How to complete a migration batch with PowerShell in Exchange Online manually? You created new…
How to configure Microsoft 365 to only accept mail from third-party spam filter
A third-party spam filter works perfectly with Microsoft 365 if you configure it correctly. One important configuration you must apply is to lock down the Exchange Online organization and only accept mail from the third-party spam filter. If you don’t do that, attackers bypass the third-party mail filtering and deliver spam messages directly to Microsoft 365. In this article, you will learn how to configure Microsoft 365 to only accept mail from third-party spam filter.
Table of contents
Attackers bypass third-party spam filtering
You must read the article about how attackers bypass third-party spam filtering so you have a clear understanding of how it works.
Only accept mail from third-party spam filter
Most third-party cloud service software shows you how to add a connector in Microsoft 365 for incoming messages and add the cloud service third-party IP addresses. After that, you can start enjoying mail filtering through the third-party spam filter. But unfortunately, this is not the correct approach. They forget to tell you an important step, which is to explicitly ONLY accept mail from the third-party service.
There are two methods to restrict mail to only accept from third-party spam filter:
- Create inbound connector and set restriction with PowerShell
- Create inbound connector and set restriction in Microsoft 365 Exchange admin center
Let’s look at both of these methods.
Method 1. Create inbound connector and set restriction with PowerShell
Lock down your Exchange Online organization to only accept mail from your third-party spam filter with PowerShell by following these steps:
1. Connect to Exchange Online PowerShell.
2. Run the New-InboundConnector cmdlet and fill in the details:
- Name: The name of the inbound connector
- RequireTls: True (consult your third-party spam provider)
- ConnectorType: Partner
- SenderDomains: *
- RestrictDomainsToIPAddresses: True
- SenderIpAddresses: The third-party spam filter IP addresses
PS C:\>New-InboundConnector -Name "Third-party spam filter" -RequireTls $true -ConnectorType Partner -SenderDomains * -RestrictDomainsToIPAddresses $true -SenderIpAddresses 46.121.243.14,62.114.24.104,69.63.54.125,94.42.233.5,185.202.12.210Method 2. Create inbound connector and set restriction in Microsoft 365 Exchange admin center
Lock down your Exchange Online organization to only accept mail from your third-party spam filter in Microsoft 365 Exchange admin center by following these steps:
