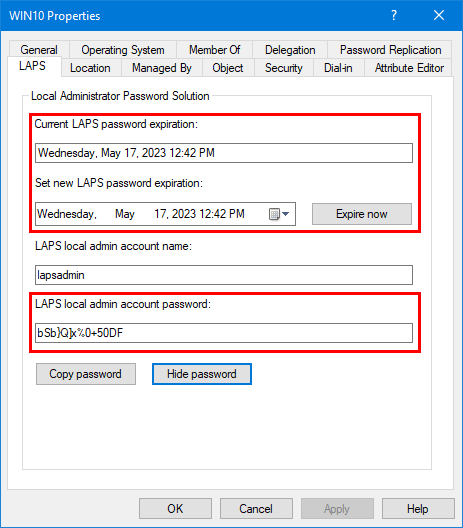
There are times when you want to reset the Windows LAPS password.
1. Click on Expire now.
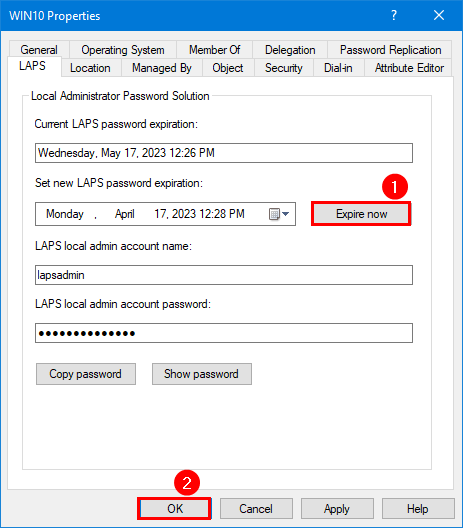
2. Run a GPO update on the Windows computer and verify that the LAPS local admin account password is reset.
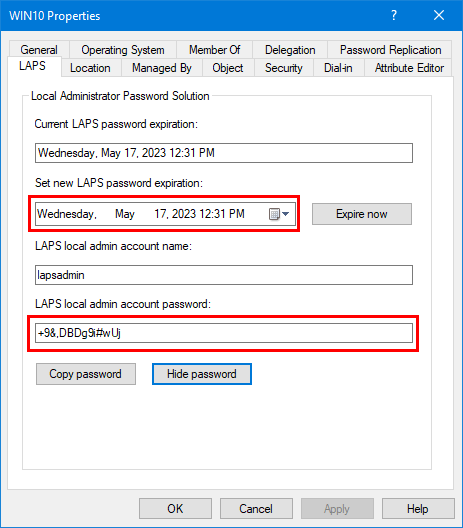
3. You can also run the Reset-LapsPassword cmdlet on the Windows computer.
Reset-LapsPassword4. It will reset the current/new password expiration and LAPS local admin account password.
You successfully set up Windows LAPS in Active Directory and tested that everything works.
Read more: Create Central Store for Group Policy Administrative Templates »
Conclusion
You learned how to configure Windows LAPS in Active Directory. The Windows Local Administrator Password Solution is an excellent Windows feature to manage local administrator passwords for domain-joined computers. Configure it once, and Microsoft will automatically push updates for it through Windows Updates.
Did you enjoy this article? You may also like Manage Microsoft Office with Group Policy. Don’t forget to follow us and share this article.


These are the best instructions for new deployments! Thanks for this.
Great how to,
thank you so much for sharing!
Great guide!! Question: my domain is mixed environment of 2019 and 2012 Domain Controllers. Will Windows LAPS work? I’m concerned about extending the schema if the 2012 servers won’t support the attributes.
Great guide. thanks!
Hi Ali,
This is the best how-to that I could find. Thanks for the awesome work!
My question is, does LAPS generate the password automatically whatever the password age is set to?
I created local admin account and pushed it through domain joined computers, I guess the part that is not clear to me, do we create the password or LAPS does.
Thanks again!
HI
After updating the server and executing the commands line by line, there is still no laps folder in the group policy management console!
There are lapsed folders in Local Group Policy Editor in Active Directory
Thanks for an outstanding write-up.
I have read on Microsoft’s websites that the new Windows LAPS doesn’t play very nicely with the old, original LAPS solution, but it is hard to find out exactly what is needed to really make it work right. Have you worked in this area too?
Thanks for the detailed guide. As I see, only Domain Admins can see / reset the password. Can I change it to some other group? I do not get, how this is made correctly.
Thanks again!
Hello Ali,
I have 2 2016 DCs in
Can i upgrade the AD Shema from any other Server or PC (With Admin Account) and then folow ur instructions after Step .4 or it will cause Problems..
Thanks for replying
You need Windows Server 2019 or higher, including the ADDS role installed, to follow this guide.
I have configured Password encryption in LAPS GPO, only DAs can decrypt passwords. Is it possible to add another account to “AuthorizedDecryptor”?