1. Sign in to Microsoft 365 Exchange admin center.
2. Click on Mail flow > Connectors > Add a connector.
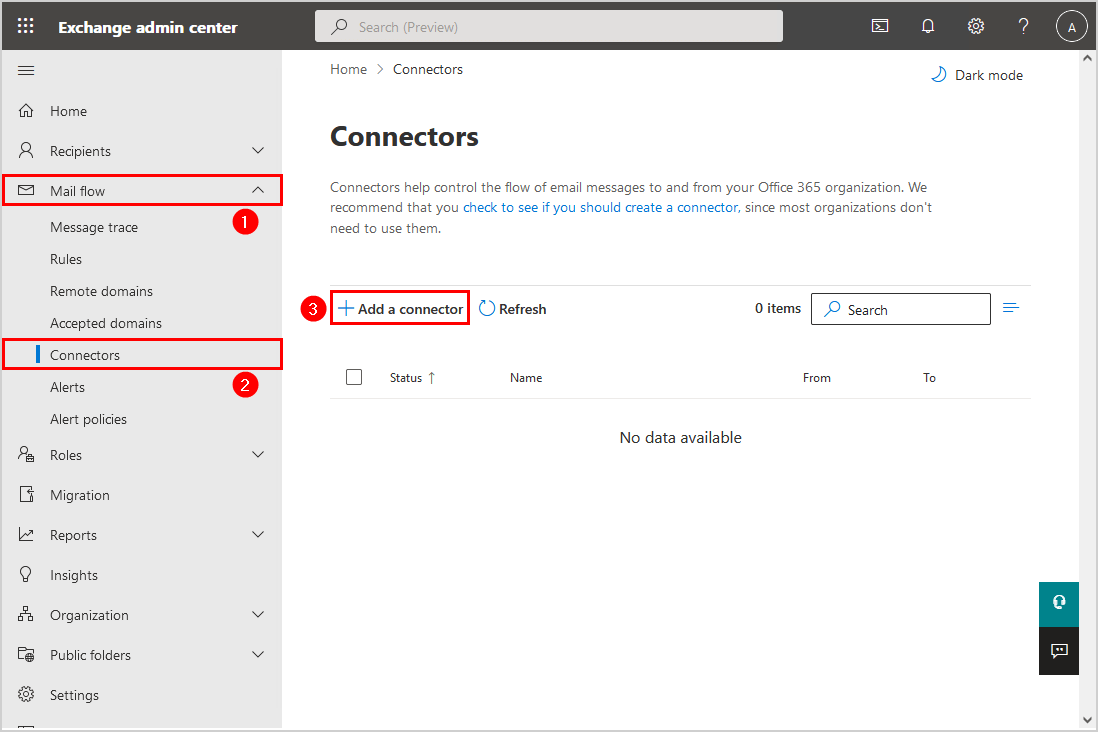
3. Choose Partner organization. Click Next.
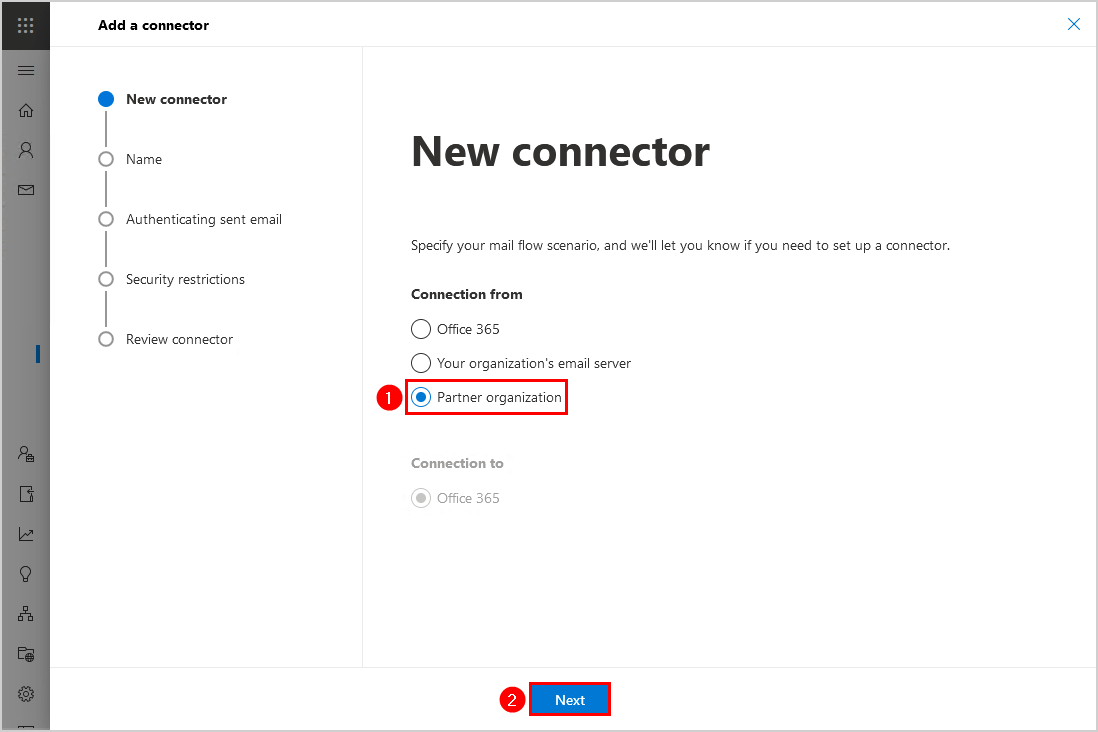
4. Give it the name Third-party spam filter. Check the checkbox Turn it on. Click Next.
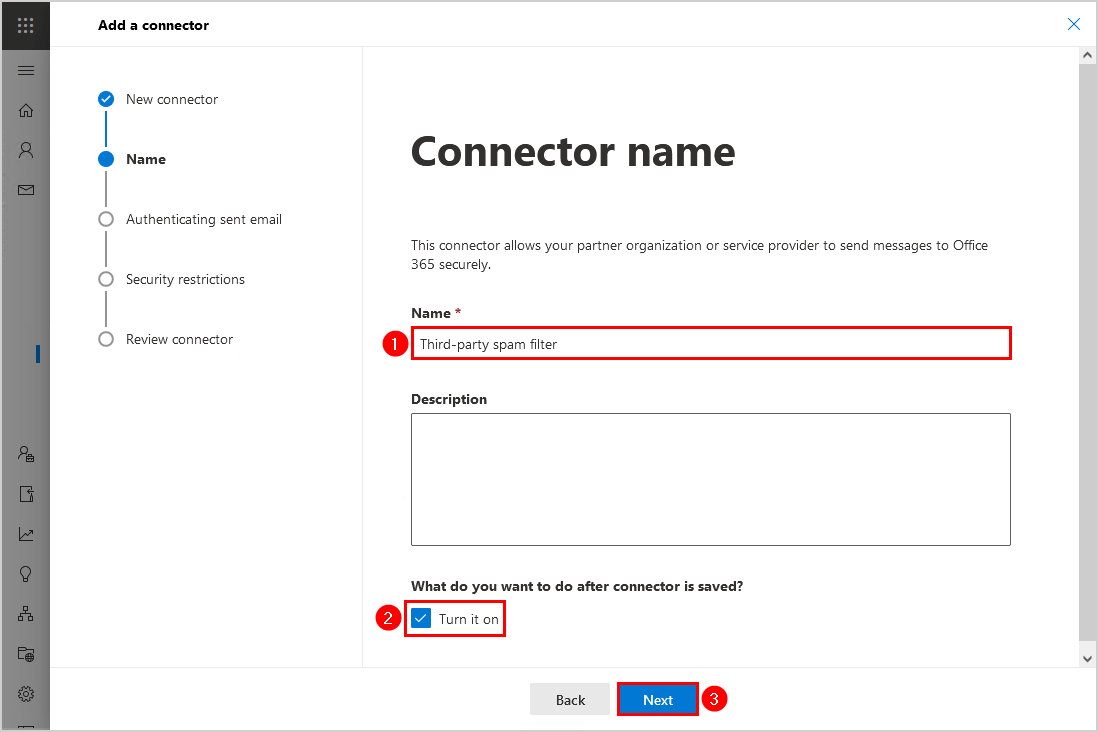
4. Select By verifying that the sender domain matches one of the following domains. Add the * (asterisk). Click Next.
Note: The * (asterisk) means every sender domain.
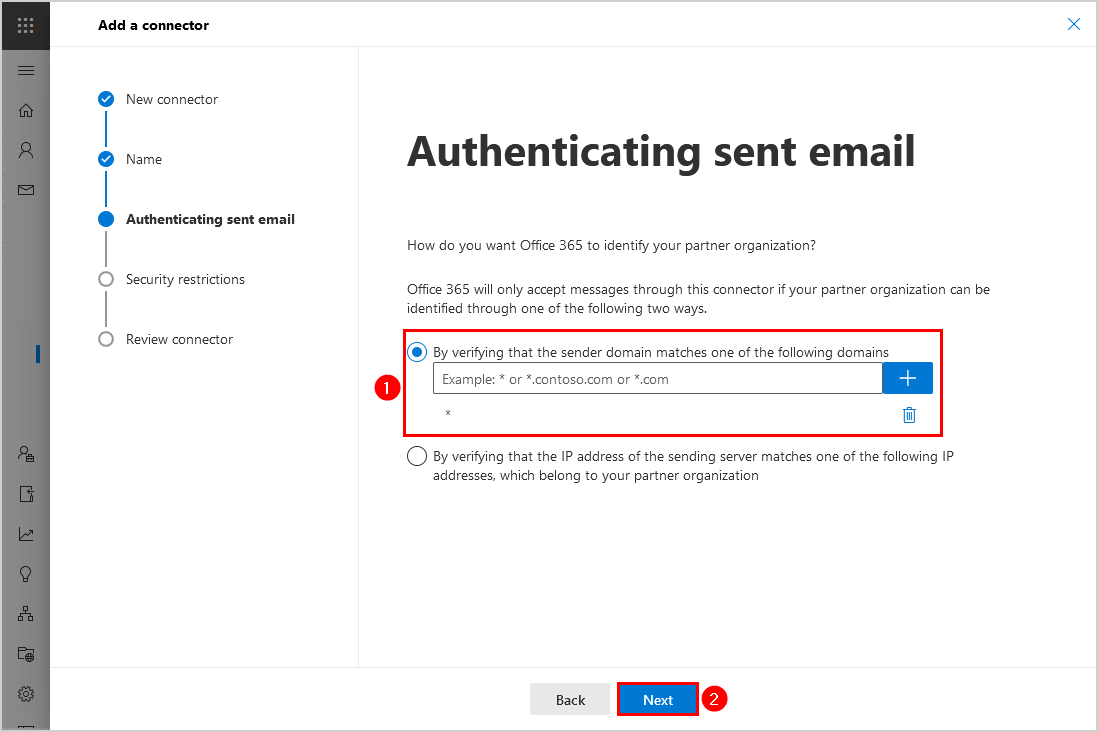
5. Select Reject email messages if they aren’t sent over TLS. Next, select Reject email messages if they aren’t sent from within this IP address range and add the third-party spam filter IP addresses. Click Next.