Im trying to add a user account that runs a scrpit to update our password manager solution without giving it DA.
This laps that was released as part of a patch has caused havoc in our environments. Firstly it stops us from installing any software that has to create local accounts to run a service for our apps. It also breaks the database installs. In the current environment it breaks our database connections on the local machine. ms for you….
Hi Ali,
Thanks for your tutorial (again)!
I have tried to implement the Windows LAPS (not the legacy microsoft laps), but somehow the LAPS tab in AD remains empty and the powershell command doesn’t display an output. I have followed your procedure to the letter and I can see that the policy is applied. Am I overlooking something?
Thanks!
greetings,
Guillaume
why can’t we enable the permission on the computers present in the default “computers” OU ?
Thank you for your contribute this info. i already has the Microsoft laps in our enviroment , looking for how to use Windows laps or migration config. thanks
Under computer – policies – admin templates – LAPS
I only have 4 settings
Password settings
name of admin account o manage
do not allow password expiration longer than required
enable local admin password mgt.
What do I need to do to enable the other settings you show? i have the Laps,admx files in the sysvol …. folder.
Thanks
The April 2023 update the admx file is updated on the local machine (server 2019 and 2022). Retrieve the “LAPS.admx” and the “en-US\LAPS.adml” files under the folder in “%windir”\PolicyDefinitions” copy it into the GC main repository (\DOMAIN\SYSVOL\DOMAIN\Policies\PolicyDefinitions for the admx file and .\en-US for the adml file. Wait for the replication
John, I saw the same thing, but I was looking at the old location. The new LAPS policy can be found under the System folder. Computer Configuration > Administrative Templates > System > LAPS.
Ali,
I left a post last week about not being able to see LAPS in GP. I had not installed the standalone version and was missing the admx/adml files. I thought the files I needed were something other than the laps.admx/adml files. I found that the laps files were installed by default to c:\windows\policy definitions. Since I have a defined central store for my admx files, they were not seen at the default location. I copied them to my central store and everything works as it should!
Thanks for all you do for the community. It is appreciated.
Kirk
Hi Ali,
Thank you for all this amazing posts i can’t find better explanations than yours and i have followed you for years.
I saw in this post that you need to create also a powershell script to create lapsadmin as as administrator if i am not wrong?
As i know from microsoft recomandations is it a good idea that laps with two security groups view and change to manage the default built in administrator?
Can we have a material about the tier model or implementation of laps solution in a tier model where it is complicated about the permission of the users that can read the password.
I will be thankfully if you will post something like this.
Ali-
As usual, another great article. Your “how to” writeups are among the best out there. Thanks for all you do!
I have an environment with all 2019 and 2022 DCs. I’ve run through all the steps and can see the LAPS attributes in the Attribute Editor. When I try to build the GPO LAPS doesn’t exist at Computer Configuration > Policies > Administrative Templates > System. My entries go from
…
Kerberos
Kernel DMA Protection
(LAPS should be here but isn’t)
Locale Services
Logon
…
I did see that when I click on Administrative Templates it takes a minute to expand, then says “Administrative Templates: Policy definitions (ADMX files) retrieved from the central store.”
Suggestions?
So i was following your guide and got all the way to the part of creating a GPO and when i open my GPMC and drill down to SYSTEM, LAPS is not there
You probably have a Central Store policy, so you don’t see the LAPS folder under Administrative Templates.
Copy the ADMX files from “C:\Windows\PolicyDefinitions” to your Central Store “\\exoip.local\SYSVOL\exoip.local\Policies”. After that, you will see the LAPS folder.
Hi Ali,
thanks for your great work! I following your blogs for years – awesome!
Do you know if I can use the new Windows LAPS if I have domain controllers on server 2016 or is server 2019 mandatory?
When it is possible how can I extend the AD schema on domain controllers with server 2016?
Thanks for your help!
Glad to hear that, Ralf.
Windows Server 2019 is mandatory.
Hey Ralf,
We have 2016 DCs and got it to work. You need at least a 2019 server with the AD DS role installed. Then you can update the schema and Windows LAPS will show up in AD. Note: DSRM with LAPS will not work until you upgrade your DCs to 2019 or above.
Dear Ali,
Can you guide how we can create user lapsadmin on local systems via GPO
How would this work in conjunction with policy that renames Administrator account to something else, should we specify an alternative name we used on the GPO than renames Admin account, or just not enable the policy at all, because it is technically going to manage the well known account?
Don’t enable the GPO setting “Name of administrator account to manage” and keep the “Not Configured” state.
Windows LAPS will show you the renamed local admin account and the generated local admin account password in ADUC/PowerShell.
Thank you!!
how do you change the Group from domain admins to and other group to read the passwords please
PS C:\> Find-LapsADExtendedRights -Identity newlaps
Awesome! Thanks a lot.
Hi Ali, I have been following your blog for years and you keep amazing me with your content. Thank you and keep it up!