Consult your third-party spam filter and ask for their IP addresses. In our example, we use the cloud spam filter SpamBull.
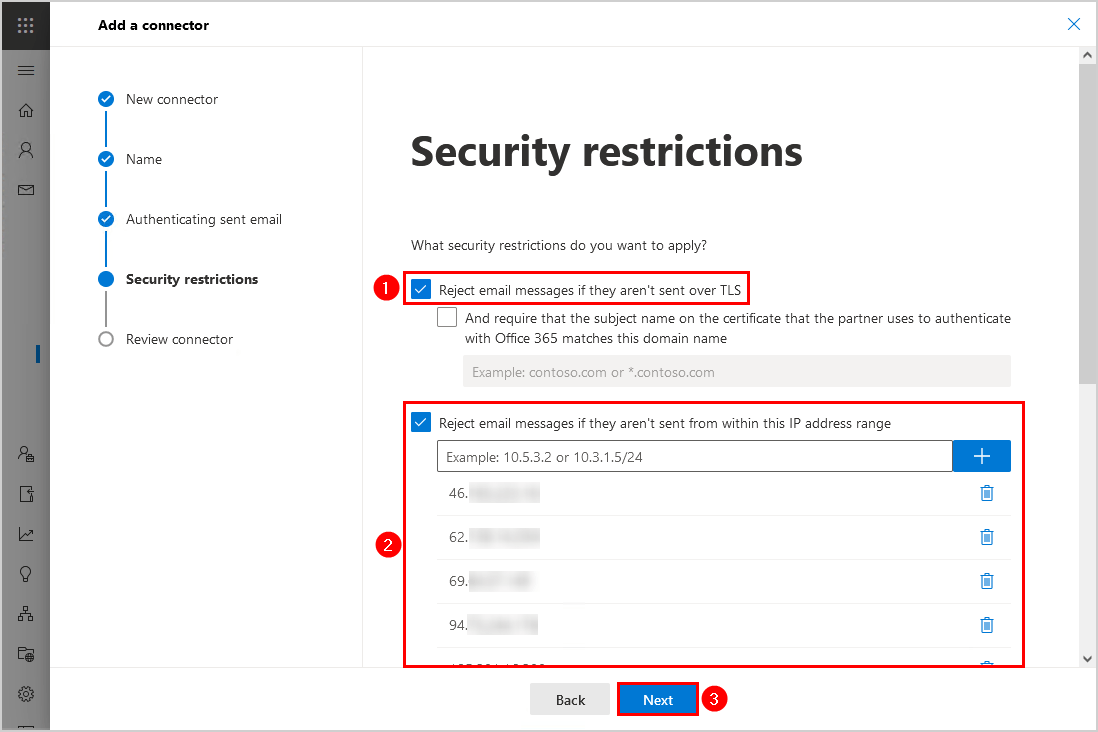
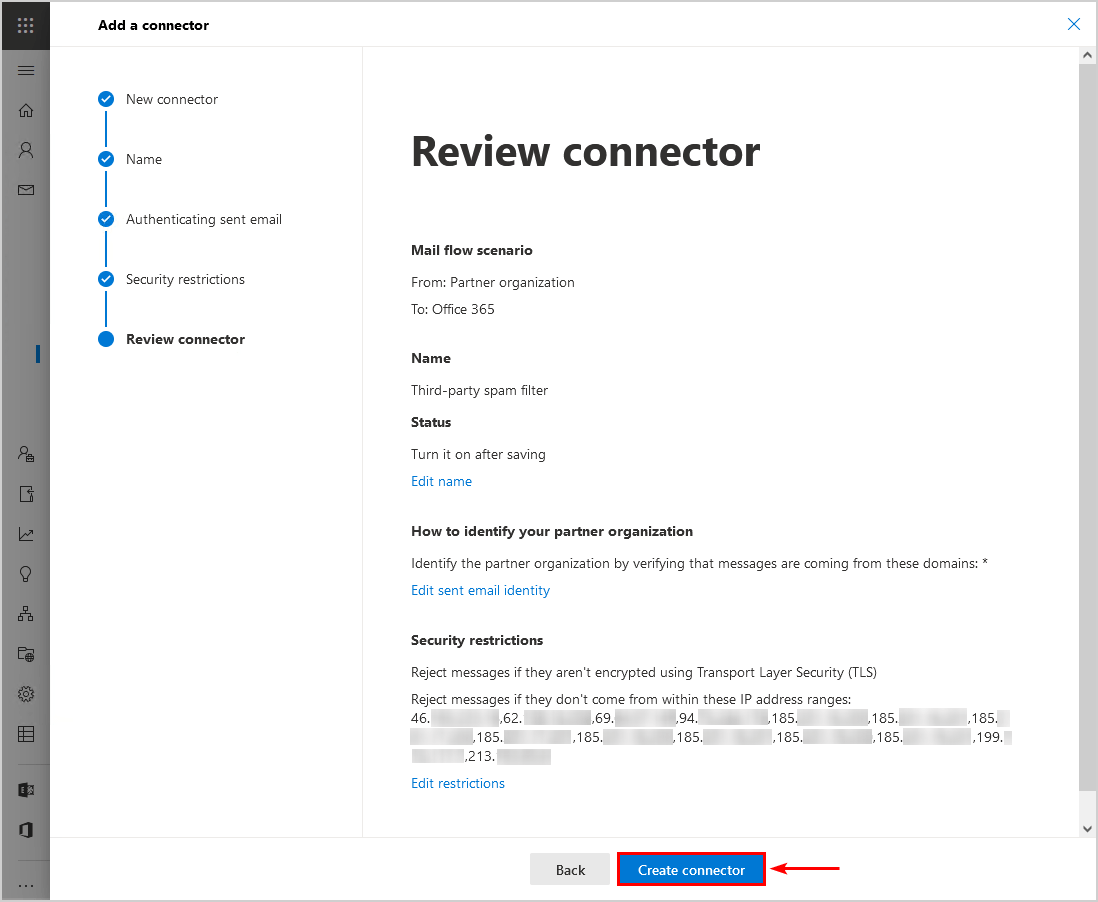
6. Review the connector and click on Create connector.
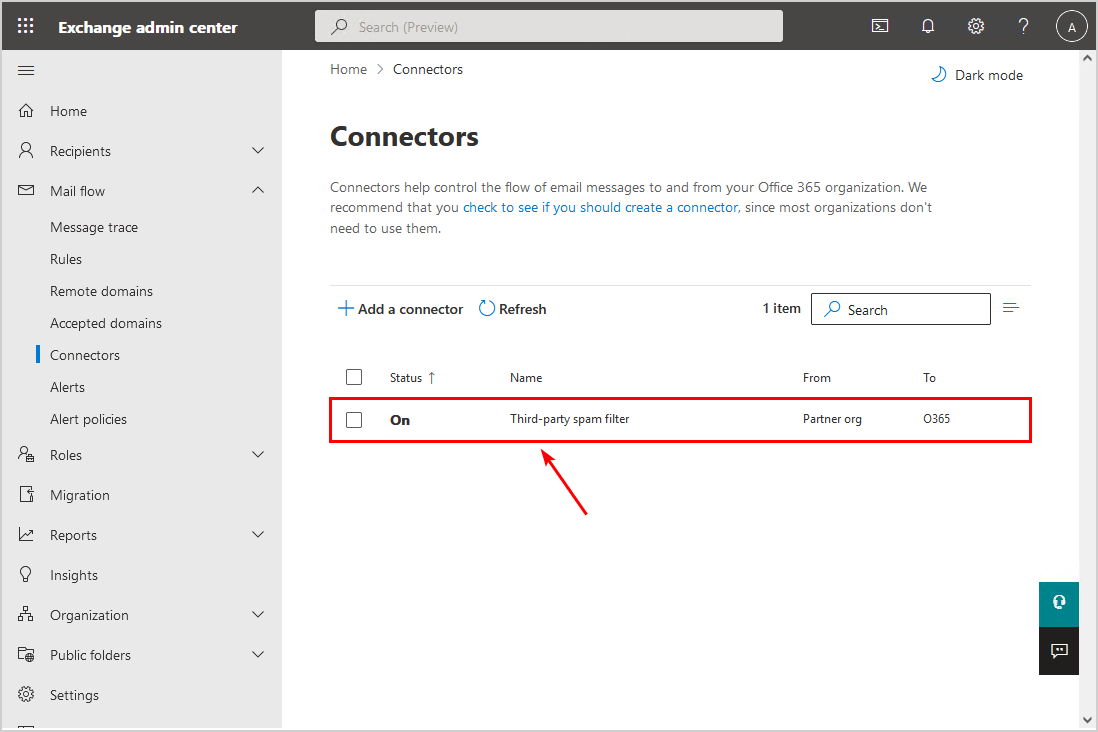
7. The inbound connector appears in the Connectors list.
Configure enhanced filtering on connector
Enable enhanced filtering on the connector you created in the previous step. Go through the article how to configure enhanced filtering for connectors (skip listing).
Test Microsoft 365 only accept mail from third-party spam filter
Let’s try it out and see that everything works as you expect.
Important: Give it 15 minutes before you test the mail filtering, as it needs time to propagate the changes in the Microsoft cloud servers.
Send email to Microsoft 365 MX record hostname
We will use the Wormly SMTP test tool to send a message and use the Microsoft 365 MX record hostname as the SMTP server. You can also try to use telnet and send a message. But, some ISPs close port 25, and you can’t proceed. So it’s good to use an external SMTP test tool, as shown here.
Fill in the below details:
- Hostname or IP: The Microsoft 365 MX record
- Email address: The user’s email address
- TCP port: 25 or leave empty
- Send SMTP test email?: Yes (so we can inspect the message header)
After you fill in everything, click on the button START SMTP TEST.
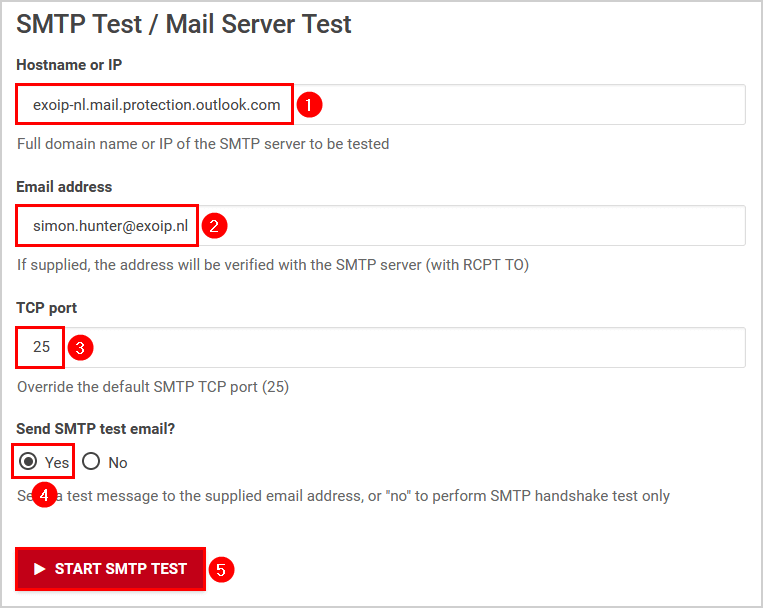
The STMP test results show that it resolved the MX record to an IP address and CAN’T send the message to the user’s mailbox.
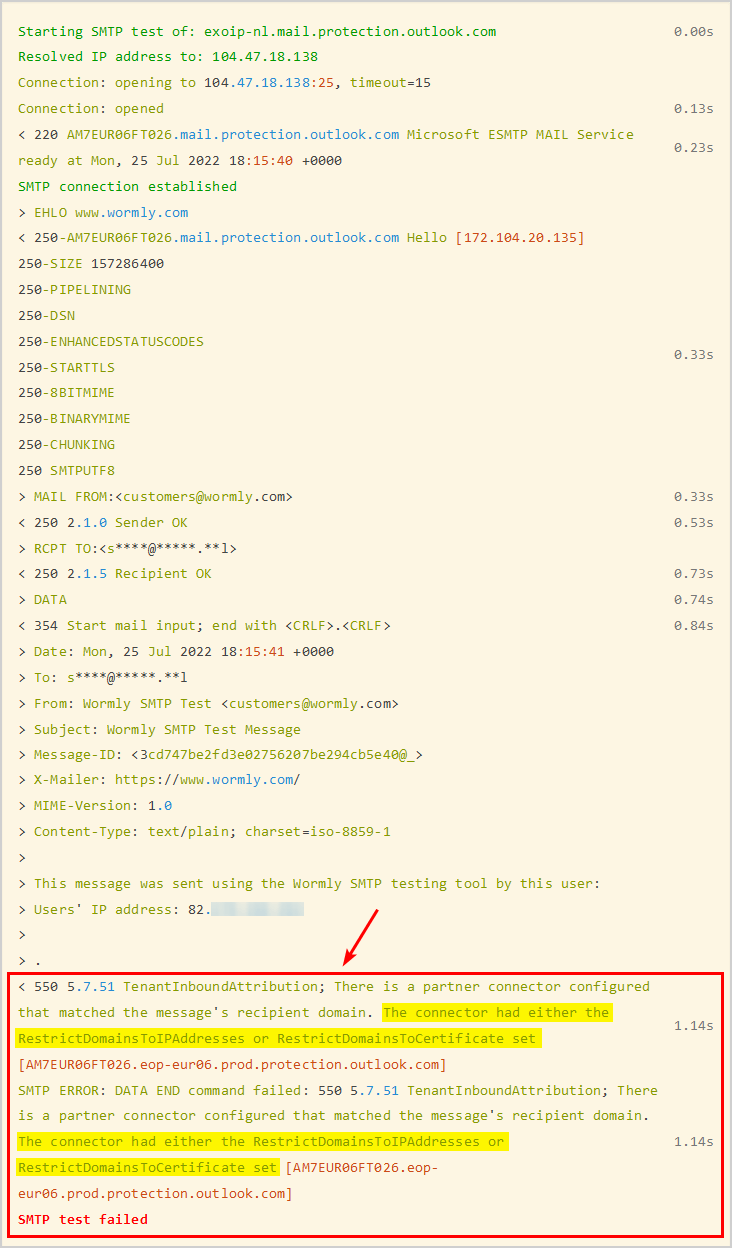
The error in the below text (which is the expected behavior and is good):
< 550 5.7.51 TenantInboundAttribution; There is a partner connector configured
that matched the message's recipient domain. The connector had either the
RestrictDomainsToIPAddresses or RestrictDomainsToCertificate set
[AM7EUR06FT067.eop-eur06.prod.protection.outlook.com]
SMTP ERROR: DATA END command failed: 550 5.7.51 TenantInboundAttribution; There
is a partner connector configured that matched the message's recipient domain.
The connector had either the RestrictDomainsToIPAddresses or
RestrictDomainsToCertificate set [AM7EUR06FT067.eop-
eur06.prod.protection.outlook.com]
SMTP test failedSend email to Microsoft 365 user
Sign in to a Gmail account or another external mail provider. Next, send an email to the Microsoft 365 user. After that, view message details and copy the message header.
Paste the copied message header into Message Header Analyzer by Microsoft. Click Analyze headers button.
The message went first to the third-party spam filter, routed through Exchange Online, and delivered to the user’s inbox.
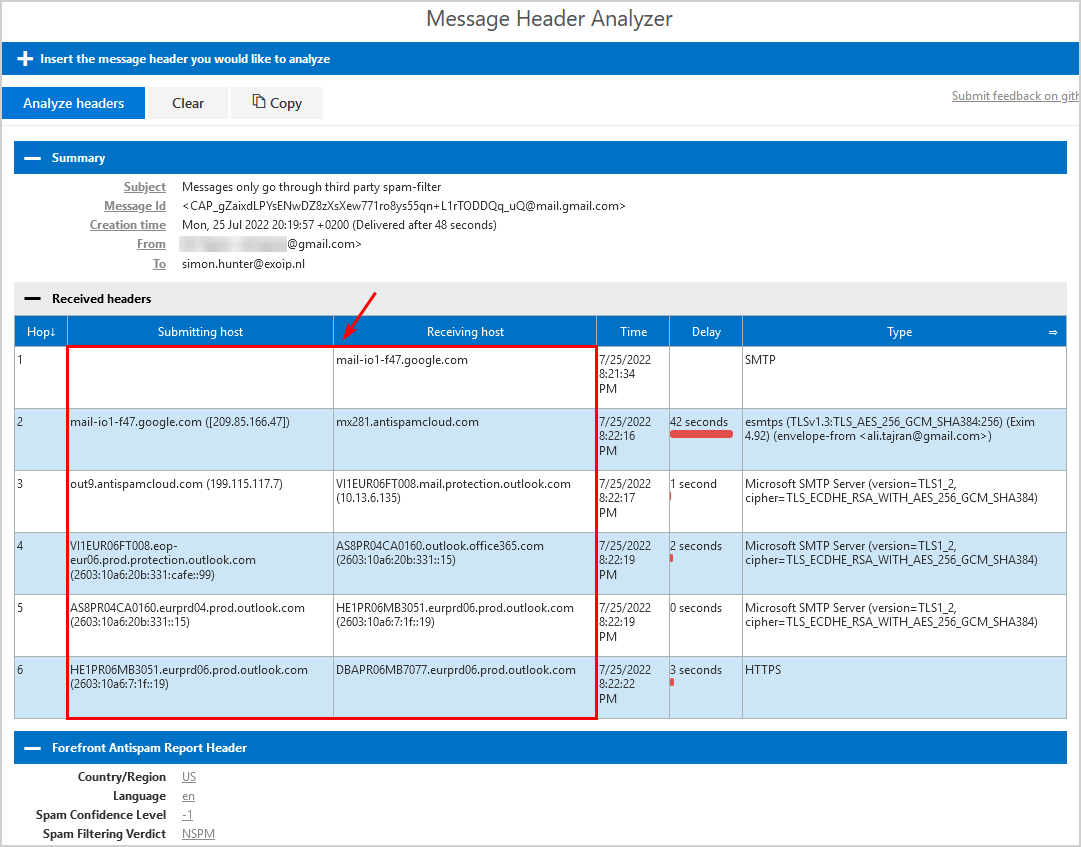
You successfully locked down inbound email flow in Exchange Online to only accept emails from your third-party spam filter.
Read more: Protect domain from spam, phishers and viruses »
Conclusion
You learned how to configure Microsoft 365 to only accept mail from third-party spam filter. After the configuration is set up, spammers can’t bypass the MX records and deliver mail direct to Exchange Online. Instead, everything will go through the third-party service for mail filtering, and you’re protected as it should.
Did you enjoy this article? You may also like Add tag to external emails in Microsoft 365 for extra security. Don’t forget to follow us and share this article.


how to Exclude external teams meeting invite forwarded emails to internal emails
Hello Ali,
I went through the configuration of the partner to O365 connector, and I verified it was working a while ago. I just tested it again, and now it’s not working, it allows the Wormly tester to send a test message without blocking it. I’ve looked over the page here and how we’ve got the connector set up and it sure looks like it should work.
Do you have any tips for how to debug what is going on? Are there logs someplace that would show how a given message is processed?
Thanks
What is needed to block when Hybrid is enabled with centralized mail transport and mailboxes still on-prem? I’ve seen e-mail sent from O365 to Org using an outbound connector to the onprem mailbox.
Hi Ali,
The connector did not work for me the way I expected. Testing still allowed messages to be sent directly to the Office 365 address, bypassing the 3rd party filter?
I had to setup a rule to block everything from outside the organization except what comes from the 3rd party spam filter to stop the messages from coming into Office 365 directly?
Is that what you have found, or did I miss something?
Thank you,
Dan
Hi Dan,
I configured this for a new Microsoft 365 tenant, and it works perfectly.
Remember that you need to wait at least 15 minutes for the changes to take effect before you do a test.